|
Key Takeaways
|
Remember when your biggest online privacy concern was your parents friending you on Facebook? Ah, simpler times.
Now, we're navigating a digital minefield where giants like Yahoo, Equifax, and, yes, Facebook have made personal data a hot commodity on the dark web. To make it on this list of the biggest data breaches, the attacks include both a massive number of records exposed and a wide range of data accessed by threat actors.
Keep reading to learn more about the biggest global data breaches, what they have in common, and how to prevent them at your organization.
The biggest data breaches in history
From big names in the credit card game like Capital One to shopping sites like eBay, anyone can fall victim to a data breach, especially if the right protections aren’t in place.
It’s important to note that while the term data breach is commonly used to describe any sort of incident involving data, this list actually includes three distinct types of data threats:
-
Data breaches: These are traditional, unauthorized infiltrations of a secure system.
-
Data leaks: This often refers to an unintentional exposure of data due to a misconfiguration issue, such as the storage of unencrypted passwords.
-
Data scraping: This is the automated extraction of large amounts of data, often publicly available, but done in a massive, unauthorized way that violates terms of service.
Here’s an overview of some of the largest data incidents of the past 20 years.
|
Breach |
Location |
Records exposed |
| |
|
|
Chinese Surveillance Network |
China |
4 billion |
WeChat data, bank details, Alipay profile information, phone numbers, home addresses, and behavioral profiles |
|
|
Yahoo |
Global |
3 billion |
Names, email addresses, dates of birth, phone numbers, and encrypted or unencrypted security questions and answers |
|
|
National Public Data |
US, UK, and Canada |
2.9 billion |
Full names, dates of birth, addresses, phone numbers, and Social Security numbers |
|
|
Real Estate Wealth Network |
United States |
1.5 billion |
Names, addresses, phone numbers, mortgage information, and tax identification numbers |
|
|
River City Media |
United States |
1.4 billion |
Email and IP addresses, full names, and physical addresses |
|
|
Aadhaar |
India |
1.1 billion |
Names, addresses, photos, phone numbers, emails, and biometric data |
|
|
Alibaba |
China |
1.1 billion |
User IDs and phone numbers |
|
|
First American Financial |
United States |
885 million |
Social Security numbers, bank account details, mortgage and tax records, wire transfer receipts, and driver's license photos |
|
|
|
Global |
700 million |
Names, email addresses, phone numbers, location, and gender |
|
|
Sina Weibo |
China |
538 million |
Names, usernames, phone numbers, location, and gender |
|
|
|
Global |
533 million |
Names, Facebook IDs, locations, dates of birth, and phone numbers |
|
|
Marriott International (Starwood) |
Global |
500 million |
