Threat actors don’t need to hack your network to cause damage. Often, just one stolen password is enough.
Account takeover fraud is a simple and effective form of cybercrime. More than half of adults who've experienced identity fraud say it started with an account takeover. It gives attackers direct access to personal or business accounts, so they can steal data and money or impersonate legitimate users to commit fraud.
These attacks can hit any organization with online systems or customer accounts, and they’re becoming harder to spot as attackers automate and scale their methods.
Account takeover fraud prevention starts with understanding how these schemes work and what tools and defenses can stop them before credentials are compromised.
Account takeover fraud, defined
Account takeover fraud (or “ATO”) happens when a threat actor gains unauthorized access to a user’s login credentials and uses them for malicious activity, like theft or impersonation.
Attackers don't always need to "hack" your account—sometimes, they just log in. Account credentials can be bought on the dark web or stolen through social engineering, data breaches, or phishing campaigns. Once they have access, they quietly change settings, send messages, reset passwords, change contact details, or make fraudulent transactions that look legit.
Effective account takeover fraud solutions focus on early detection, identifying unusual behavior that doesn't fit a user's normal patterns, and shutting down stolen credentials before they can be reused.
If you’ve ever gotten an email from a “friend” asking for help—or a strange link, that's probably an email account takeover scheme in action.
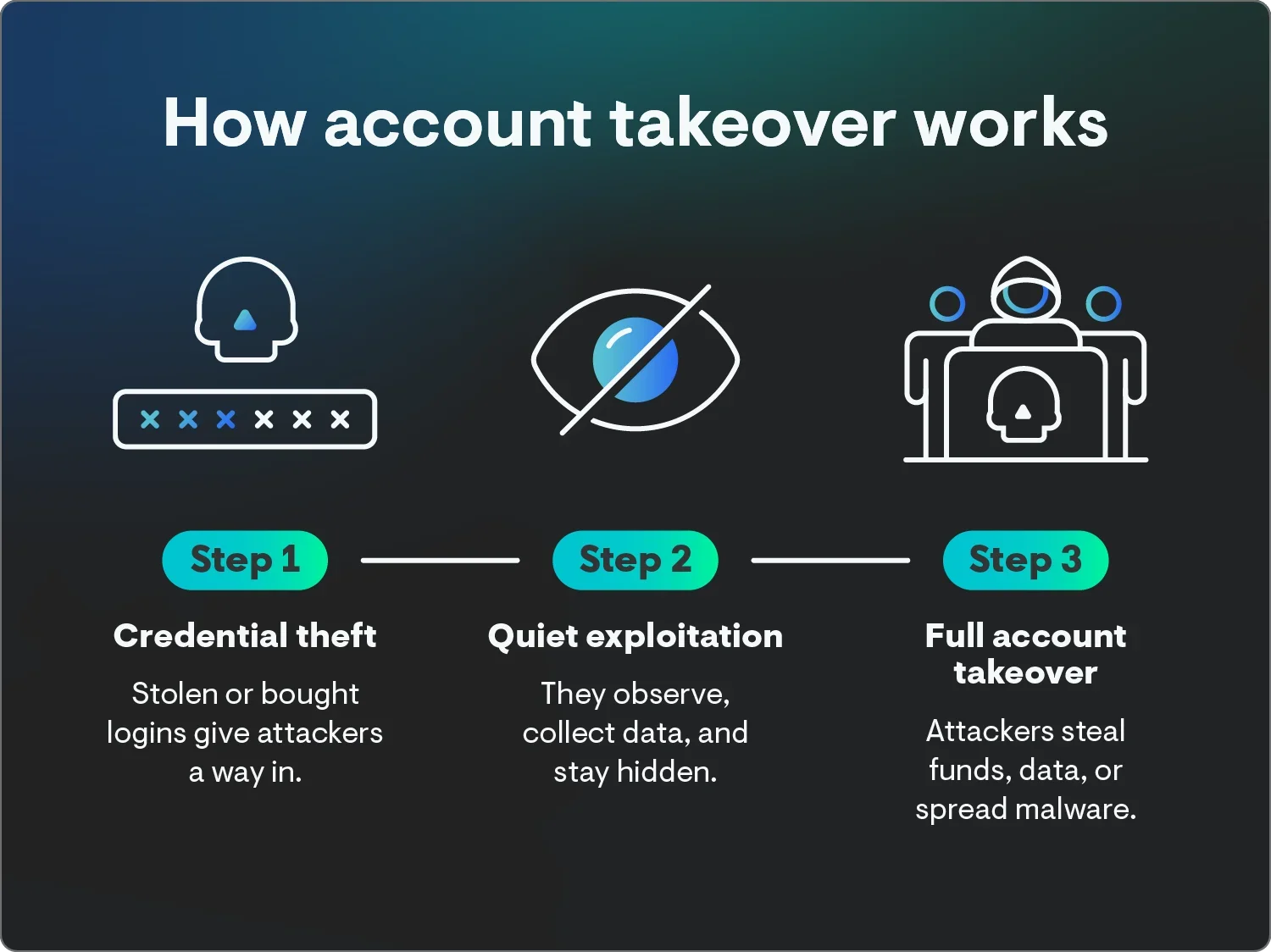
How account takeover fraud works
ATO attacks play out in stages. Threat actors gamble on finding easy targets, usually starting small by testing stolen credentials before escalating to full control once they have access. For them, it’s like spinning a roulette wheel in Vegas. With enough spins, malicious actors can win it big.
