Quick comparison: Top phishing protection solution
Provider | Best for | Key features | Pricing |
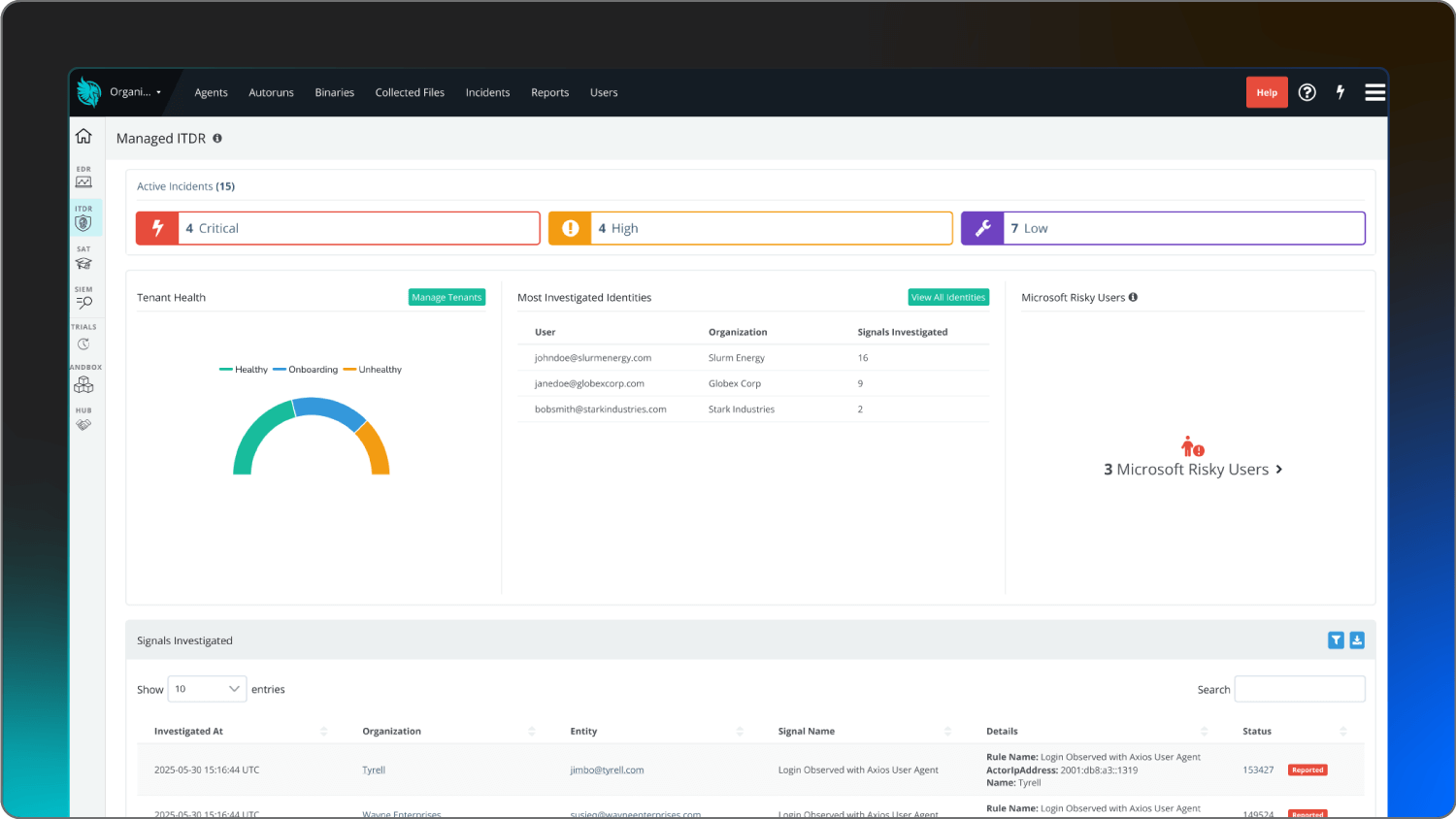
Huntress Security Platform | Total managed protection without the enterprise