
In this exclusive online event, you'll see real-world attack demos, get expert tips, and see how attackers structure their teams, manage projects, and innovate at speed.
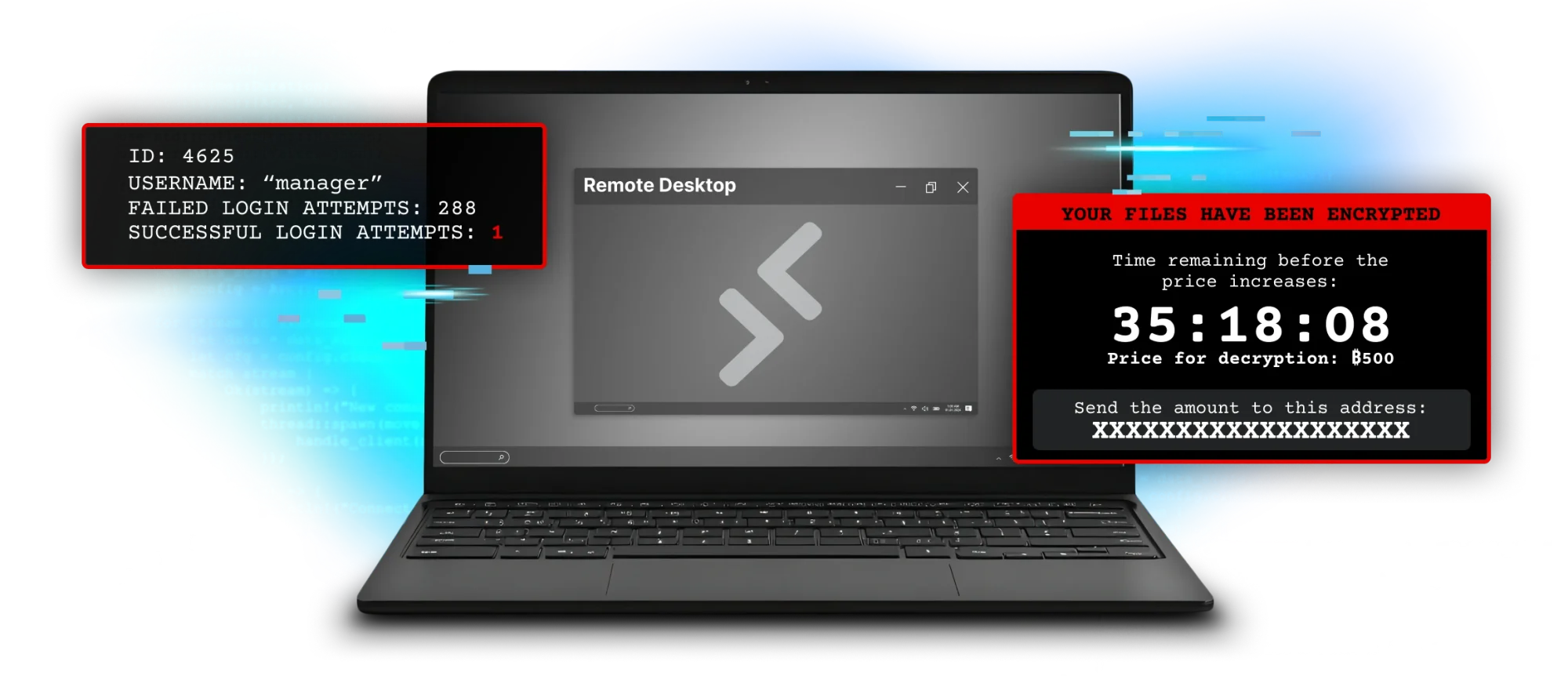
One exposed server. One stolen password. One minute too late. That’s all it takes for productivity to grind to a halt. Downtime, data loss, and costly ransom payments can ruin everything you’ve worked so hard to build. We find the backdoors your current tools missed and wreck the hacker before encryption begins.
