Hackers aren’t always this obvious. Huntress is built for threats you can’t see.
#ShadyHacks



Your business is exposed to hacks you’d never see.
Some are clear scams, but hacks are hidden in ways you don’t even know about.
Huntress helps businesses of all sizes stay protected with the tools and the team that handle the obvious #ShadyHacks and more.

Top Threats Your Business Should Watch For


THE HACK: Ransomware Attack
When a hacker drops ransomware in your environment, they do it through clever tactics or just by relying on human error, like clicking on a fishy link. Hackers also use AI to craft smarter attacks that can adapt to stay hidden, and their goal is to steal information, mess up your business operations, or demand money to get your data back.

HOW YOU STOP IT
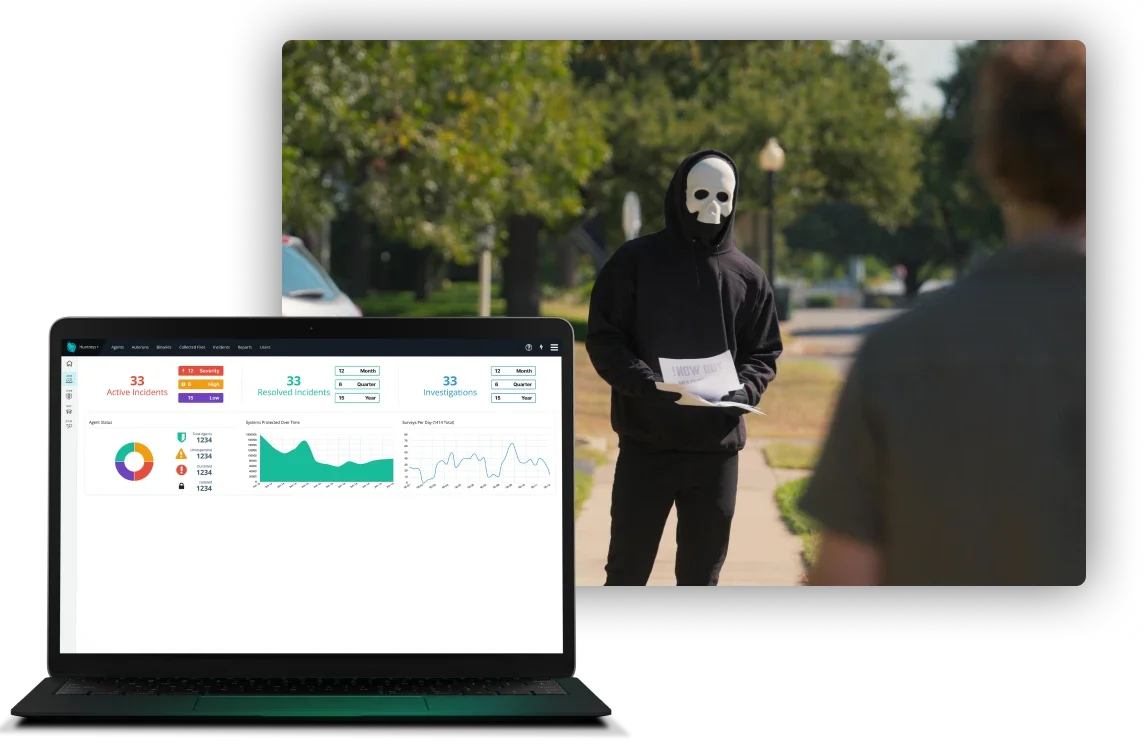
Huntress Managed EDR
EDR, or Endpoint Detection and Response, monitors and responds to threats on your business’s endpoints—think laptops, desktops, and servers—by proactively collecting and analyzing your endpoint data. Huntress Managed EDR is your unfair advantage against malware attacks and more, protecting your business from cybercriminals 24/7.