pricetag | 24/7 human-led, AI-assisted SOC monitoring, managed ITDR and security awareness training | |
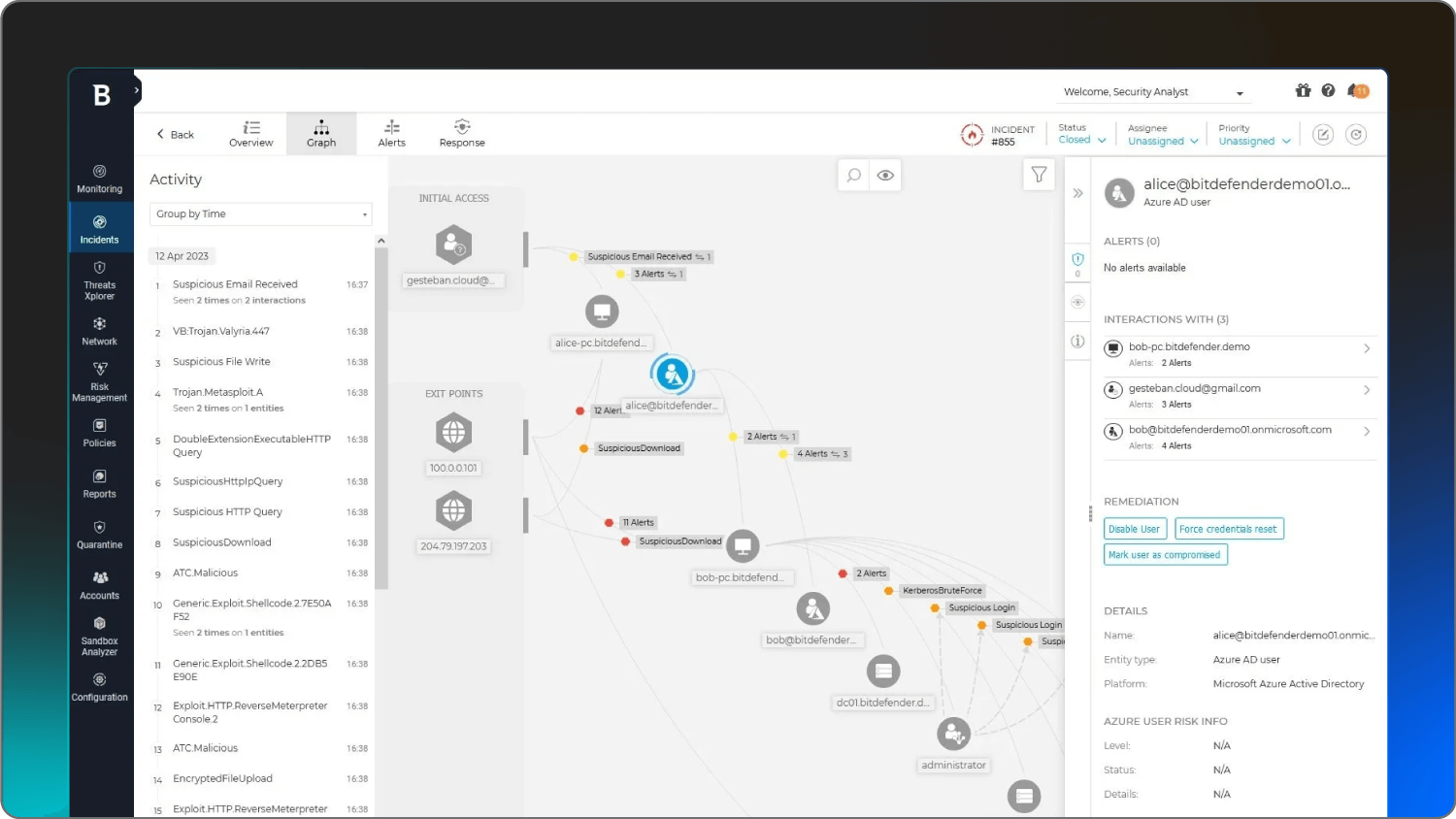
Bitdefender | Small office devices | AI-powered Scam Copilot | Starting