Cybersecurity has always relied on trust. Every software update, hardware purchase, and cloud integration depends on the implicit belief that vendors will protect their customers. That trust affords both parties operational fluidity, allowing teams to adopt new capabilities and maintain systems without having to question the integrity of every single component. But it also creates a valuable target for attackers: compromise a supplier and gain access to every trusting, interconnected customer behind it.
Today’s enterprises operate in a tangled web of platforms, SaaS solutions, tools, and managed services. Trust is the glue holding this ecosystem together, often granting vendors privileged access, automated permissions, and a direct line into critical systems.
In this blog, we’ll explore the cracks in this trust-based model and dive into why the software supply chain is shifting toward a zero-trust approach.
A brief, ongoing history of supply chain attacks
The first major supply chain attack was founded on trust. In 1989, Joseph Popp distributed the AIDS Trojan on floppy disks at the World Health Organization’s AIDS conference. The disks seemingly contained introductory information on the disease, but installing them instead introduced malware that encrypted files and demanded payment.
In 2025, brands including Hertz and Sam’s Club reported breaches that involved the exfiltration of customer data. The incidents were traced back to a compromised third-party transfer platform used across multiple industries. Malicious components remained in the vendor’s environment for months before detection, a compromise that would propagate downstream.
In 1989, people put their trust in a floppy disk from a reputable source and suffered the consequences. In 2025, companies trust a third-party provider, and the story repeats itself. What has changed in the modern era of supply chain attacks is the scale. Managed Service Providers (MSPs) and small to mid-sized businesses (SMBs) rely heavily on vendor tools and automated integrations. Each new product added to their tech stack increases the number of external systems that have privileged access, directly widening a company’s attack sRecent industry reports reflect this expansion of trust as a driving force for exploitation. Cowbell Cyber reports a 431% increase in supply chain attacks between 2021 and 2023, and Verizon's 2024 Data Breach Investigations Report (DBIR) indicates that 15% of breaches involved a third party.
The new geography of digital supply chains
The security supply chain isn’t just about software anymore—it’s evolved. Enterprises now rely on third-party apps, servers built with components from countless manufacturers, cloud providers for data storage, and MSPs to handle security operations.
These multiple, sprawling dependencies have shifted the shape of the digital supply chain. What was once a long, sequential chain of X is now a web of interconnected services. With this mesh comes a diverse and difficult-to-manage ecosystem, one where trusted partners with privileged access, automation hooks, or credentials could be the source of a breach.
Over the last few years, this overprovisioning of trust has taken its toll:
- Software Supply Chain Breaches: SolarWinds, Log4j, and Codecov all revealed how compromised updates, vulnerable libraries, or corrupted build tools can instantly infect thousands of connected organizations.
- Hardware Supply Chain Vulnerabilities: Supermicro vulnerabilities and firmware-level exploits show how weaknesses can be introduced into devices before they even reach an organization. Acting beneath the operating system, hardware vulnerabilities are hard to trace and can exist for years without detection.
- Cloud and SaaS Exposure: Breaches affecting Okta, issues tied to GitHub Actions, and the trojanized 3CX component demonstrate how attackers can exploit APIs, compromise integrations, and misuse credentials. As a tool for mass centralization, an incident within cloud platforms can extend far beyond the original target.
- MSP and IT Vendor Compromise: Events involving Kaseya and exploitation attempts against ConnectWise demonstrated how attackers can abuse remote management platforms to move laterally into customer ecosystems. When a privileged service, like an MSP, is compromised, its connected companies become targets.
Today’s supply chain poses a multi-directional threat, one that is facilitated and accelerated by the trust that companies place in their software, hardware, and solution suppliers.
How attackers are reshaping the software supply chain landscape
The complex web of trust between suppliers and businesses means that attackers no longer need to directly target companies. Instead, by focusing on vectors, suppliers, and integrations that organizations already trust, cybercriminals are able to bypass a company’s security defenses entirely. Understanding who is behind these attacks sheds light on why the threat continues to escalate.
Nation-state groups are sophisticated actors that exploit supply weaknesses. Teams such as APT29, UNC2452, and Lazarus use upstream compromise to establish long-term, covert access to high-value networks. The SolarWinds intrusion demonstrated this strategy, with attackers infiltrating the company’s build pipeline and inserting malicious code into digitally signed updates. The exploit impacted 425 Fortune 500 companies as they unknowingly installed the compromised software, bypassing all internal security controls.
