Welcome to the dark web. Maybe you’re a threat actor looking to cash in on the latest data swiped in a breach. Maybe you’re a security researcher snooping on the shop-talk and service offerings to gather intel. Maybe you just want to sit back with some popcorn and watch the ever-entertaining cybercrime drama play out.
Dark web forums showcase the full threat ecosystem in all its splendor—from initial access brokers peddling compromised RDP credentials to ransomware actors setting data leak countdowns on their name-and-shame sites. But like any other commerce platform, they also include dealings that feel strangely business as usual: sales promotions, codes of conduct, technical support, and more.
We’ve taken several deep-dive looks into the dark web before, and this latest one is part of our August Tradecraft Tuesday episode, where Huntress’ John Hammond, principal security researcher, and Dave Kleinatland, principal product researcher, explored some of the most popular underground forums, marketplaces, and ransomware data leak sites.
What is the dark web?
First, what is the dark web? Essentially, the dark web is still part of the internet; it’s just made up of unindexed content that users can access anonymously. Popular forums on the dark web, like BreachForums, can be reached through networks like Tor via a technique called onion routing. Onion routing encapsulates network traffic with encryption and sends the traffic from the client through a series of hops before reaching the end server. This process anonymizes users’ traffic so they can’t be traced. The end server only knows the most recent connecting node (also known as the exit node). It’s great for privacy, but also used by cybercriminals for untraceable illicit dealings.
Figure 1: A look at BreachForums, a popular dark web marketplace
You may have also heard about the deep web, and while “dark web” and “deep web” are sometimes used interchangeably, there are notable differences. The deep web also includes sites that aren’t indexed by standard search engines, but these sites are available on the clearnet, meaning that they can be reached via regular web browsers. There’s also a slight difference when it comes to the top-level domains (TLDs). Deep websites use uncommon TLDs, like .hn or .so. These TLDs aren’t the typical ones we’re used to (like .com), but they’re also different from those used by dark websites, which will have a .onion address.
We can’t talk about the dark web without mentioning bulletproof hosting providers, like Webcare 360, Offshore Racks, AbeloHost, PrivateAlps, or Koddos. These are essentially web hosting services that enable cybercrime—like malware hosting or sites used for phishing—by ignoring or evading law enforcement or various abuse complaints.
Dark web forums and marketplaces: XSS, Exploit, and more
The dark web is an eclectic mix of forums and marketplaces, including RAMP, Cracked, OnniForums, and more. Many resources are available to improve the browsing experience, including a search engine called Torch, which is basically the dark web equivalent of Google or Yahoo.
Many of these sites are pay-to-play, meaning users need to pay with cryptocurrency to gain entry into the forum. From there, users can sell or buy anything from malware, exploits, access via FTP, carding or banking information, and more. Site visitors also congregate to trade tips, ask questions, and discuss the latest news. Exploit, a popular Russian cybercrime forum, categorizes its topics across all different aspects of the hacking ecosystem, as Figure 2 shows. There are posts about cryptography, spam, bluejacking, social networks, and, of course, AI.
Figure 2: A range of topics discussed on the Exploit cybercrime forum
A closer look at the bulletin boards, threads, and postings on the Russian-speaking forum XSS, meanwhile, shows people looking for access to company environments. Like many other forums, this one also features infostealer malware logs, which are credentials sold in data dumps that can be used by threat actors for business email compromise (BEC) or other identity attacks. Note: while Europol in July announced the arrest of the forum’s administrator, and a takedown banner was placed on the site, XSS has since migrated and appears to be currently up and running again.
Figure 3: A marketplace on XSS shows people looking to buy access
Despite their user base, these forums ironically have codes of conduct. In an interesting twist on the phrase “no honor amongst thieves,” if users are ever wronged by someone who doesn’t pay up, the moderator will step in and ban them.
Sellers on these forums also use innovative marketing techniques to push their products. The video below shows a giveaway promotion in an Exploit posting, which claims to include a dump of 130,000 US credit card numbers. The giveaway appears to be a way to increase engagement and drive future sales.
It’s hard to know exactly how many people actually use the dark web, but the membership numbers for these forums are not insignificant. Exploit claims to have 68,000 total members, with 101,000 attendees being present online at one point. XSS, meanwhile, had more than 50,000 registered users as of July, according to Europol.
BreachForums: The latest in its tumultuous history
BreachForums—one of the most infamous cybercrime forums—has had a tumultuous history, which includes multiple law enforcement takedowns and subsequent revivals under new ownership (including ones in 2022, 2023, and 2024).
The forum appeared to be revived in July. Then, on August 12, BreachForums administrator ShinyHunters issued a message in their Telegram chat (and via a PGP-signed message on Pastebin). The message warned of a “serious incident affecting BreachForums” and said that BreachForums and its official PGP key had been compromised and were currently being operated by law enforcement agencies.
In a strange twist, a recent announcement on BreachForums had also appeared on August 11, offering a “substantial bounty” in exchange for the identification and location of an individual called “Yukari.”
We can only speculate about what this all means and how these two events are linked. We don’t know if the bounty for “Yukari” was posted pre-compromise by ShinyHunters or as bait by law enforcement officials who had compromised the site. Either way, this puts the “cybercrime high school drama” of these forums on full display.
Ransomware groups pressure victims with ‘name and shame’ sites
For ransomware groups, dark web sites play a critical role in their operations: data leak sites.
