Cloudflare Turnstile challenges leading to MetaStealer. Deepfake meetings impersonating company executives, which trick employees into downloading malicious extensions. Exposed ASP.NET machine keys that open the door for ViewState deserialization attacks against company servers.
These are only a few snapshots of the techniques that threat actors have been relying on in 2025 so far. In our most recent Tradecraft Tuesday episode – The Craftiest Trends, Scams, and Tradecraft of 2025 (So Far) – John Hammond and Greg Linares with Huntress dove into the top types of tricky tradecraft that threat actors are using to target businesses.
ClickFix: The attack we’ve seen everywhere
ClickFix has been around since last year. But in 2025, attackers continued to put new spins on the crafty social engineering attack.
This simple technique literally weaponizes “copy and paste.” It involves attackers tricking users to “fix” a purported issue. They typically send victims a phishing message, which leads them to a supposedly broken CAPTCHA on a webpage. The “solution” to fixing the broken CAPTCHA is copying and pasting a command into the Run dialog box, which is given to victims via an attacker-controlled prompt. This triggers the attack chain.
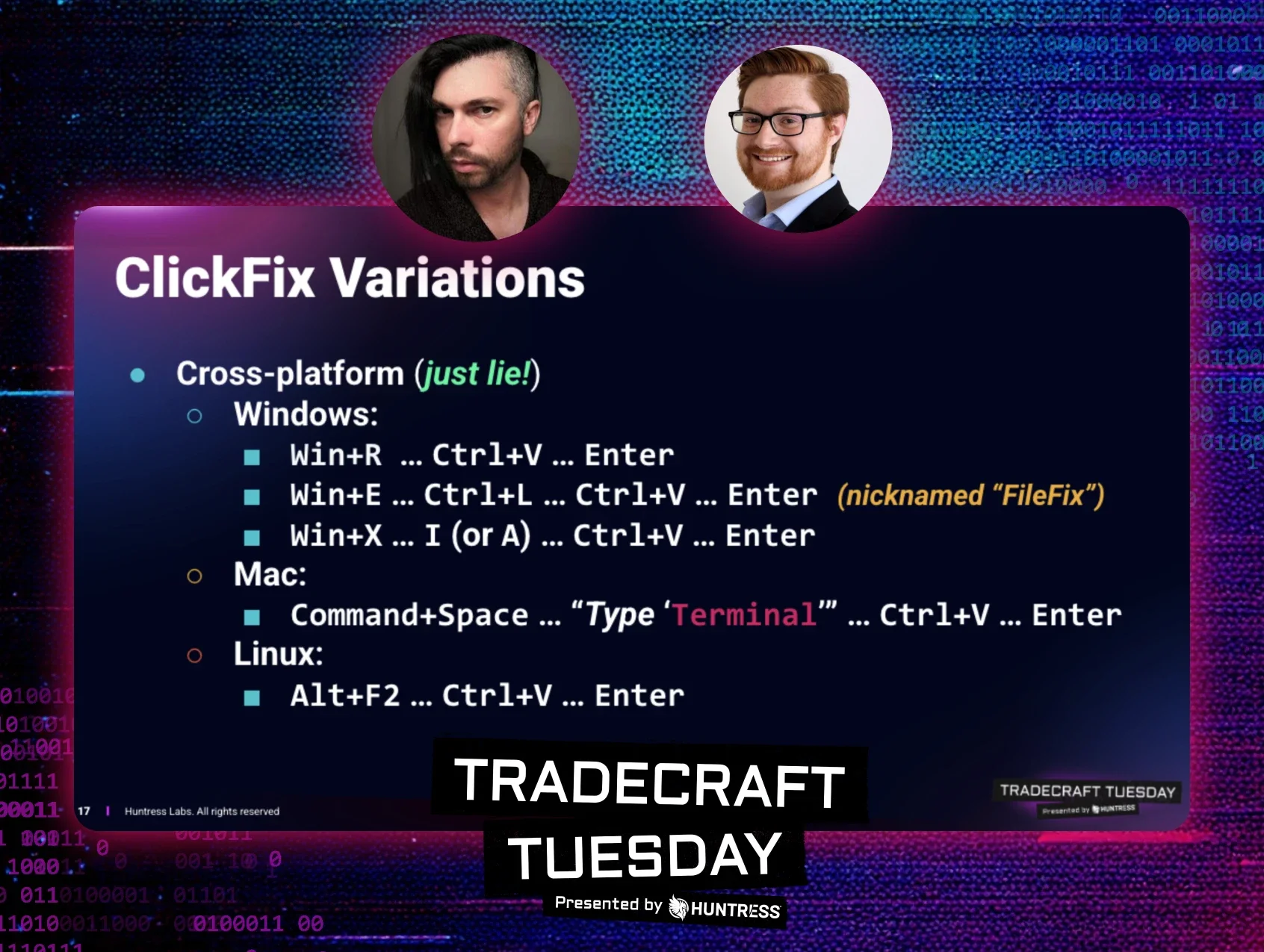
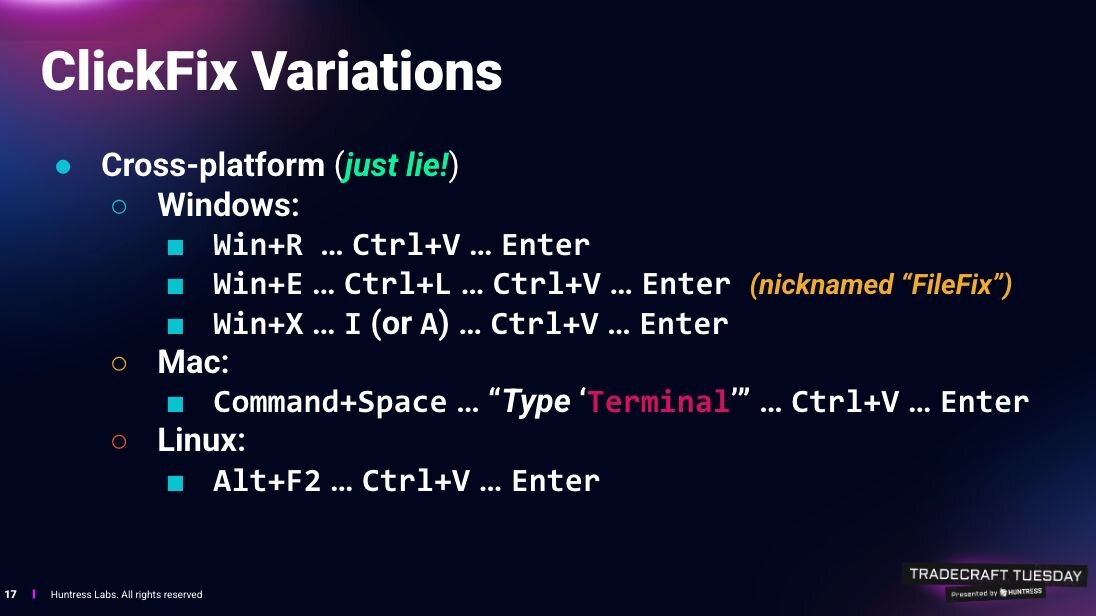
Seems simple enough, but since the original concept of ClickFix was uncovered in 2024–being used in LummaStealer infostealer attacks–threat actors have found a surprising amount of success in the technique. As seen in Figure 1, we’ve seen cross-platform ClickFix variations, including ones targeting Mac (Command+Space → “Type ‘Terminal’” → Ctrl+V → Enter) and Linux systems (Alt+F2 → Ctrl+V → Enter).
Adversaries are also putting new twists on the known ClickFix playbook. For instance, a few months ago threat actors started using FileFix, a ClickFix offshoot that involves Windows File Explorer instead of the Run dialog box.
Most recently, we spotted an attack with ClickFix-like aspects. This shows that attackers are capitalizing on their apparently successful blend of social engineering with mundane processes, like CAPTCHAs or other verification tools.
The attack started with a fake AnyDesk installer while searching for the AnyDesk remote tool. While early indicators of the attack looked like it would turn into another ClickFix scam, a little bit of digging revealed a unique infection chain that involved a fake Cloudflare Turnstile lure, the Windows search protocol handler, and an MSI package disguised as a PDF that sneakily grabbed the victim’s hostname. The attack ultimately aimed to drop MetaStealer, a commodity infostealer that’s been around since 2022 and is known for harvesting credentials and stealing files.