TRADECRAFT
Exposed RDP
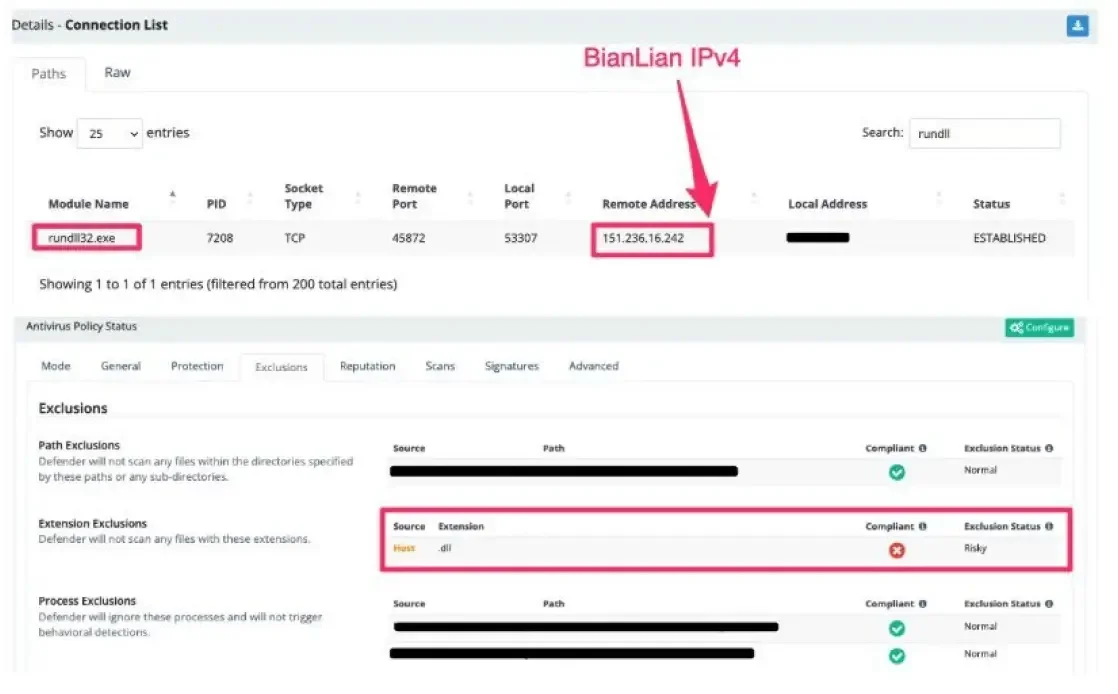
Exposed RDP can lead to anything—even attempted ransomware attacks, like at this manufacturing business👇
- A suspected ransomware group thwarted Windows Defender using registry modifications to exclude *.DLL
- With Windows Defender on the fritz, they dropped a malicious GoLang DLL payload: rundll32.exe C:\\ProgramData\\HP\\Installer\\Temp\filter.dll,Entry
- The payload and IPv4 are possible BianLian activity, a ransomware group known for raking in payments with data exfiltration and extortion over encryption.
Fortunately, the Huntress SOC sent them packing before serious damage was done.


THE HACK: Business Email Compromise
Business email compromise (BEC) threats infiltrate the inboxes of organizations across all industries. According to the FBI's Internet Crime Complaint Center (IC3), BEC was the second-most expensive cybercrime in 2024, accounting for nearly $2.8 billion in total reported losses.


HOW YOU STOP IT
Huntress Managed ITDR
ITDR, or Identity Threat Detection and Response, continuously monitors identity-related activities in your environment to spot potential threats. Huntress Managed ITDR protects your users 24/7 from identity-based attacks like email business compromise, credential theft, and more. Most incidents involve identity threats, so your business needs protection against these risks.

