In today’s always-connected world, the line between dark and light is blurring.
Well, actually, you’re still protected from finding out what the dark web looks like because you need to download a special browser to access it. But the drama of the dark web can be intriguing. And it’s not all wicked criminal activity either.
Curious about what’s lurking in the shadows of the internet? Keep reading to learn more about the state of the dark web, what it is, and how to access it (safely, of course!).
What is the dark web?
Everyone has their own preconceived notion of what the dark web is. (Of course, with a name as ominous as dark web, it kind of sets the mood, right?) For the sake of this blog, we focused on finding a credible definition that isn’t muddied with preconceptions. So, we turned to the dictionary.
According to the Merriam-Webster online dictionary, the dark web is:The set of web pages on the internet that can't be indexed by search engines, are not viewable in a standard web browser, require specific means (like specialized software or network configuration) in order to access, and use encryption to provide anonymity and privacy for users.
(If you were expecting a more sinister-sounding definition for the term dark web, you’re not alone. 😅)
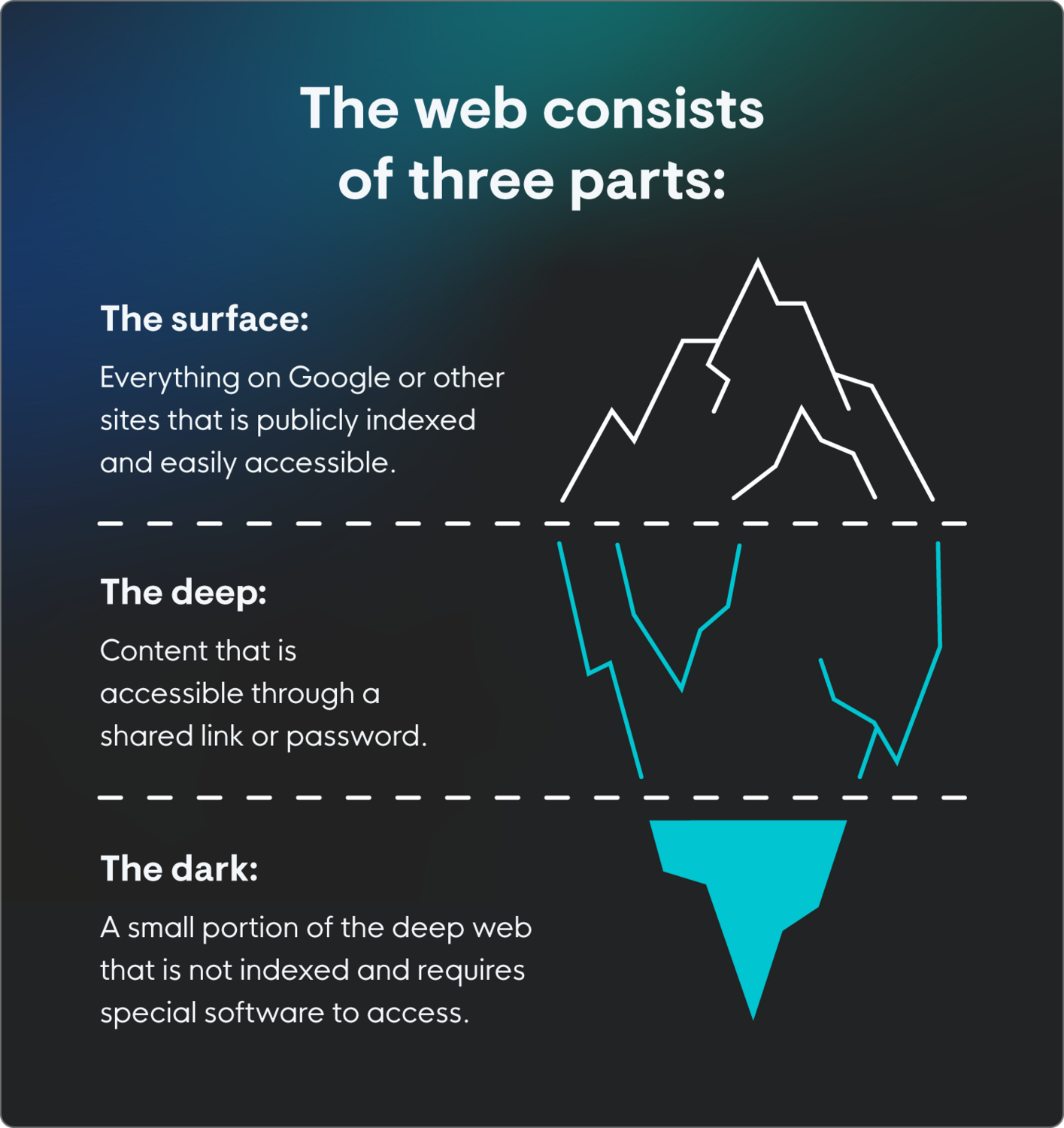
The web, as a whole, can be divided into three parts: the surface web vs. deep web vs. dark web:
-
Surface web: The surface web is everything that’s automatically indexed by search engines. It’s everything that pops up when you Google something (or Bing or whatever search engine), and you don’t need any sort of special software or login to access it.