Yes, if you have the right visibility across your network and systems. These days, many initial access broker groups and ransomware gangs rely on weaknesses in security tools like firewalls and VPNs to gain access to a network. But they can’t do it quietly, making it possible to detect attacks through log and event monitoring.
Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.


Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.
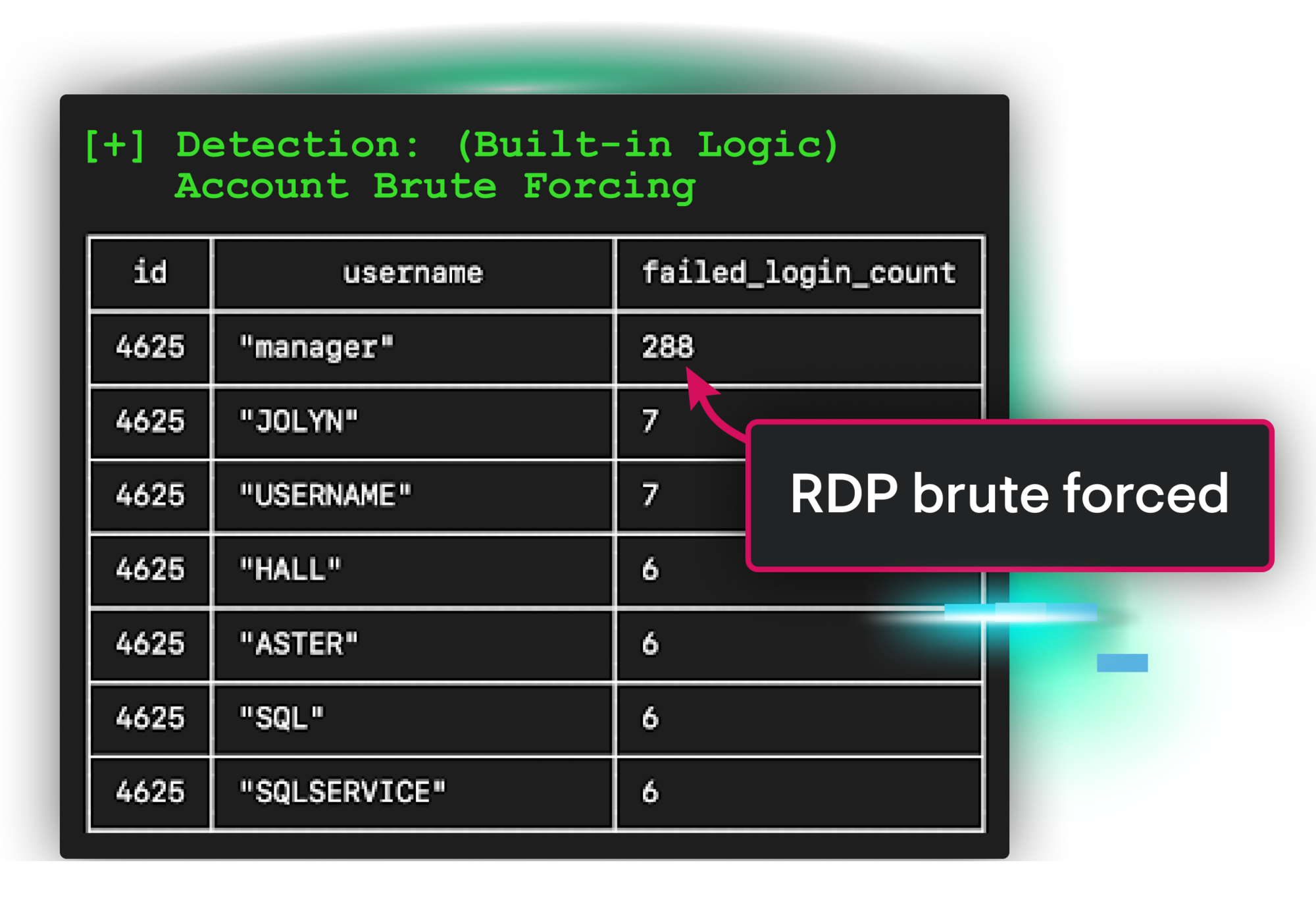
You’re asleep, so you miss what’s just happened—a brute force login. The attacker moves fast. They’re stealing credentials, installing a disguised remote access tool, and hiding persistence under a fake system process.
