At this point, it’s no secret that threat actors are abusing remote monitoring and management (RMM) tools in their attacks for access to and persistence in victim environments.
While businesses use RMMs to increase efficiencies and reduce cost, threat actors have also been compromising legacy RMM tools or installing their own RMM once they gained access to the endpoint. And, in several cases this year, Huntress has also observed incidents involving multiple RMM tools. These incidents have involved all kinds of RMM platforms, including ScreenConnect, TeamViewer, Atera, NinjaRMM, and more.
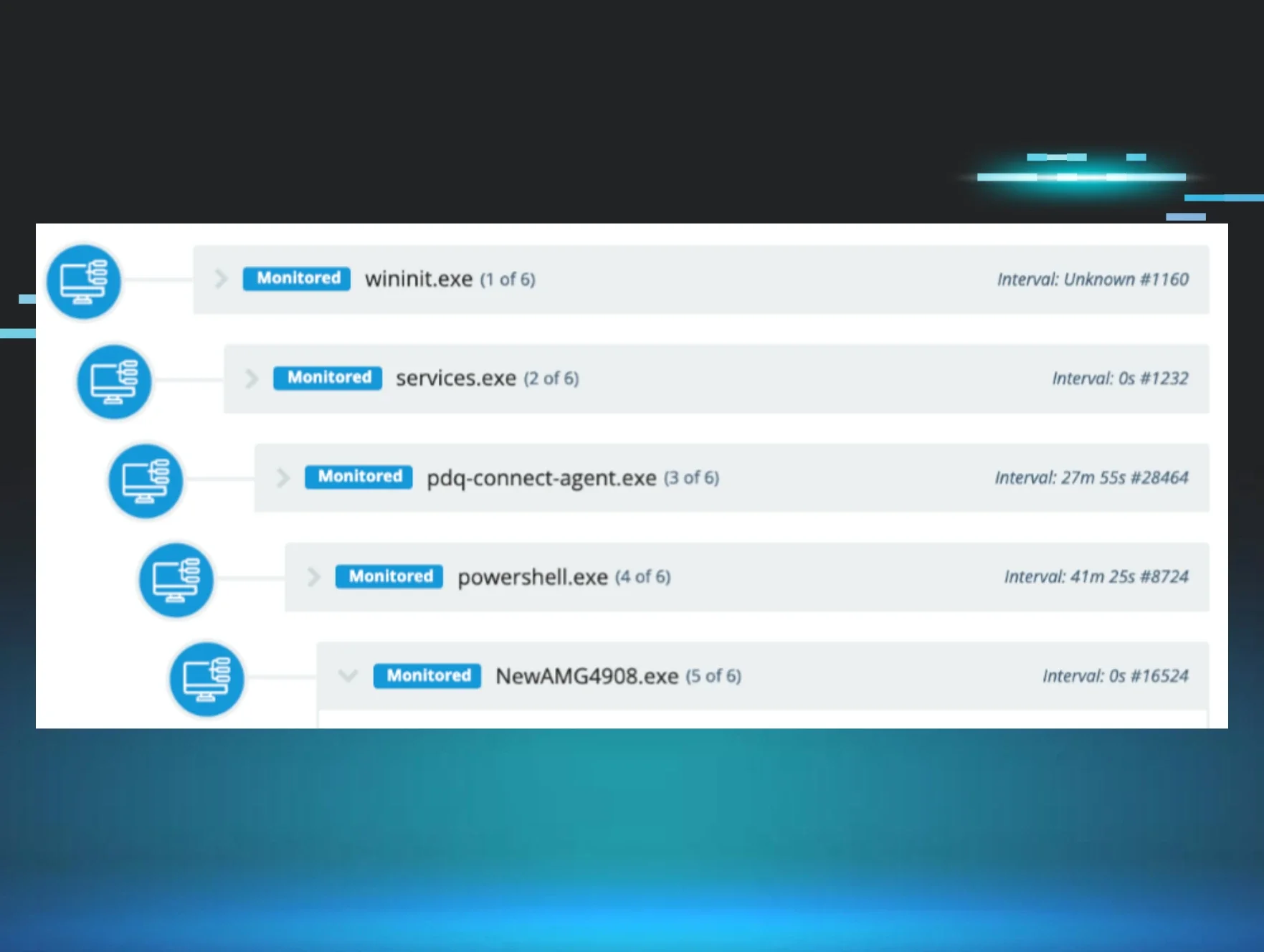
Recently, the Huntress Security Operations Center (SOC) has seen a very specific pattern emerge in this attack chain involving RMM tools: incidents that start with threat actors using PDQ or GoTo Resolve in order to then deploy secondary RMM tools, such as ScreenConnect or SimpleHelp.
