Cybercrime is among one of the world’s largest economies.
While this statistic obviously isn’t excellent, it’s not all doom and gloom. According to our June 2025 survey of more than 500 American IT professionals, IT professionals in the US are mostly very confident about their ability to prevent attacks.
Cybercrime trends have fluctuated in recent years, with growing concerns around AI-driven attacks and how increasingly remote workplaces create more opportunities for bad actors to sneak in.
“As we highlighted in the Huntress 2025 Cyber Threat Report, over the last year, threat actors have stepped up their game, shifting their ransomware strategies to data theft and extortion over encryption and relying on remote monitoring and management (RMM) tools for access, lateral movement, and persistence, for instance,” says Lindsey O'Donnell-Welch, Staff Technical Community Engagement Writer at Huntress. “Cybercriminals have targeted various industries like the healthcare, education, and government sectors. Organizations can take several first steps to protect against cybercrime, like security awareness training, implementing multi-factor authentication (MFA), and regularly updating all software and systems.”
Read on to see the top cybercrime trends of 2025, plus critical cyber statistics for your business –– and how you can best protect yourself.
|
Key Takeaways
|
1. More than half of American organizations experienced a malware attack in the last year
When asked which types of cybercrimes their organization has experienced in the past 12 months, the most common answer was malware infections, with 54% of people reporting they’d experienced one. With malware encompassing such a wide range of attacks—viruses, ransomware, spyware, the list goes on—it’s not surprising that it was the leading type of cyberattack for most organizations.
“Malware and phishing are common attack types because of their versatility,” says Lindsey. “Cybercriminals can achieve multiple objectives, like gaining system access, stealing data, and disrupting operations, all with one single tool.”
The next most commonly reported attack type is phishing, including spear phishing and whaling, which 44% of organizations experienced. Other attacks, which may have some overlap, that happened this year include:
-
Business email compromise (BEC) attacks (36%)
-
Website defacement or denial-of-service attacks (35%)
-
Insider threats leading to data theft or sabotage (32%)
-
Credential stuffing or account takeover attacks (28%)
-
Supply chain compromise leading to cyber incidents (24%)
This high rate of malware and phishing attacks can be blamed on a number of things, but bigger attack surfaces mean more entry points and potential for vulnerabilities. It's become incredibly easy for threat actors to launch these attacks, often exploiting common weaknesses like exposed Remote Desktop Protocol (RDP) ports or unpatched systems.
On the flip side, the cybercrime landscape itself has evolved. We're seeing a more competitive malware development scene with sophisticated features, formalized operational models like Ransomware-as-a-Service (RaaS) and Initial Access Brokers (IABs), and a highly streamlined process for compromising and selling data on underground forums.
This is why multi-pronged approaches to cybersecurity are so important, including endpoint detection to quickly find and disable attacks, as well as security awareness training to ensure employees can recognize threats.
2. Organized criminal groups are the biggest perceived threat actor
Just over a quarter of respondents (26%) rated organized cybercriminal groups as the threat actor that poses the greatest risk to their organization. These are essentially groups of hackers who make it their full-time job to access your system. It was the most commonly cited threat, followed by:
-
Competitors (19%)
-
Malicious insiders (18%)
-
Hacktivists (16%)
-
Negligent insiders (12%)
-
Nation-state actors (9%)
-
Other (1%)
Threat actors are typically responsible for the majority of cybercrimes, with varying motivations like activism, or in this case, “hacktivism,” and even revenge. For most attackers, their primary focus is monetary gain, but hacktivists, for example—people who commit cybercrimes for information or political motivations—may be motivated by other reasons.
Let’s unpack what really drives attackers to do what they do.