-
Deep web: The deep web is sites that are not indexed, but are accessible to the average person, usually through encryption or password protection (or both, both is good!). This includes things like online banking and cloud storage.
- Dark web: This is where things get…different. As we said, dark web activity isn’t indexed and requires special software or network configuration to access. While it can be a place where people broker illegal activities, it can also be used for legal activities, like anonymously sourcing information.
|
Surface web |
Deep web |
Dark web | |
|
Indexing |
Yes |
No |
No |
|
Accessibility |
Standard browser |
Standard browser with a login or link |
Special software required |
|
Common domain |
.com, .org, .net, .gov |
.com, .org, .net, .gov, with additional authentication |
.onion |
|
Estimated size |
Smallest portion (~5%) |
Largest portion (~90-95%) |
A tiny subset of the deep web (<0.1%) |
|
Primary content |
Publicly available, general information, news, e-commerce, and social media |
Private, secured, and dynamic data (e.g., email accounts, online banking, cloud storage, medical records, private company intranets) |
Anonymous sites, darknet markets, whistleblower platforms, forums, sites for political dissent, and illegal content |
|
Legality |
Legal |
Legal and routinely used |
Legal to access, but does have high levels of illegal activity |
|
Risk level |
Low to moderate |
Low |
Can be high |
What does the dark web look like?
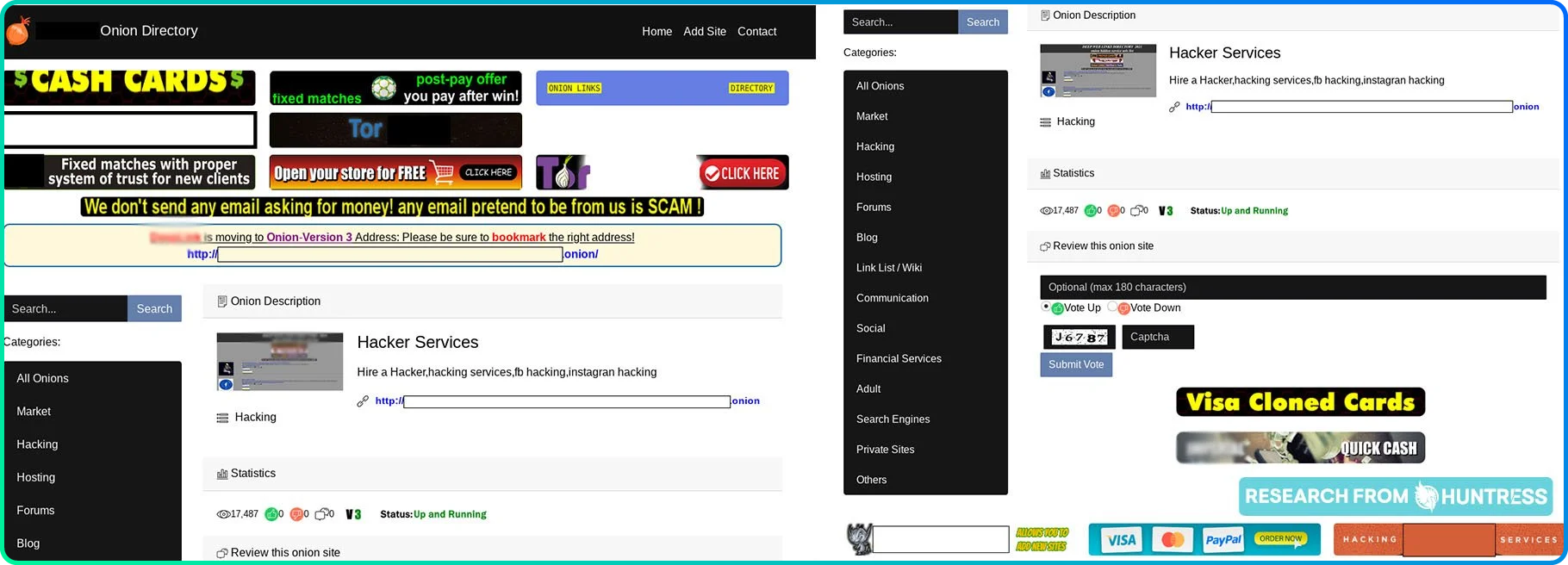
The dark web often looks surprisingly ordinary—with familiar features like About Us sections, pricing pages, and even customer reviews. You’ll see, though, in the screenshots below, that a lot of sites are basic or outdated, often tricky to navigate.
