
Watch this video for a breakdown of the ransomware attack path, so you can spot it early, shut it down, and steer clear of hacker paydays.
Yes, if you have the right visibility across your network and systems.
These days, many initial access broker groups and ransomware gangs rely on weaknesses in security tools like firewalls and VPNs to gain access to a network. But they can’t do it quietly, making it possible to detect attacks through log and event monitoring.
Yes, if you have the right visibility across your network and systems. These days, many initial access broker groups and ransomware gangs rely on weaknesses in security tools like firewalls and VPNs to gain access to a network. But they can’t do it quietly, making it possible to detect attacks through log and event monitoring.
Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.


Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.
Yes, if you have the right visibility across your network and systems. These days, many initial access broker groups and ransomware gangs rely on weaknesses in security tools like firewalls and VPNs to gain access to a network. But they can’t do it quietly, making it possible to detect attacks through log and event monitoring.
No. Ransomware threats move past basic defenses in minutes. You need modern endpoint detection and response combined with human expertise to hunt, analyze, and eject the threat fast.
Definitely. Identities are the new perimeter. Ransomware groups will intercept MFA requests, steal session tokens, and ultimately compromise accounts to get access to your systems and data.

Empower your employees to detect and avoid phishing and identity-theft attacks, making ransomware groups work hard to get access to your network.
Centralize logs and events, and implement 24/7 monitoring across critical devices, systems, and applications to detect threat actors trying to compromise your business.

Add depth and resilience to ransomware attacks with enterprise-grade endpoint and identity threat protection, to detect, contain, and evict threats before they lock down your environment and impact your business.

Ransomware doesn't just appear. It starts with an attacker gaining access to your network - whether through a phished employee installing a malicious remote access tool, abusing a vulnerable VPN, or using a compromised admin password and walking in through the front door. The Huntress Platform solves these attack vectors with Managed Security Awareness Training to educate and empower employees against modern threats, Managed SIEM to provide visibility of threat actor activity across your environment, and Managed EDR and Managed ITDR to protect your endpoints and identities when ransomware gangs get past other defenses and shutting them down before they can ransom your business.

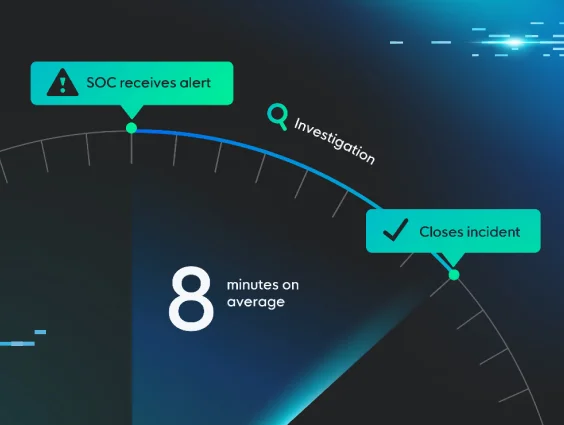
Traditional security tools generate overwhelming alerts that security teams don't have the staff to investigate. Our human-led, AI-assisted 24/7 SOC validates every potential threat, performing the investigation for you. This means zero false positives, a rapid response to contain and remediate threats, and expert-driven guidance to improve the resilience of your organization against future attacks. When a real threat is found, we provide the verified information and tools you need to eject the attacker in minutes, minimizing business disruption. The end result is fast MTTR with high-fidelity expert response without needing to hirie a 24/7 security team of experts.


The true damage from ransomware is business interruption and recovery cost. Leveraging the Huntress Platform, we give you an unfair advantage against ransomware groups targeting your business. When threats are discovered compromising your network with Huntress Managed SIEM, our SOC proactively activates defenses on endpoints with Huntress Managed EDR, preventing attackers from gaining a foothold, and moving laterally across your network to compromise and ransom your organization. We deliver a surgical response, not a panic button, ensuring your business stays online and operational.
Competitive Edge: Rapid, surgical containment that protects your recovery plan.




