Email is a cornerstone of communication today, but it’s also a favorite attack vector of threat actors.
Phishing is a deceptively simple but highly effective technique used by threat actors to obtain sensitive information about a person, organization, or its computer systems. It's not driven by complex technology or elaborate hacking skills; instead, it preys on human psychology and behavior. Why? Because it works. Over 90% of all cyberattacks begin with phishing.
In this blog post, we will dive into the world of phishing and explore how phishing emails work, why they succeed in luring victims in, and most importantly, how you can protect yourself by spotting common red flags.
What is Phishing?
Phishing is a form of cyberattack in which an attacker attempts to trick individuals into revealing sensitive information, such as passwords, credit card numbers, or personal identification. This is typically done through deceptive emails, messages, or websites that impersonate trusted entities.
Social engineering attacks like phishing are regarded as one of the largest cyber threats organizations face today. They are fast, effective, and cannot be stopped with technology alone.
How Phishing Emails Work
To phish is to trick and deceive. In order to infiltrate an inbox or carry out their goal, threat actors will use phishing emails to play on a victim’s emotions and exploit their trust. This is done in a few distinct ways:
- Impersonation: Phishing emails often impersonate trustworthy sources, such as banks, well-known companies, and in target cases, trusted vendors or colleagues. Attackers can forge a sender's name and email address to appear legitimate at first glance, making it difficult to detect the deception.
- Urgent or Threatening Language: Phishing emails often create a sense of urgency or use threatening language to pressure recipients into taking immediate action. This can include warnings of account suspension, fraudulent activity, or the need to update personal information.
- Request for Personal Information: Phishing emails will request personal information, such as passwords, social security numbers, or credit card details. Legitimate organizations will never ask for such sensitive information via email.
- Suspicious Links and Attachments: Phishing emails contain links or attachments that, when clicked, may lead to malicious websites or download malware onto your device. These links often appear legitimate but redirect you to a fraudulent site designed to steal your information.
Examples of Phishing Emails
To better understand the dangers of phishing and social engineering, let's take a closer look at some common examples of phishing emails and the tactics they employ.
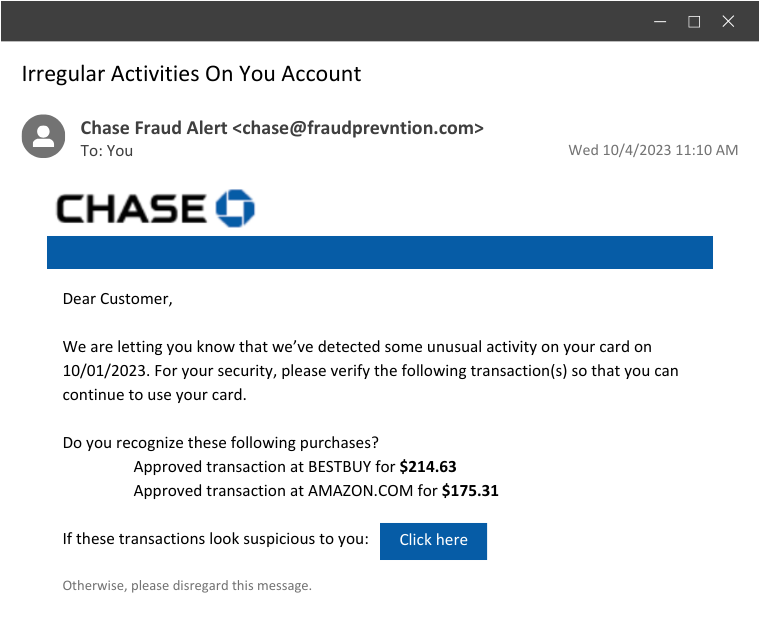
Example 1: The Fake Financial Alert
Almost as classic as the Nigerian prince, this tactic still manages to catch people off guard. In this scenario, a user receives an email that appears to be from their bank or financial institution, alerting them to suspicious activity on their account.
The email includes a link to report suspicious charges, but beware; it is a well-disguised trap.
How It Works:
- Knowing they didn’t spend hundreds of dollars at Best Buy and Amazon, the user would click on the link to “report” the charges. This would bring them to a malicious site that looks like Chase Bank, where they would enter their banking login details… straight into the attacker’s hands.