Many of these sites still work like any other ecommerce website. Threat actors advertise, highlight their skills, and market themselves, their expertise, and their services just like any salesperson.
How does the dark web work?
Frankly, the dark web has earned a bad reputation—and unfairly so. At its core, the dark web isn’t inherently evil or mysterious. (Okay, it's a little mysterious.)
It’s simply a collection of websites that require a specific, anonymity-powered web browser to access. Usually, these sites use a .onion domain and are only accessed through the anonymous Tor Browser.
The dark web isn't all crime and chaos—detectives and journalists sometimes access the dark web to do research while maintaining their anonymity. You can play chess on the dark web. At one point in time, you could even navigate to a Tor website and watch a slideshow of cats and kittens submitted by other users.
The dark web isn't any one thing—it's shaped entirely by how people choose to use it.
How to safely access the dark web
Because there are so many different reasons that you might be interested in the dark web, it’s important to know how to access it safely. Here are some tips:
-
Use a dark web browser: Use the official Tor browser to access the dark web. This is the essential tool for "onion routing" that provides anonymity.
-
Use a VPN: While Tor provides encryption, using a high-quality virtual private network (VPN) before launching adds an extra layer of privacy by hiding the fact that you are even connecting to the Tor network from your internet service provider (ISP).
-
Never use personal information: Don’t log into any personal accounts—email, social media, or bank accounts—while using Tor because it immediately de-anonymizes you.
-
Avoid downloads and scripts: Avoid downloading unknown files, especially on the dark web, and disable scripts like JavaScript in Tor's settings—they can be exploited to reveal your identity or install malware.
-
Know what’s legal: Accessing the dark web is completely legal in the US, but engaging in illegal activities (such as buying/selling drugs, weapons, or accessing child pornography) is a serious felony, regardless of anonymity.
Our journey into the dark (web)
We’re firm believers in the buddy system when it comes to doing scary things like journeying through the dark web. Don't worry, though— we’ve suited up, strapped on our protective gear, and done the risky part for you.
How did we suit up?
First, we booted up our virtual machine (VM) to add an extra layer of security while browsing. Then, we fired up our anonymous Tor Browser. Finally, we disabled JavaScript—a quick but important safeguard against websites that run malicious code.
With these precautions in place, we were ready to access the dark web. We began our journey by navigating to a few .onion directories to find some ~shady~ websites to peruse.
One of the first things we found? A Tor scam list, complete with "safe" browsing recommendations. How… thoughtful.
Who is using the dark web?
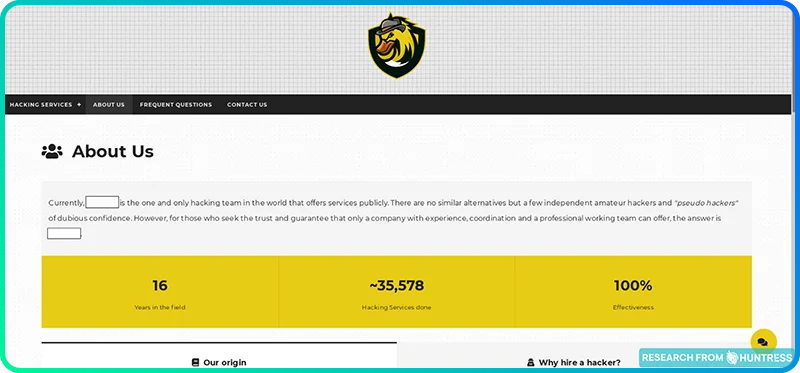
There are About Us pages to answer that question.
Chances are, you wouldn’t hire a plumber without doing some research. You’d want to make sure she’s got the experience and skills to leave your pipes in better shape than she found them. So why would anyone hire a hacker without seeing a well-written About Us page?
You might think this requirement would narrow the pool of hackers to choose from, because are hackers really spending their time writing About Us pages? Yes. Yes, they are.
You’ve got to hand it to them: These hackers did a great job at flexing their hacking skills while staying anonymous. It's not exactly LinkedIn, but the info they share gives these folks some credibility (in a strange way).
If you’ve never browsed the dark web before, you probably weren’t expecting to see several websites with About Us pages. It’s eye-opening to see these hackers flaunting their skills and competing with one another to earn new business.