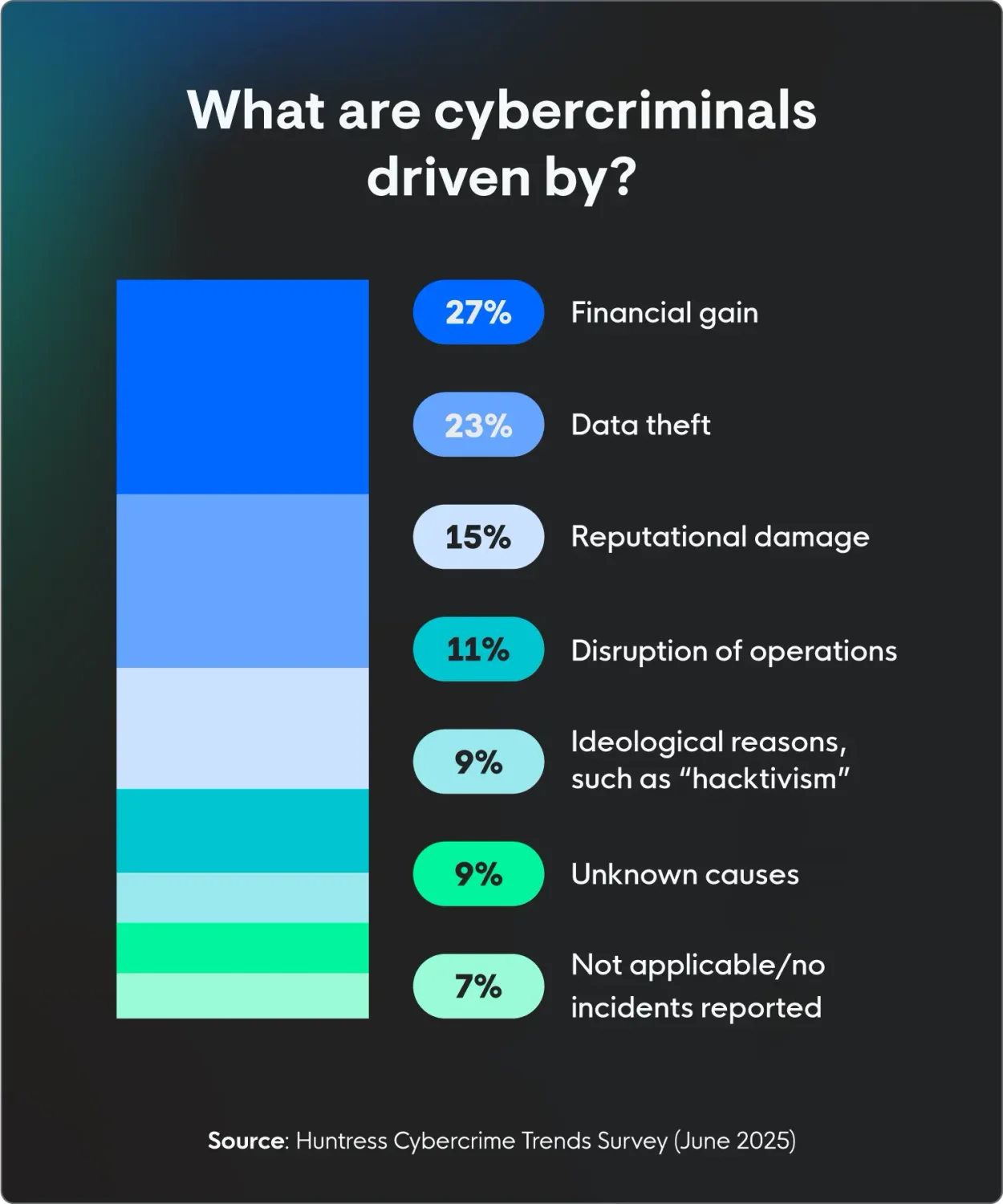
3. Financial gain is the suspected primary motivation of most cybercrimes
More than 1 in 4 (27%) American IT professionals think threat actors are mainly after money when targeting their companies. Other possible motivations include:
-
Data theft (23%)
-
Reputational damage (15%)
-
Disruption of operations (11%)
-
Ideological reasons, like “hacktivism” (9%)
And, of course, the IT professionals are right. When it comes to the most common cyberattacks, the main motivation is––you guessed it––money. Even when attackers access personal information, they typically do it to either gain access to financial records or to ransom the info they steal for money, leaving sensitive information up for sale.