There are several reasons why threat actors may deploy multiple RMM tools. The use of a second (and even third or fourth) RMM tool can help ensure longer term access, even if the first tool is blocked. Below are a few examples of what our SOC is seeing, including some of the popular social engineering lures that threat actors are using to trick victims into downloading rogue RMMs, and the use of different RMM instances beyond ScreenConnect.
GoTo Resolve to ScreenConnect
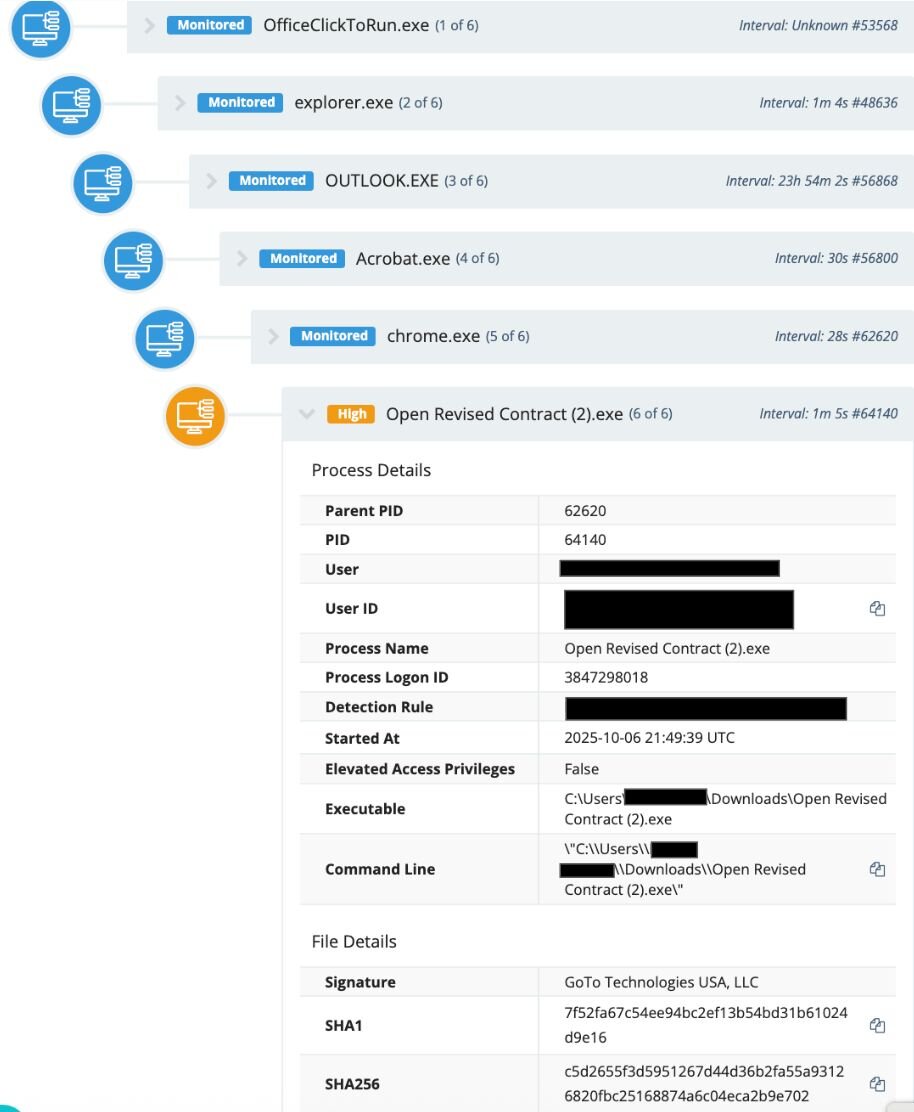
On October 7, an employee at a real estate company received a phishing email through Outlook, which led to them installing Open Revised Contract (2).exe. This executable file was actually a renamed GoTo Resolve instance signed by GoTo Technologies USA, LLC, as seen in Figure 1.