One site was even gracious enough to list the team’s favorite well-known hackers:
It’s kind of sweet, in a weird sort of way.
The takeaway:Threat actors are just like any other entrepreneurs out to make a profit. The difference? They skip the red tape and regulations that everyone else has to follow. This leaves the door wide open for them to advertise whatever services they please—as long as they abide by the Hacker’s Code of Conduct. (More on that later.)
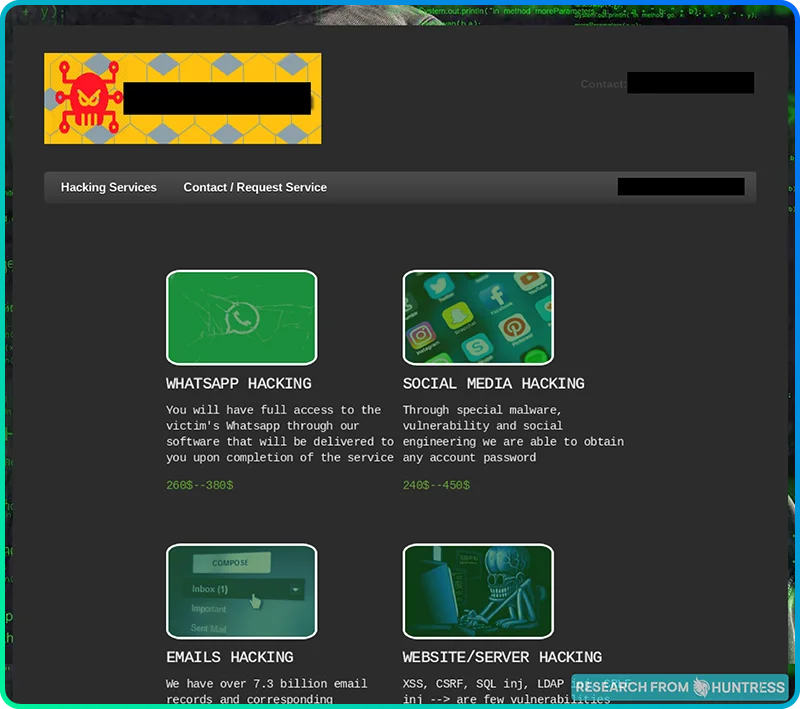
What’s on the dark web?
Product pages, packaged deals, and more.
