A hacker installed Huntress on their machine—see what we uncovered.

There’s a reason cybercrime’s the world’s third-largest economy: hacking’s no longer a solo sport. Now, cybercriminals work at scale and run well-funded organizations that look a lot like your business. Learn who’s behind modern cybercrime, how they operate, and what you can do to protect yourself.

There's your industry competition, and then there's the competition you never thought you had—cybercriminals. Come see John Hammond and YouTuber Jim Browning expose them LIVE.
Mar 18, 2026 | 12:00pm EST / 5:00pm GMT
Mar 31, 2026 | 10:00am AEDT

Imagine a business with specialized offerings, they’re recruiting talent, tracking and improving KPIs, and selling sought-after services. It sounds like they’re growing and successful, right? It might even sound like your business or one of your industry peers. But that’s how cybercriminal groups are operating. And here’s how they do it.
Latest Trends | Ransomware | Business Email Compromise | Your 24/7 Team | Huntress Products


Increase in RMM abuse
Of malware loader activity involved ClickFix & fake CAPTCHAs
Were added to the average time-to-ransom (TTR)

RANSOMWARE
Ransomware groups make up a huge chunk of the cybercrime economy for a reason: their attacks work. If an org isn’t secure, it doesn’t take long for attackers to quietly steal data and take over their infrastructure…at least until they get paid. But here’s how you wreck ‘em.



BUSINESS EMAIL COMPROMISE
While the cybercriminals behind business email compromise are after wire transfers and stolen data, they get there by targeting human trust—and they’re only getting better at it. (Just not good enough to hide from Huntress, though.)



YOUR 24/7 TEAM
While cybercriminals work on new ways to wreck you, the Huntress Adversary Tactics and SOC teams are busy finding new ways to wreck them. Whether we’re shutting down novel exploits, building tech to stop threats like ransomware and BEC, or hunting and stopping threats 24/7, Huntress has your back.