But Huntress moves faster. Our threat hunters detected the attack, validated it, and acted immediately by:

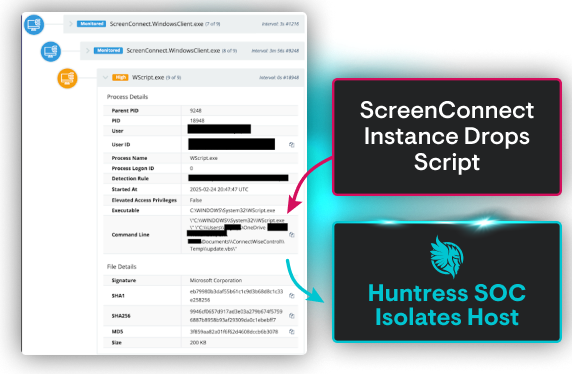
Our SOC—a 24/7 team of elite threat analysts backed by AI—is your always-on force multiplier. We provide the fast, agile response you need to maintain business operations, protect your reputation, and keep your mind at ease.


RAFTRx had expansion down to a science. But their rapid growth meant their tools couldn't keep up. When phishing attacks, suspicious logins, and compromised accounts started causing trouble, their two-person IT team needed backup—like, yesterday.
See how Huntress swapped their growing pains for effortless, scalable protection, helping them onboard seven tenants in just two weeks and putting control firmly back in their hands.


Global threat analyst coverage
Led by a team of elite, industry-recognized threat analysts who’ve seen it all, our 24/7, AI-assisted SOC works around the clock to find and eliminate ransomware threats before they can damage your business.
False positive rate across 4M+ endpoints