In anticipation of more ClickFix attack variants in the future, John Hammond has been building a resource called ClickFix Wiki that shows the variety of tools that can be used and abused in ClickFix attacks, the lures that might trick individuals, and the subsequent mitigations.
Companies that want to mitigate against ClickFix attacks can take the following steps:
-
Disable the Win+R Run dialog box, and restart Explorer
-
Disable the Win+X Power Menu
-
Disable hotkeys and disable copy to clipboard
Deepfakes coming in hot
2025 is the year of the deepfake. Threat actors have incorporated AI-enabled voice and video deepfakes into attacks to up the ante for phishing, initial access, financial fraud, social media disinformation, and more.
Perhaps the closest visibility into a deepfake attack we got this year was during a North Korean intrusion on a Web3 organization. Here, the threat actors tricked an employee at the company by inviting them to a Zoom meeting with video deepfakes of known senior leadership. These deepfakes convinced the employee to download a “Zoom extension,” which kicked off the attack. This is a great example of how threat actors are using deepfakes as a social engineering mechanism to push their agenda.
This incident is one of many deepfakes that have happened this past year; in fact, 2025 is projected to have a 35 percent increase in reported deepfake incidents over 2024.
Deepfakes are also creating financial headaches for businesses, as the world saw after London-based company Arup in 2024 revealed it was the victim of one such scam. That attack involved one of the firm’s Hong Kong employees paying out $25 million to fraudsters after joining a call where attackers used fake voices and images to convince him to make the transaction.
Attackers have also been using deepfakes in elaborate scams. In these scams, they pretend to be legitimate IT workers during job interviews. After securing a role, the workers infiltrate organizations to steal sensitive data.
Today’s deepfake technology has also advanced to the point where it’s increasingly difficult to detect. Previously, users could spot certain red flags about deepfakes, such as out-of-sync audio or strange visuals when the deepfakes move their hand in front of their face. However, these have improved with the latest live deepfakes.
So, how do we counter deepfakes? Because they are advancing so quickly, trying to detect them is a losing battle. Organizations should assume all of their employees have been cloned into deepfakes and create a response plan accordingly. This might include incorporating some level of physical validation or maybe implementing hard restrictions on resetting accounts.
(Continued) ViewState exploitation
ViewState exploitation is by no means new, but in 2025, we’ve seen several attacks in this area.
To understand ViewState, you need to first understand ASP.NET, which is a server-side web app framework that was made by Microsoft for building web pages, applications, and service. ViewState enables ASP.NET pages and websites to communicate in a secure manner.
If threat actors are able to target an ASP.NET Windows-hosted server using ViewState to handle a session, they can decode and intercept content that they normally don’t have access to. In order to do so, threat actors must first access cryptographic keys used to secure ViewState data from unauthorized disclosure. These are called machine keys, and they include a validation key and a decryption key, which together ensure the ViewState session’s integrity and confidentiality.
In a best-case scenario, these machine keys are protected at the system level. However, if they’re not properly protected, they can be stolen, leaked, or inadvertently made publicly accessible.
In fact, Microsoft this year said that it has identified over 3,000 publicly disclosed keys that could be used for ViewState code injection attacks. Previous ViewState code injection attacks have used compromised keys that were typically sold on dark web forums–but these publicly disclosed keys are more dangerous because they may have been pushed into development code without modification. That means if servers are using these known keys, attackers can just point and shoot.