As the Huntress 2025 Cyber Threat Report shows, more threat actors are shifting their attacks from traditional encryption to data theft and extortion, particularly as targeted organizations improve their backup and data recovery efforts. Name-and-shame sites are a key piece of the extortion model for ransomware actors. These provide a platform for threat actors to threaten victims with the public release of their data if they don’t pay the ransom.
A closer look at the name-and-shame site for Play—which has allegedly racked up 900 or so victims—shows that different data sets linked to breaches even have timers leading to the deadline until publication. The site also signals data that has already been published. This is all part of the psychological manipulation that comes with ransomware attacks, using scare tactics and mounting pressure on victims to pay the ransom.
Over time, ransomware groups have adopted “official” processes for their operations. Many groups offer technical support, customer service, and knowledge-base resources for their victims. As part of this, we can see that Play’s data leak site features an FAQ page addressing questions about the incident, such as what makes up their ransom pricing, what happens if they don’t pay, and more.
Chats, sales, and…a Huntress Easter egg?
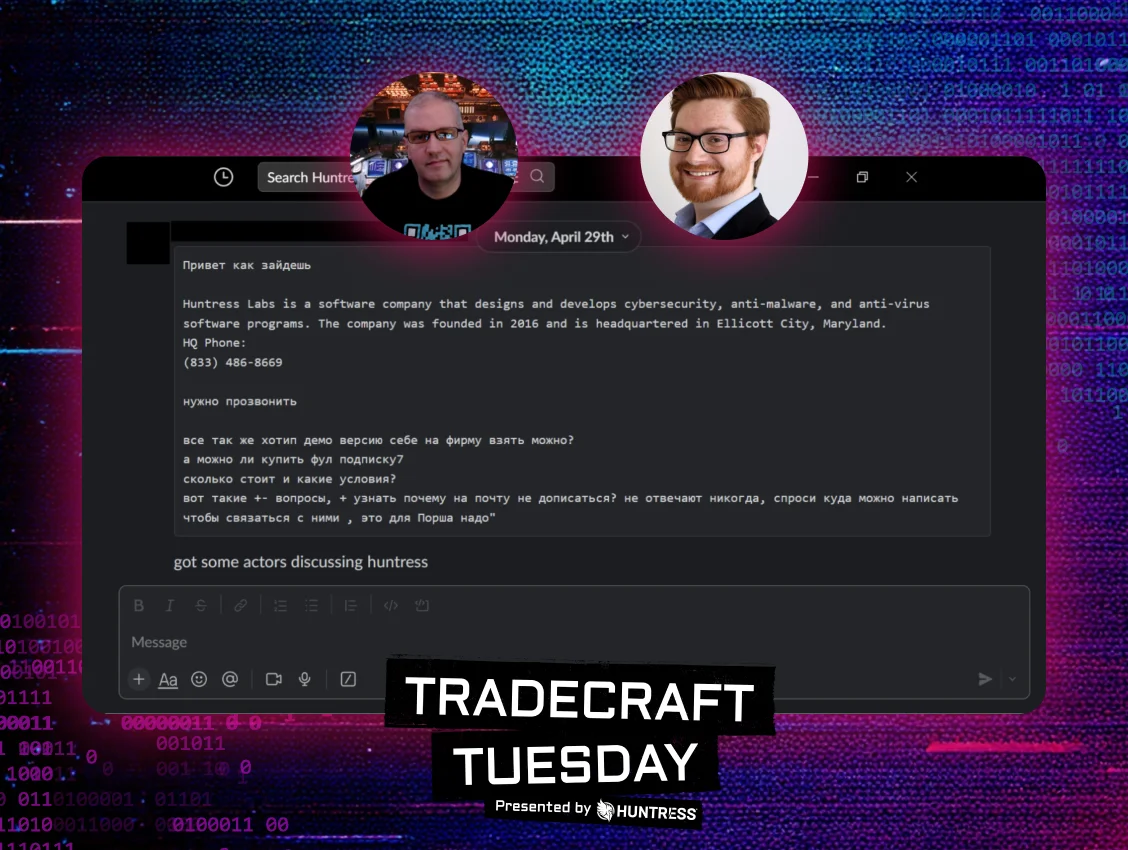
The dark web is a unique place to collect information on areas of interest for cybercriminals—and sometimes, that interest hits close to home. Our researchers recently received a tip that ransomware actors were discussing Hutress in a series of messages. The actors said they were trying to start a trial to see how Huntress’ endpoint detection and response (EDR) platform would perform against some samples.
Figure 4: Huntress is one of many topics of discussion by threat actors on the dark web
Whether it’s infostealer logs, exploits, or even Huntress itself, you can find all kinds of topics being discussed on the dark web. But navigating the dark web shows much more than the latest threats—it exposes the adaptability and resourcefulness of threat actors, from innovative operational strategies to business-style negotiations. This gives defenders a sense of what they’re up against and can help shed light on the areas of their business that are at risk.
Like what you just read? Join us every month for Tradecraft Tuesday, our live webinar where we expose hacker techniques and talk nerdy with live demos. Next month, our Tradecraft Tuesday episode, “The Craftiest Trends, Scams, and Tradecraft of 2025 (So Far),” will tackle the top threats that our SOC is seeing so far in the trenches this year. Snag your spot now!