A Windows Scheduled task was also created to start the GoTo Resolve service for persistence purposes: C:\WINDOWS\system32\sc.exe start GoToResolve_2362921307173827601
Then, the threat actor used their access through this initial GoTo Resolve installation to infect the victim with another RMM, ScreenConnect, via the file path:
c:\program files (x86)\screenconnect client (fdeeb5df8057eef0)\screenconnect.clientservice.exe
A search for the ScreenConnect binary (f1b5c000794f046259121c63ed37f9eff0cfe1258588eca6fd85e16d3922767e) on VirusTotal shows the “Execution Parents” revealing the names of different lures connected to the execution chains (as seen in Figure 2).
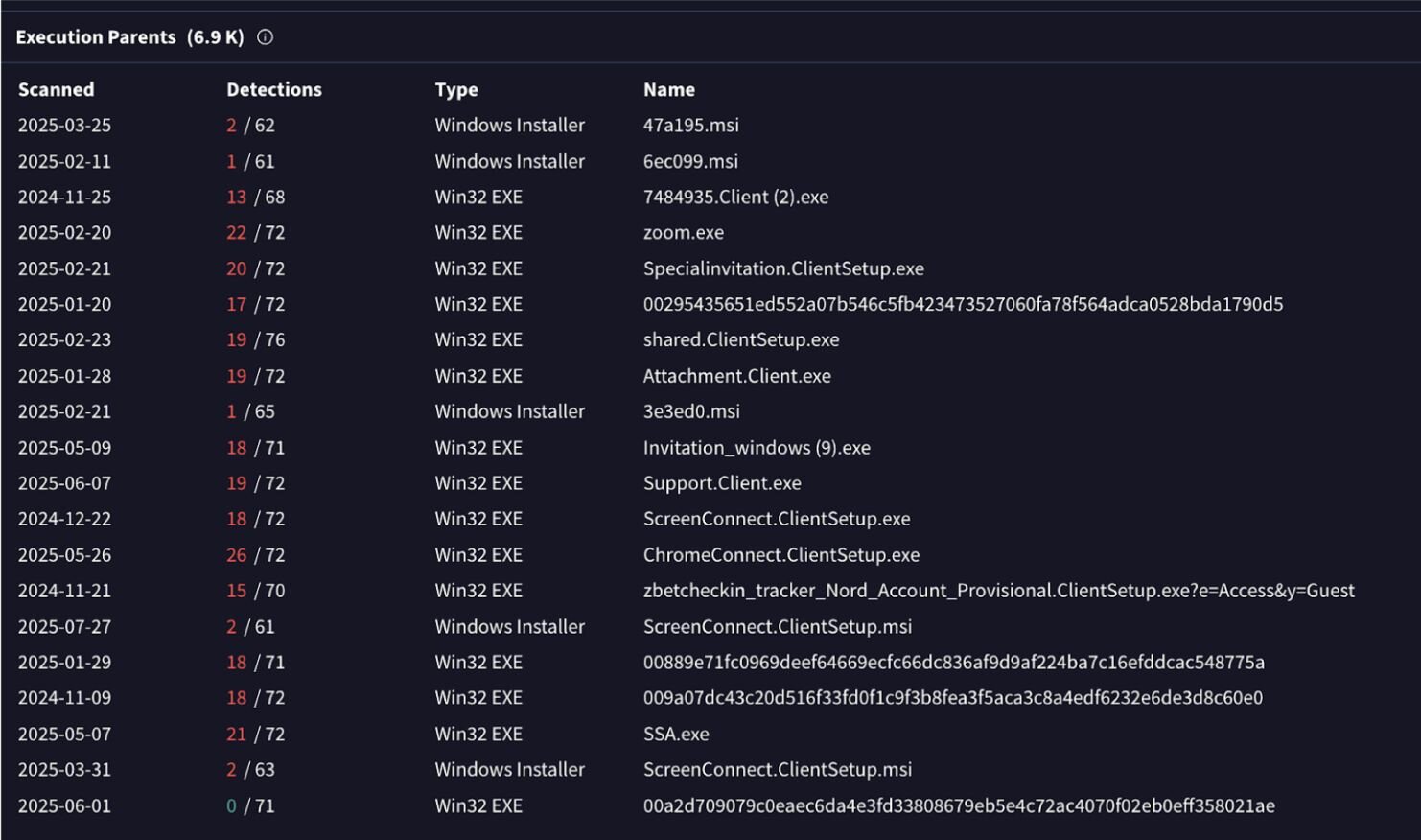
The SOC identified this threat through a retrospective threat hunting exercise, which allows us to query various telemetries with specific security hypotheses. Huntress is constantly using new technologies and threat intelligence to deploy retrospective threat hunting across our existing telemetries; this helps us continuously reassess past and present telemetries. For this specific case, we worked with the business to neutralize the rogue RMMs.