Social Engineering Tactics Used:
- Fear and urgency play a significant role here. By impersonating a trusted source, the threat actors count on the user’s anxiety about their finances and the fear of losing money to fraudulent charges. They apply pressure, making them believe that immediate action is required to protect their assets.
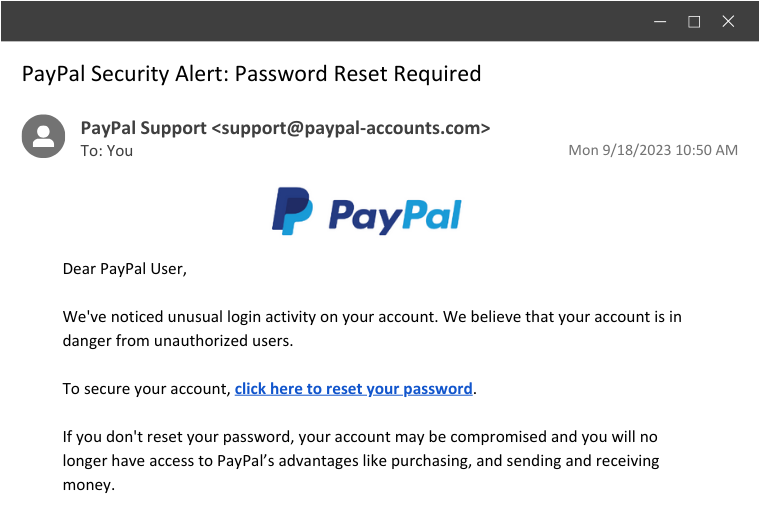
Example 2: The PayPal Password Ploy
Another common example is when a user receives an email claiming there's been unusual login activity on their PayPal account. To secure your account, they simply have to reset their password by clicking a link. Seems like a legit security measure, right? Not quite.
How It Works:
- Similar to the first example, this scenario is phishing for login credentials. The link would bring the user to a seemingly legitimate PayPal login page. Under the guise of resetting their password, they would be prompted to enter all their current login information, which the threat actor will swiftly take and use to take over their account.
Social Engineering Tactics Used:
- In this case, fear is the driving force. Fear of a compromised PayPal account is a nightmare for many users. Additionally, the email convincingly impersonates PayPal, making it seem like a genuine security alert from the platform.
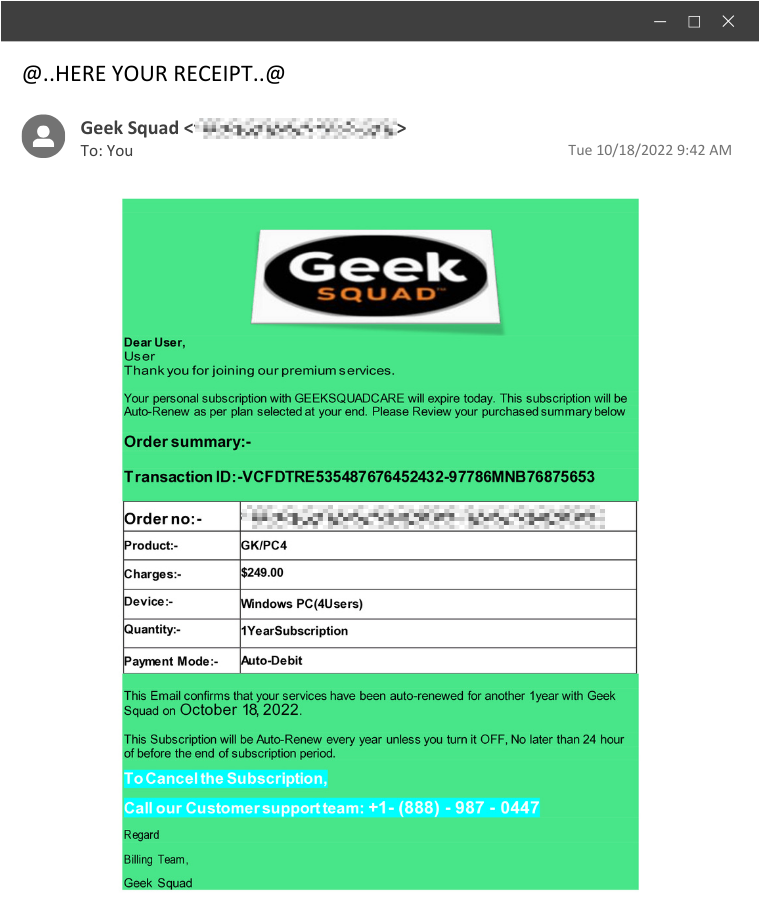
Example 3: The Geek Squad Fraud
Here, we encounter a unique tactic—one that the Huntress SOC actually encountered. Instead of the typical malicious link, this phishing email almost uses reverse psychology and provides a phone number to call.