4. About 1 in 4 businesses see up to $500,000 a year in losses from cybercrimes
More than 26% of respondents said that the estimated financial impact of cybercrimes each year was between $100,000 and $500,000. This includes costs related to recovery, downtime, fines, legal fees, and reputational damage leading to lost business. Cybercrime certainly pays well for attackers so they’re motivated to keep doing it.
In fact, the median salary for cybercriminals is $4,000 per job. According to Cybersecurity Ventures, the cost of cybercrimes is predicted to reach $12.2 trillion globally by 2031. That’s a massive paycheck for the cybercriminals.
Cyberattacks are getting more advanced and happening more often, which is a growing concern across every industry. Specifically, AI is helping attackers launch more advanced threats, like AI-generated deepfakes, such as the North Korean BlueNoroff attack. Attackers are also able to attack with wider nets, such as compromising one business to reach multiple downstream customers, like gaining access through remote monitoring and management (RMM) tools.
5. Nearly a quarter of organizations in the US don’t have cyber insurance
Despite the growing prevalence of cybercrimes and the potential for huge losses, Huntress’ 2025 Cyber Insurance Trends Report revealed that 22% of American organizations still lack cyber insurance.
The leading reason: the cost of coverage. But with cybercrimes costing organizations hundreds of thousands of dollars a year, the real question becomes, can they afford not to have coverage?
According to Embroker, the average cost of an annual cyber insurance plan in 2024 was between $1,200 and $7,000, with the scope of coverage varying depending on business size and specific needs. On the other hand, attacks can cost millions of dollars in direct and indirect expenses, from getting systems back up and operational delays, to the potential reputational damages.
Organizations should continue assessing their risk profile to decide if the several thousand dollars a year isn’t worth protecting themselves from potentially hundreds of thousands of dollars' worth of financial impact if a threat actor is successful.
6. Most IT professionals believe their company leadership is very prepared for cyber incidents
The good news is that most teams are on the same page regarding the gravity and risk of these cybercrime trends.