Now that we know our threat actors, let’s investigate what they can do for us.
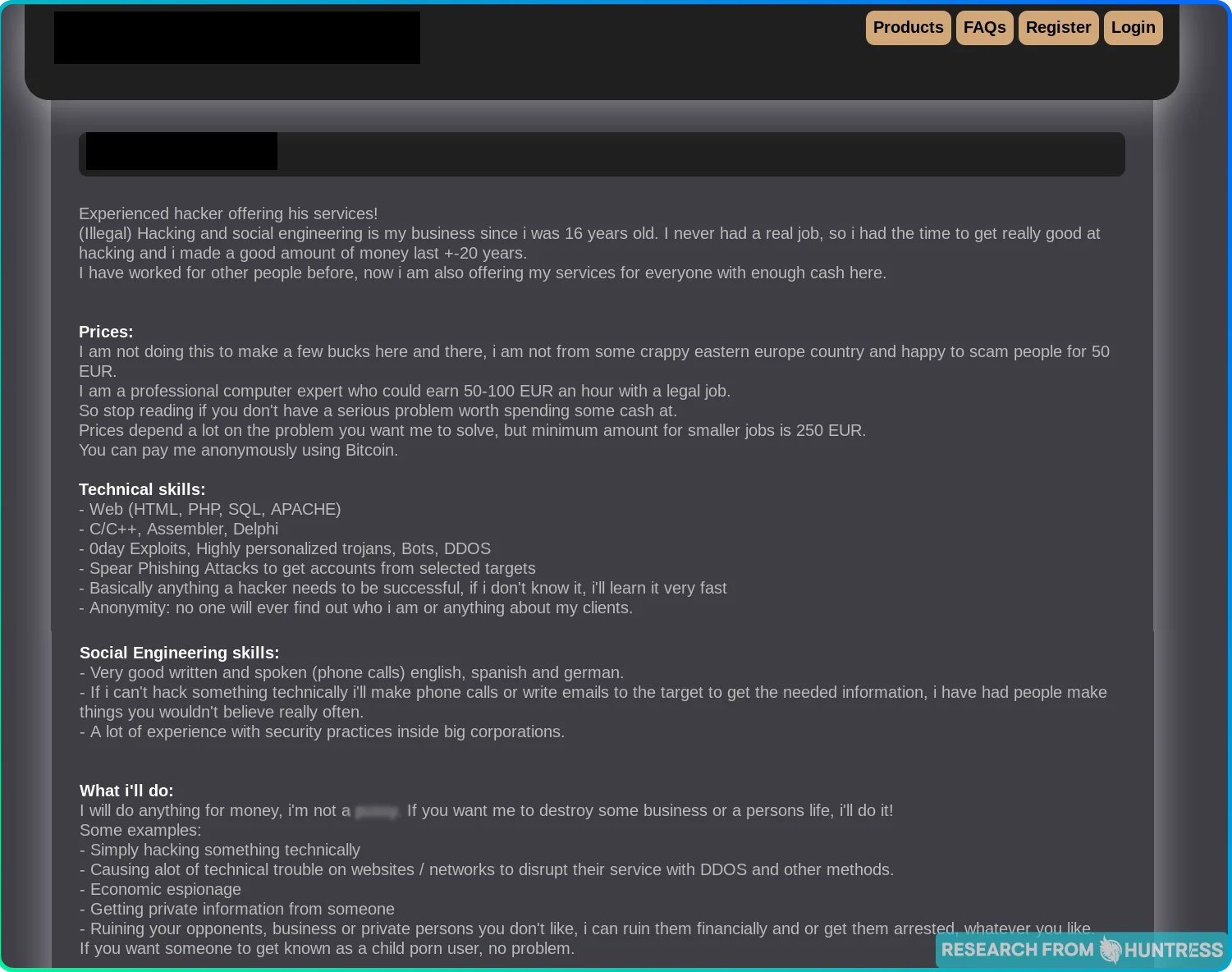
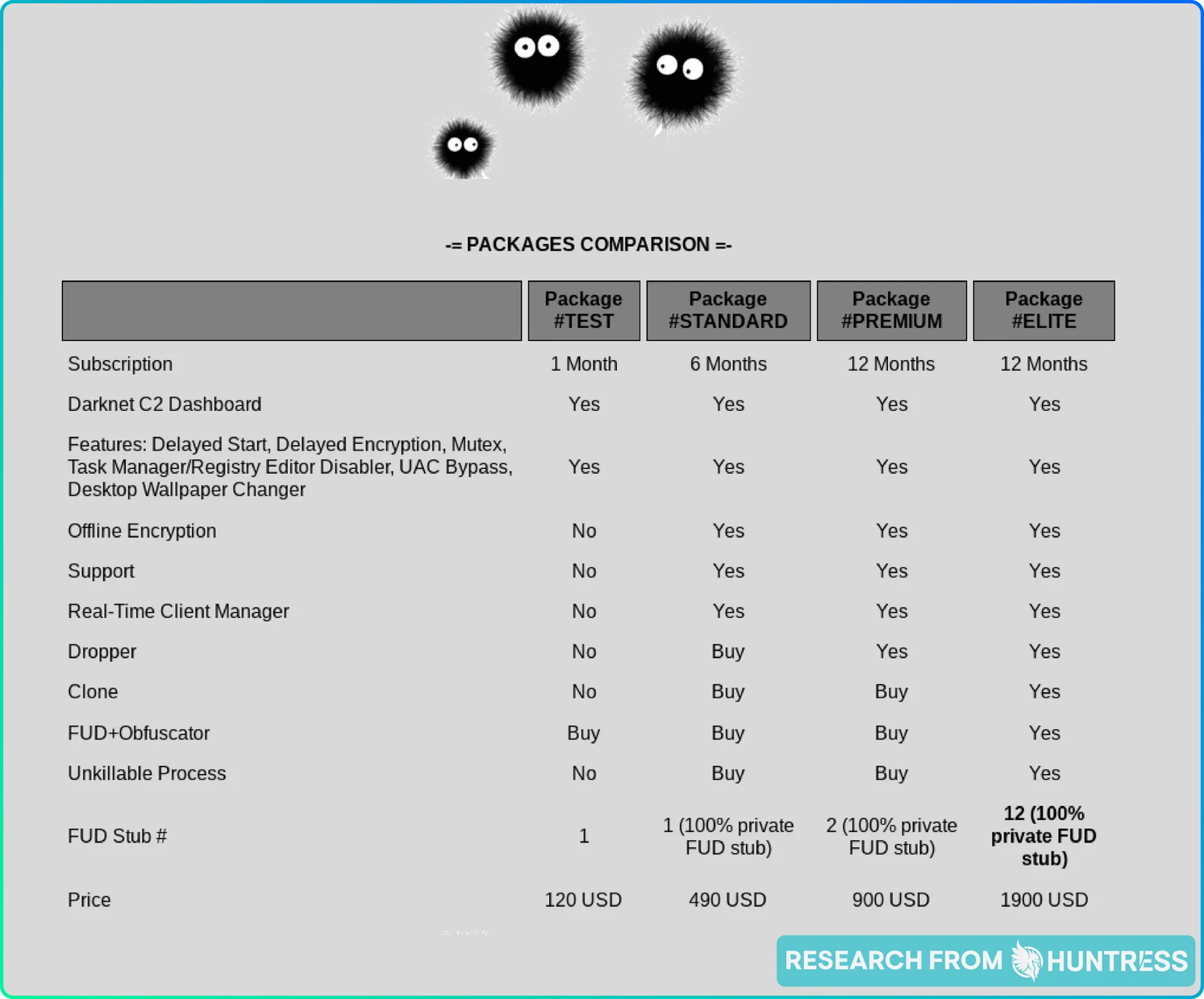
Like any good businessperson, hackers aren’t shy about broadcasting what they can do if the price is right. In fact, some are so business-savvy that they provide packages and tiered solutions:
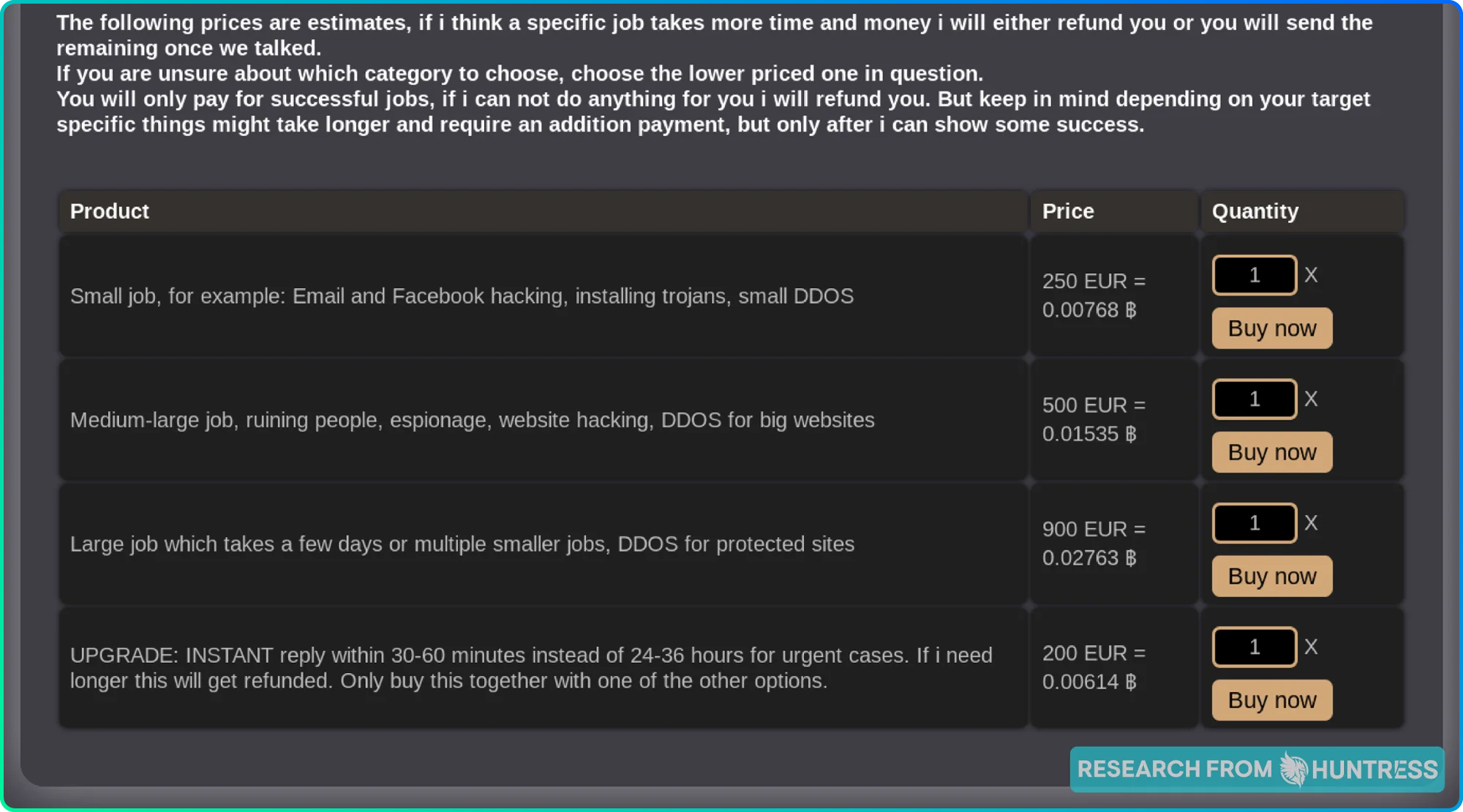
Others simply prefer to put all their services out there for people to pick and choose from:
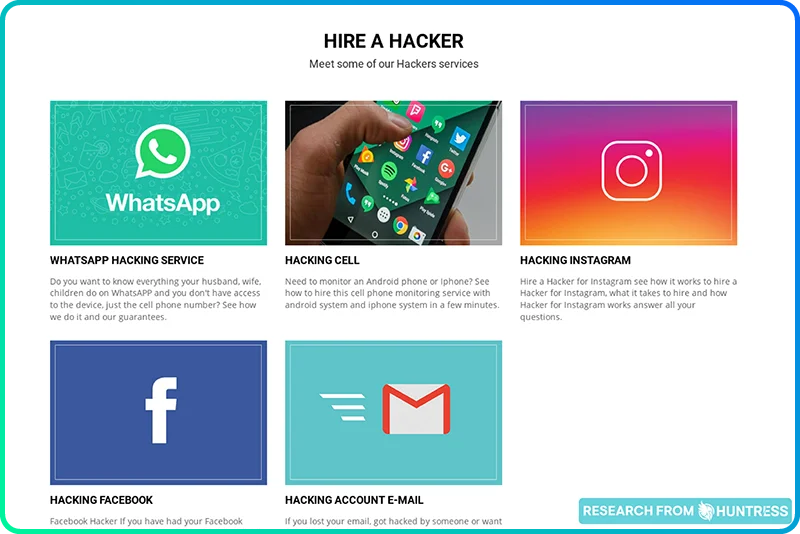