How It Works:
- When the victim dials the provided phone number, the adversary is on the other end of the line and convinces them to run an installer. In this instance, the installer is a ScreenConnect installer, which will allow the adversary remote access into that environment.
Social Engineering Tactics Used:
- This preys on trust and urgency. With the threat of auto-renewal, the user is forced to act fast. And since they are calling a provided number instead of clicking a link, they may believe they're receiving legitimate technical support.
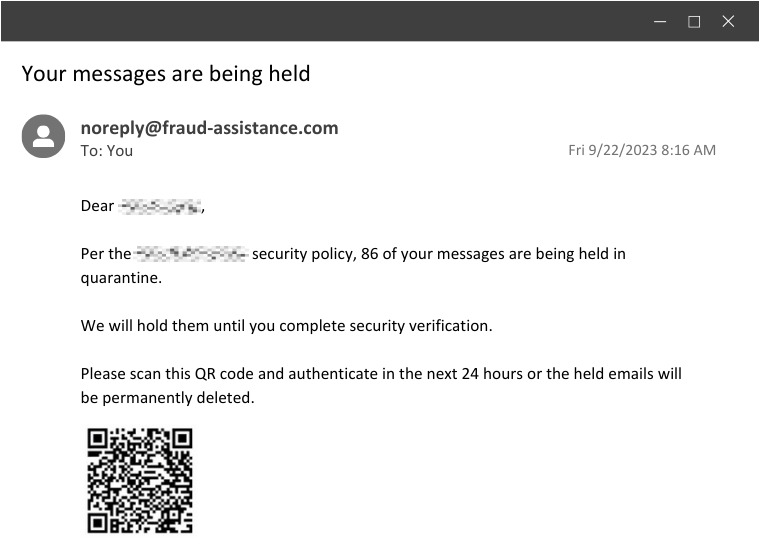
Example 4: The QR Code Con
This is a relatively newer tactic that leverages the use of QR codes in order to bypass URL scanning.
In this example, the email notifies the user that their messages are quarantined until they scan the code to complete a security verification.
How It Works:
- Instead of a malicious link, this uses something that’s harder to pre-scan or hover over: a malicious QR code. Upon scanning, it redirects the user to a malicious website or downloads malware onto their device.
Social Engineering Tactics Used:
- This creates a sense of urgency, but it also takes a modern twist on using suspicious links. With QR codes being normalized in restaurants and other familiar places, the user likely won’t think twice before scanning—that’s exactly what these clever attackers are banking on.
