(Doctor Evil voice:) One million dollars.
It’s actually multiple millions when it comes to the average cost of a data breach, including both direct and indirect costs. But because of those indirect and long-term costs, there’s actually no way to know how high the total costs of the biggest data breaches may be. Perhaps, billions of dollars?
Keep reading to learn more about the costs of data breaches, the key factors that impact the dollar amount, and how to protect your organization.
Key takeaways
Below are some key findings for data breaches and their costs
-
Data breach statistics show that the average cost of a data breach has reached $4.4 million globally. (IBM)
-
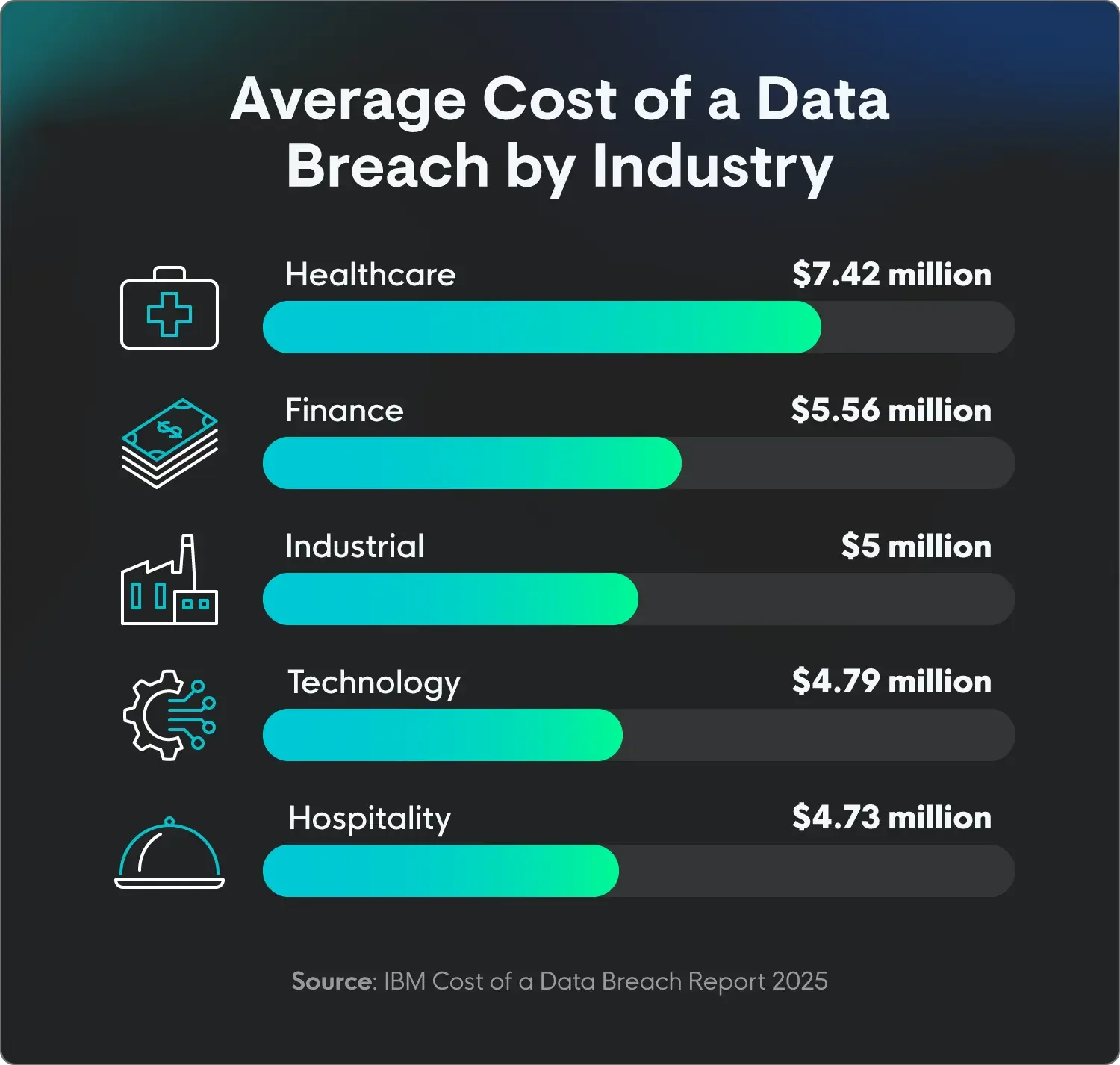
Data breaches are most expensive in the healthcare and finance industries, reaching $7.42 million and $5.56 million, respectively. (IBM)
-
Data breaches are typically covered for about 80% of organizations that have cyber insurance. (Huntress)
-
A third of IT professionals in healthcare rate data breaches as their top concern. (Huntress)
-
Nearly a quarter of cyber incidents used info stealers to extract data. (Huntress)
-
Cyberattacks cost 27% of organizations upwards of $500,000 per year. (Huntress)
Cost of a data breach by industry
Data breach costs vary by industry mainly because of the type of data they handle and the regulations they have to follow. Industries like healthcare and financial services regularly have the highest average breach costs because they collect and store highly sensitive and valuable data, like medical records and financial information.