Alert fatigue is brutal, and it’ll burn out your most skilled pros. That's why we cut through the noise and surface only the alerts that matter. Let us handle the distractions, so you and your team can focus on what matters most.
Organizations protected by Huntress
We see millions of attacks each year, and every one of them makes us smarter. These insights constantly evolve our tech and our approach to wrecking hackers. The result is greater efficiency for your team and herd immunity across our customers.
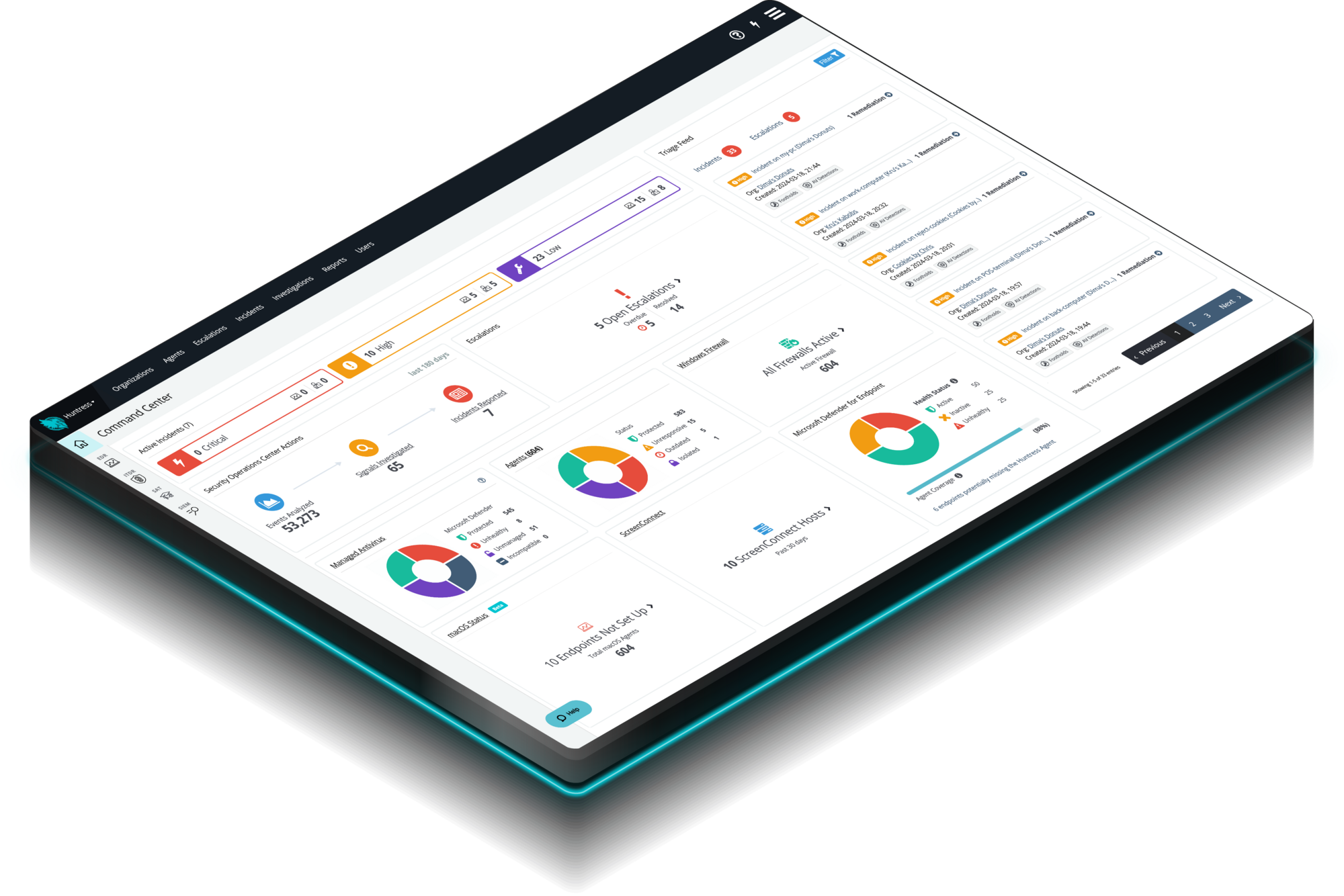






Huntress Managed EDR doesn't just watch your endpoints—it’s a complete solution. From the second a threat appears until it’s eliminated, we handle everything. You get 24/7 continuous protection, detection, and response that disrupts and remediates threats.
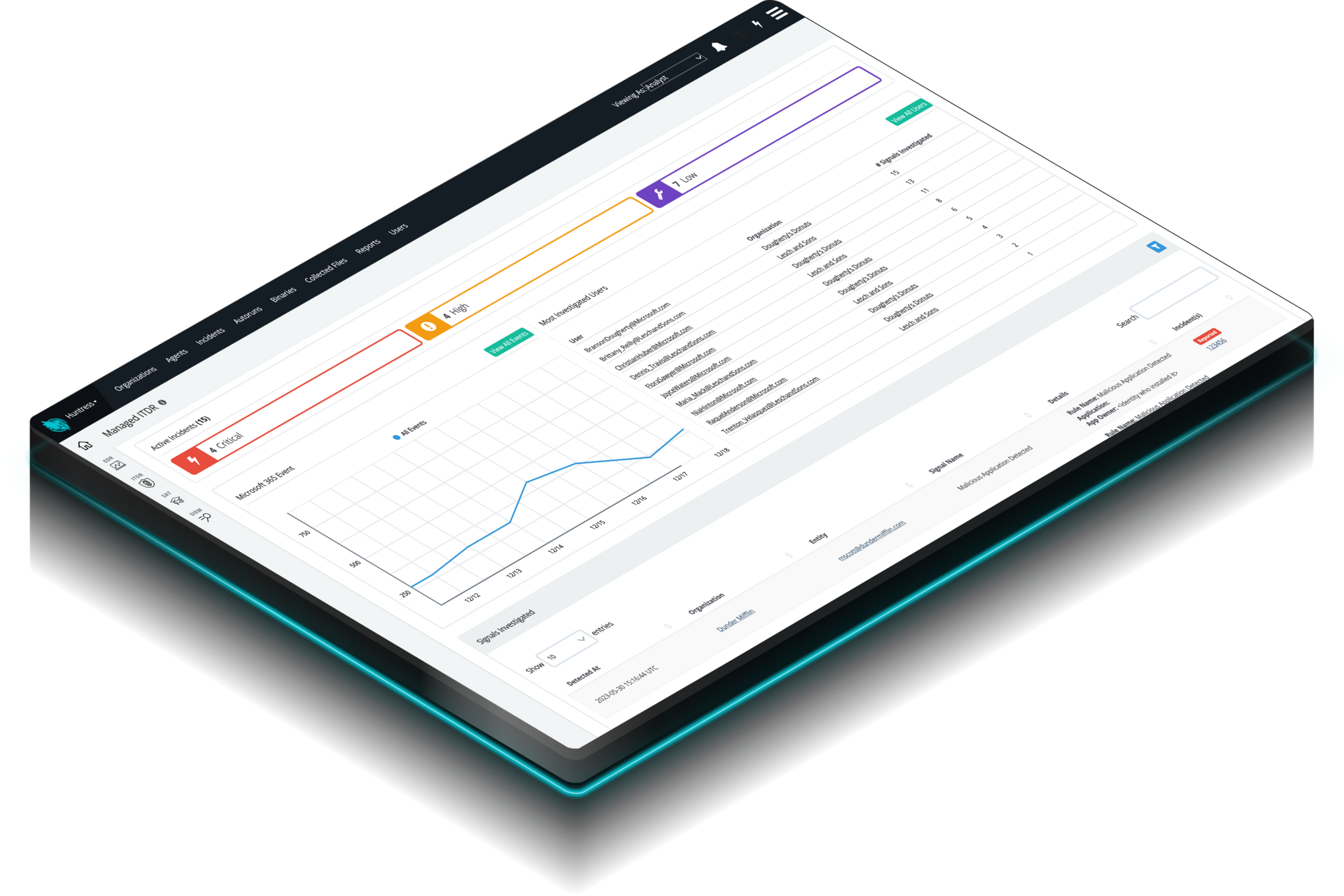
Identity Threat Detection and Response (ITDR)
Finds and stops identity-based threats in Microsoft 365—because identity is the new endpoint, and attackers know it. Huntress Managed ITDR is designed to detect, respond to, and resolve critical identity-based threats like account takeovers, business email compromise, unauthorized logins, and more.