TRADECRAFT
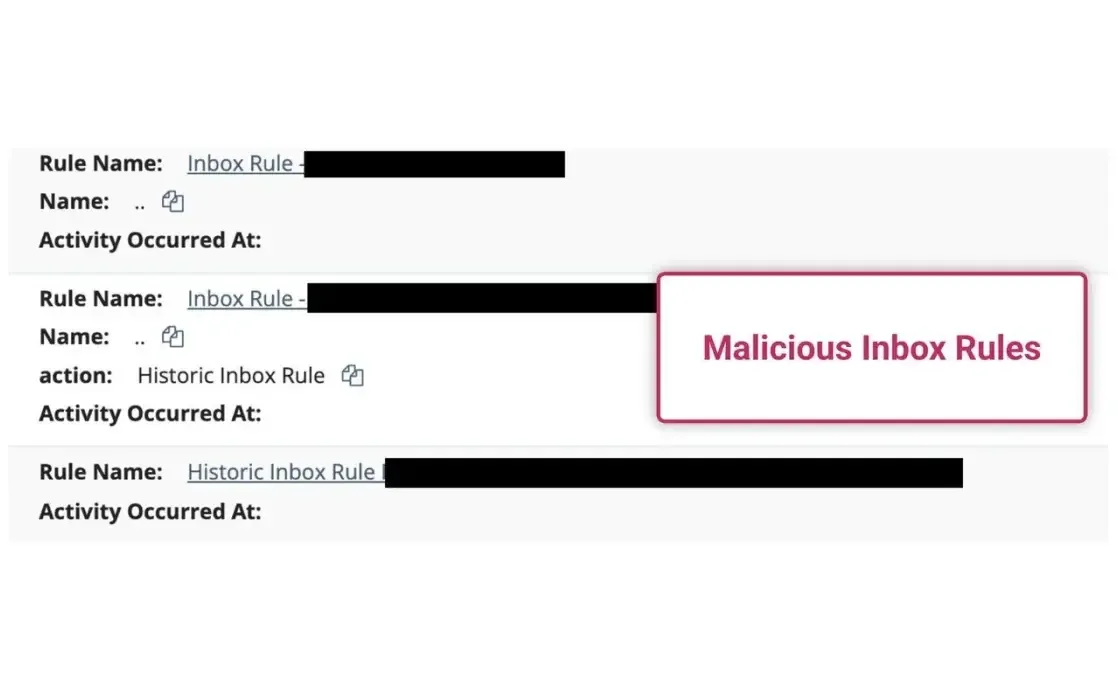
Malicious Inbox Behavior
Business Email Compromise costs enterprises $2.9 billion every year.
How hackers do it:
- Shady logins: Attackers use sketchy user agents to mimic legitimate browsers or email clients.
- Malicious inbox rules: Hackers hide warning emails or auto-forward your sensitive info.
- Unknown VPNs: Logins from untrusted VPNs are a dead giveaway someone’s sidestepping your network controls.
- Malicious infrastructure: When IP addresses link back to known attacker hubs, we move fast.
Hackers know your people are the easiest way in. Huntress Managed ITDR keeps threats out of inboxes and money in bank accounts.


THE HACK: Digital Account Theft
Identity-based attacks involve stealing credentials so hackers can become you to take what they want from your business: your passwords, your credentials, and customer financial and billing info. Hackers don’t even need to break in if they can just log in, camp out in your environment, and steal everything over time before your team ever notices.