This data is a prime target for threat actors, and a breach can lead to massive fines from strict regulatory standards like HIPAA, along with other data recovery costs and legal fees. Industries that handle less sensitive data or operate under less strict regulations, like retail or hospitality, generally have lower breach costs.
|
Average cost of a data breach by industry | |
|
Industry |
Average cost |
|
Healthcare |
$7.42 million |
|
Finance |
$5.56 million |
|
Industrial |
$5 million |
|
Technology |
$4.79 million |
|
Hospitality |
$4.73 million |
|
Education |
$3.8 million |
|
Retail |
$3.54 million |
|
Source: IBM Cost of a Data Breach Report 2025 | |
Cost of a data breach by location
The cost of a data breach varies by location for many reasons. This can include factors like:
-
Regulatory fines: Often the most significant factor, different countries and regions have distinct data protection laws with varying fines and penalties.
-
Local costs: A country's economic landscape influences the cost of a breach, like hiring forensic investigators, legal counsel, and public relations experts.
-
Cybersecurity infrastructure maturity: Locations with a cybersecurity skills shortage may face higher hiring and retention costs, as well as those with fewer advanced technologies like AI and automation.
-
Competition: In areas where businesses are highly competitive, any downtime or reputational damage caused by a data breach can lead to lost customers and a lack of new customers—and, ultimately, higher costs.
|
Average cost of a data breach by location | |
|
Location |
Average cost |
|
Globally |
$4.4 million |
|
United States |
$10.22 million |
|
Canada |
$4.84 million |
|
United Kingdom |
$4.14 million |
|
Germany |
$4.03 million |
|
France |
$3.73 million |
|
Japan |
$3.65 million |
|
Source: IBM Cost of a Data Breach Report 2025 | |
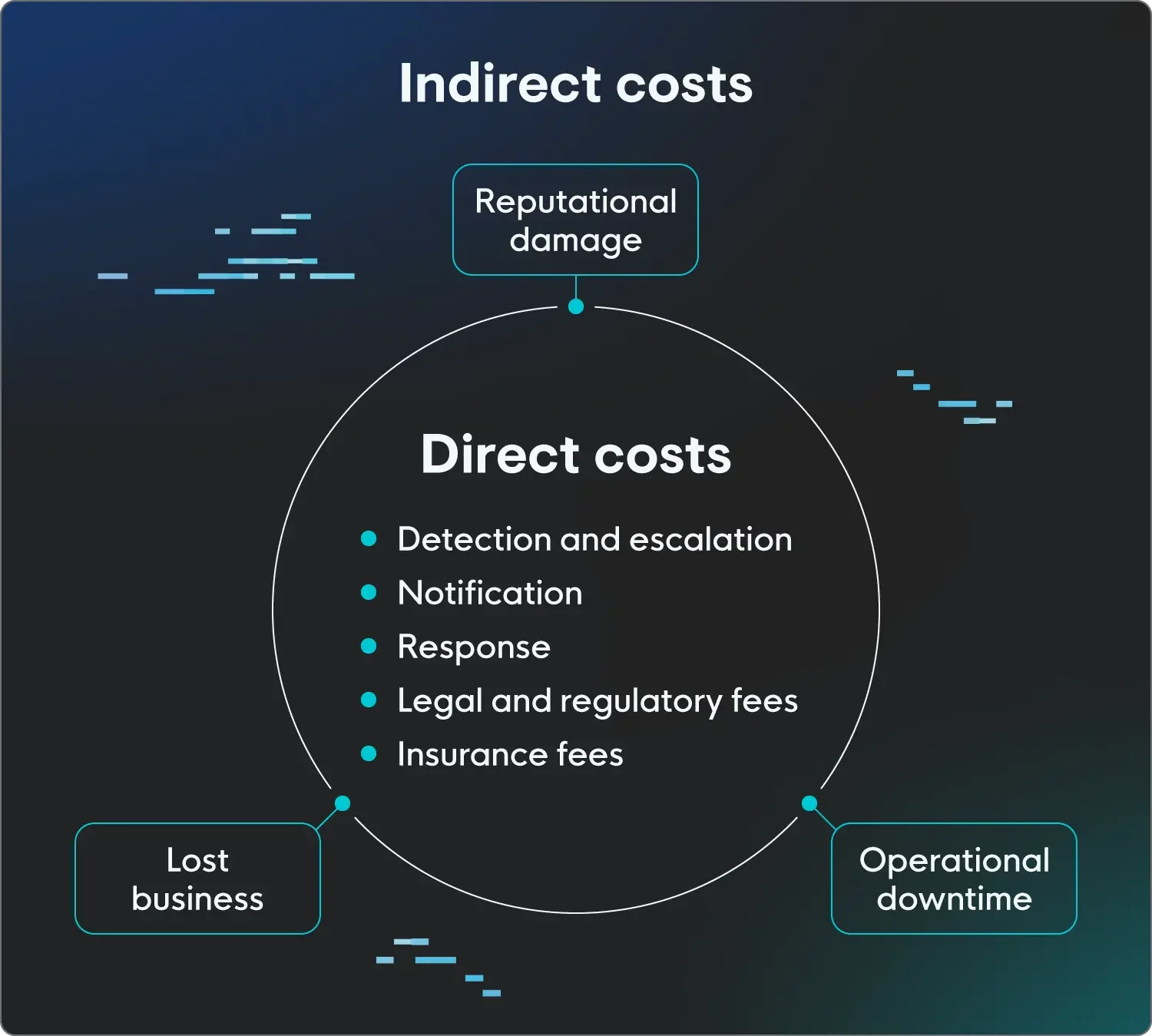
Components of data breach costs
When looking at the cost breakdown of a data breach, many different things contribute to the total cost. Some of them are easily calculable, while others…not so much. This is the distinction between direct and indirect costs of a data breach.
Learn more about the true cost of a cyberattack.
Direct costs
The direct costs of a breach are the most obvious ones. These include the cost of detecting, shutting down, and recovering from a breach. They’re often also the immediate, short-term consequences of the breach, like:
-
Detection and escalation: These costs are a part of the immediate response to a data breach. This includes hiring forensic experts to investigate the attack, conducting internal and external audits to understand the scope of the breach, and engaging a crisis management team to guide the response.
