A recent blog post that we wrote sparked some conversation in the infosec community about how endpoint detection and response (EDR) products work, how investigations play out, and why forensic data, like browser history artifacts, is valuable to an investigation.
Today, we want to pull that thread a bit further, because it’s a very important and valid conversation. Most importantly, we want to show you exactly what it means to go toe-to-toe with hackers–and why you shouldn’t settle for anything less in 2025.
The role of telemetry data in managed versus unmanaged EDR
Managed EDR provides businesses with an EDR service so that they don’t need to use their own in-house resources. Unmanaged EDR (or self-managed) solutions leave organizations responsible for purchasing, implementing, and managing the solution entirely on their own, including handling all alerts. While this approach offers control and flexibility, it can be resource-intensive and challenging for companies lacking the necessary personnel or expertise.
Telemetry data is at the very heart of an EDR solution, both managed and unmanaged. The processes and files running on an endpoint can give important clues about potentially malicious activity. However, managed EDR helps businesses derive meaning from that telemetry through a dedicated security team.
Huntress takes that to the next level. We offer a unified security platform for endpoints and identities, and managed EDR is a key component of our offering: our solution combines proprietary technology with a 24/7 SOC team to deliver comprehensive EDR capabilities. However, our SOC team’s creativity and aptitude sets us apart from the pack. Here’s how:
-
Our SOC doesn’t just stop at detection and response. They spend every single day looking at persistent footholds, poring over forensic evidence, and gathering contextual information for each unique incident, all to help our customers better understand and get ahead of the threats facing their environments.
-
SOC analysts step up the game with proactive threat hunting, combing through telemetry data to uncover previously undetected malware, compromises, or threats that may have evaded traditional detection methods.
-
We go head-to-head against hackers through our comprehensive investigations, and provide value to the broader community by sharing our findings from our analyses.

These investigations aren’t only valuable to your business. They’re an absolute necessity to keep up with the reality of incidents in 2025. Attackers aren’t relying on one clear-cut attacker playbook that can be readily detected every single time. Many threats are indistinguishable from regular, run-of-the-mill processes on a company’s system and can only be discernible through a human investigation. Sometimes there are other external forces at play too: for instance, alerts may be tripped by pentesting or red teams engaging in scheduled assessments of our customers.
What leads up to an investigation?
An investigation may kick off in a number of different ways. Many times, investigations are launched after a signal comes through, alerting that something potentially suspicious is happening on the endpoint. Maybe our detection rules trigger an alert for a living-off-the-land binary (LOLBin) after certutil downloads a file on a company’s machine. This event is not inherently malicious by itself–certutil is a legitimate Certificate Services command line tool–however, threat actors also abuse it to download files. To figure out what’s really going on here, SOC analysts need more information, like browser history, which can be helpful in determining if a file was downloaded intentionally or not, and where it came from. Then, if the team determines an alert is malicious, they can take the appropriate steps to protect the organization, like containing the threat.
Other times, investigations roll out from a threat hunting initiative. These operations rely on telemetry based on process behavior insights and persistent footholds gathered from the Huntress EDR to find intrusions that have slipped by normal security defenses. This type of hunting methodology has powered some of our deeper-dive investigations, including one that discovered a 2024 intrusion by an APT targeting Vietnamese human rights defenders. You can learn more about the unique value of threat hunting–and how it tips the scales in defenders’ favor–in our video below.
As seen in both cases above, analysts need to study various forensics artifacts on the company’s endpoints–like the target endpoint’s Windows event logs, installed files, and browser history–to help figure out more information about a threat’s severity, scale, and scope. Like other managed EDR providers, every request that we pull from customer endpoints is cataloged and logged with information about the analysts who made the request, what data was requested, and the date and time. This helps us internally identify who is working on investigations, what aspect of the incident is being handled, and helps us prevent double tasking data requests from the endpoints.
The ultimate goal here is to help the impacted business–or in some cases, multiple businesses–figure out the answer to the following questions.
How did an attack happen?
By conducting investigations, our SOC team can figure out how an attack happened. Maybe malware on a victim organization came from a random drive-by download, or maybe it came from a targeted phishing attack–two different things with very different implications for the impacted customer. This type of information can help the SOC team determine how severe the threat is and how remediation should be handled.
Earlier this year, for instance, a customer was flagged for a rogue ScreenConnect remote monitoring and management (RMM) tool installation. We see a ton of RMM abuse by cybercriminals, so at the surface this seemed like a fairly standard incident. However, by digging just a little bit deeper, SOC analysts found that a user at the organization had fallen for a fake tech support scam.
Analysts looked at a few breadcrumbs while investigating this incident. The first was a contextual signal that came through the Huntress portal just before the rogue ScreenConnect alert popped. This contextual signal–which is low fidelity and does not require investigations when detected in isolation–indicated that the QuickAssist RMM had executed. These signals combined indicated that QuickAssist had given access to a remote user, who then deployed the malicious ScreenConnect instance on the host.