HOW YOU STOP IT
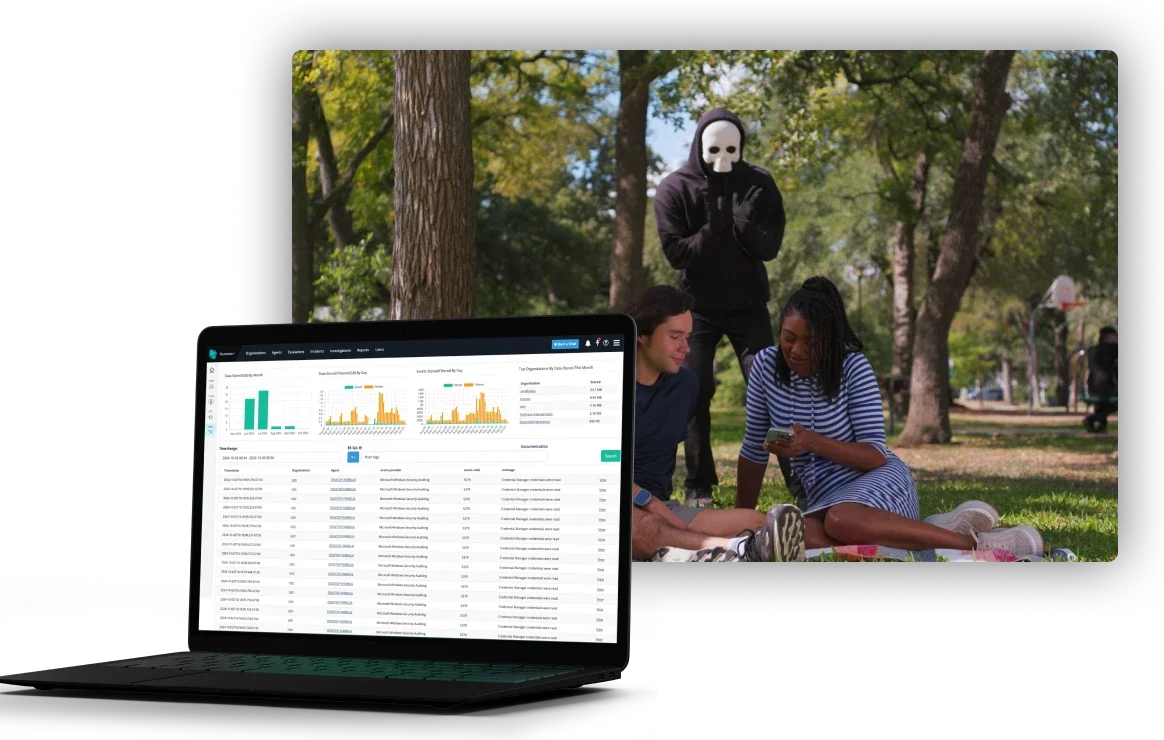
Huntress Managed SIEM
SIEM, or Security Information and Event Management, collects and analyzes data from across your network to spot and manage threats with real-time visibility. It works with EDR and ITDR solutions, correlating data and spotting compromised infrastructure access to alert you on potential endpoint and identity threats. Huntress Managed SIEM gives your business quick, relevant alerts to stay safe and compliant.

TRADECRAFT
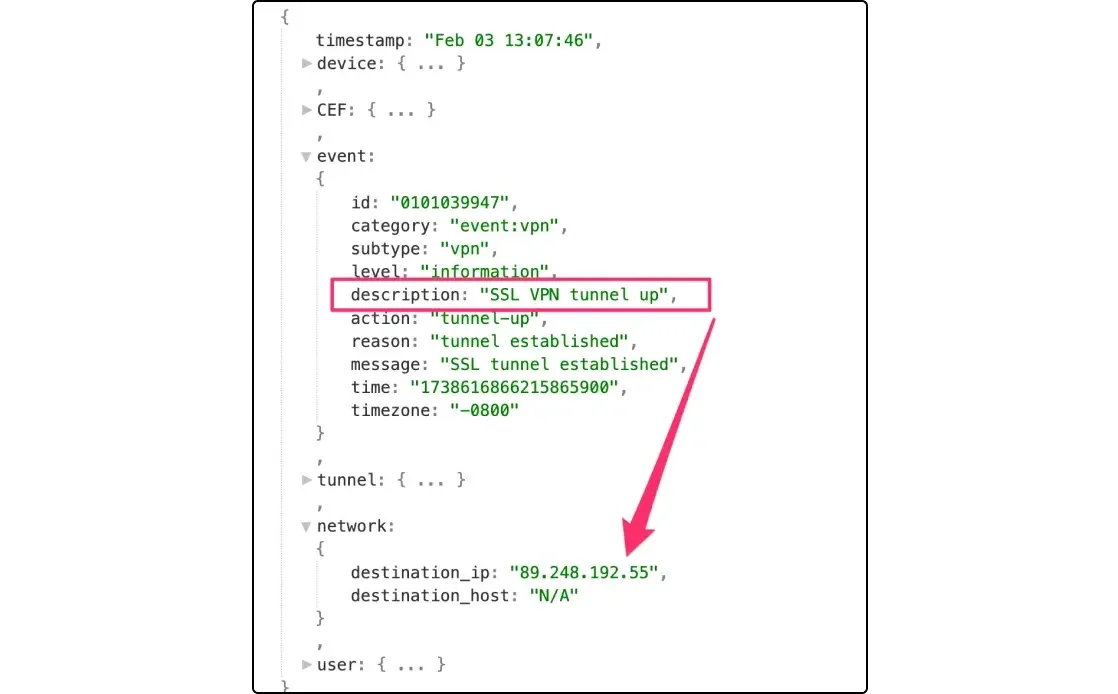
VPN Compromise
A threat actor:
- Broke into the Fortigate VPN as a legitimate account, from the malicious public IPv4 89.248.192[.]55
- Created a user for persistence on the Fortigate device
- Tried to steal credentials via Registry dumping and browser stored credentials, but was frustrated by Huntress Managed AV
With Huntress SIEM, the SOC moved with lethal haste, filtering through Fortigate logs, isolating the network, and pinpointing the root cause of the intrusion. Keep your external perimeter hostile, and threat actors don't stand a chance.