at $324.99/year for 1 device |
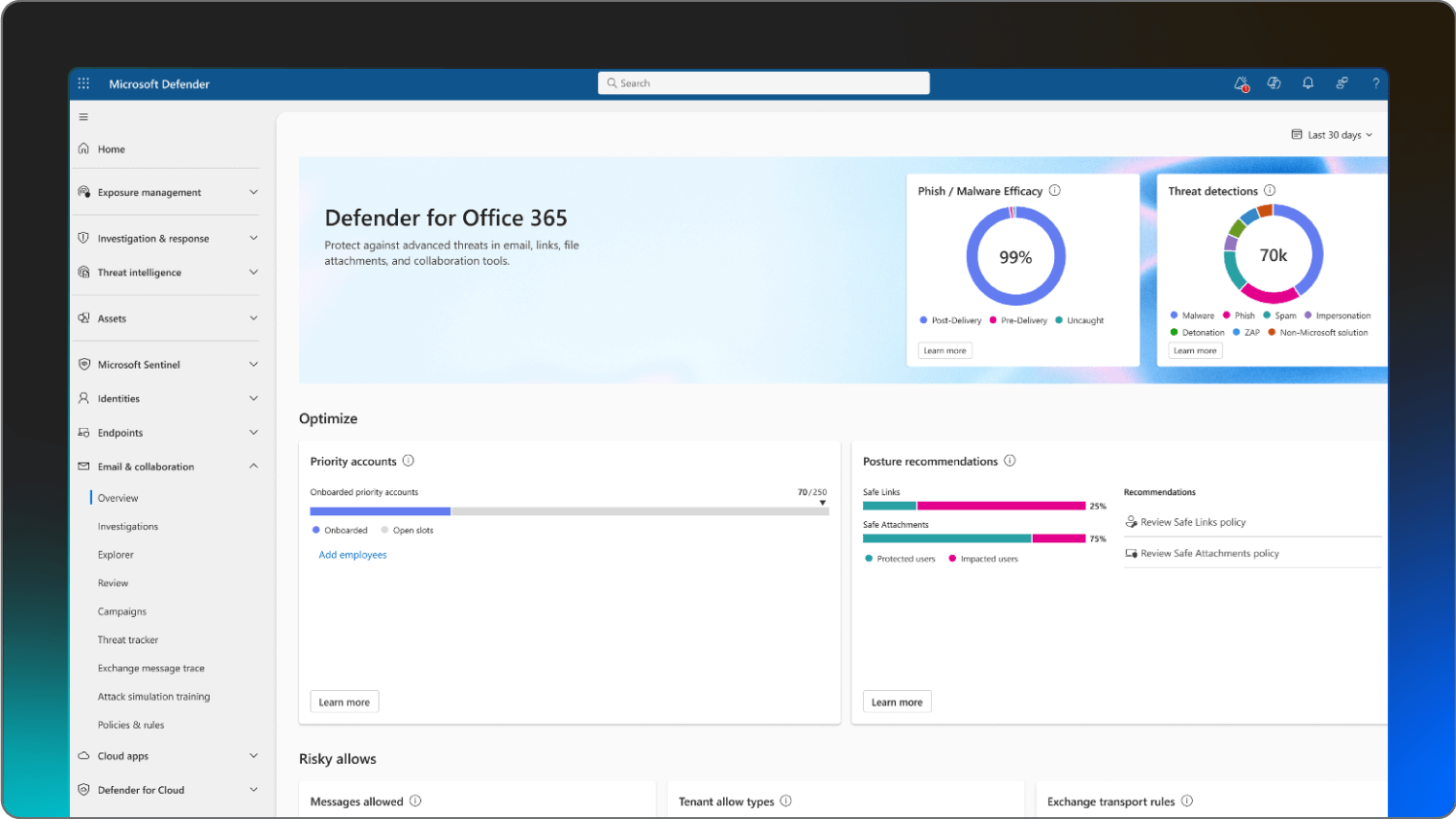
Microsoft Defender for Office 365 | Native Microsoft 365 users | Anti-phishing for Teams and email | Starting at $2.00 per user/month, paid yearly |