More than 3 in 5 American IT professionals (64%) believe that their non-IT leadership, like C-suite and board members, are very prepared to understand the technical implications and respond effectively to a significant cyber incident. No elevator pitch is necessary, as more board members are increasingly viewing cybersecurity as a business risk and are adding IT professionals to their boards.
But here’s where things get interesting: confidence drops slightly when looking at the actual security measures in place. More than half of respondents (57%) are very confident that current security measures can detect and mitigate an advanced, multi-stage attack that doesn't rely on traditional malware signatures.
7. IT professionals are most worried about AI threats
AI is coming for more than just our jobs—it wants our data, too.
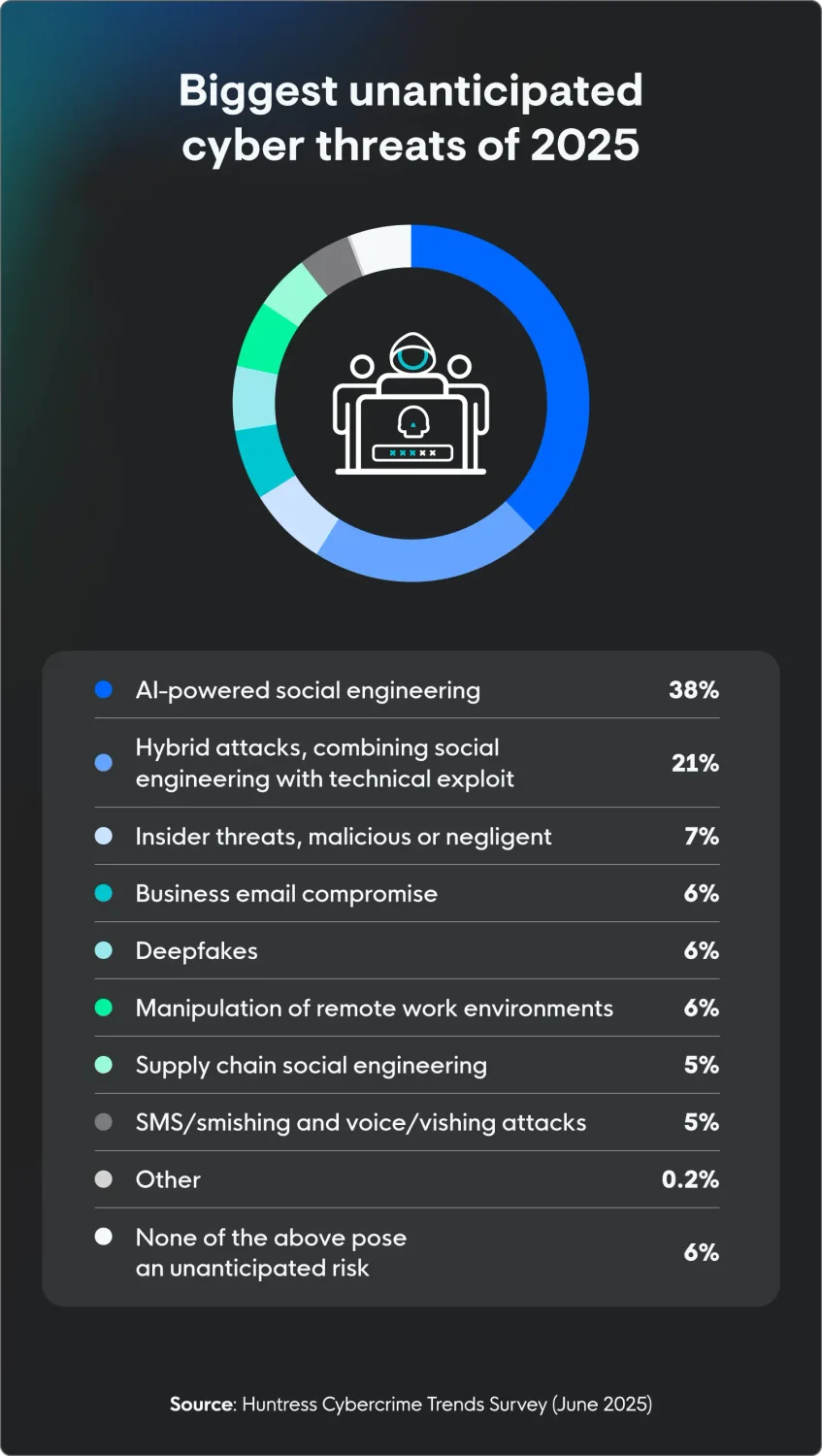
More than a third of IT professionals (38%) believe that, beyond phishing and similar threats, AI-powered social engineering poses the biggest unanticipated risk to their organization this year. Other threats include:
-
Hybrid attacks, combining social engineering with a technical exploit (21%)
-
Insider threats, malicious or negligent (7%)
-
Business email compromise (6%)
-
Deepfakes (6%)
-
Manipulation of remote work environments (6%)
And more than 2 in 5 IT pros (42%) think that the rise of AI-powered attacks will be the biggest game-changer in cybercrime over the next five years. This highlights concerns that while AI can streamline operations, it also has the potential to make cyberattacks more sophisticated and widespread.
8. Security awareness training is the most underfunded cybersecurity protection
When it comes to cybersecurity, there's a wide range of measures IT professionals feel aren't getting enough funding or resources, especially when you consider how important they are for the threats they're supposed to tackle.
The most common answer was security awareness training, which nearly 1 in 5 IT professionals (16%) rated as the most underfunded.
“Employee security training is a critical component of cybersecurity, especially if it's engaging and is performed on an ongoing basis,” says Lindsey. “It can help organizations educate employees on how to spot social engineering red flags, understand the best processes to take in the event of an incident, and most importantly, build a culture of security across the business.”
With Huntress, you can empower your employees to be part of the cybersecurity solution with security awareness training (SAT), giving you personalized phishing defense coaching based on real threats our security experts see.
