
Guide
Buyer’s Guide for Security Awareness Training
Training content and simulations learners actually enjoy, managed for you to make administration easy. Unlike the rest, it’s powered by current threat intelligence so you have fewer security incidents.






Purpose-built and Headache-Free
Built with admins in mind to take work off your plate, without sacrificing quality. Onboard in minutes and enjoy a hassle-free experience with always-relevant content, industry-leading completion rates, and learning plans that are curated and managed for you.
Expert-Backed for Real Results
Outdated training doesn’t stop hackers. Huntress security experts build content and simulations based on proprietary threat intel from millions of endpoints and identities under our protection so training reflects today’s threats to effectively reduce human risk.
Impactful Training to Build Resilience
Expansive training libraries aren't helpful if they don’t create change. Huntress Managed SAT follows adult learning frameworks along with hands-on simulations and gamification to make concepts stick. So every learner is engaged, informed, and more resilient to attacks.

Elevated access builds ideal targets for hackers. Learn to limit risk before chaos strikes!

Get to know the Huntress SAT solution: designed, built, and managed by our experts for real outcomes without the headaches.



Built to be headache free and deliver peace of mind. Onboard in minutes with robust integrations and enterprise-grade scale. Best of all, effective training is planned and delivered for you so you can cross one more thing off your list.

Prepare learners for real threats with training built by world-renowned experts in cybersecurity, adult learning, and animation, leveraging threat intel from millions of endpoints and identities.

Approachable and consumable content, immersive Threat Simulations, gamification, & more make every learner an active participant in your company’s cybersecurity.

Address risky behaviors with targeted training from just-in-time Phishing Defense Coaching and behavior-based assignments for those compromised in the wild.

Hackers continually target users with new tactics. Prepare your learners for the threats they’re most likely to see using hands-on experiences for phishing and beyond.

Stay in the know with reporting on everything from compromise rates, assignment completion, and Phishing Recovery Progress, to prove business, insurance, and regulatory compliance.


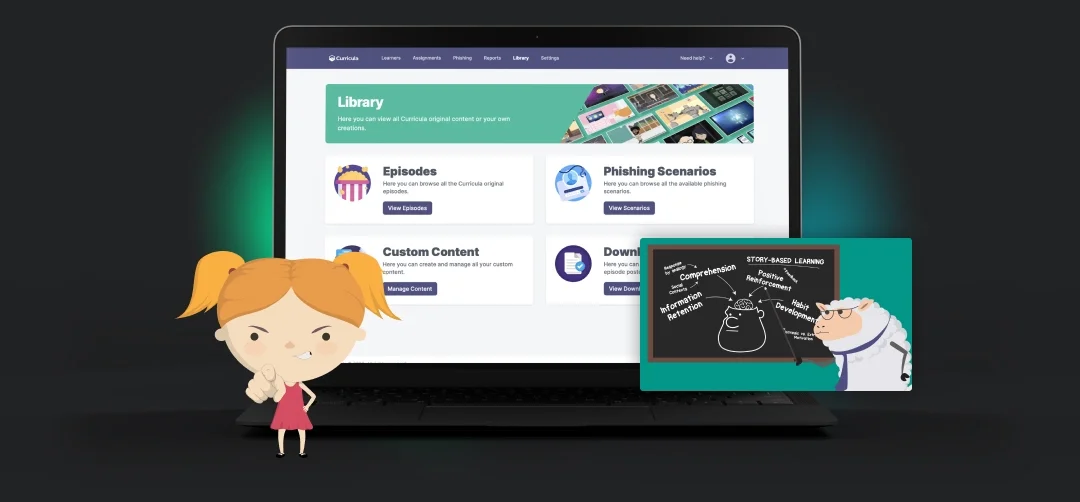
Huntress Security Awareness Training’s (SAT) content authoring software gives you the tools to quickly build and customize online training content.
Huntress Managed Security Awareness Training changes the entire compliance training experience. Everything you need to stay compliant is available in our simple and fun online training software.
Explore the world of Currivulaville. Learn about cybersecurity by taking a journey with characters and stories—all designed to make employees smarter with their cybersecurity decisions.

Follow along for a guided view of onboarding, phishing assignments, custom training, and more.



Read how Huntress Managed SAT delivers “hands-off” training that still results in improved security posture and positive behavioral change.


Managed Security Awareness Training is a solution where the Huntress cybersecurity experts develop, implement, and oversee your organization's comprehensive security awareness training program. This service teaches and empowers your employees about cybersecurity best practices, helps them recognize potential threats like phishing and social engineering, and teaches them how to respond.
Designed for companies of all sizes, our program provides an easy and accessible way to provide cybersecurity training for small businesses. By partnering with Huntress, small businesses can keep their staff informed about the latest cyber threats without the burden of creating and maintaining the program internally, all with scalable pricing.
Huntress Managed Security Awareness Training primarily includes engaging, story-driven cybersecurity episodes and phishing simulations based on real world threats. Our team manages the creation, curation, and scheduling of all learning programs, and automatically sends manager reminders and monthly reports. The program also includes personalized phishing simulation recovery training, Phishing Defense Coaching, gamification, a Custom Content Creator Tool for tailored training modules, comprehensive compliance support, easy onboarding, detailed reporting, and robust integrations to ensure your employees are well-equipped to recognize and respond to cyber threats.
Most episodes are roughly 7 to 10 minutes in length. When considering aspects like employee participation, they can sometimes last up to 30 minutes for each episode.



What businesses of all sizes are saying about Huntress Managed Security Awareness Training








Don’t just check a compliance box. Elevate your workplace’s security culture while giving your employees an enjoyable experience.