THE HACK: Phishing Scam
Phishing is where hackers pretend to be a legit company or trusted person in an email or SMS message, so you’ll give up sensitive data like passwords or financial info. Employees are susceptible to this, and they need regular training on how to spot modern phishing scams so they don’t put your business at risk.

HOW YOU STOP IT
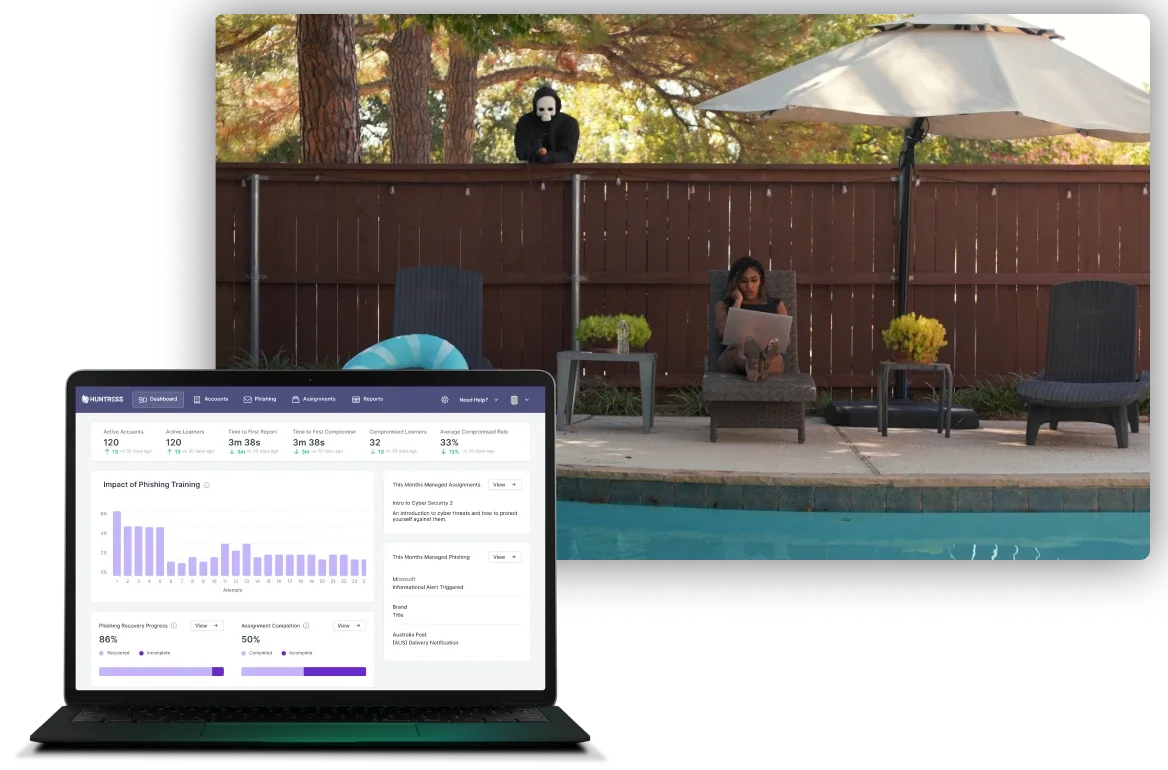
Huntress Security Awareness Training (SAT)
SAT, or Security Awareness Training, teaches employees how to identify and mitigate potential threats in your digital environment. Huntress Managed SAT is just-in-time training designed by experts in human risk management to get your users to think like hackers, so they can spot even the most clever online schemes and stop them before they wreck your business.