Key Methods, a top managed service provider (MSP) in Washington state, has a solid reputation for keeping security front and center in their business for their nearly 80 clients.
“When your primary security layers are all unified in one platform, it’s easier to build depth with a vendor,” says Paquette. “And when everything feeds into the same SOC, it’s even better.” - Dan Paquette | Key Methods


Powered by strategic acquisitions, RAFTRx is a fast-growing network of regional brands that helps customers across nine states and is growing. But keeping up cybersecurity with rapid growth is far from simple.
“Our IT department is just me and my VP,” says Reese Borel, System Administrator and Cybersecurity Lead at RAFTRx. “When your company scales this fast, you need trusted tools that do the heavy lifting.” - Reese Borel | RAFTRx


Early detection and defense in depth to remove the attacker's advantage.

Our experts validate and respond to every critical threat 24/7.

Protection from employees to endpoints to make ransomware groups miserable.

Protecting against ransomware requires a defense in depth approach due to the multiple approaches threat actors use to gain access to your systems and data. Endpoint detection and response is no longer the single solution. Businesses need to be educating their employees to detect and avoid phishing and credential theft attacks, and secure password practices. You need visibility into pre-attack activities by threat actors targeting your IT infrastructure, and monitoring for identity and credential theft in the event the “human firewall” is compromised.
Speed matters when responding to a ransomware attack. The faster an attack is detected and the threat is contained, whether that’s shutting down VPN access or isolating an endpoint, the greater likelihood your business will minimize the impact of a ransomware attack.
Current trends in ransomware protection are to ensure protections are in place to counter the range of ransomware attacker tradecraft - phishing users for access to their systems and accounts, abusing vulnerabilities in systems to gain access to networks, gaining access to endpoints and moving laterally around a network. And being able to quickly recover from an incident with documented and tested incident response procedures along with a robust and secure data backup strategy.
AI is helping IT and Security teams defend against ransomware attacks by allowing them to triage and prioritize alerts faster, letting them move at the speed ransomware attacks are happening.
It’s important to have a strong ransomware incident response process that has been tested, validated, and refined. It requires a robust data backup strategy to quickly recover systems and data that have been impacted in order to get business operations back as soon as possible.
Antivirus is based on known file signatures and often fails against modern, fileless attacks. Huntress Managed EDR looks for the tradecraft of the human attacker—how they move, escalate privileges, and execute commands—after they bypass basic defenses. Our human-led SOC is dedicated to threat hunting for these subtle activities, ensuring a response that generic preventative tools simply cannot deliver. We stop the human attacker before they can deploy the automated ransomware payload.
Our focus is on speed and quality. For example, Huntress Managed SIEM provides broad-visibility across your security controls and IT infrastructure to detect signs of threat actor activity before they can compromise your network. The human-led, AI-assisted SOC ensures verified, actionable alerts are delivered within minutes with the specific context and steps needed to defend against an attack. Unlike solutions that leave you to investigate a flood of alerts, we provide a definitive path to eject the attacker immediately, dramatically reducing the window of opportunity for the ransomware to execute.
Backups are crucial for recovery, but they don't prevent downtime, reputational damage, or the increasing risk of data exfiltration (where attackers steal data before encrypting it). Modern ransomware is a two-step attack: steal data, then encrypt. Huntress helps stop the attacker before they can execute either step, saving you the massive cost, time, and reputational hit of a full recovery process. Prevention is always cheaper than recovery.
Ransomware groups prey on employees because they can provide an expressway into a network. Employees can be phished to install an attackers' tools or steal administrative passwords making it easy to compromise a network.
No. Ransomware threats move past basic defenses in minutes. You need modern endpoint detection and response combined with human expertise to hunt, analyze, and eject the threat fast.
Definitely. Identities are the new perimeter. Ransomware groups will intercept MFA requests, steal session tokens, and ultimately compromise accounts to get access to your systems and data.


See Huntress in action. Our platform combines a suite of powerful managed detection and response tools for endpoints and Microsoft 365 identities, science-backed security awareness training, Managed SIEM, and the expertise of our 24/7 Security Operations Center (SOC).
Schedule a demo to:


Secure endpoints, email, and employees with the power of our 24/7 SOC. Try Huntress for free and deploy in minutes to start fighting threats.