Understanding each stage can help you spot red flags before serious damage can happen.
1. Credential theft
The attack usually starts with stolen credentials. Phishing emails, data breaches, social engineering, or malware are the usual techniques. Threat actors can also buy username and password combinations on the dark web or use automated botsto test different login combinations across sites known to have personal, customer, or business data until they find one that works.
2. Quiet exploitation
With access secured, attackers move carefully to avoid detection. Some move fast, but others lurk—reading messages, collecting sensitive information, and forwarding copies of emails to external inboxes. This lets them learn the account owner's behavior, so their activity looks normal.
3. Full account takeover
After studying the environment, attackers act. They might transfer funds, request payments from vendors, or spread malware. Some use the compromised account to launch even more account takeover schemes, extending the attack across other users or systems.
By the time the real account owner notices any suspicious activity, the attacker has often erased any evidence or changed privileges to maintain long-term control.
Types of account takeover fraud
Attackers use many techniques to gain and exploit unauthorized access. Each method targets different parts of your environment but follows the same goal of stealing credentials, data, or funds and doing it while staying under the radar.
1. Internal phishing
Internal phishing occurs when a threat actor uses a compromised corporate account to send emails inside the same organization. Because the messages look like they come from a trusted coworker, recipients are more likely to click links, download malware, or share credentials without thinking twice.
2. Supply-chain phishing
Supply-chain phishing takes advantage of your business’s existing vendor or partner relationships. An attacker impersonates a legit contact to send fraudulent invoices, links, or payment requests. Because these emails come from a known source, recipients often act without question.
3. Business email compromise
Business email compromise (BEC)is a high-impact impersonation tactic where criminals hijack or spoof a corporate email account. Once in control, they send realistic requests, like asking for wire transfers or sensitive data, using the executive’s tone and signature.
4. Data exfiltration
Data exfiltration gives bad actors access to confidential information stored in your email, calendars, contacts, and sensitive data in file shares. Once stolen, this data can be used for blackmail, competitive intelligence, or sold to the highest bidder on the dark web.
5. Session hijacking
Session hijacking happens when an attacker intercepts or steals active session cookies. These stolen tokens let them bypass logins entirely, so they look like an authenticated user.
6. Credential stuffing
Credential stuffing uses automation to test large lists of stolen usernames and passwords on multiple sites. Password statistics show that many people reuse passwords, so this method lets attackers compromise several accounts at once.
7. SIM swapping
In a SIM swap, the attacker convinces a mobile carrier to transfer a victim’s phone number to a SIM card they control. From there, they can intercept calls, texts, and multi-factor authentication (MFA) codes to reset passwords or authenticate fraudulent logins.
8. Malware
Malware-based ATO attacks involve installing keyloggers or stealers on a user’s device. These programs record every keystroke and steal credentials, handing attackers direct access to accounts and systems.
Consequences of account takeover fraud
The lasting effects of an account takeover can be severe for any business. Here’s what that damage can actually look like:
-
Financial loss and uninsured costs: According to the Huntress Cybercrime Report, more than one in four organizations lose between $100,000 and $500,000 each year to cyber incidents like ATOs. Some incidents cost more than $250,000 each, and 22% of businesses lack cyber insurance entirely, leaving them completely on the hook for recovery.
-
Reputation damage and customer churn: Nearly 73% of consumers believe the brand, not the user, is responsible for preventing an account takeover. When customers lose trust, they don't usually complain—they just leave.
-
Operational downtime and resource strain: The Huntress Cyber Threat Report found that infostealers and remote access trojans (RATs) account for nearly half of all identity-related intrusions, often granting attackers persistence within systems. Recovery efforts can take days, halting productivity and stretching IT and security teams thin.
-
Higher chargebacks and transaction disputes: ATO fraud often triggers fraudulent purchases and payment reversals. Excessive chargebacks can increase processing fees, or worse, account termination from payment providers.
-
Regulatory and legal exposure: For sectors like healthcare, where 33% of professionals cite data breaches as their top concern, ATO-driven incidents can violate privacy regulations, exposing organizations to steep fines and compliance scrutiny.