TRADECRAFT
Slippery Phish
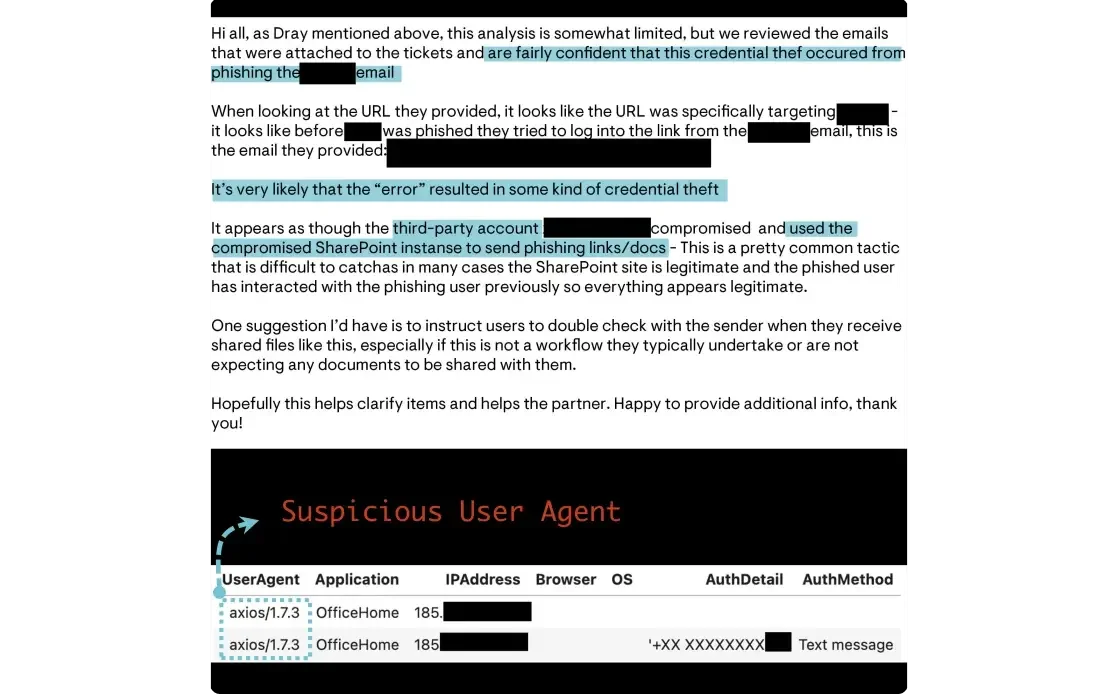
The Huntress SOC was alerted to a suspicious Microsoft 365 login at an accounting firm.
- The threat actor registered a new MFA device for the victim user to establish persistence.
- Upon reviewing additional telemetry, the source of the intrusion was identified, but this phishing email came from a trusted party using an existing email thread.
- A third-party Microsoft 365 account was compromised and used to stage phishing payloads on the compromised SharePoint service.
This tactic is clever, but does not get by Huntress analysts, who identified the source of phish, notified both parties, and restored account functionality.


See It All Come Together
You’ve learned more about our solutions, but nothing really compares to witnessing the Huntress Platform in action. We’ll customize a demo around your specific business needs, and you’ll see how we spot and wreck hackers to keep you safe from cyber threats.

Meet the Humans Protecting You
The 24/7 Huntress Security Operations Center (SOC) and team of threat hunters protect companies like yours, day in and day out. These are real human cybersecurity experts recognized by their peers as industry leaders—think of them as the “always-on” cyber badasses by your side, dedicated to keeping your business safe.

See Huntress in Action
You’ve learned more about our solutions, but nothing compares to seeing the Huntress Platform in action. We’ll customize a demo around your specific business needs so you can watch how we spot and wreck hackers.
Solutions Built for Real-World Threats
Our team gets inside the mind of a hacker to anticipate their next move and shut them down before they can hurt your business. From enterprises to the MSPs supporting them, organizations of ALL sizes trust us to stay ahead of what's coming.