Names, mailing addresses, phone numbers, email addresses, passport numbers, dates of birth, other travel details, and encrypted payment card information for a smaller number of people |
|
|
Adult FriendFinder |
Global |
412 million |
Usernames, email addresses, dates of last visits, passwords, and IP addresses |
|
14. |
MySpace |
Global |
360 million |
Email addresses, usernames, and passwords |
|
15. |
Exactis |
United States |
340 million |
Full names, email addresses, phone numbers, home addresses, plus the number, age, and gender of a person's children, their interests, and their estimated income |
|
16. |
NetEase |
China |
235 million |
Usernames, passwords, and security question answers |
|
17. |
Zynga |
Global |
218 million |
Usernames, email addresses, passwords, Facebook IDs, and phone numbers |
|
18. |
Court Ventures (Experian) |
United States |
200 million |
Names, addresses, dates of birth, and Social Security numbers |
|
19. |
Dubsmash |
United States |
162 million |
Usernames, email addresses, geographic locations, and passwords |
|
20. |
Equifax |
US, UK, and Canada |
159 million |
Names, Social Security numbers, dates of birth, addresses, and driver's license numbers |
|
21. |
Adobe |
Global |
153 million |
Names, email addresses, and encrypted passwords |
|
22. |
eBay |
Global |
145 million |
Names, encrypted passwords, email addresses, physical addresses, phone numbers, and dates of birth |
|
23. |
Heartland Payment Systems |
Primarily US |
130 million |
Credit and debit card numbers |
|
24. |
Capital One |
US and Canada |
100 million |
Names, addresses, dates of birth, self-reported income for applicants, Social Security numbers, and linked bank account numbers |
|
25. |
JPMorgan Chase |
United States |
76 million households and 7 million small businesses |
Names, addresses, phone numbers, and email addresses |
|
26. |
Home Depot |
US and Canada |
56 million |
Card numbers, expiration dates, and the three-digit Card Verification Value (CVV) codes |
|
27. |
Microsoft |
Global |
250,000 servers |
Business emails, passwords, and administrative privileges |
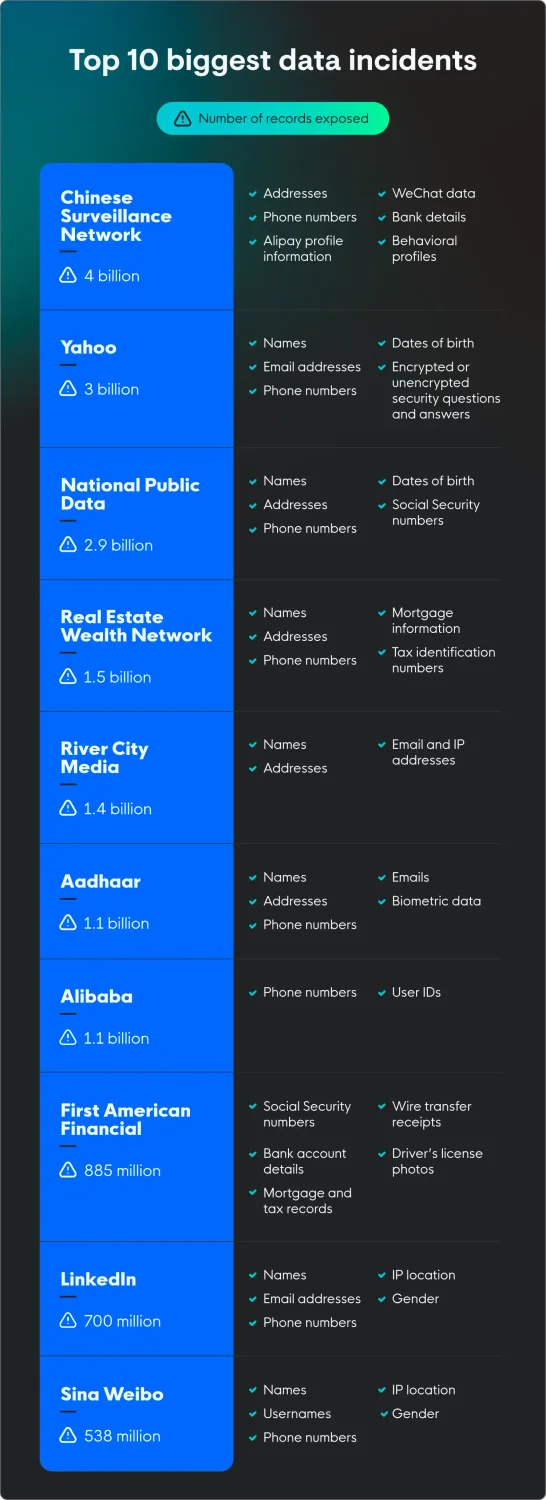
1. Chinese Surveillance Network
Date: June 2025
Location: China (primarily)
Records exposed: 4 billion personal records
Types of data: WeChat data, bank details, Alipay profile information, phone numbers, home addresses, and behavioral profiles
A massive data leak in China, discovered by Bob Dyachenko at SecurityDiscovery.com and the Cybernews research team, exposed a database of 4 billion records containing sensitive personally identifiable information (PII). The 631-gigabyte database was found without a password, making it easily accessible.
The researchers said they believed the data was likely intentionally gathered to build comprehensive profiles of nearly every Chinese citizen. The leak, which primarily affected Chinese users, is considered one of the largest data leaks to ever occur in China.