But then, we stumbled across two different websites that made us raise an eyebrow. Here’s the first site:
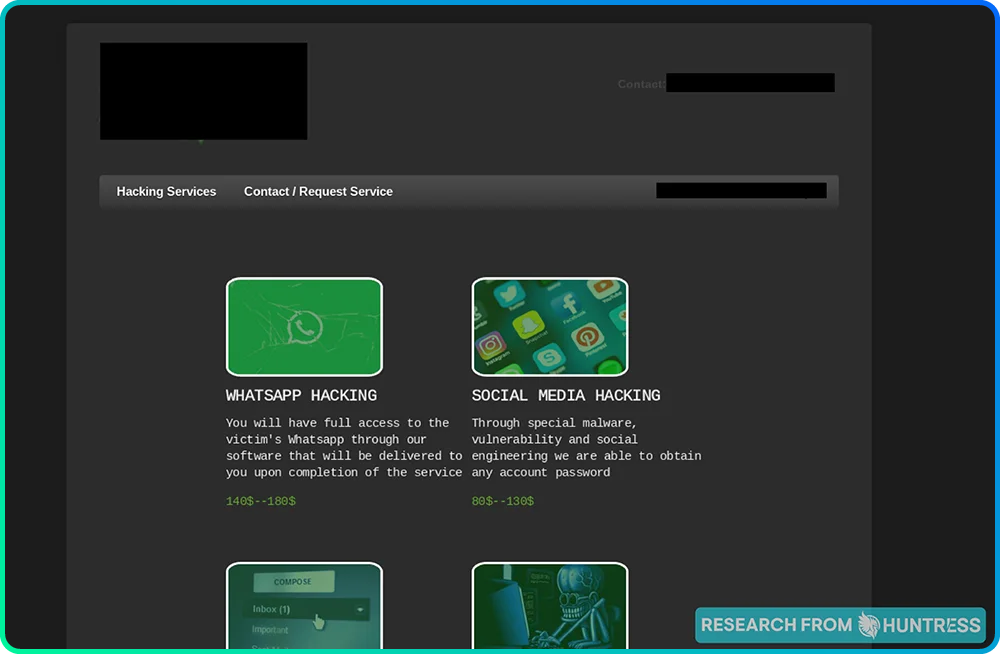
And here's the second site:
These two sites look eerily similar to each other except for one thing: on the latter site, the prices for each service are noticeably higher. That’s weird, wouldn’t you say?
The takeaway: Just like any other website where you can purchase products or services, threat actors also have tiered options, promotional packages, and detailed descriptions of their offerings.
One key difference that seems to be standard across dark web websites is that hackers request that their payments be made in cryptocurrencies. Why? Because it’s anonymous.
Our Principal Security Researcher, John Hammond, nicely sums up why cryptocurrencies are a hacker’s best friend:
"No other technology offers a bad actor the perfect crime: anonymous threats without borders, blackmail and extortion without a financial oversight or governing authority. [...] Unless the bad actors make any unintentional mistake, the inherent design of cryptocurrency makes for a perfect getaway car."
