Fully Managed Threat Detection & Response
Leave it to Huntress to manage EDR, and monitor and respond to threats 24/7
Our 24/7 SOC detects and investigates threats, triages alerts, and responds with an industry-leading MTTR of 8 minutes and a false positive rate under 1%. All at an affordable price that doesn’t compromise quality.
No Credit Card Required


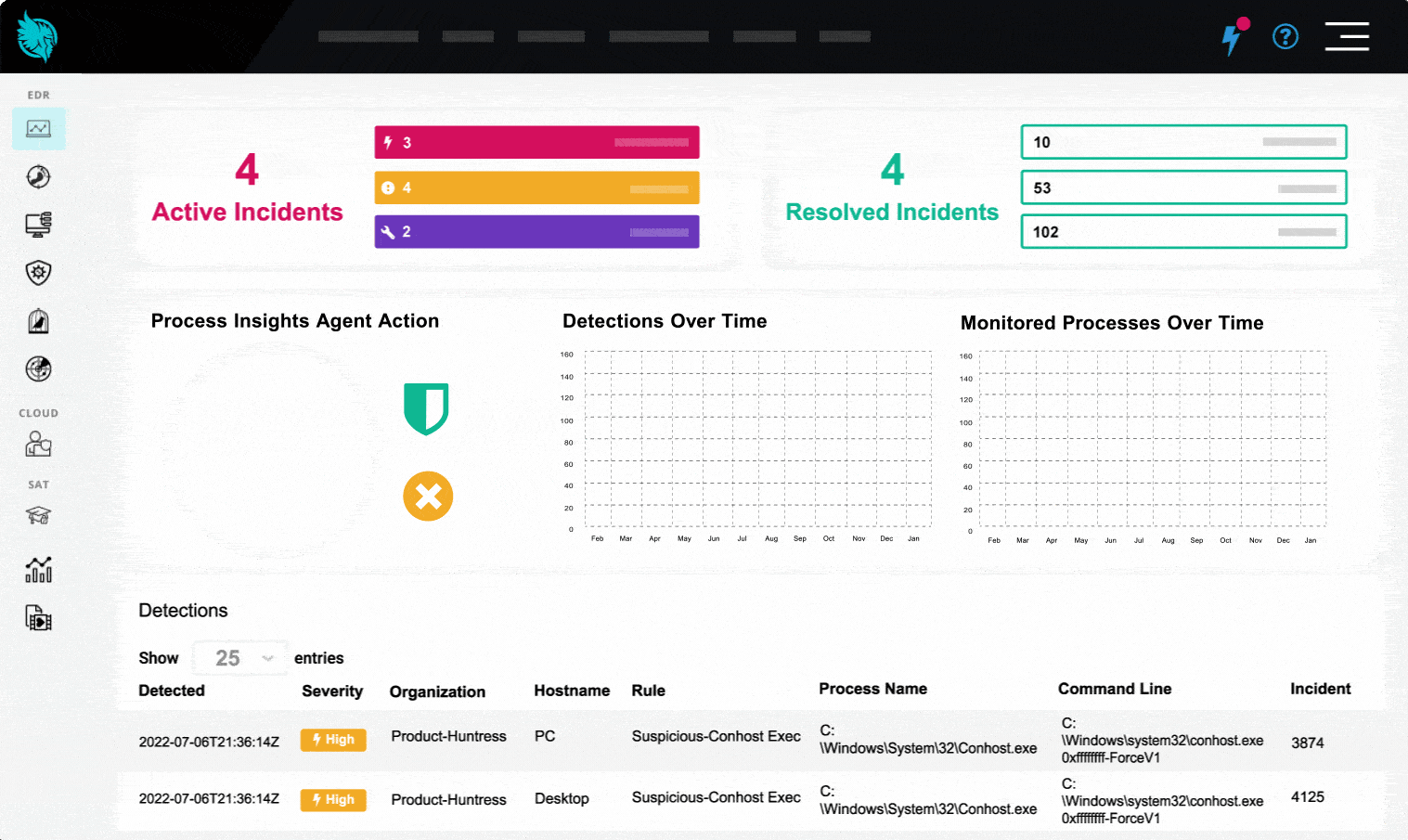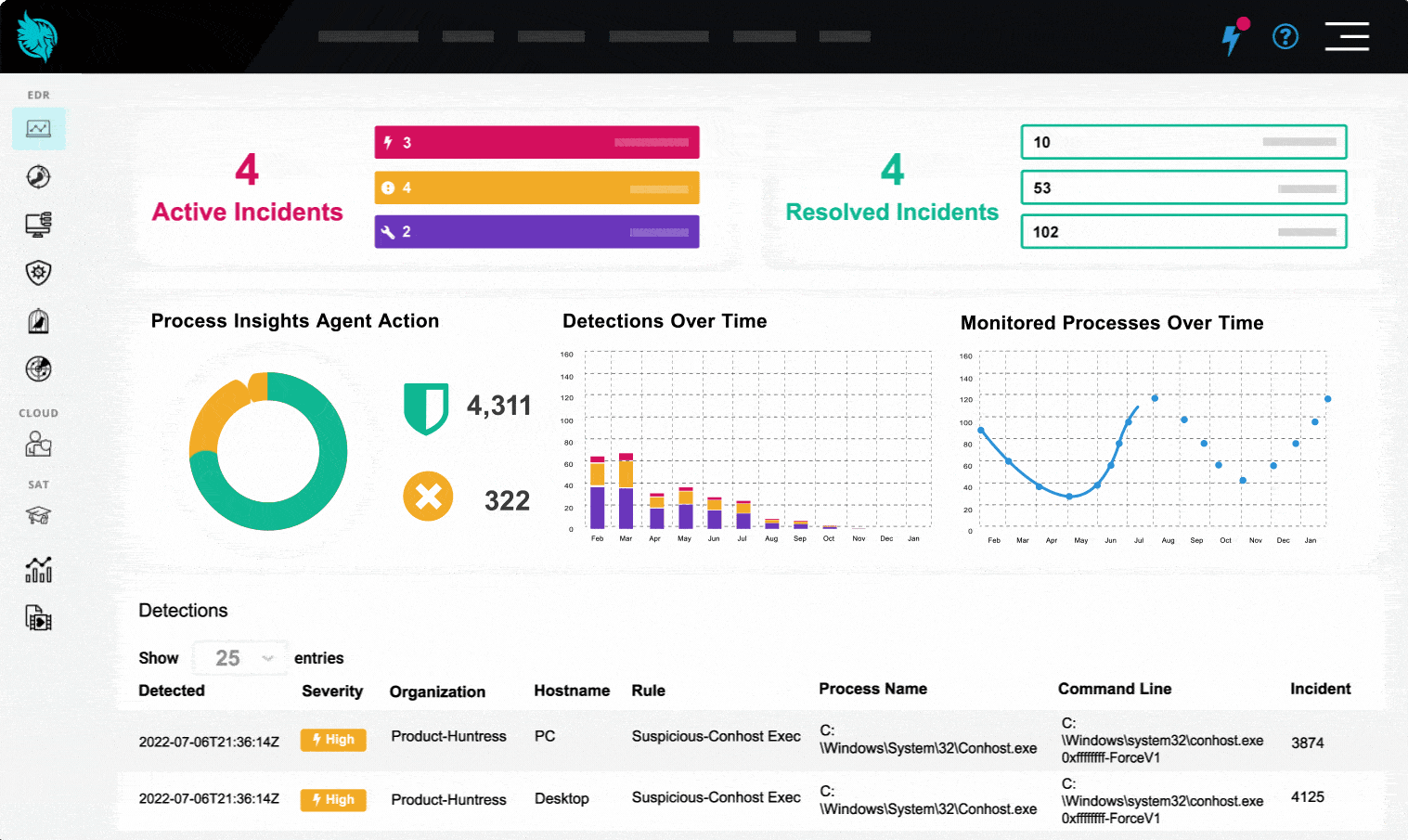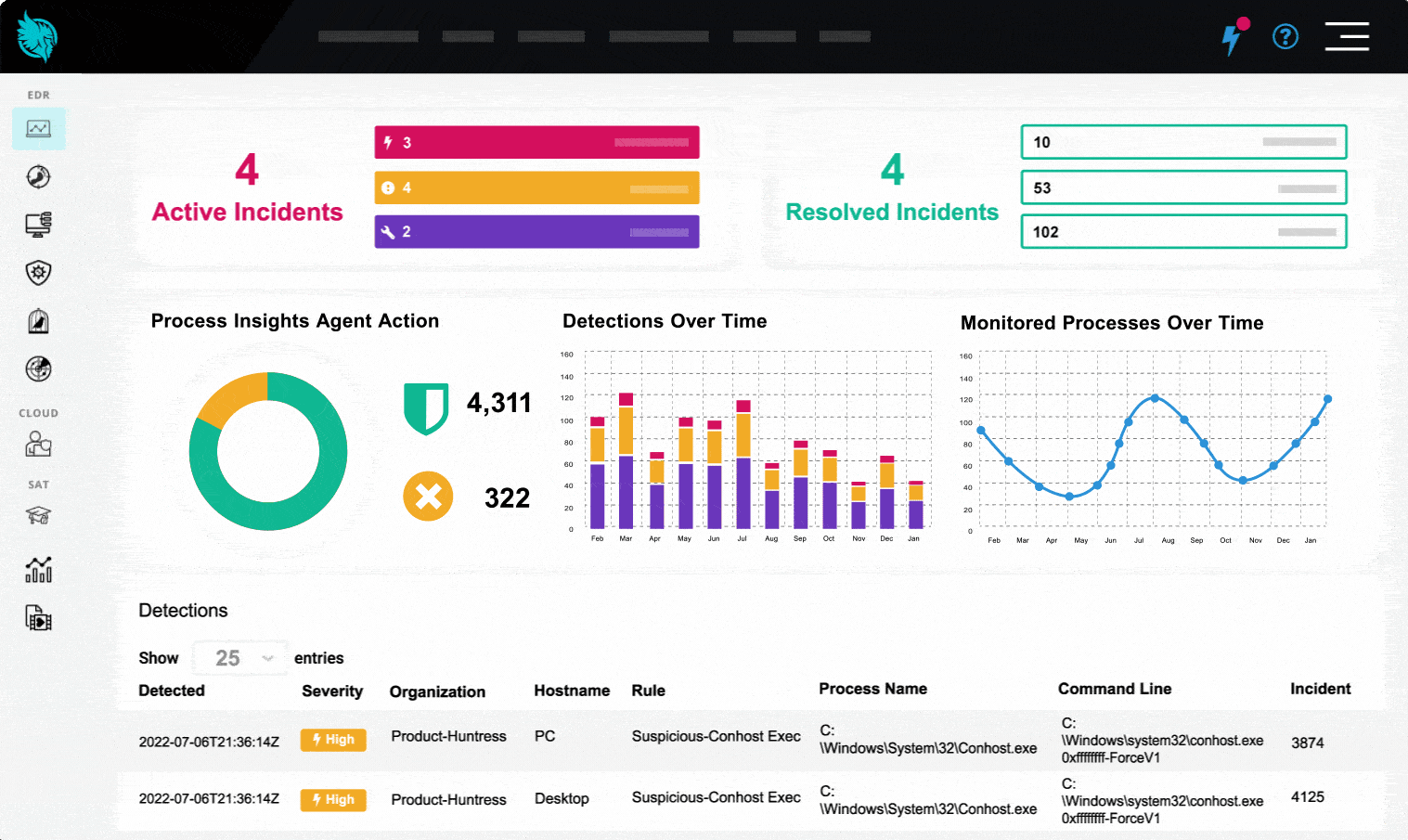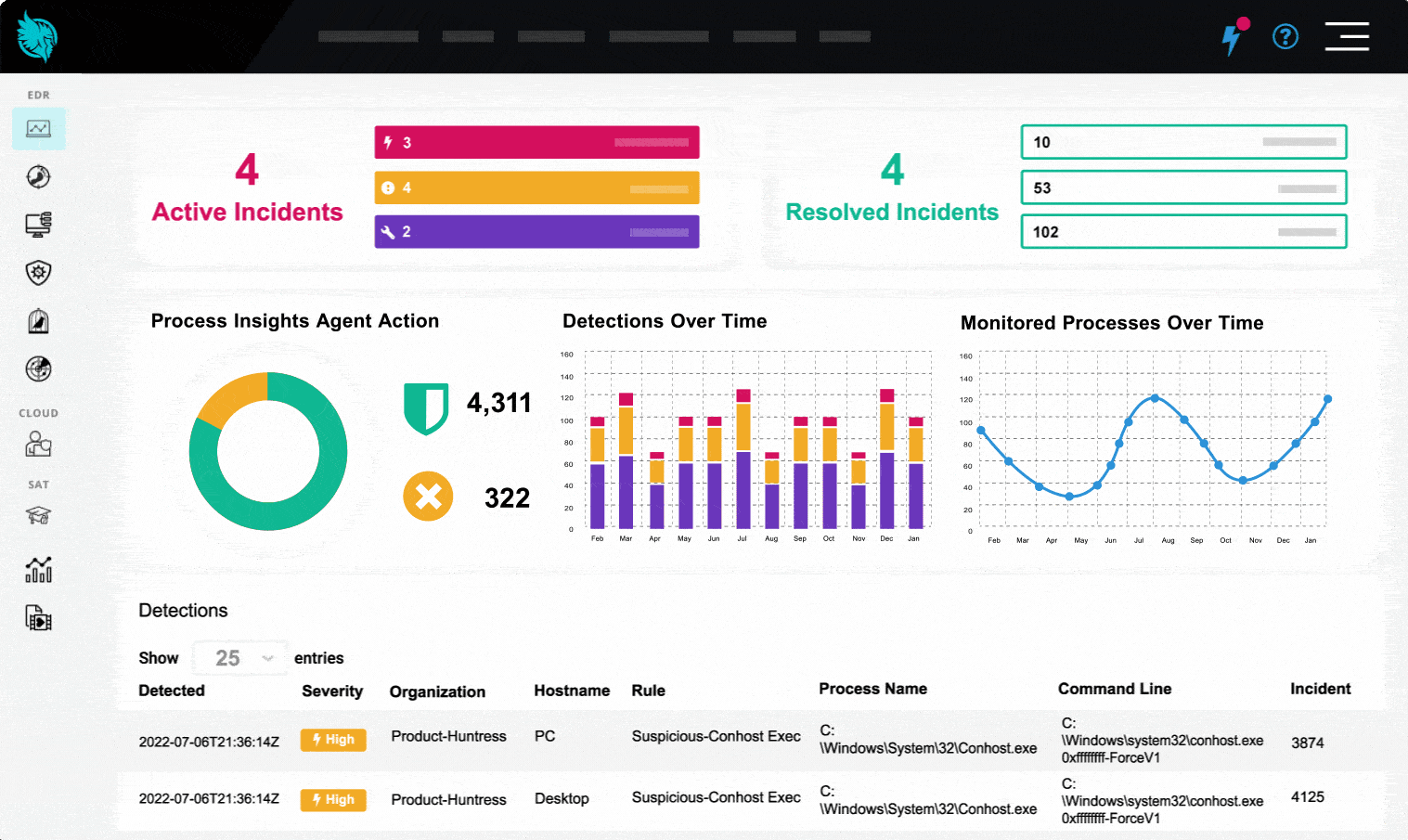