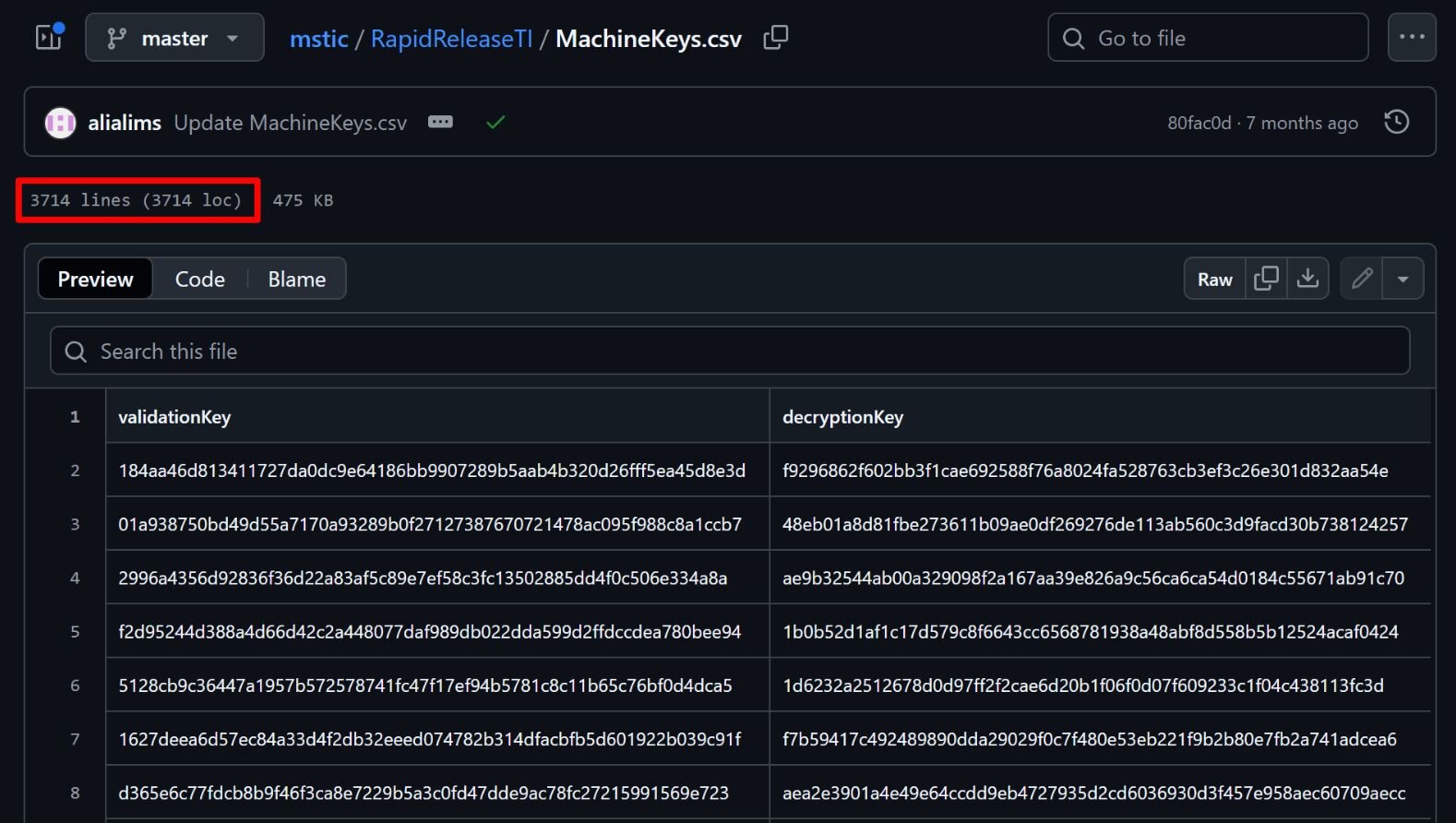
ViewState exploitation can result in all kinds of security incidents. In April, threat actors targeted ViewState while exploiting critical flaws in the Gladinet CentreStack and Triofox flaw (CVE-2025-30406). This attack stemmed from the fact that machine keys were hardcoded in the CentreStack portal, allowing threat actors to track them down in the web.config file. They could then deserialize data from a ViewState intrusion and execute arbitrary code.
