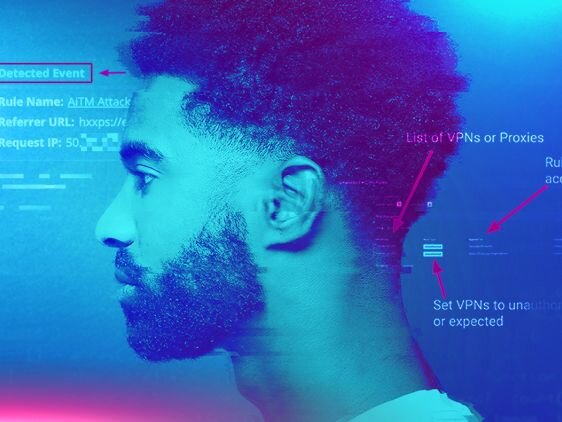
Identity-based attacks are now the main way attackers get in.
According to the Identity Defined Security Alliance (IDSA), 90% of organizations experienced an identity-related incident in the last year. Meanwhile, the Verizon Data Breach Investigations Report (DBIR) found that stolen credentials now lead the charge for breaches involving a human element. As everyone piled into Microsoft 365, their user accounts became the #1 target.
And it's expensive. The FBI's 2024 IC3 report clocked Business Email Compromise (BEC) as the second costliest cybercrime, to the tune of $2.77 billion in losses. You need a strong identity threat detection and response (ITDR) plan to get ahead of the risk. This checklist outlines the features you need to build layered identity protection that actually detects, responds to, and stops attackers.
What is Managed ITDR?
ITDR is a security strategy that watches over your user and machine identities. It means monitoring who’s logging in, what they’re doing, and how they’re behaving across your entire setup—both across cloud and on-prem.
Here's the problem: most "solutions" just dump alerts on you. Huntress Managed ITDR gives you enterprise-grade identity protection, backed by our 24/7 SOC, even if you don't have a security team on standby. We built it for the "99%"—the businesses that don't have a basement full of security analysts. By combining automated detection with actual human experts, Huntress kills the alert fatigue and makes sure real threats get shut down, fast.
This approach is critical because identity isn't just one thing. It’s a complex web of logins, permissions, and behaviors across every app. An attacker stealing a single password can look like a legit user. Without a human-validated operation correlating that login with other faint signals, the attacker can slip by completely unnoticed.
Multi-factor authentication (MFA) and legacy access prevention
MFA is your seatbelt. Enabling it is the absolute baseline for identity protection and helps prevent 99.9% of phishing attacks on your accounts.
Effective MFA means enforcing it across all user accounts, especially admins. But MFA isn't a silver bullet, especially if you leave the back door open. If you still allow legacy authentication (like POP3 and IMAP), attackers don't even need to bypass MFA. They can just walk right in using those ancient, insecure protocols.
Your "must-do" list:
Block basic authentication. All of it. Everywhere.
Use conditional access policies to block logins from unmanaged devices.
Block connections from countries where your company knows traffic shouldn’t come from. (Why let them even try?)
Privileged identity management and just-in-time access
Stop handing out admin rights like candy. Privileged identity management (PIM) is how you shrink your attack surface by locking down those powerful accounts. Grant "god mode" access only when someone actually needs it, and only for a short time.
Limit your Global Admins to five or fewer accounts. Period. For everything else, use just-in-time access, which gives temporary permissions for a specific task and then snatches them back. This dramatically cuts down the time an attacker has to do damage.
This isn't optional. Gartner predicts that by 2026, organizations with advanced identity-first security programs will suffer 50% fewer identity-related breaches than those without. While Huntress isn't a PIM tool, our SOC is always watching for privilege abuse and escalations, ready to catch attackers who try to make themselves an admin.
Setup | Security Impact | Attacker Risk | Admin Effort |
With PIM | Drastically reduced attack surface | High friction for attackers | Moderate initial setup |
Without PIM | Massive attack surface | Low friction for attackers | Easy setup, but a primary cause of major breaches |
Advanced threat protection with Microsoft Defender
Microsoft Defender for Identity is a powerful tool. It has massive telemetry and can spot all sorts of identity attacks. But let's be honest: it also creates a ton of alerts.
This is where a managed service becomes a game-changer. Huntress wraps a 24/7, human-led SOC around Microsoft’s tools. We investigate the noise, correlate the data, and only escalate the real threats. We add the human-powered threat hunting and remediation that turns Defender's noisy alerts into a quiet, effective defense.
This human layer is what stops sophisticated, low-and-slow attacks. An automated tool without human insight might miss an attacker using legitimate admin tools (like PowerShell) for malicious ends. Our SOC analysts, however, are trained to spot that malicious intent—the 'how' and 'why' behind an alert—which provides the context needed to prevent a breach.
Continuous monitoring and automated response
"Dwell time" is the polite term for "how long an attacker gets to roam free in your network." Continuous monitoring is how you crush it. You need systems that can spot the subtle signs of a compromise, not just the obvious ones.
This is the core of the Huntress Managed ITDR service. Acting as the first line of defense, it helps ensure that only authorized users can access your system. When necessary, it offers automated remediation. You can't afford to wait for someone to wake up and check an alert. Continuous monitoring plus real humans ready to respond when necessary gives you an edge that attackers don’t expect.


Shut Down Identity Attacks
Get identity protection for attacks like credential theft, session hijacking, and rogue OAuth apps, backed by a 24/7 AI-assisted SOC to keep your users safe. Experience ITDR’s impact with a free trial.