-
Increased insurance scrutiny: Huntress data shows that 58% of insured organizations saw reduced coverage over the past five years. Insurers now require stronger safeguards like MFA, Endpoint Detection and Response (EDR), and security awareness training, controls that help but take time and investment to maintain.
Account takeover attacks are increasing, and fast. Industry data shows a 354% year-over-year jump, and Huntress research found credential theft in at least 14% of all observed attack patterns.
No matter the target—a healthcare network, school district, or small business—the outcome is the same: stolen access, financial damage, reputational fallout, and broken trust.
How to detect account takeover fraud
Spotting an account takeover early can make all the difference. The problem is, attackers don’t kick down the door—they log in, look around, and act like they've been there all along. Staying alert to the small signs of unusual behavior helps you catch them before they dig in deeper.
Here’s what to watch for:
-
Logins from locations or devices that don’t match your normal activity.
-
A sudden wave of failed login attempts that could point to credential stuffing or brute force testing.
-
Password or MFA reset notifications you didn’t request.
-
New or hidden email forwarding rules that quietly reroute messages outside your organization.
-
Large file downloads or access to folders you don't normally use.
-
Alerts from endpoint or identity monitoring tools, which often catch early signs of malware or credential theft.
-
Reports from customers or partners about suspicious messages coming from legitimate company accounts.
These signals don’t always mean you’ve been compromised, but they should never be ignored.
How to prevent an account takeover
Account takeover is a growing concern for businesses and individuals. But if you use a combination of best practices, your business can level up account takeover fraud detection and take action to prevent further damage.
Malicious hackers are actually really lazy, so the more access barriers you build around your known security attack surface, the greater the chance they're going to look elsewhere for an easier target. These practices form the foundation of how to prevent account takeover fraud across your business
-
Turn on MFA everywhere you can: It's one of the easiest ways to block most attackers, yet Huntress data shows only 40% of businesses use it consistently. SMS-based MFA is too easy to intercept, so stick with app or hardware-based options.
-
Use endpoint detection and response: Malware is still everywhere, with 54% of organizations saying they faced it this year, according to our Cybercrime Report. Managed EDR spots it fast and cuts off infected systems before credentials or sessions can be stolen.
-
Keep employees trained and alert: Phishing and social engineering remain the biggest entry points for ATOs. In our Healthcare Threat Report, 37% of IT pros said employee training was their biggest security focus for 2025. Awareness matters more than fancy tools.
-
Adopt a zero-trust mindset: Don’t assume anyone or anything is safe by default. Every login, every device, every request gets verified. That friction is what keeps attackers from moving freely once they’re in.
-
Secure how passwords are stored and shared: Weak or reused passwords are what attackers count on most. Encrypted password managers make unique logins standard and limit the damage when one credential leaks.
-
Watch for identity weirdness: Unexpected logins, “impossible” travel, or session anomalies are all early clues. The Huntress Managed Security Platform looks for these patterns and alerts our SOC analyst team the moment something’s off.
-
Shorten session times and tighten access: The less time a login stays active and the fewer permissions it has, the smaller the window for attackers to exploit it.
You can’t stop every attempt, but you can make it too much work to be worth their time. Staying a hard target means solid defenses, informed users, and nonstop visibility into your environment.
Protect your identities and stay ahead of threat actors
Account takeover fraud isn’t going anywhere. But neither are you. With the right defenses in place, you can make life a lot harder for attackers and keep your team focused on what matters.
An identity threat detection and response (ITDR) solution can dramatically reduce your risk and protect your business from malicious hackers.
Huntress Managed ITDR makes it easier to secure identities and safeguard your environment. With continuous monitoring and 24/7 threat detection, you can spot the warning signs of account takeover fraud and stop attackers before they get comfortable.
Learn how we can help keep your business safe—schedule your custom demo today.
FAQ
What are the examples of account takeover?
Account takeover fraud can happen in many ways, like when a hacker steals login credentials through phishing or a data breach and then uses those credentials to send emails, transfer funds, or access private data. It’s basically any situation where someone gains control of a legitimate account and uses it to act as the real owner.
What is the difference between identity theft and account takeover?
Identity theft involves stealing someone’s personal details—like their name or Social Security number—to open new accounts or commit fraud. Account takeover fraud, on the other hand, uses existing credentials to hijack active accounts and act as the legitimate user.
How do I stop account takeover fraud?
Once you spot suspicious activity, act fast: reset affected passwords, review access logs, and remove any unauthorized devices or users. Then, enable multi-factor authentication and use tools like Huntress Managed ITDR to stop future takeovers before they spread.
How do I prevent account takeover fraud?
Start with layered protection: use MFA on all accounts, train employees to spot phishing, and watch login behavior for odd patterns. Encrypted password managers and endpoint protection tools—like Huntress Managed EDR—help close the gaps attackers exploit most