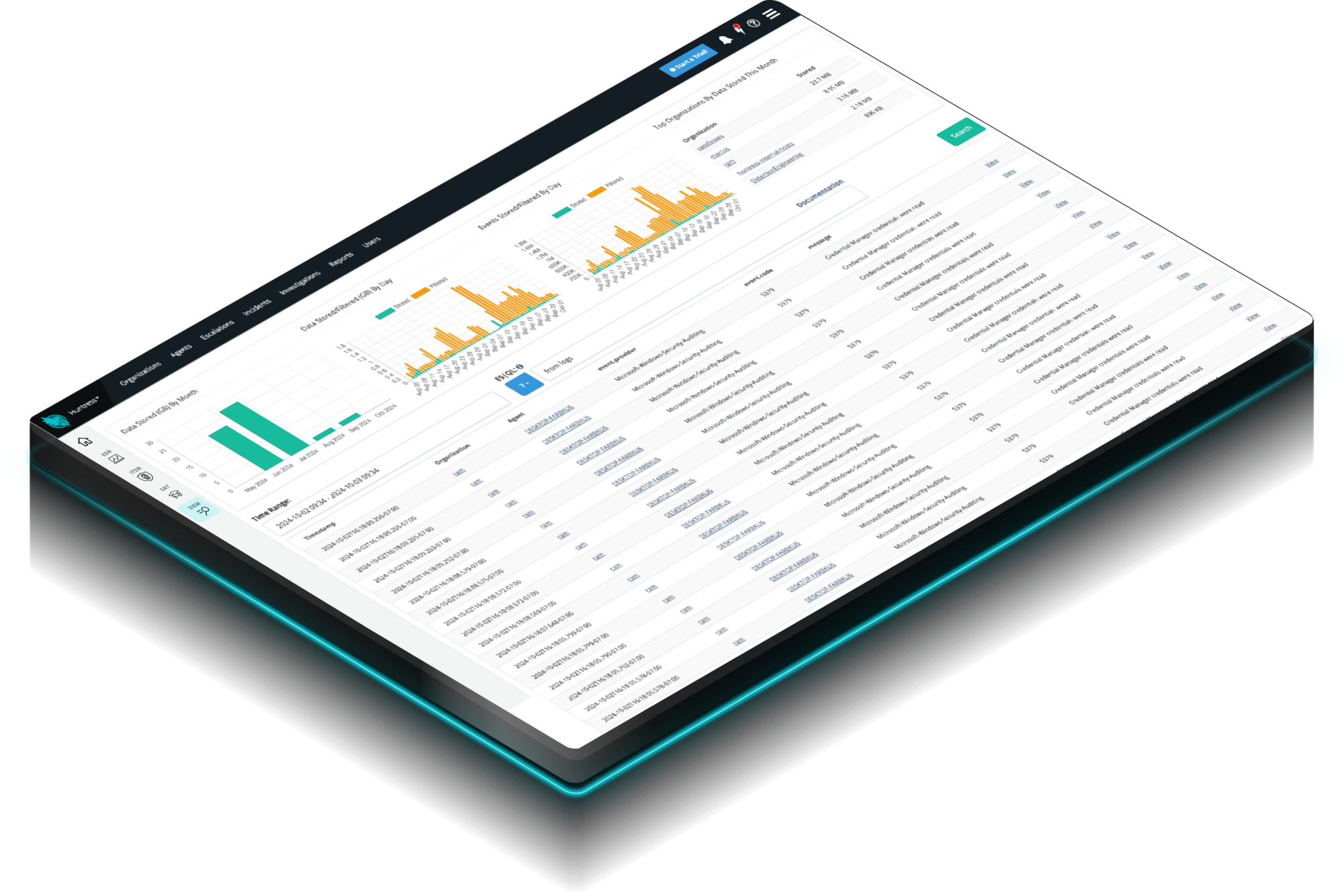
Huntress Managed SIEM takes away the complexity and overhead usually associated with traditional SIEMs, giving you everything you need and nothing you don’t. 24/7 threat response and strengthened compliance, fully managed by SOC experts, at a predictable price.
Engaging, expert-backed, personalized training content built on real-world threat intelligence and created by Emmy® Award-winning animators to reduce human risk and build a strong security culture.
2025 World’s 50 Most Innovative Companies
Top 25 CRN Technology Disrupters
2025 Best SIEM Solution SC Awards Europe






Protecting against ransomware requires a defense-in-depth approach due to the multiple approaches threat actors use to gain access to your systems and data. Endpoint detection and response is no longer the single solution. Businesses need to be educating their employees to detect and avoid phishing and credential theft attacks, and secure password practices. You need visibility into pre-attack activities by threat actors targeting your IT infrastructure, and monitoring for identity and credential theft in the event the “human firewall” is compromised.
A layered defense-in-depth approach means you need EDR to catch attacker behavior on endpoints, identity protection (especially for Microsoft 365) to spot account takeover, and centralized visibility into logs from VPNs, firewalls, and servers to catch “pre‑ransomware” activity. Pair that with security awareness training so users are less likely to get phished, and a tested incident response and backup plan so you can respond and recover quickly if something slips through.
Fast, precise containment is what turns a potential disaster into a contained incident. The faster you isolate compromised endpoints, lock or reset abused accounts, and shut down risky remote access, the fewer systems and data sets are impacted and the less time you spend rebuilding. Good containment is surgical: you keep the business running while cutting off just the attacker’s access.