HUNTRESS PRODUCTS
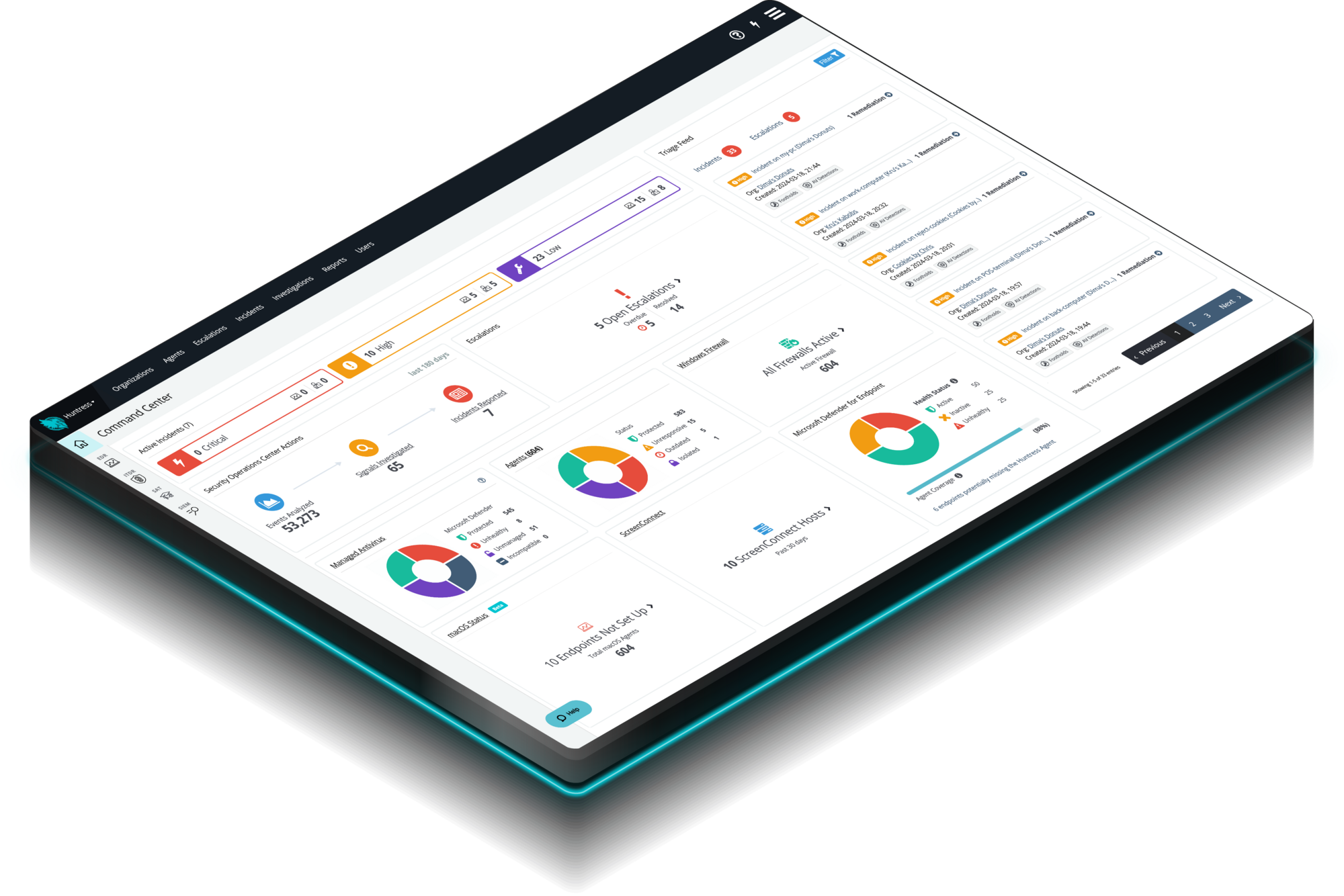






Huntress Managed EDR doesn't just watch your endpoints—it’s a complete solution. From the second a threat appears until it’s eliminated, we handle everything. You get 24/7 continuous protection, detection, and response that disrupts and remediates threats.
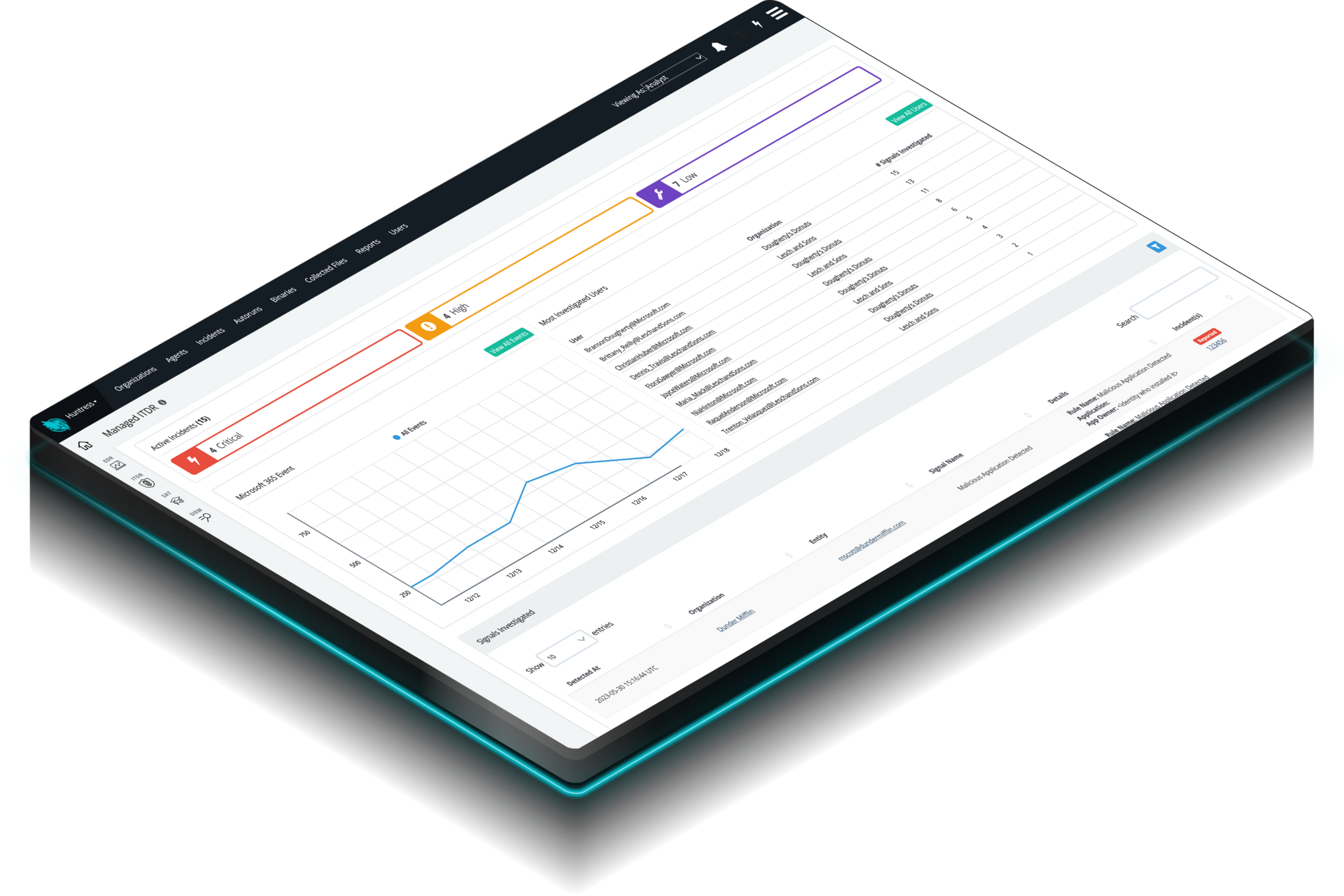
Identity Threat Detection and Response (ITDR)
Finds and stops identity-based threats in Microsoft 365—because identity is the new endpoint, and attackers know it. Huntress Managed ITDR is designed to detect, respond to, and resolve critical identity-based threats like account takeovers, business email compromise, unauthorized logins, and more.
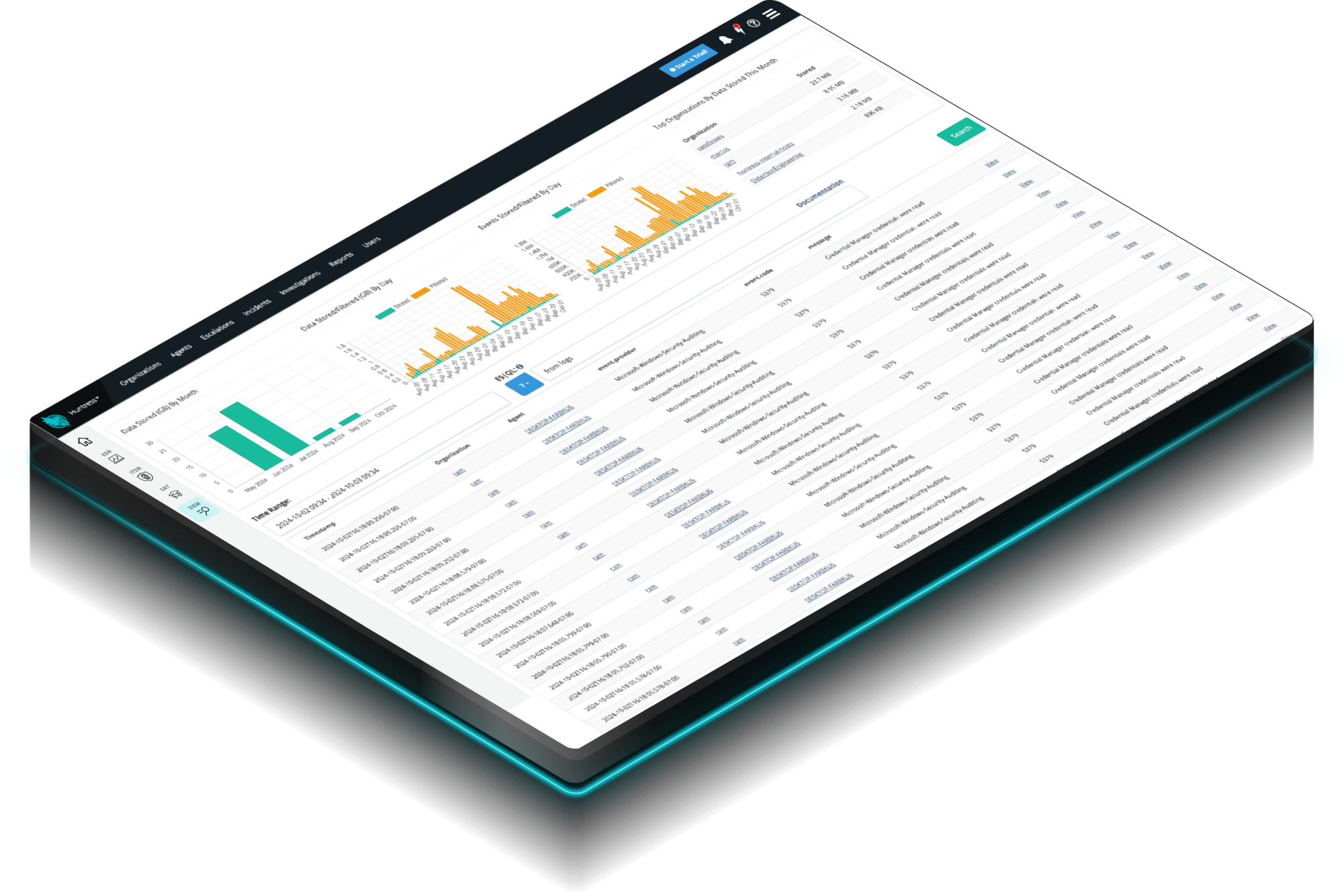
Huntress Managed SIEM takes away the complexity and overhead usually associated with traditional SIEMs, giving you everything you need and nothing you don’t. 24/7 threat response and strengthened compliance, fully managed by SOC experts, at a predictable price.
Engaging, expert-backed, personalized training content built on real-world threat intelligence and created by Emmy® Award-winning animators to reduce human risk and build a strong security culture.

The Huntress Security Platform combines powerful managed detection and response tools for endpoints and Microsoft 365 identities, science-backed security awareness training, fully managed SIEM, and the expertise of our AI-augmented, 24/7 Security Operations Center (SOC).
Cybercriminals might be your competition, but we’re their competition. So wherever they go, they won’t stand a chance. Book a demo to see it yourself.