PDQ to SimpleHelp instance
We’ve seen multiple instances that start with the installation of PDQ, and then use a secondary RMM in the next phase of the attack.
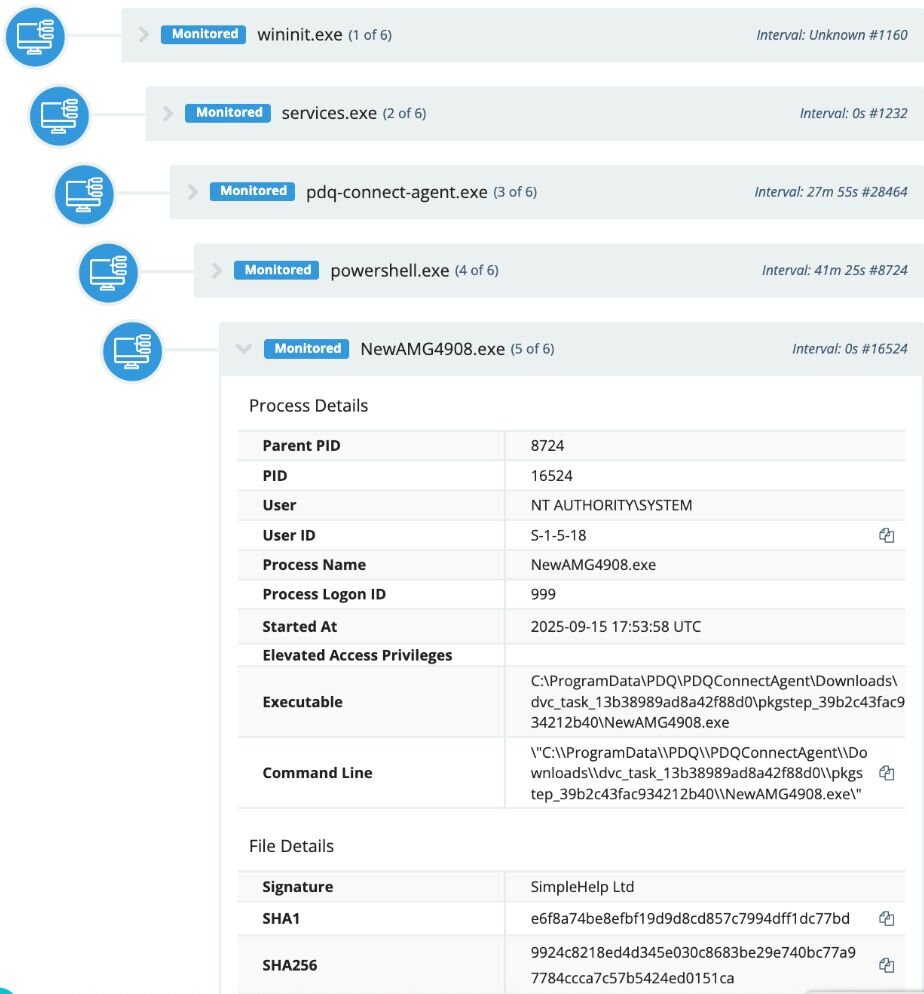
In September, a user at an investment firm downloaded a file (C:\Users\REDACTED\Downloads\276Special%10Invitation9756.msi) from hxxp[://]elegantparty[.]de, which led to the download of a renamed PDQ Installer.
The threat actor then used PDQ to install a malicious SimpleHelp instance (NewAMG2908.exe), which was signed by SimpleHelp Ltd. and configured to connect to the domain stsmithchurchitems[.]shop.
Any domains or IP addresses for SimpleHelp can be pulled from the configuration file from the following path: C:\ProgramData\JWrapper-Remote Access\JWAppsSharedConfig\serviceconfig.xml
This rogue SimpleHelp RMM was installed in the path: C:\ProgramData\JWrapper-Remote Access\JWAppsSharedConfig\restricted\SimpleService.exe
At this point, SOC analysts stopped the attack before it could escalate, isolating the host to prevent further ingress and working with the impacted business on remediation steps.