2. Yahoo
Date: August 2013
Location: Global
Records exposed: 3 billion user accounts
Types of data: Names, email addresses, dates of birth, phone numbers, and encrypted or unencrypted security questions and answers
Widely considered one of the biggest data breaches in history, the August 2013 Yahoo incident wasn’t disclosed until December 2016. The breach compromised all 3 billion of Yahoo's user accounts. The breach resulted in a significant financial and reputational loss for Yahoo, including fetching a lower price when sold to Verizon.
3. National Public Data
Date: December 2023
Location: US, UK, and Canada
Records exposed: 2.9 billion
Types of data: Full names, dates of birth, addresses, phone numbers, and Social Security numbers
The National Public Data (NPD) breach, which the company did not confirm until August 2024, was caused by a security lapse that allowed a threat actor to access and steal data. The compromised information was later put up for sale on a dark web forum, with the threat actor claiming it included the Social Security numbers of over 272 million people.
The breach was not a traditional hack, but a failure of security on the part of NPD and a sister site, which had a publicly accessible file containing plain-text usernames and passwords, including ones reportedly belonging to the site’s administrator. The incident ultimately led to numerous class-action lawsuits against NPD and their parent company, causing them to go out of business completely.
4. Real Estate Wealth Network
Date: December 2023
Location: United States
Records exposed: 1.5 billion
Types of data: Names, addresses, phone numbers, mortgage information, and tax identification numbers
The Real Estate Wealth Network (REWN) breach resulted from an unsecured database, totaling 1.16 terabytes, that was left open without a password. The exposed information was meticulously organized into categories like property history, motivated sellers, and tax records, and included sensitive details on millions of people, including celebrities and politicians.
A cybersecurity researcher discovered the vulnerability and notified REWN, who then secured the database. While it's unknown how long the data was exposed or if malicious actors accessed it, the leak highlights the severe risks of unprotected databases, including the potential for identity theft, fraud, and a significant invasion of privacy.
5. River City Media
Date: March 2017
Location: United States
Records exposed: 1.4 billion
Types of data: Email and IP addresses, full names, and physical addresses
The River City Media data leak involved a spam operation, where the spam email operators were masquerading as a legitimate email marketing firm. The data was left on a backup server without any password protection, making it accessible to anyone who knew where to look.
The leak was discovered by a security researcher—a hero, if you ask us—who found the open repository and then notified law enforcement and anti-spam organizations. The incident revealed the inner workings of a large-scale spam operation and served as a clear reminder of how easily sensitive data can be compromised thanks to simple configuration errors.
6. Aadhaar
Date: January 2018
Location: India
Records exposed: 1.1 billion
Types of data: Names, addresses, photos, phone numbers, emails, and biometric data
This breach came to light when a reporter from an Indian newspaper claimed to have bought access to a portal for a small fee, which allowed them to get the details of over a billion Aadhaar cardholders. While the Unique Identification Authority of India (UIDAI)—which manages Aadhaar—denied a breach of their central database, it was later revealed that the leak was likely due to vulnerabilities in the systems of third-party government websites and utility companies that had access to Aadhaar data.
The incident highlighted the risks associated with the centralized storage of sensitive data and raised significant concerns about identity theft and privacy for billions of Indian citizens.
7. Alibaba
Date: November 2019
Location: China
Records exposed: 1.1 billion
Types of data: User IDs and phone numbers
An employee of a third-party marketing firm illegally scraped over 1.1 billion records from Alibaba's Taobao shopping platform. The individual used a web-crawling tool to collect sensitive information, which was then used to serve the marketing firm's clients.
A Chinese court sentenced the developer and his employer to over three years in prison, though Alibaba maintained that their users incurred no financial losses.
8. First American Financial Corp.
Date: May 2019
Location: United States
Records exposed: 885 million
Types of data: Social Security numbers, bank account details, mortgage and tax records, wire transfer receipts, and driver's license photos
This major insurance provider’s data leak was caused by a website vulnerability that allowed unauthorized access to a vast database without any password or authentication. By simply changing a single digit in a URL, anyone could access a different customer's documents. A cybersecurity journalist discovered and reported the leak after a real estate professional stumbled upon the flaw.