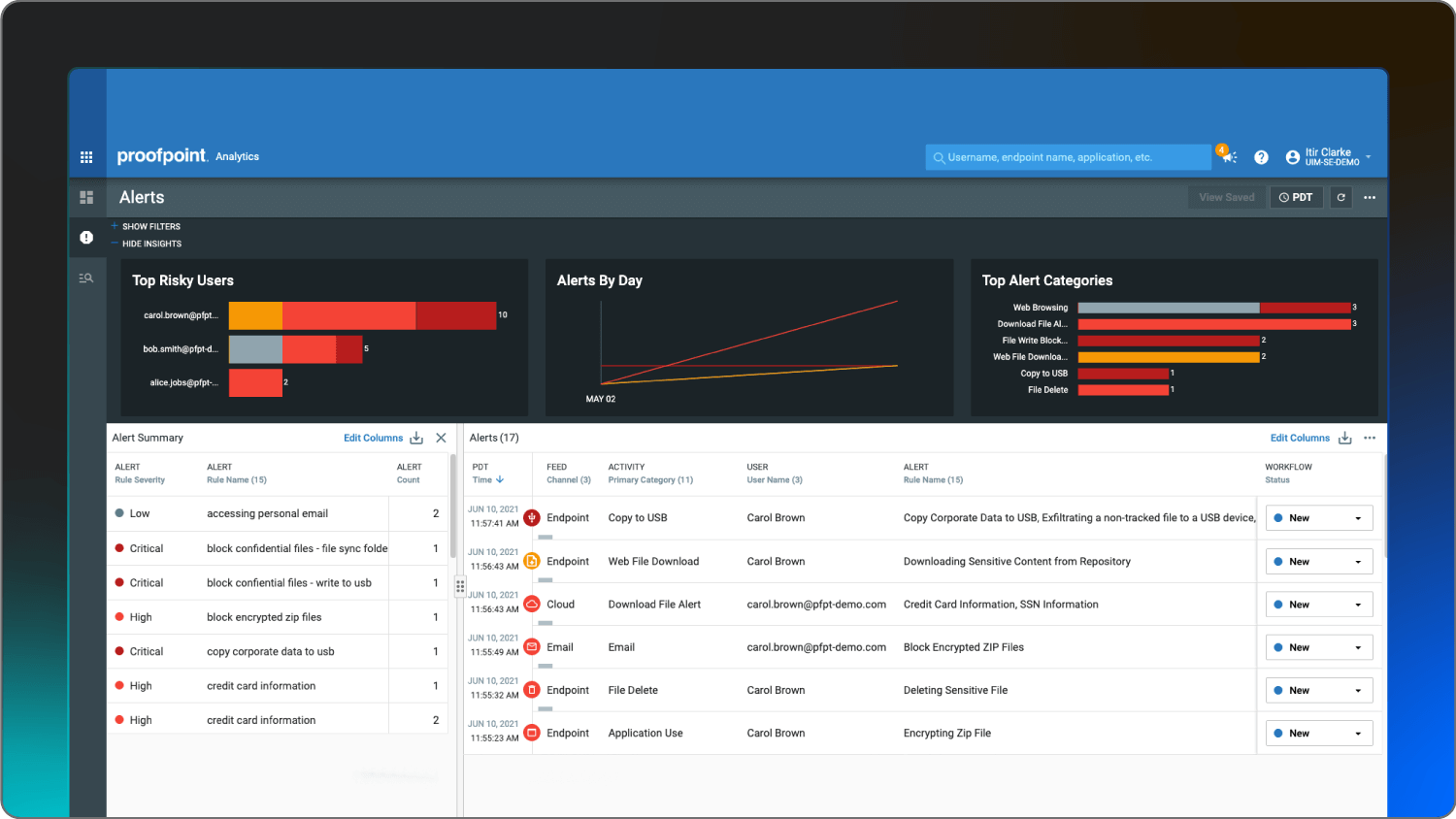
Proofpoint | Large-scale enterprises | URL isolation for VAPs | Contact Proofpoint |
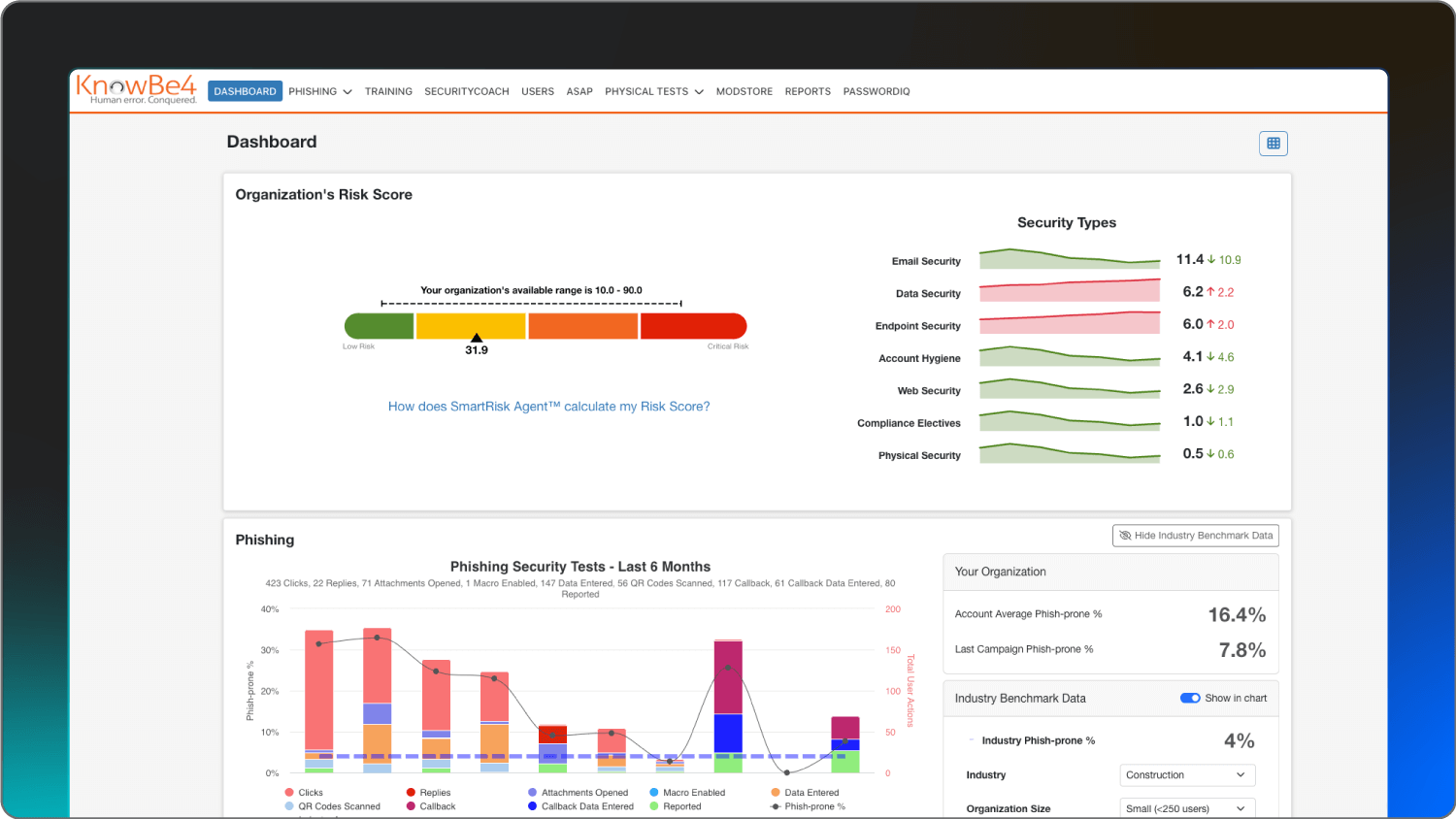
KnowBe4 | Human risk training | Unlimited