Other RMM instances
The SOC also sees a number of other RMM types, such as malicious Chrome Remote Desktop, Atera, and ITarian instances. The latter RMM has popped up in a couple of recent incidents in November, leading to threat actors executing a secondary ScreenConnect installer.
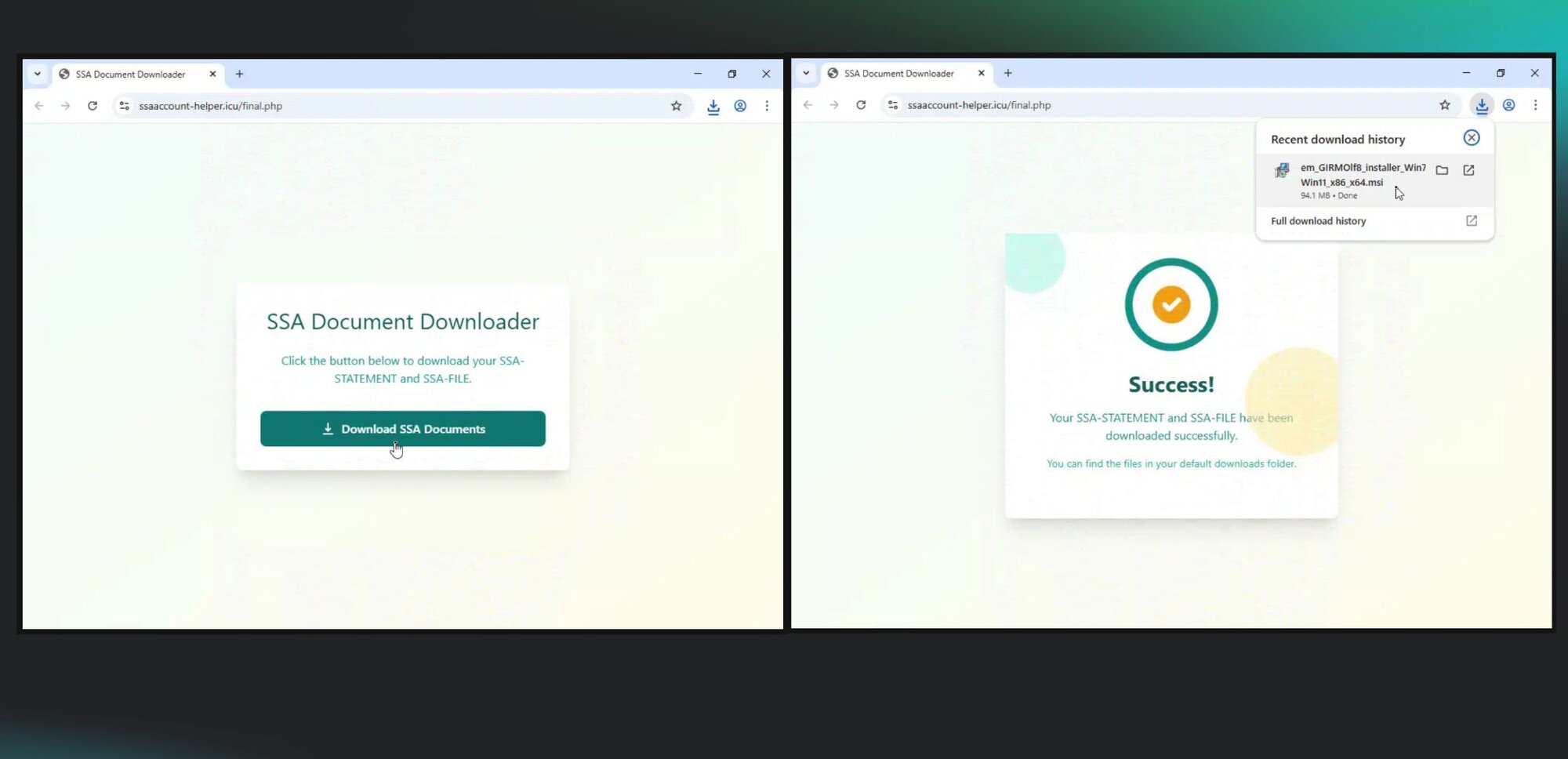
On November 24, the SOC team conducted a retrospective threat hunt that revealed that a company employee had downloaded a rogue ITarian RMM installer earlier that day. A closer look into the user’s Chrome browser history showed that the installer was downloaded from ssaaccount-helper[.]icu.