-
Notification: Expenses include sending notices, staffing call centers, and providing credit monitoring/identity theft protection for affected individuals. These costs can increase significantly based on the number of people impacted and relevant jurisdictional laws.
-
Post-breach response: Incident response includes both detection and action, as well as what happens next, like releasing public statements, improving defenses, and any other type of damage control.
-
Legal and regulatory fees: Different regions and industries have varying regulations. When a breach happens, they may be in breach of those regulations (get it, in breach?) and need to pay a fine. For example, for serious breaches, the General Data Protection Regulation in the European Union can impose fines of up to 4% of a company's total worldwide annual revenue or €20 million, whichever is higher.
-
Insurance fees: Cyber insurance, like other types of insurance, usually requires a deductible payment. More than that, rates are impacted by claims, so any cyber incident will play a role in deciding future renewal rates.
Indirect costs
Indirect costs of a data breach are harder to measure and may have longer-lasting impacts. These costs include:
-
Reputational damage: Ultimately, the biggest indirect cost, which cascades into the others, is reputational damage. Regardless of what caused the breach, current and potential customers will question the company’s ability to protect their information.
-
Operational downtime: While you can calculate the direct costs of downtime, the longer-term effects, like losing clients and new business due to that downtime, are difficult to put into numbers.
-
Lost business: Whether your business loses customers temporarily due to downtime or permanently, lost business is considered an indirect cost because it can be difficult to measure. Are those customers who would’ve churned anyway? It’s also hard to figure out the cost of losing out on new business because of a breach.
Key factors that influence data breach costs
The costs of a data breach aren’t uniform—they’re influenced by many things. We’ve already talked about how industry and location impact costs, but here’s an overview of some other factors that may play a part:
Existing protections
The cybersecurity protections already in place play a role in both how quickly the threat is detected and the next steps. An organization with no existing protections will take longer to detect the threat and have higher costs associated with mitigating and preventing future threats.