simulated phishing tests | Starting at $1.90 per seat/month (3-year term, 25-seat minimum) |
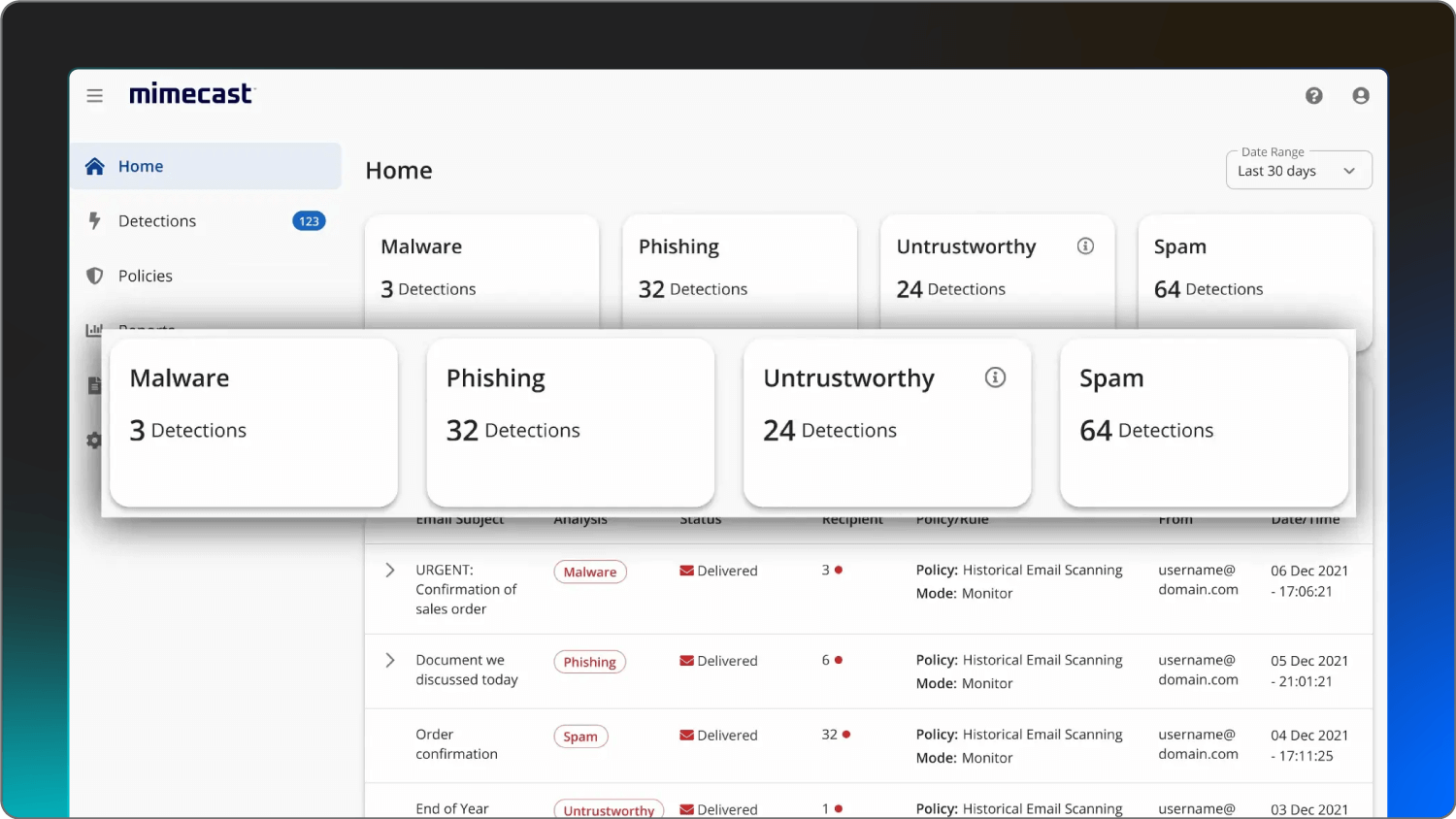
Mimecast | Collaboration security | AI-powered social engineering defense | Contact Mimecast |
