Endpoint Detection and Response Built for Every Business
Huntress Managed EDR gives you an unfair advantage against hackers with comprehensive, enterprise-grade protection, continuously backed by our 24/7 AI-assisted SOC



What Users are Saying

How Huntress Managed EDR Wrecks Hackers

Huntress’ EDR solution is endpoint security made for your business. We don’t rely on other vendors' EDR tools, tied to their pace of development and innovation. We own and build our tech to move and respond faster, focusing on what’s most important to defend against the latest hacker tradecraft.
A global team of threat experts helps power Huntress Managed EDR. While others chase headlines, we’re the ambulance in the cybersecurity community, finding and responding to new threats and attacks first and distilling those insights into our EDR.
Most teams can’t afford a 24/7 SOC to continuously monitor their endpoints for hacker activity, and prioritize and respond to potential threats. Our EDR integrates the tech, expert human oversight, and 24/7 AI-assisted SOC and threat hunters without adding to your workload, so you can focus on your most critical priorities, not chasing alerts and false positives.


Enterprise-Grade EDR



Hackers love hiding in plain sight. Huntress’ EDR solution identifies the abuse of legitimate applications and processes that attackers use to stay hidden on your endpoints.

Attackers change their tools constantly, but their techniques stay consistent—so we focus on behavioral analysis to spot and stop shady hacker activity.

Like a canary in a coal mine, Huntress monitors for early indication and detection of ransomware activity to take action fast and contain the threat.

Make your endpoints more resilient with intel on open ports and unsecured credentials. External Recon gives details on exposed ports that gives attackers an opening into your enterprise. We discover and alert on potentially unsecured credentials stored on endpoints before hackers find them.

An industry-leading 8 minute MTTR minimizes the impact to your business. We don’t stop there, including remediation to evict threats from endpoints, plus guidance on improving defenses to make your enterprise resistant to future attacks.

Get more from your Microsoft investment. Huntress manages Microsoft Defender Antivirus at no additional cost. You get our recommended configs and risky exclusion monitoring to make Defender Antivirus even more effective.
Get the next-level outcomes every enterprise deserves.

You get a team of threat experts and hunters and our 24/7 AI-assisted SOC handling every alert from detection to resolution. We do the heavy lifting managing EDR, giving you outcomes not headaches.
Protection from threats is a necessity, not a luxury. That’s why our EDR includes everything in one straightforward price—no add-ons, no service tiers, no BS. You get everything that is needed to wreck hackers, not your budget.


Featured Case Study
How Do You Sleep at Night: The Real Value of 24/7 Coverage
For UK-based managed service provider Greystone Technology, Huntress is more than just a product—it's peace of mind
The Huntress Platform
What people are saying about Huntress Managed EDR








Cybersecurity Education
The Ultimate Buyer’s Guide to EDR
Most EDR tools aren’t built for the needs of all enterprises. So how do you pick the right one? Don’t worry, we’ve got you covered. Download our comprehensive guide on how to find the right EDR solution.
How to evaluate your EDR requirements
What capabilities to consider (and avoid)
The differences between self-managed EDR versus Huntress EDR
How to evaluate your EDR requirements
What capabilities to consider (and avoid)
The differences between self-managed EDR versus Huntress EDR


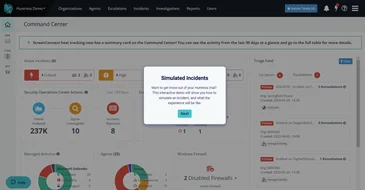
Watch Huntress Managed EDR in action
Take a self-guided tour to see the power of our EDR.



See how threats are remediated

Walk through a macOS incident
Learn how Huntress Managed EDR customers get peace of mind


Frequently Asked Questions
Endpoint detection and response (EDR) is a technology that helps detect, investigate, and respond to threats that get past automated defenses like antivirus. It captures endpoint activity telemetry that is used to detect suspicious activity, support investigations with data and context, and enables a threat to be contained and remediated.
Managed EDR is a comprehensive approach that provides end-to-end coverage, from managing the EDR solution to finding and stopping threats abusing an enterprise’s endpoints. It’s inclusive of the technology (agents, platform), management of the tech, threat expertise to tune the tech to detect the latest threats, and continuous threat detection, response, and remediation by a dedicated 24/7 AI-assisted SOC backed by humans.
Managed detection and response (MDR) services focus on monitoring and responding to alerts generated from a customer’s self-managed security tools, like EDR, network detection and response (NDR), and SIEM. Many MDR providers integrate a customer’s tool into their platform that is monitored by a SOC. Some technology vendors bolt-on MDR services for their customers to layer on SOC services.
Managed EDR is a comprehensive approach that provides end-to-end coverage, from managing the EDR solution to finding and stopping threats abusing an enterprise’s endpoints. It’s inclusive of the technology (agents, platform), management of the tech, threat expertise to tune the tech to detect the latest threats, and continuous threat detection, response, and remediation by a dedicated 24/7 AI-assisted SOC backed by humans.
Huntress Managed EDR removes the challenges with managing, tuning, and monitoring an EDR tool, allowing enterprise IT and security teams to focus on other critical priorities. The technology is fully managed, reducing the day-to-day operational burden for teams. It includes threat experts who are constantly finding and understanding the latest hacker tradecraft to ensure the EDR solution can detect the latest threats and minimizes false positives. And it addresses one of the biggest challenges leaders and teams face: how to monitor, analyze, and prioritize alerts around-the-clock, which is prohibitively expensive for most enterprises and organizations. It does this as a low-impact, easy-to-deploy solution, available for a simple, affordable, and predictable price without any hidden costs.
With Huntress Managed EDR, you get effective, proactive endpoint protection powered by advanced threat detection technology and human experts that always have your back. With real-time threat detection, response, and remediation backed by our 24/7 AI-assisted Security Operations Center (SOC), Huntress gives you peace of mind with round-the-clock protection that’s always on.
Plus, our lightweight, user-friendly agent for Windows and macOS is designed for easy deployment with seamless operations, and we manage it for you.
Finally, you also get straightforward pricing with no hidden fees and unmatched scalability, making Huntress the smart choice for enterprises serious about keeping their endpoints safe so they can remain focused on what matters the most.
Huntress Managed EDR is an excellent solution for environments running a mix of operating systems (OSs). Huntress covers all three major OSs - Windows, macOS, and Linux. This is vitally important as attackers are abusing all of these OSs, whether it’s for ransomware, credential theft, malware, or other threats. Attackers are crafty and even use cross-platform attacks (like LockBit v5.0) looking for any advantage to infiltrate a business and wreak havoc. Therefore, comprehensive coverage across all the OSs used in your environment helps reduce the shadows hackers like to hide in, making sure all the endpoints in your business are protected.


Continue Exploring the Huntress Platform

Capture what matters. Ignore what doesn’t.
Shield your Microsoft 365 environments and employee identities.
Empower your teams with science-backed security awareness training.


Ready to experience next-level endpoint protection?
See how our EDR goes beyond other vendors’ EDR products to deliver next-level endpoint protection for all enterprises.