The exposed data, some dating back to 2003, included a wide range of highly sensitive personal and financial information. While First American claimed there was no large-scale unauthorized access, the vulnerability allowed for a big potential exposure of personal information. The company later paid a $1 million penalty for violations of cybersecurity regulations.
9. LinkedIn
Date: June 2021
Location: Global
Records exposed: 700 million
Types of data: Names, email addresses, phone numbers, location, and gender
LinkedIn actually experienced two data breaches in 2021: the first in April, which exposed 500 million users, and the second in June, which exposed 700 million users. While these incidents were widely reported as data breaches, LinkedIn has consistently claimed they weren’t. Technically, they’re right, as they’re actually better described as data scraping incidents.
The company stated that no private data was compromised, but rather, the information was scraped from publicly viewable user profiles and aggregated with data from other websites. Although passwords and financial details weren’t part of the leaks, the exposed data is still a massive risk for users, as it can be used for sophisticated phishing scams, spam campaigns, and identity theft.
10. Sina Weibo
Date: March 2020
Location: China
Records exposed: 538 million
Types of data: Names, usernames, phone numbers, location, and gender
One of China's largest social media platforms, Sina Weibo’s 2020 data breach exposed the personal information of over 538 million users. A threat actor advertised the user database for sale on the dark web, claiming to have stolen it in mid-2019, selling it all for a relatively low price of about $250.
Sina Weibo initially attributed the leak to an API vulnerability, later admitting it was a data scraping operation exploiting a system loophole. While passwords were safe, phone numbers and names were exposed, increasing the risk of phishing and cybercrime for millions.
11. Facebook
Date: April 2019
Location: Global
Records exposed: 533 million
Types of data: Names, Facebook IDs, locations, dates of birth, and phone numbers
In 2019, Facebook (now Meta) experienced a major data exposure that affected over 533 million users across more than 100 countries. The personal data was scraped from the platform's contact importer feature. While the incident was widely reported in 2021 when the scraped data was posted for free on a hacking forum, the underlying vulnerability was exploited in 2019.
Facebook's official stance was that the incident was not a hack but rather data scraping, which involved collecting public information. However, once compiled into a single database, the information created a significant risk for users that they certainly didn’t “like.” Not to mention, Facebook didn’t even notify affected users. Maybe that’s the reason they still haven’t added a dislike button?
12. Marriott International (Starwood)
Date: September 2018
Location: Global
Records exposed: 500 million
Types of data: Names, mailing addresses, phone numbers, email addresses, passport numbers, dates of birth, other travel details, and encrypted payment card information for a smaller number of people
In a huge 2018 data breach, Marriott International announced that the guest reservation database of its Starwood hotel brand had been compromised. An investigation revealed that the attackers had been inside the Starwood network since 2014, two years before Marriott acquired the brand. The breach was only discovered after an internal security alert in September 2018.
The compromised data was extensive and highly sensitive. Personal information was stolen for approximately 327 million guests, while encrypted payment card information was also stolen for a smaller number of guests. It's suspected that the attackers may have also obtained the decryption keys.
13. Adult FriendFinder
Date: October 2016
Location: Global
Records exposed: 412 million
Types of data: Usernames, email addresses, dates of last visits, passwords, and IP addresses
The FriendFinder breach resulted from a major security vulnerability that exposed the private data of members, including those from other adult-based activity sites, if you catch our drift. The most sensitive aspect of the breach was the exposure of passwords, which were either stored in plain text or with weak encryption that was easily cracked.
Of course, that’s not the only sensitive part of this particular breach. For a site of this nature, the exposed data could lead to blackmail and public shaming. The incident also revealed that the company had failed to properly secure data from deleted accounts, with millions of "purged" records being part of the leak.
14. MySpace
Date: 2013
Location: Global
Records exposed: 360 million
Types of data: Email addresses, usernames, and passwords
The year was 2013. We Are Young by fun. was blasting on the radio, and we were young, sitting down to update our MySpace page after a long day. It wasn’t publicly revealed until 2016 that user data had been stolen when a hacker began selling it on a dark web marketplace. The stolen information was for all accounts created on the platform before June 11, 2013.