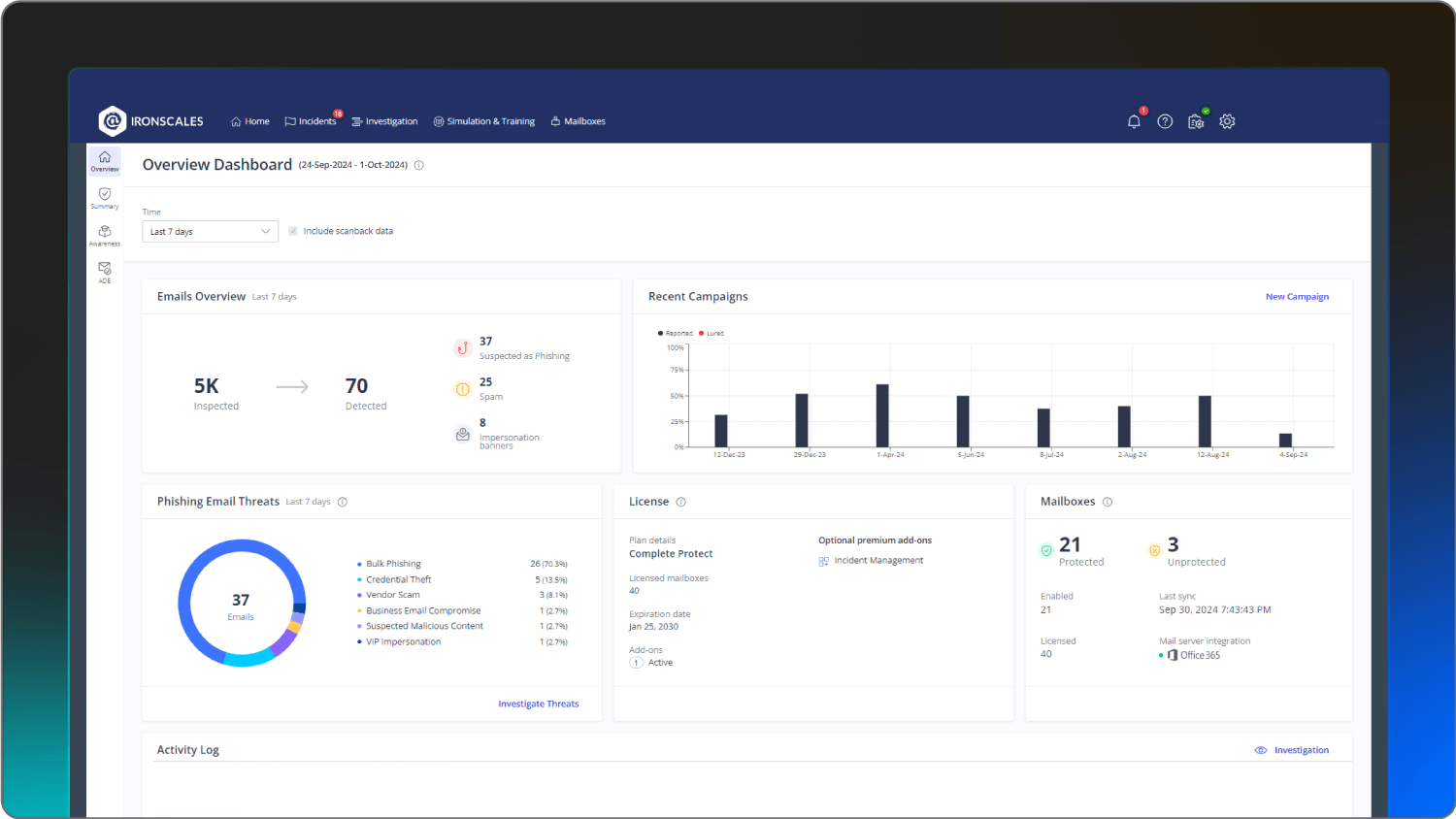
Ironscales | Lean IT teams | Agentic AI autonomous threat remediation | Contact Ironscales |
OpenText | Budget-conscious protection | Real-time phishing shield | Starting at $150/year for five seats |











![A screenshot of the Webroot platform.]](https://cdn.builder.io/api/v1/image/assets%2F3eb6f92aedf74f109c7b4b0897ec39a8%2Fab56379c2df5487e8345fc6724a70f82)