11+ cybercrime statistics for 2025
Looking at recent data shows the many ways that the threat landscape continues to evolve. Here’s an overview of some of the top cybercrime trends and cybersecurity statistics from the past year:
-
Remote access trojans (RATs) are becoming more and more popular, with over 75% of remote access incidents last year utilizing them. (Huntress)
-
Threat actors are increasingly using infostealers, with almost 24% of attacks using them. (Huntress)
-
Education was one of the most targeted industries in 2024, accounting for 21% of attacks. (Huntress)
-
There was a 33% increase in reported losses from cybercrime between 2023 and 2024, for a total loss of more than $16 billion. (FBI)
-
People 60 years old and older report the most losses from cybercrime, accounting for almost $5 billion of the total $16 billion lost last year. (FBI)
-
The top three most reported cybercrimes in 2024 were phishing/spoofing, extortion, and personal data breaches. (FBI)
-
Cyber incidents are the most important business risk globally, with 38% of businesses highlighting these incidents as their top concern, higher than business interruptions, natural disasters, and legislative changes. (Allianz)
-
2025 marks the fourth year in a row that cyber incidents have been the number one concern among businesses. (Allianz)
-
Data breaches are the top cyber exposure concern for 61% of organizations globally. (Allianz)
-
Data breach expenses surged to $4.88 million worldwide in 2024, marking a 10% rise compared to 2023. (IBM)
-
Globally, the most expensive part of data breaches is the "detection and escalation" phase, which averages $1.63 million. (Statista)
How to protect against cybercrime
As cybercrime continues to evolve fast and threat actors look for new ways to gain access, organizations face a constant threat to their data, systems, and operations. In today's digital world, you have to have strong, multi-layered cybersecurity in place. This helps us proactively reduce risks and protect our valuable assets.
Here are some key recommendations for protecting your organization against cybercrime:
-
Invest in endpoint detection and response tools: Endpoint detection and response (EDR) tools are designed to detect malicious threats, investigate, and respond to them in real time.
-
Implement robust employee training: Regularly educate staff on cybersecurity best practices, including recognizing phishing attempts, strong cyber hygiene, and safe online behavior, as human error remains a leading cause of breaches.
-
Adopt a zero trust security model: Assume no user or device can be trusted by default, requiring strict verification for every access attempt, regardless of whether it originates inside or outside the network.
-
Maintain up-to-date software and systems: Regularly patch and update all operating systems, applications, and security software to fix vulnerabilities that attackers could exploit.
-
Utilize multi-factor authentication (MFA): Implement MFA for all accounts, especially those with privileged access, to add an extra layer of security beyond just passwords.
-
Enforce strong password policies: Require complex, unique passwords for all accounts and consider using password managers to help employees manage them securely.
-
Develop an incident response plan: Create a clear, actionable plan for detecting, responding to, and recovering from cyberattacks, including communication protocols.
Choose proactive solutions against cyber threats
While these cybercrime trends might seem scary, they really don’t have to be. To protect your organization and mitigate risks, consider investing in employee security awareness programs to slash the risk of accidental insider threats, cyber insurance to protect you if there is a cyber incident, and Security Information and Event Management (SIEM) systems to detect and mitigate threats.
"Businesses can use multiple layers of security controls to make sure that they cover all their bases - from MFA to protect accounts against compromise to security awareness training to help protect against social engineering attacks,” says Lindsey.
Huntress Managed SIEM uses proprietary Smart Filtering technology that only captures the data you need and cuts through all the noise. Our 24/7 expert-led monitoring helps you find and wreck elusive hackers.
FAQ
What are the current trends in cybersecurity?
In the past year, cybercriminals have updated their strategies, employing more sophisticated tactics and transforming ordinary tools into malicious instruments. This escalation includes leveraging generative AI to craft phishing content and produce deepfakes for social engineering schemes.
How often does a cyberattack happen in the US?
Threat actors try to gain access to systems as frequently as every 39 seconds.
Is cybercrime increasing?
Yes, cybercrime is consistently increasing year-over-year. The FBI's Internet Crime Complaint Center (IC3) reports increases each year—for example, they saw 9% increase in ransomware complaints between 2023 and 2024.
Methodology
The survey of 542 US IT professionals ages 18+ was conducted via Centiment Audience for Huntress between May 27 and May 28, 2025. Data is unweighted and the margin of error is approximately +/-3% for the overall sample with a 95% confidence level.