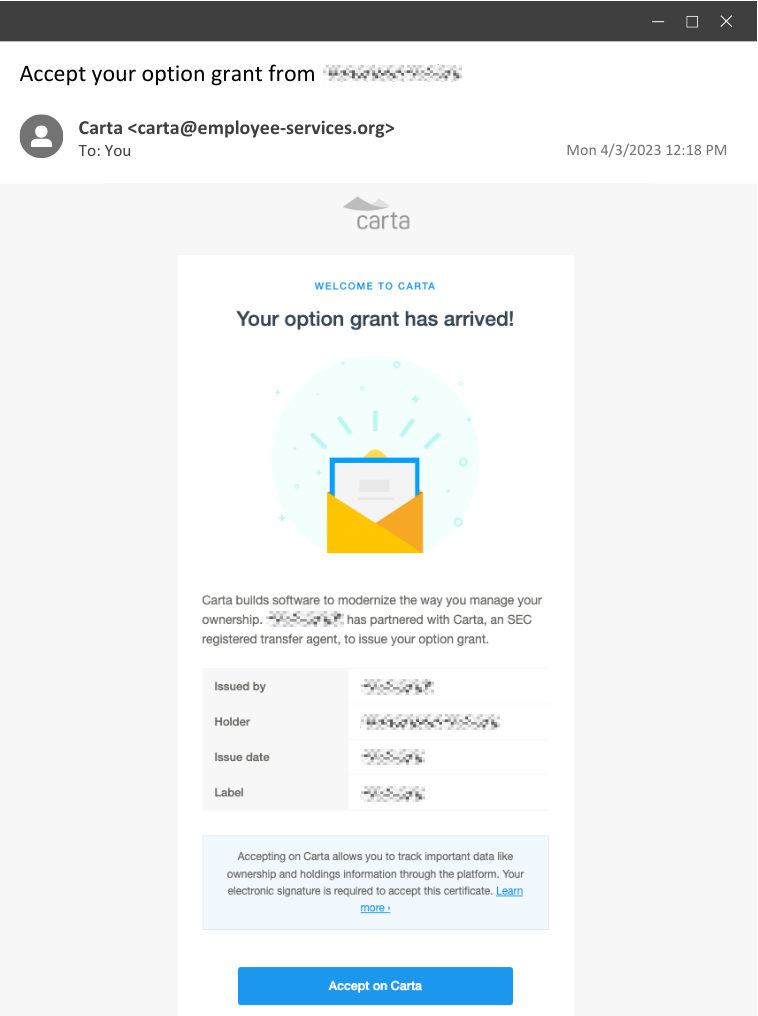
Example 5: The Stock Option Swindle
This example takes a more targeted approach. It masquerades as a stock option grant from the user’s workplace, enticing them to click a link to claim their options. This can be especially effective when targeting employees of a startup.
Actually, this is a real phishing simulation we’ve sent as part of Huntress’ internal security awareness training. And truth be told, this one has been by far the most effective. 😈
How It Works:
- If a threat actor were behind this, typically, the aim would be to steal user credentials or download a malicious payload once the button is clicked. But since this was a simulated phishing test as part of security awareness training, the user would be taken to a benign website where this message would appear… and hopefully, they would learn from their mistakes.
Social Engineering Tactics Used:
- Trust and timing are the driving factors here. Trust is abused by impersonating an organization that employees are familiar with, and the timing is another factor because these emails are typically sent after actual, real stock options are granted to employees.
How to Spot A Phishing Email
Now that you understand how phishing emails work and what they could look like, the next step is knowing how to identify common red flags to protect yourself. Here are some key indicators to watch for:
- Check the sender. Verify the sender's email address and name. Be cautious if it doesn't match the official domain of the organization or if there are typos or special characters in those fields.
- Beware of urgency. If the email creates a sense of urgency, especially regarding sensitive information or immediate action, it might be a phishing attempt.
- Don't click on suspicious links. Hover over links to reveal the actual URL before clicking. You can also use tools like Domain Dossier to learn about domain names and IP addresses, ICANN to see who domains are registered to, and urlscan.io to show a screenshot of the page you’d land on if you were to follow a link.
- Double-check requests for personal information. Be cautious if an email asks for sensitive information via email. Always verify through official channels.
- Look for spelling and grammar errors. Typos, awkward phrasing, and grammatical mistakes are often tell-tale signs of a phishing attempt.
Huntress Managed SAT
Smishing Simulation
Phishing doesn't just happen over email. See how Huntress SAT trains employees to spot SMS-based attacks too—with a free simulation preview.
Knowledge is Power
Although phishing is a common attack method, the tricks and tactics that threat actors use are always improving, which means that users won’t always recognize the common red flags. That’s where security awareness training comes in.
Security awareness training is no longer an “as-needed” or “nice to have” thing; it's a necessity. Regular, consistent training ensures users stay ahead of the tactics employed by cybercriminals, keeping defenses sharp and information secure.
In a world where phishing emails will continue to be a favored weapon of threat actors, your best defense is knowledge. Make it a habit to educate yourself, share this knowledge with those around you, and become an invaluable line of defense against today’s clever hackers.
Looking for a fun and effective security awareness training solution? Check out Huntress Security Awareness Training!