The scale of the breach was exacerbated by MySpace's weak security practices at the time. The passwords were stored poorly, which made them relatively easy for the attackers to crack. As a result, millions of MySpace users who had reused common passwords on other websites were put at risk of having those accounts compromised as well, leading to a wave of credential stuffing attacks after the data became public.
15. Exactis
Date: June 2018
Location: United States
Records exposed: 340 million
Types of data: Full names, email addresses, phone numbers, home addresses, plus the number, age, and gender of a person's children, their interests, and their estimated income
A security researcher discovered marketing firm Exactis’ leak, which was caused by a database left unsecured and publicly accessible on the Internet without any password protection. The exposed data was extremely detailed, containing hundreds of data points on individuals and businesses, including a huge amount of personal information collected by Exactis for marketing purposes.
While the breach didn’t include credit card numbers or Social Security numbers, the sheer depth of the exposed data made it a goldmine for malicious threat actors. The information could be used in highly convincing and targeted social engineering attacks, phishing scams, and identity theft.
16. NetEase
Date: October 2015
Location: China
Records exposed: 235 million user accounts
Types of data: Usernames, passwords, and security question answers
Chinese internet services company NetEase suffered a significant, but unconfirmed, data breach. While reports from security researchers showed that the company’s internal system was compromised, the breach was not officially acknowledged by NetEase, despite the compromised data being found for sale on the dark web.
The breach was a major concern for users, as NetEase's email service was widely used as a primary login for other popular Chinese platforms, including Weibo, WeChat, and QQ. The incident highlighted the dangers of using the same password across multiple platforms, a common practice that puts millions of users at risk of having their other online accounts hijacked.
17. Zynga
Date: September 2019
Location: Global
Records exposed: 218 million
Types of data: Usernames, email addresses, passwords, Facebook IDs, and phone numbers
It’s not always fun and games for online gaming platform Zynga. The company behind popular mobile games like Words With Friends and Draw Something suffered a major data breach in 2019. A Pakistani threat actor claimed responsibility for the attack, stating they had exploited a vulnerability in the company's systems.
While the passwords were reportedly stored securely, the incident still posed a serious risk to users who may have used the same password on other websites, making them vulnerable to credential stuffing attacks.
18. Court Ventures (Experian)
Date: October 2013
Location: United States
Records exposed: 200 million
Types of data: Names, addresses, dates of birth, and Social Security numbers
In 2013, a significant data breach involving Court Ventures, a company that had been acquired by Experian, a major credit bureau, came to light. A Vietnamese threat actor managed to pose as a private investigator and gain access to a database of personal information from a company called US Info Search, with which Court Ventures had a contract. Over the course of nearly a year, the attacker used this access to run a giant identity theft service on the dark web.
The breach was not a traditional attack but rather a failure of third-party verification and security. Experian claimed that the number of accessed records was much lower than the 200 million mentioned, but still in the millions. The incident highlighted a critical vulnerability in the data brokerage industry, where a simple lack of due diligence can expose a vast amount of private information.
19. Dubsmash
Date: December 2018
Location: Global
Records exposed: 162 million
Types of data: Usernames, email addresses, geographic locations, and passwords
While the video messaging service’s breach occurred in 2018, the stolen data was put up for sale on a dark web marketplace in early 2019, where it circulated more widely. The attack was part of a larger, sophisticated campaign that targeted multiple companies simultaneously.
While the breached passwords were reportedly stored using a cryptographic hash known as PBKDF2, the exposure of email addresses and other personal details still created a significant risk for users, especially if users had reused their Dubsmash password on other accounts.
20. Equifax
Date: 2017
Location: US, UK, and Canada
Records exposed: 159 million
Types of data: Names, Social Security numbers, dates of birth, addresses, and driver's license numbers
Equifax, one of the three major American credit reporting agencies, suffered a massive data breach that exposed the personal information of around 159 million Americans. The breach was caused by the company's failure to patch a known vulnerability in their web application software, Apache Struts. Threat actors exploited this flaw undetected for more than two months to gain access to the company's network and steal highly sensitive consumer data.
Because Equifax collects and maintains credit information, this breach was particularly concerning, as the data it holds is the key to a person's financial identity. The incident led to widespread public outrage, numerous lawsuits, a large settlement, and investigations by government bodies in the US and abroad.