SOC analysts also looked at the user’s notepad.exe tabs and found that the user was actively getting scammed in real time. Analysts also checked the archive of the user’s browser history, which revealed that they had visited a “support” page and “cancellation and refund” form, before visiting the webpage for their personal bank.
As seen in the video above, the team was able to get in touch with the impacted customer and stop the scam in its tracks. We take response to the next level by digging up the root cause and stopping the threat at its source.
What is the extent of the attack?
The extent of an incident is another key piece of information that can help SOC analysts determine its severity. Sometimes, an attacker may have been in a business environment for days, weeks, or even months before they were detected. For businesses, incidents with a longer duration could have important implications. Maybe an initial access broker compromised an organization a month ago, and sold that access to multiple ransomware groups–or maybe a stealthy threat actor has been laying low in a company’s environment, quietly gathering data.
We frequently see this type of situation when businesses first install our agent, or test out our services in a trial. Because they didn’t previously have EDR, threat actors were able to lurk in their environments undetected.
In July, for instance, we were installed post-incident on two endpoints at a manufacturing company. Immediately upon installation, Managed Antivirus alerts signalled the file system had been encrypted by Akira ransomware. While trying to figure out the extent of the attack, the SOC team dug through historical Windows Defender detection events and logs from impacted endpoints.
This involved tasking logs from days prior to the incident. Upon closer investigation, it was clear that the threat actor first gained access to the infrastructure on July 24–almost four days prior to the ransomware deployment on July 28. That’s because the logs revealed malicious logins on July 24, which were linked back to a certain hostname and IP address. The telemetry that the SOC looked at in this investigation also revealed that the threat actor gained access via a publicly accessible Remote Desktop Protocol (RDP) instance, and likely deployed the ransomware via UNC paths.
SOC analysts isolated the impacted host from the network. However, this information about the attack’s root cause and extent was valuable for the targeted organization as they strategized moving forward.
Are others at risk?
Another important determination from our investigations is whether a threat is isolated, or if it has an impact at a wider scale.
Last year, the SOC received an alert indicating a 7zip binary had been executed from a suspicious location. Further digging into the incident showed several other techniques used by the threat actor, including the use of a LOLBin (Windows Program Compatibility Assistant, or pcalua.exe) to execute malware and commands. The scale of this investigation widened when we found the same types of tradecraft–including the use of pcalua.exe–on additional hosts, and at various other organizations. As part of the investigation, the team studied historical EDR telemetry and found that the activity went back as far as November 2023 in the observed hosts.
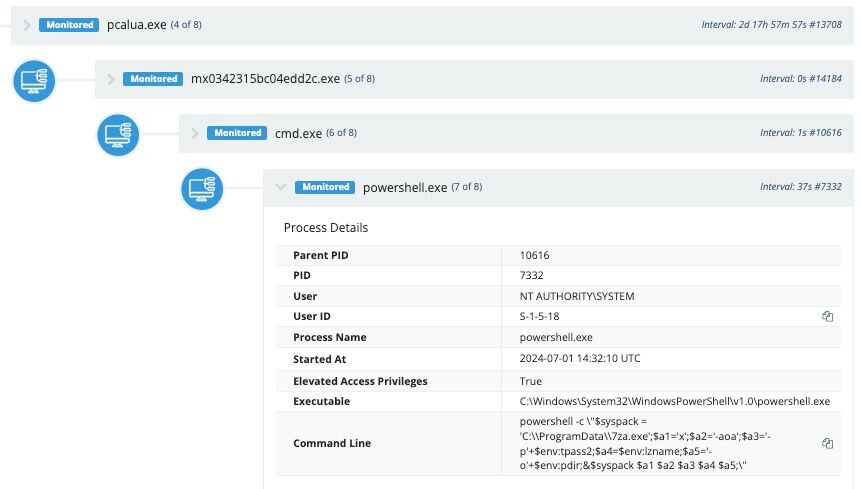
At the end of the day, we uncovered three intrusions across three different organizations that were located in Canada. We also found that this activity matched closely with known TTPs from RedCurl, a known APT group.
The value of investigations for you
Businesses today are playing a constant game of threat whack-a-mole. Our SOC team’s telemetry-driven investigations, and creative and deductive threat hunting prowess, gives our customers a leg up against hackers.
They help businesses by providing important contextual pieces of clarification around the scope, root cause, and severity of an incident.
They help the broader community by sniffing out whether an attack has a broader impact, and by looking at indicators of compromise (IoCs) that can help other organizations defend themselves (by the way, you can check out our open source sharing of IoCs here). Together, along with our Hunt teams that are actively pursuing threats night and day, they provide a multi-layer capability for us to track down hackers rapidly.
Many other endpoint solutions will simply suspend a threat for a company, but we do much more than that. As an industry, this is a gold standard we should all be striving toward. We should be making informed decisions to uproot them at the source, sharing information to make it more accessible, and working together to hit attackers where it hurts.
Our question to you is this: in 2025, do you deserve anything less?