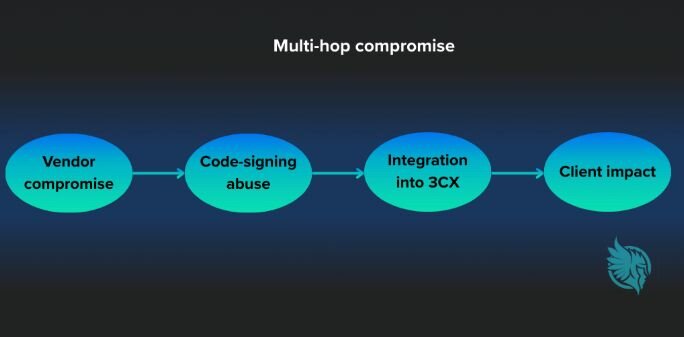
Criminal cybergroups have adopted a similar tactic of targeting vendors, but focus on monetizing their exploits rather than gathering information from them. The 3CX intrusion reinforced this tradition when a compromised third-party trading application, whose code-signing certificate was stolen, allowed attackers to insert a malicious component into 3CX. When the installer was pushed to customers, thousands of environments and MSPs unknowingly deployed the infected software.
On a smaller scale, hacktivists and opportunistic attackers also play a role in supply chain attacks. Open-source ecosystems, especially NPM packages and widely used libraries, are a common site of attack. By publishing malicious packages, hijacking abandoned projects, and injecting harmful code into widely trusted dependencies, they steal credentials or plant ideological messages.
These trends reveal a shifting and dangerous supply chain threat landscape. A single vendor exploit can cascade into thousands of connected systems. Mandiant’s M-Trends 2024 reports a significant rise in intrusions stemming from upstream compromises, with a steady increase over the past five years.
Flying under the radar: hardware supply chain exploits
While the software supply chain dominates headlines, hardware vulnerabilities are often harder to detect and can cause long-term damage. The Supermicro motherboard controversy, first reported by Bloomberg in 2018, demonstrated how components from unverified manufacturers could be altered before assembly.
For organizations in the manufacturing and industrial sectors, where hardware integrity supports production systems, safety controls, and automation, the risks are particularly acute.
Firmware-level attacks are problematic, as they persist across OS reinstalls and reboots, alongside being extremely difficult to identify. Once implanted at the chipset or BIOS level, these vulnerabilities can remain in place for years, invisible to traditional monitoring tools and remediation.
Hardware supply chain attacks present differently from software attacks but are often more persistent, difficult to detect, and high-risk.
The cloud and SaaS supply chain: Shared responsibility or shared vulnerability?
The “shared responsibility” model that most cloud providers use dictates that the provider will secure all its infrastructure, while the customer handles data and access. While this works for most environments, it creates a gap that obscures who takes responsibility when an upstream integration is compromised.
Misconfigured CI/CD pipelines, API tokens, and third-party connectors can allow malicious actors to inject code into otherwise secure environments. This is what happened in 2023 with Okta, when a compromise in their support system gave attackers access to customer data, creating a cascade of downstream exposure.
While neither the cloud provider nor the customer acted negligently, the interconnected nature of the modern supply chain caused a breach. Downstream customer data was exposed due to the failure of upstream systems and integrations.
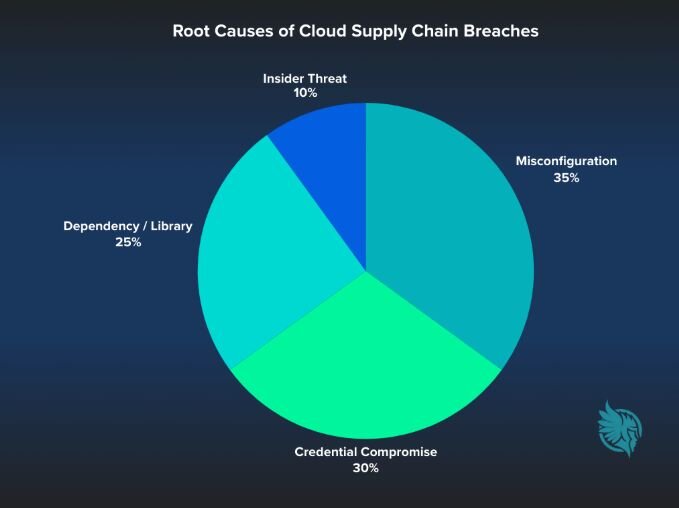
The percentages shown in the pie chart are conceptual; exact distributions of cloud supply chain breaches are not publicly disclosed.
High-value targets: the SMB & MSP reality check
A Managed Service Provider’s business model relies on vendor tooling, privileged access, and complete trust in their tech stack. Due to the elevated access they have across their clients’ companies, MSPs are a particularly valuable target for cybercriminals.
When groups gain access to a tool an MSP uses, compromise can quickly spread. The 2021 Kaseya VSA incident, where a malicious update was delivered through a legitimate mechanism, spread ransomware to 1,500 organizations worldwide. One trusted operational layer turned into a direct tunnel that malicious actors could use to secure systems.
If an MSP operates with a small team, constrained resources, and limited telemetry, they may have reduced visibility over upstream tools. When partnering with SMB customers, this is intensified, as SMBs may assume that MSPs have complete visibility into their environment. In reality, upstream third-party platforms can create blind spots that the MSP can’t easily mitigate.