21. Adobe
Date: October 2013
Location: Global
Records exposed: 153 million
Types of data: Names, email addresses, and encrypted passwords
Adobe’s 2013 data breach was initially thought to impact “only” 3 million users, but was later revealed to have compromised over 153 million accounts. Threat actors infiltrated the company's network, accessing tons of sensitive data. The breach was particularly severe because the attackers were not only able to steal user information but also gained access to source code for valuable Adobe products, including Acrobat, Photoshop, and ColdFusion.
What made the breach so dangerous was the weak security used to store the passwords; they were protected with unsalted SHA-1 hashes, which are easy for threat actors to crack. This vulnerability put many users at risk, especially those who had reused their Adobe passwords on other websites. In the aftermath, Adobe reset passwords for all affected accounts and faced lawsuits and a $1 million fine from multiple state attorneys general.
22. eBay
Date: 2014
Location: Global
Records exposed: 145 million
Types of data: Names, encrypted passwords, email addresses, physical addresses, phone numbers, and dates of birth
eBay’s attack happened in late February and early March 2014 but wasn’t detected by the company until May. Threat actors gained access to a database containing user credentials by exploiting a compromised employee account, stealing a substantial amount of customer data. eBay publicly disclosed the breach and, in a rare move for a company of its size, advised all users to change their passwords.
Again, having accessed this PII, the threat actors could use it for continued attacks like identity theft and phishing scams. The incident highlighted the dangers of both internal security lapses and the potential for a single compromised account to be a gateway to a huge data breach.
23. Heartland Payment Systems
Date: May 2008
Location: Primarily the US
Records exposed: 130 million
Types of data: Credit and debit card numbers
This breach of one of the largest credit card processors in the US was orchestrated by a sophisticated operation. The threat actors installed malware on Heartland's network to steal payment card data as it was being processed. This type of attack is known as a "sniffer" because it intercepts data in transit.
Although the breach was detected in 2008, it wasn't publicly disclosed until early 2009. The incident was a landmark case that exposed the vulnerabilities of payment card systems and led to heightened security measures, including a greater emphasis on encryption and compliance with the Payment Card Industry Data Security Standard (PCI DSS).
24. Capital One
Date: July 2019
Location: US and Canada
Records exposed: 100 million
Types of data: Names, addresses, dates of birth, self-reported income for applicants, Social Security numbers, and linked bank account numbers
The Capital One breach was carried out by a former Amazon Web Services employee who exploited a misconfigured firewall in the company's cloud infrastructure. The attacker was able to access and steal a vast amount of customer data, including credit card application information from 2005 to mid-2019. The hack was not a traditional brute force attack but rather an inside job that took advantage of a security weakness in the cloud environment.
The incident was a major blow to Capital One's reputation and highlighted the security risks associated with cloud migration. The breach resulted in an $80 million fine from the US Office of the Comptroller of the Currency and numerous lawsuits.
25. JPMorgan Chase
Date: June 2014
Location: United States
Records exposed: 76 million households and 7 million small businesses
Types of data: Names, addresses, phone numbers, and email addresses
JPMorgan Chase was the largest bank in the United States at the time of their 2014 data breach. The attackers gained access to the bank's network by exploiting a vulnerability in one of their servers that lacked multi-factor authentication. Once inside, they were able to compromise the data of customers who had used the bank's website, Chase.com, or its mobile app.
While the breach was a big one, its impact was somewhat mitigated by the fact that the most sensitive financial information, like account numbers, passwords, Social Security numbers, or dates of birth, wasn’t compromised. The incident was a serious wake-up call for the financial industry, highlighting the need for robust security measures in an increasingly digital world.
26. Home Depot
Date: April 2014
Location: US and Canada
Records exposed: 56 million
Types of data: Card numbers, expiration dates, and the three-digit Card Verification Value (CVV) codes
You can do it, and they helped themselves—the attackers, that is. They gained access to the company's network via a third-party vendor's credentials and then installed custom-built malware on the self-checkout systems in US and Canadian stores. This malware acted as a "sniffer," capturing credit and debit card information as customers swiped their cards. The attack went undetected for months, from April to September 2014.