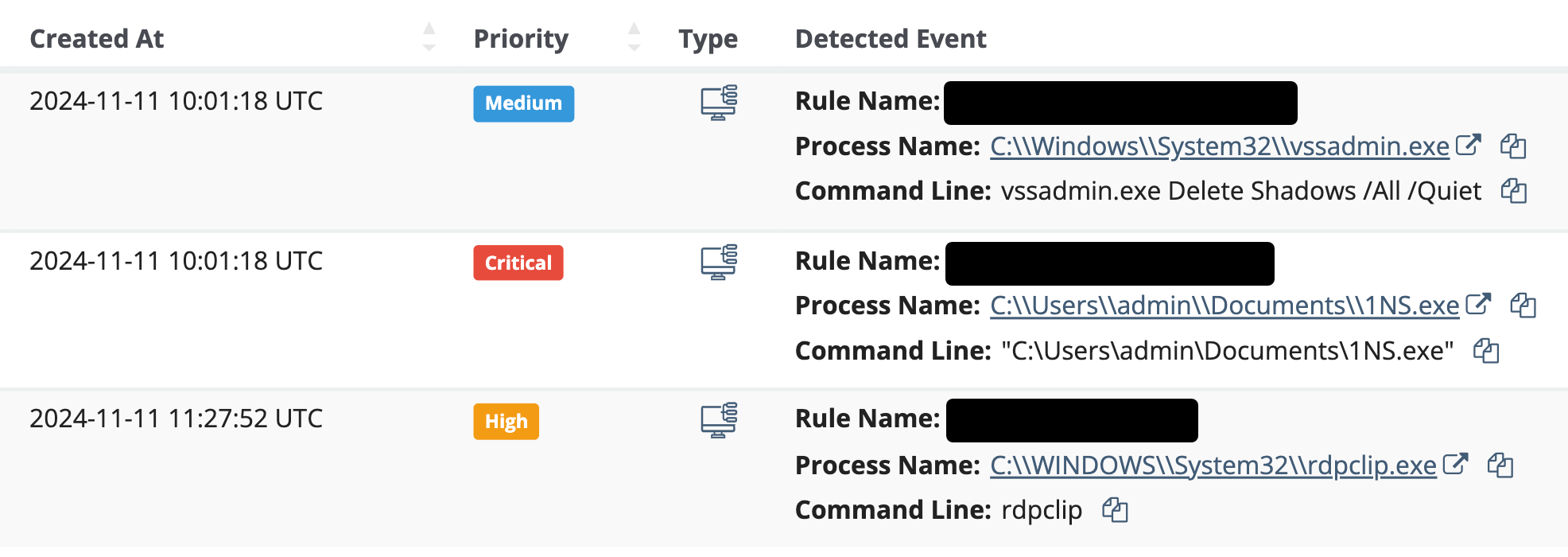
We Wreck Threat Actor Tradecraft Daily
How does your IT and Security team prevent hackers from:



Attackers change their tools all the time, but their techniques stay consistent—that’s why we focus on behavioral analysis to identify and stop shady hacker activity.

Like a canary in a coal mine, the Huntress SOC monitors small, lightweight files for early indication and detection of ransomware.

Remediate issues automatically or in a single click. You’ll have guidance written in a plain, jargon-free way to quickly get your systems back into a healthy state.

Swap out your current AV with the built-in version of Managed Microsoft Defender, and Huntress will manage it for you at no additional cost. Don’t want to use Defender? No problem. Huntress runs side-by-side with almost every AV.
The Huntress Managed Security Platform








See Managed EDR in Action