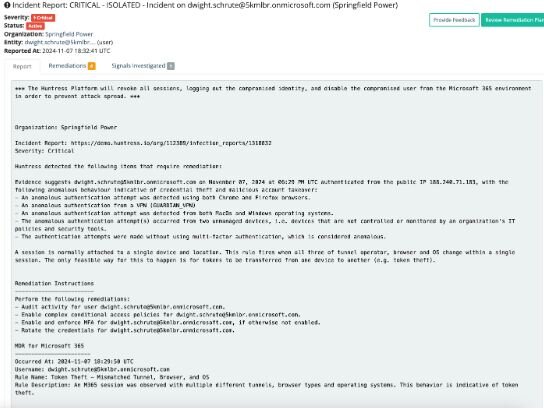
Endpoint tools like antivirus or EDR and MFA are a no-brainer—but remember that these tools were not built to identify and detect identity abuse. Attackers often use stolen valid credentials to get past these and log in with a business account. ITDR closes this gap by zeroing in on identities, accounts, and directories.
Given that ITDR is still a new solution, there’s a lot of confusion about what ITDR stands for and how it works. That’s not surprising since this emerging security category overlaps with many other popular security acronyms. Let’s break down the overlap, as well as how ITDR is different from other solutions.
ITDR vs. XDR
XDR (Extended Detection and Response) solutions pool telemetry from endpoints, networks, and cloud apps. ITDR solutions focus on identity abuse. As a result, they’re ideal complements—XDR for big-picture coverage, ITDR for laser-like focus on identity-related threats.
ITDR vs. IAM
IAM (Identity and Access Management) is about provisioning and access control—preventative controls that say who is and isn’t allowed to access your IT resources. ITDR is the second line of defense that comes into play if someone manages to get in. IAM is your lock; ITDR is the alarm system when the lock gets picked.
ITDR vs. MDR
MDR (Managed Detection and Response) is a broad category that covers monitoring and incident response for threats that are active across networks and endpoints. ITDR is the identity specialization that makes sure there’s nothing human-based slipping through the castle walls.