Speed to detection
The longer a threat actor has access to a system, the more damage they can cause. Breaches that are identified and contained quickly cost much less than those that go unnoticed for extended periods. This emphasizes the value of having a strong incident response plan and using security tools like endpoint detection and response to speed up detection and containment.
Attack methods
The way an attack happens plays a major role in its final cost. For example, breaches that start with credential theft or compromise are among the most expensive. Once an attacker has legitimate login information, they can move freely within a network, access more sensitive data, and remain undetected for longer periods.
Similarly, business email compromise (BEC) attacks, where an attacker impersonates a companindiry executive, often lead to significant financial losses, as they can trick employees into making fraudulent wire transfers.
Size and type of data breach
The sheer number of records stolen and the type of data they include directly impact costs. Breaches involving a larger number of records are almost always more expensive due to the increased costs of notification, credit monitoring, and potential lawsuits.
Breaches involving highly sensitive data like personally identifiable information (PII) or intellectual property are also more costly than those that expose less critical data, like generic contact information or other publicly accessible data.
Reputational damage
A huge part of a data breach's cost is tied to lost business. This includes customer turnover, loss of new business, and the time and resources spent restoring the company's reputation.
After a breach, customers may lose trust and switch to competitors, leading to a long-term decline in revenue. This indirect cost often outweighs the more immediate expenses like fines and legal fees, especially over time.
How do data breaches happen?
Data breaches are usually the result of malicious attacks, but they can also be caused by human error or system failures. Here are some of the most common ways a data breach happens:
-
Phishing and social engineering: Phishing, a top cause of data breaches, is a social engineering tactic. Attackers use fraudulent communications (emails, texts) to trick individuals into revealing sensitive information or clicking on malicious links.
-
Stolen or compromised credentials: Once an attacker gets a username and password, they can gain unauthorized access to a network. This is often a result of phishing attacks, information-stealing malware, or credential stuffing, where threat actors use credentials from one data breach to gain access to accounts on other platforms.
-
Malware and ransomware: Malicious software, or malware, is designed to infiltrate a system to steal data, disrupt operations, or both. Ransomware is a particularly damaging type of malware that encrypts a victim's data and holds it hostage until a ransom is paid.
-
Human error and system misconfigurations: Not all breaches result from a malicious attack. Employees can accidentally expose data by emailing sensitive information to the wrong person, misplacing a device like a laptop, or storing files in an unsecured location. Similarly, misconfigured cloud storage settings or outdated software with known vulnerabilities can leave data on a system open to compromise.
How to reduce your risk
There are many ways to prevent a data breach from happening, or, at the very least, make sure your organization is prepared. Handling attacks quickly and effectively can help minimize financial and reputational damage. Here are some tips:
-
Implement a multi-layered security strategy: Relying on a single security tool isn’t enough. A robust defense involves multiple layers, from strong access controls and multi-factor authentication to advanced threat detection and continuous monitoring.
-
Prioritize a strong security culture: Technology is only one piece of the puzzle. Human error is a leading cause of breaches, so regular security awareness training on topics like phishing, secure data handling, and password hygiene is essential.
-
Practice good cyber hygiene: This includes keeping all software and systems updated, completing regular data backups, and removing any unnecessary or outdated software and hardware from the network to reduce your attack surface.
-
Develop and test an incident response plan: Knowing what to do before a breach occurs is critical. A well-defined plan helps an organization respond quickly to an incident and contain the damage.
Reduce data breach costs with faster response time
A critical factor in controlling data breach costs is your response speed. The longer a threat actor lurks in a system, the more data they can access and the more damage they can cause. Organizations that can quickly detect and contain a breach can save millions of dollars.
Threats can seem overwhelming, but with our in-depth understanding of how threat actors think, we know what to look for. Huntress gives you fully managed endpoint detection and response (EDR), so you've got 24/7 support from security experts ready to respond to threats.
FAQ
What’s the average total cost of a data breach?
Globally, the average total cost of a data breach is $4.4 million, but it varies by industry and location.
What’s the most expensive data breach ever?
The most expensive data breach ever was the NotPetya/ExPtr data breach in 2017, which cost $10 billion.
What’s the most expensive data breach of 2025?
Without the full year of data, it’s not clear which breach is the most expensive yet, considering both the direct and indirect costs. However, the healthcare industry is currently leading the way with an average cost of $7.42 million.