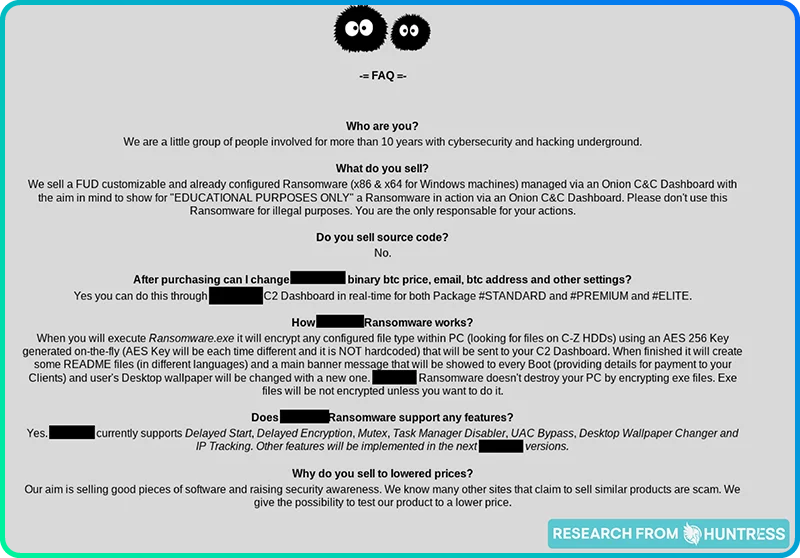
Dark web customer experience and reviews
Threat actors are actually quite concerned with creating a positive customer experience, with features like customer reviews and FAQ on many of the pages we visited.
The takeaway: Just like any other website selling goods and services, threat actors also want to show that they have happy customers and give potential customers all the info they need to make an informed purchase.
Bottom line: The dark web is a business
If a business owner feels she’s been wronged, there are courts for that. The same can be said for hackers. That’s right—threat actors have their very own court system, along with codes of conduct to follow to minimize the chances of landing there themselves.
What happens in “hacker’s court”? The same thing that happens in any other court: Plaintiffs and defendants get together to tell their respective stories in front of a jury before a ruling is made.
We can't stress this enough: Most bad actors today don’t just hack into websites and devices for the fun of it. These are professionals who become experts in their trade and master their skills to earn a paycheck.
They build websites to sell their services, cut their customers special deals, and ask for reviews from satisfied customers. If they’re wronged, they handle it in a civilized manner in hacker’s court. These are organized operations that function just like any other business.
Don’t be afraid of the dark (web)
We hope that this field trip to the dark web has been enlightening. It’s incredible to see just how many parallels exist between anyone with a “normal” day job and dark web threat actors. Many different careers, from marketing and sales to cybersecurity and infosec, have dark-mirror versions of themselves—hackers and scammers running the same playbooks in reverse—on the dark web.
If nothing else, we hope this blog will make you more vigilant against cyberattacks. Hackers are in it for the money. What could destroy your personal records or your business’s reputation is just another payday for a hacker. Think twice before clicking on an email from an unfamiliar sender. Keep your devices updated and install patches as soon as they become available.
Threats can seem overwhelming, but with our in-depth understanding of how threat actors think, we know what to look for. Huntress gives you fully managed endpoint detection and response (EDR), so you've got 24/7 support from security experts ready to respond to threats.
* Special thanks to our Principal Security Researcher, John Hammond, for his help with writing this blog.
FAQ
Is it legal to look at the dark web?
Yes, exploring the dark web is legal—as long as you aren’t breaking any laws. If you’re just browsing or doing legitimate research, accessing the dark web is fine. If you engage in any criminal act, you’ll be subject to prosecution.
What is the dark web actually used for?
The dark web is a mixed bag. Some people use it for both legitimate purposes, like preserving privacy and free speech, especially in restrictive countries, and, unfortunately, others for shady activities like selling stolen data or illegal goods.
How do I know if I’m on the dark web?
If you're using a specialized browser like Tor to access websites ending with .onion that aren't reachable through regular browsers or search engines, congrats (or maybe not)—you're on the dark web!
Can you be tracked on the dark web?
The dark web offers more anonymity, but it's not exactly an invisibility cloak. With sophisticated methods and one careless click, determined parties can still track your activities, so anonymity isn't guaranteed.
What is a crime on the dark web?
Crimes on the dark web include activities like selling illegal substances, hacking services, and trafficking stolen data. Basically, if it's illegal in the real world, it's illegal on the dark web too—no free passes.