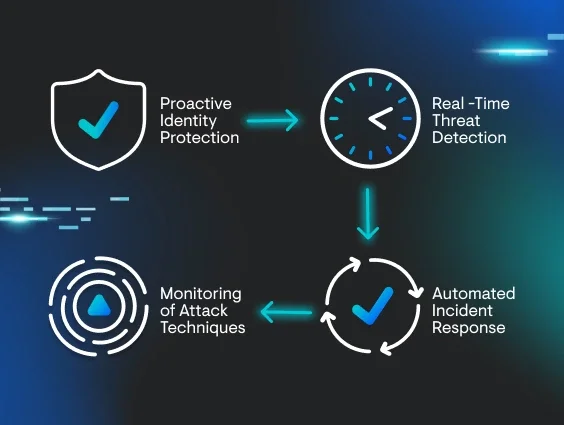
Identity protection starts with understanding how attackers move—and how to stop them mid-stride.
Instead of waiting for signs of compromise, ITDR focuses on the accounts and permissions that criminals exploit to move laterally and stay hidden. This guide breaks down the ITDR basics so you can see how it strengthens identity security across every layer.
Business owners, IT admins, and security professionals alike need to understand how ITDR solutions integrate with existing tools and close visibility gaps left by EDR and SIEM alone. These resources explain how to evaluate tools, detect threats earlier, and build an identity-focused security strategy that works in the real world.
Identity has moved from a secondary concern to the primary target. And if your tools aren't watching for identity-based threats in real time, they're not keeping up. Our team sees attacks on identities and credentials firsthand every day. We built Managed ITDR to make identity protection accessible, effective, and backed by real experts who respond immediately.