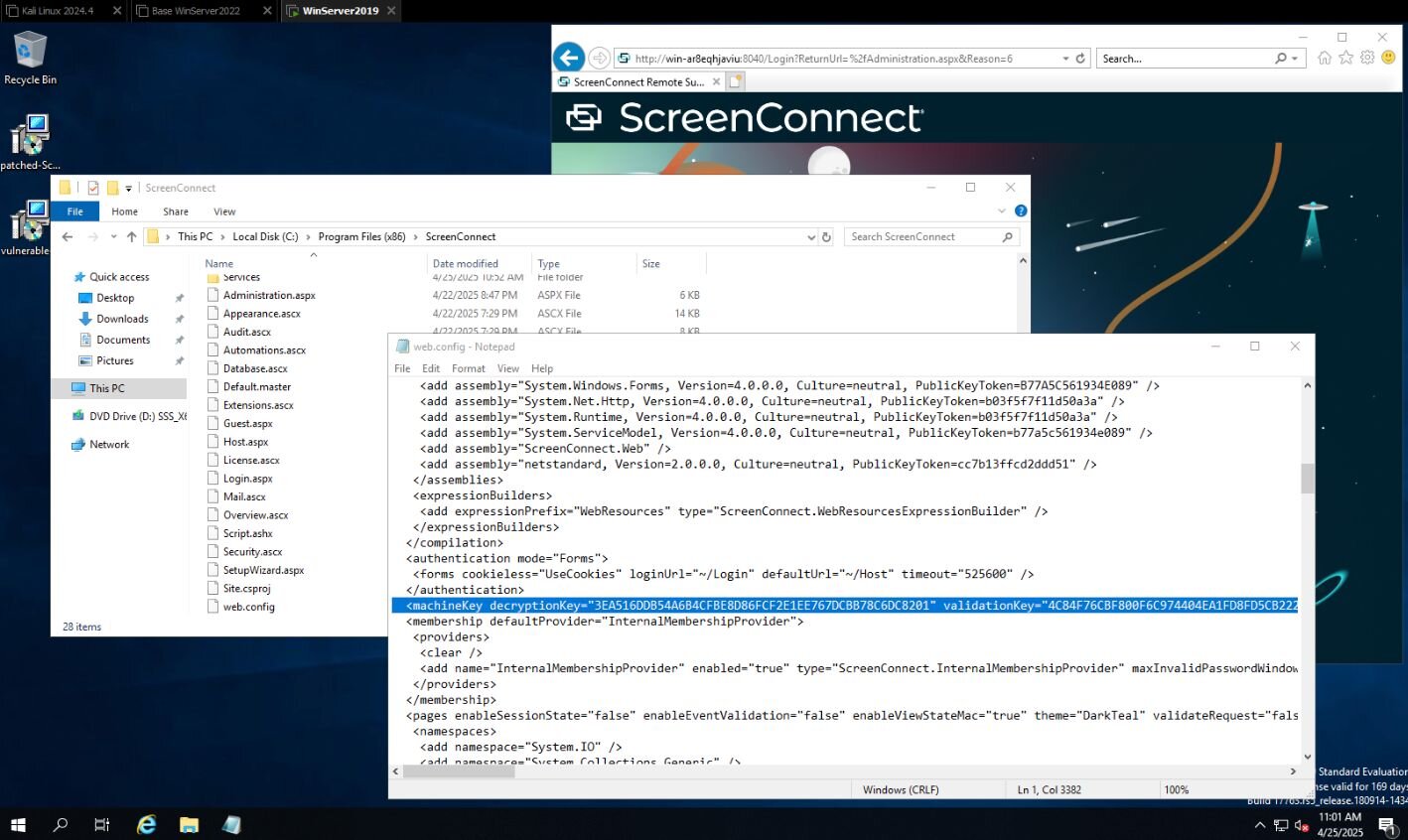
More recently, in September, Mandiant researchers revealed a ViewState deserialization zero day attack (CVE-2025-53690) that was impacting Sitecore deployments. The attack used a sample machine key that had been exposed in Sitecore deployment guides from 2017 and earlier.
More cyber threat trends to come in 2025
When you look at the top cyber threat trends of 2025 so far highlighted above, nothing stands out as completely novel. Threat actors are changing up the playbook with ClickFix, making use of advancing deepfake technologies, and targeting ViewState weaknesses where they can.
All these techniques have been around for varying amounts of time; however, if there’s one thing that we know about threat actors, it’s that if something works, they’ll continue to use those same TTPs, sometimes with their own flair.
Like what you just read? Join us every month for Tradecraft Tuesday, our live webinar where we expose hacker techniques and talk nerdy with live demos. Next month, our Tradecraft Tuesday episode, "The Dangers You Don’t See: Threats Hiding in Your Network,” will tackle the top threats that our SOC is seeing so far in the trenches this year. Snag your spot now!