While the breach didn’t compromise customers' PINs, the stolen data was enough for threat actors to create counterfeit credit cards and commit fraud. Home Depot's reputation suffered, leading to a large-scale security overhaul, including the rollout of chip-and-PIN technology in its stores. But now, doers get more done.
27. Microsoft
Date: January 2021
Location: Global
Records exposed: 250,000 servers
Types of data: Business emails, passwords, and administrative privileges
In early 2021, a series of cyberattacks exploited zero-day vulnerabilities in Microsoft Exchange Servers. Attackers, including the state-sponsored group Hafnium, gained full access to user data and administrative privileges on over 250,000 compromised servers globally, impacting government agencies and private companies.
The breach was particularly bad because the attackers installed web shells and backdoors on the compromised servers, allowing them to maintain long-term access even after Microsoft released patches. Stolen data included mailbox contents and other sensitive information, which was used for cyber espionage, crypto-mining, and ransomware attacks like DearCry.
What do the biggest data breaches have in common?
From how they start to their lasting effects, most large-scale data breaches share several things in common:
-
Scale: The biggest breaches impact millions or even billions of users, having huge short- and long-term consequences for businesses.
-
Causes: While there’s no one cause for all breaches, many are due to basic security failures. From misconfigured servers to unprotected websites and data scraping, threat actors generally take the path of least resistance.
-
Targets: As you’ve likely noted, the majority of these big data breaches targeted well-known organizations that keep a lot of PII. Threat actors focus on valuable, centralized data.
-
Consequences: Organizations experience different consequences because of data breaches, but the average cost of a breach is $4.4 million globally.
What’s the impact of a massive data breach on businesses?
Data breaches impact businesses in many ways. Aside from the obvious concerns about data and privacy loss, like identity theft and financial fraud, some effects go beyond just the actual breach of data.
In the short term, data breaches can cause:
-
Business interruptions
-
Financial losses
-
Regulatory fees
-
Insurance increases
In the long term, data breaches can cause:
-
Reputational damage
-
Lost business
-
A lack of trust
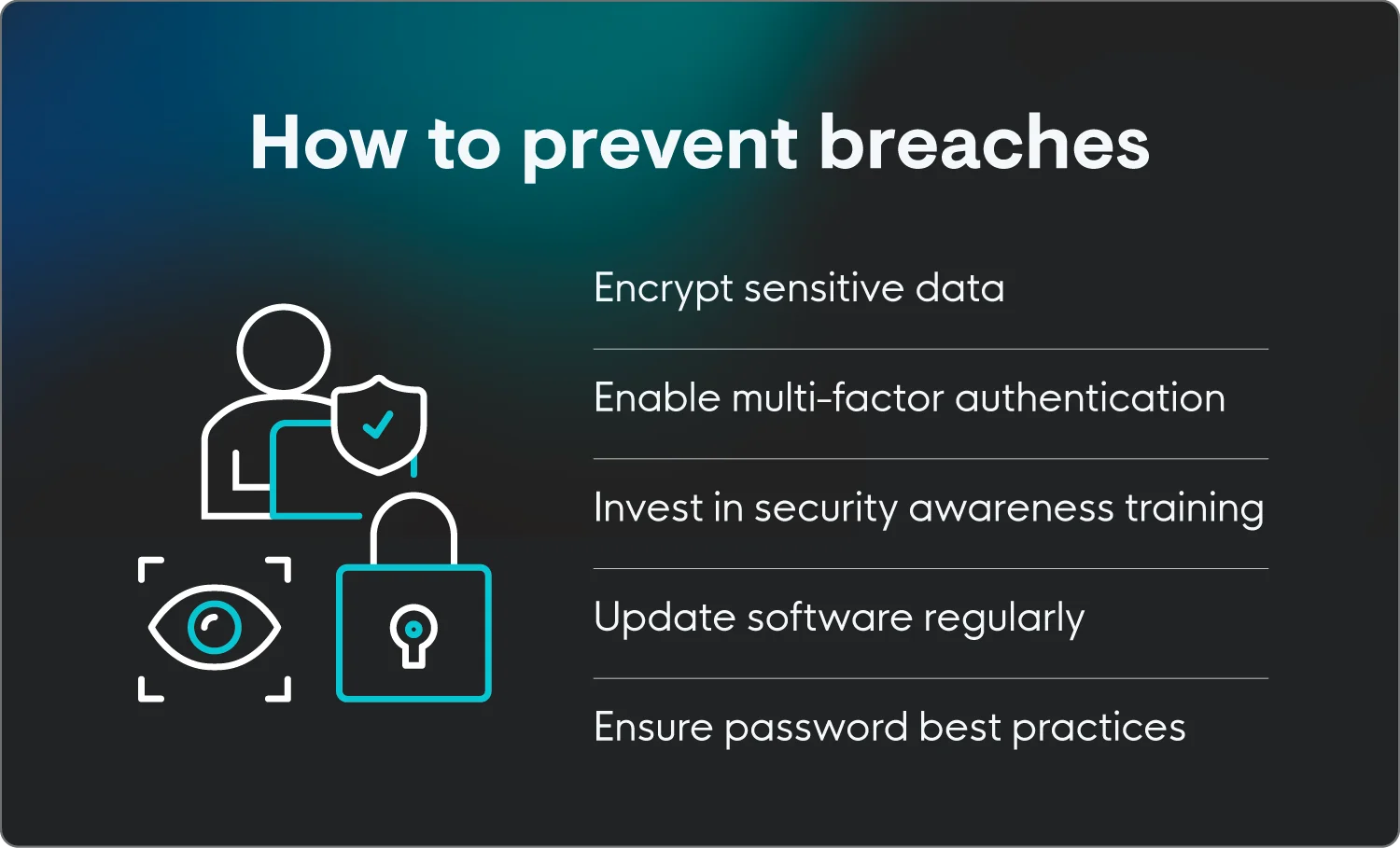
Tips for protecting against data breaches
While major companies often make headlines for big data leaks, the stuff that doesn’t make the news is all the work that goes on behind the scenes to prevent breaches from happening. Here are some ways to protect your organization:
-
Encrypt sensitive data: Use encryption to protect confidential information both in storage and in transit. This way, even if a threat actor gains access to your data, it’ll be unreadable without the decryption key.
-
Enable multi-factor authentication (MFA): MFA requires users to provide two or more verification methods to access an account. This adds a crucial layer of security, as it prevents attackers from gaining access even if they have stolen a password.
-
Invest in security awareness training. Many data breaches are caused by human error, like falling for a phishing scam or using weak passwords. Security awareness training teaches employees how to spot and avoid common threats.
-
Regularly update software: Threat actors often exploit known vulnerabilities in outdated software. To prevent this, make sure all operating systems, applications, and security software are updated with the latest patches as soon as they become available.
-
Ensure password best practices: Enforce strong password policies. This includes using long, complex passwords that are unique for each account. Consider using a password manager to securely store and generate passwords, which eliminates the need to remember them.
Protect your data from breaches
The biggest data breaches show that even the smallest oversight can lead to a big breach. But with the right preparation and vigilance, we can all become the first line of defense against the next big leak.
Threats can seem overwhelming, but with our in-depth understanding of how threat actors think, we know what to look for. Huntress gives you fully managed endpoint detection and response (EDR), so you've got 24/7 support from security experts ready to respond to threats.
FAQ
What is the largest data breach in history?
The largest data breach in history is actually multiple breaches, aptly named the Mother of All Breaches, or MOAB. The MOAB consisted of over 26 billion records and 12 terabytes of data.
It's important to note that MOAB wasn't a single new attack, which is why it’s not included in this list. Instead, it was a compilation of data from thousands of previous breaches, leaks, and privately sold databases that had been reindexed and made available in one place.
What causes 95% of all cybersecurity breaches?
Human error is the main cause of most cybersecurity breaches, including deliberate insider threats, poor password management, leaving devices unattended, and opening phishing emails.
What are the most recent data breaches?
One of the largest, most recent data breaches was the June 2025 Chinese Surveillance Network Breach, which exposed more than 4 billion records, including banking details and home addresses.