MFA, conditional access, and backups are critical, but attackers design their campaigns to work around them. They use phishing kits and adversary‑in‑the‑middle techniques to steal both credentials and MFA tokens, exploit weaknesses in VPNs and firewalls, and increasingly focus on stealing data first, then encrypting systems. Backups help you recover, but they don’t prevent downtime, data theft, or reputational damage.
Huntress adds continuous monitoring of endpoints, identities, and logs plus a 24/7 SOC that understands attacker tradecraft. That combination is what turns your existing controls into a real defense against modern ransomware, not just a recovery plan.
Antivirus is based on known file signatures and often fails against modern, fileless attacks. Huntress Managed EDR looks for the tradecraft of the human attacker—how they move, escalate privileges, and execute commands—after they bypass basic defenses. Our human-led, 24/7 SOC is dedicated to threat hunting for these subtle activities, ensuring a response that generic preventative tools simply cannot deliver. We stop the human attacker before they can deploy the automated ransomware payload.
Our SOC finds and helps you actually evict the attacker and shut down their path to encryption, instead of just quarantining a file and hoping the ransomware never runs.
Ransomware canaries are special files Huntress places on your endpoints in locations where normal activity should never touch them.
If ransomware begins encrypting a machine, it almost always hits these canaries first. Huntress monitors them for unexpected modification or encryption. When a canary is tripped, it acts as an early warning signal: our SOC investigates and can move quickly to contain the threat, typically by isolating the affected endpoint.
Canaries give you a last‑line, behavior‑based signal that pairs with other detections to catch ransomware faster, even when the variant is new.
When early ransomware activity is detected, you don’t have hours to spare. With a managed approach like Huntress, suspicious signals are reviewed by our 24/7 SOC and turned into validated, actionable incidents in minutes, not days. The short window from detection to action is what keeps “suspicious behavior” from turning into encrypted endpoints. Unlike solutions that leave you to investigate a flood of alerts, we provide a definitive path to eject the attacker immediately, dramatically reducing the window of opportunity for the ransomware to execute.
Identities are the new perimeter. Ransomware groups will intercept MFA requests, steal session tokens, and ultimately compromise accounts to get access to your systems and data.
Attackers are increasingly stealing passwords and capturing session tokens so they can impersonate real users and admins. Once they hold a key identity, they can move freely, steal data, and deploy ransomware from the inside, which is why identity‑aware detection and rapid response are now critical parts of ransomware defense.
AI is best used to sift through the noise so humans can focus on real threats. It analyzes massive amounts of telemetry, spots patterns that look suspicious, and prioritizes alerts, but human analysts still make the call on what’s truly malicious and how to respond. The winning formula is AI for speed and scale, plus humans for judgment and nuanced response.
If ransomware executes in your environment, Huntress does more than send alerts. Our SOC helps you understand which endpoints and identities appear affected, how the attacker likely got in, and where they may have moved. We then advise on targeted containment—such as isolating specific systems and disabling accounts—and on safe recovery steps, including when to reimage, when to restore from backup, and what to harden before bringing systems back online. We materially reduce uncertainty and time‑to‑action during and after a ransomware event.
Many ransomware and extortion campaigns start with Microsoft 365 account takeover or business email compromise. Managed ITDR connects to your tenant and monitors identities and email for risky behavior: suspicious sign‑ins and locations, malicious inbox and forwarding rules, unusual OAuth app consents, and signs of token theft or session hijacking. When something looks wrong, our SOC investigates and responds quickly by revoking sessions, locking or restricting accounts, and guiding cleanup.
By treating Microsoft 365 identities as a first‑class attack surface, our team helps stop identity‑driven campaigns before they evolve into data theft or ransomware.

In this exclusive online event, you'll see real-world attack demos, get expert tips, and see how attackers structure their teams, manage projects, and innovate at speed.

Our platform combines a suite of powerful managed detection and response tools for endpoints and Microsoft 365 identities, science-backed security awareness training, Managed SIEM, and the expertise of our 24/7 Security Operations Center (SOC).