Verizon’s 2024 DBIR notes that the average dwell time for a supply chain compromise exceeds 200 days, compared to only 25 for direct intrusions. The disparity between these statistics outlines how deeply attackers that embed themselves within trusted infrastructure can go before being detected.
Building supply chain resilience through visibility, verification, and vendor accountability
While supply chain attacks are complex and multi-directional, businesses can protect themselves by emphasizing three pillars: visibility, verification, and vendor accountability.
Here’s how these measures convert passive trust into active assurances:
- Visibility: Maintain a complete, continuously updated map of all vendors, integrations, dependencies, and their associated privileges. Use threat intel feeds to monitor vendor breach notifications.
- Verification: Validate the integrity of every update and component through Software Bill of Materials (SBOM) requirements, digital signature checks, and runtime integrity monitoring.
- Vendor Accountability: Hold vendors to defined security standards through transparent disclosure expectations, contractual obligations, and clear offboarding thresholds.
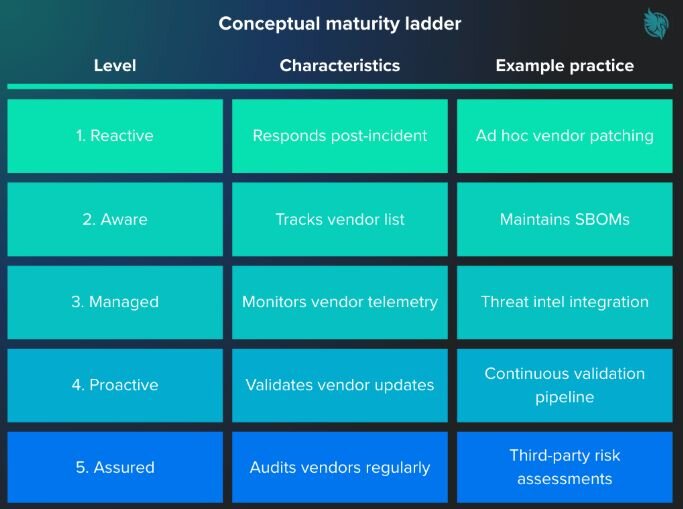
For SMBs and MSPs that want to evaluate their current supply chain security posture, here’s a useful framework to follow.
This table is a conceptual framework created for illustrative purposes. It is based on widely recognized supply chain security best practices and is not derived from survey data or published research.
The future: policy, automation, and AI-assisted verification
Understanding the severity of the supply chain threat, policy and technology are racing to keep up.
From a regulatory perspective, federal policy is looking to reform the software supply chain. Executive Order 14028 on Improving the Nation’s Cybersecurity requires software suppliers to produce SBOMs and follow secure development practices. Coordinated through CISA and NIST, this approach is driving the broader adoption of secure software supply chain precautions.
On the automation front, organizations are beginning to shift from periodic assessments to continuous assurance. Real-time telemetry, cryptographic signing, and automated attestation are replacing static vendor questionnaires. These changes aim to ensure software integrity is validated at every stage, rather than solely trust-based. NIST’s Secure Software Development Framework and the OpenSSF scorecard are helping to standardize these practices.
Artificial intelligence is also aiding in anomaly detection that can signal a potential supply chain compromise. Early-stage machine learning systems can flag irregular signing behavior, firmware deviations, and unexpected build changes long before traditional monitoring would have raised the alarm. Although still evolving, the ability to augment human analysis with continuous, context-aware AI monitoring is a big step forward for software supply chain security.
From policy to automation to the integration of AI, all roads point to a more secure and verification-based supply chain. While trust was once the currency of the supply chain, it’s quickly becoming validation.
Reframing Zero Trust to the Supply Chain
While the exact vector used in a supply chain vulnerability exploit changes, what’s continuous is a misplaced trust. From SolarWinds to Kaseya, these events demonstrate that trust must be a continuous process, not a singular contract. Zero Trust means no implicit trust is granted to assets or user accounts based solely on their physical or network location. While primarily applied to networks and identities, Zero Trust needs to expand to the software supply chain.
Reframing Zero Trust to the supply chain involves following these rules:
- Never Blindly Trust Code: Verify all components via cryptographic signatures and SBOM validation.
- Continuously Verify Vendor Integrity: Use telemetry and behavioral analytics to detect changes over time.
- Limit Blast Radius: Segment systems so a compromised integration can’t escalate or move horizontally across an enterprise.
When even your most trusted vendor can become an unwitting attack vector, Zero Trust is the natural next step in software supply chain security.
While this reality requires major shifts, they don’t have to happen all at once. MSPs and SMBs can take small steps in the right direction by enforcing least privilege for vendor accounts, verifying updates before deployment, and monitoring endpoint behavior for unauthorized script execution or persistence mechanisms.
It’s impossible to fully eradicate supply chain compromise. But by treating vendor relationships as active security partnerships, not passive contracts, businesses can take an active stance in the next phase of cybersecurity resilience.
And from our part at Huntress, we’ll keep up with our commitment to elevate and strengthen those around us and stop cyberattacks in their tracks.