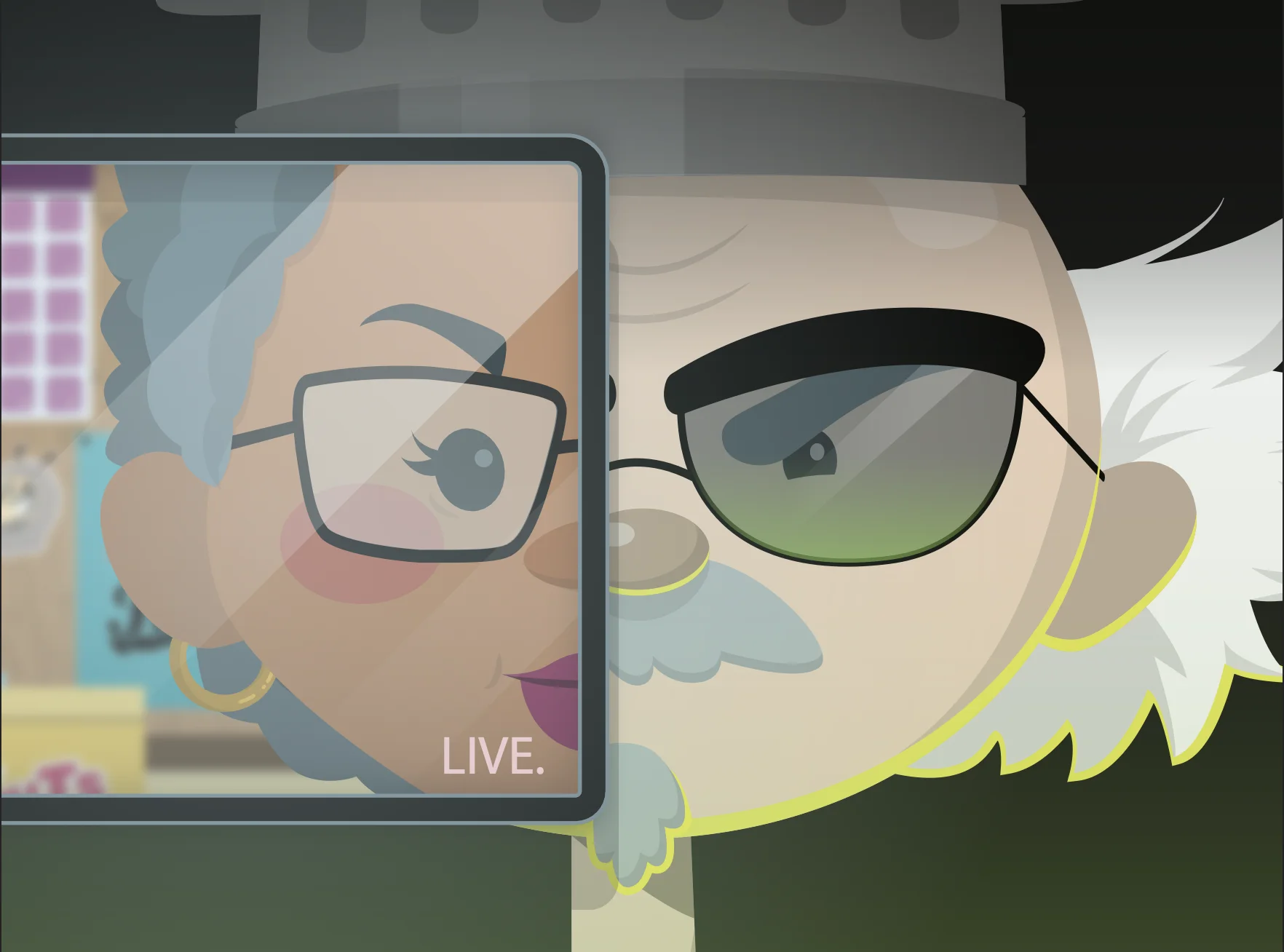
When BopTalk’s CEO, Matt Z, becomes the latest target of the All-Seeing Three, Jiya crafts a tailored spear-phishing attack using details about the company’s recent Lookie-Lookie acquisition. SSpear phishing uses publicly available information to deceive targets. Unlike generic phishing, these attacks rely on open-source intelligence (OSINT), exploit trusted relationships, and use tactics like custom landing pages and Adversary-in-the-Middle (AiTM) techniques to steal credentials or bypass multi-factor authentication (MFA). Will Matt Z recognize the threat, or will the All-Seeing Three put BopTalk and its new acquisition at risk?
Following the completion of this episode, learners should be able to:
- Recognize key signs of a spear phishing attempt
- Identify fake landing pages and spoofed websites used in spear phishing
- Understand how attackers use personal information and OSINT to target individuals
- Use safe online habits to reduce the risk of phishing
- Respond appropriately to suspected spear phishing emails
- Understand what Living Off Trusted Sites (LOTS) is and the associated risks