Figure 4 shows that the lure linked to this domain had to do with a purported social security account statement. Once the victim clicked “Download SSA Documents,” it kicked off the download for the rogue RMM installer (em_GIRMOlf8_installer_Win7-Win11_x86_x64.msi).
The ITarian installer then used its own CMD script module from the RMM management site in order to launch a .CMD file (on disk for a short period of time). That file ( seen on the endpoint in C:\Users\REDACTED\AppData\Local\Temp\7ZSfx000.cmd) then installed a rogue ScreenConnect instance, which was configured to a recently registered domain, deuwre[.]com.
At this point, the SOC team intervened in the attack, stopping the threat actor from escalating any further.
A longer chain of RMM downloads
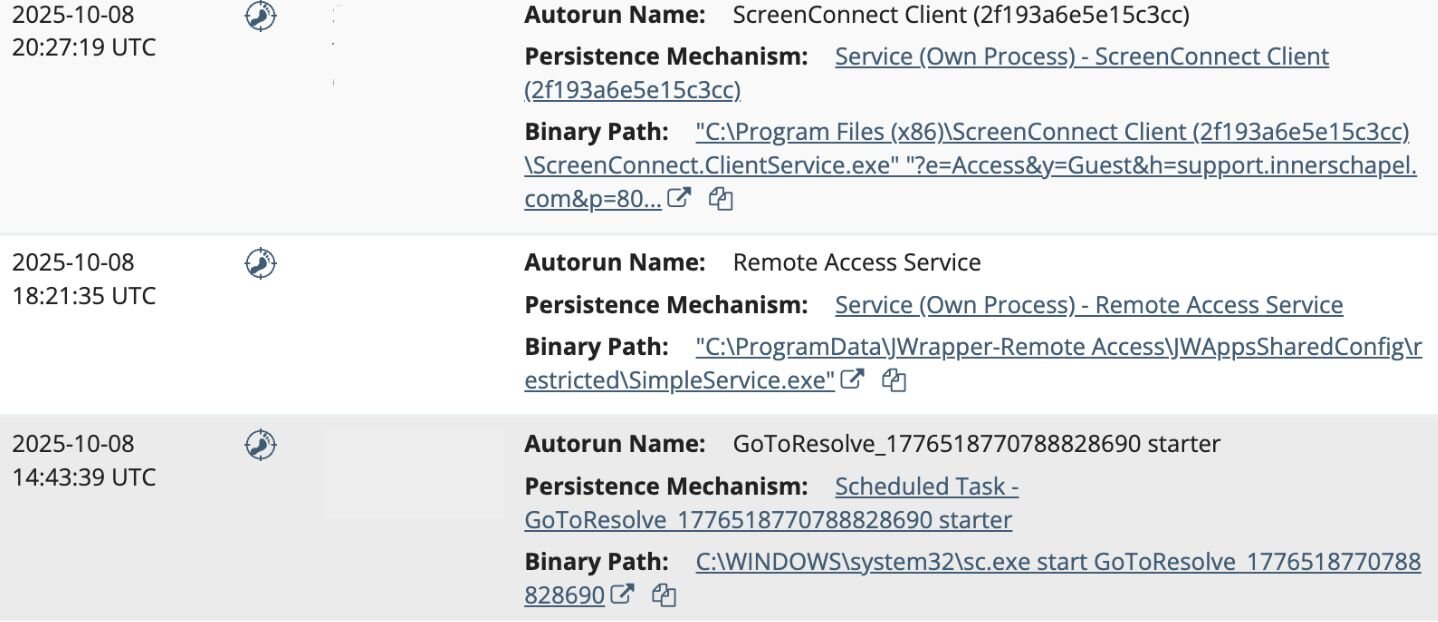
In October, Huntress observed a user at a car dealer execute the file OPENINVITATION.exe, which is a rogue GoTo Resolve RMM installer. The file was downloaded from the domain abre[.]ai.
The threat actor then used their access via GoTo Resolve to install a rogue SimpleHelp RMM (SimpleService.exe) on the host, in the following directory:
C:\ProgramData\JWrapper-Remote Access\JWAppsSharedConfig\restricted\
The instance was configured to communicate with the domain xtroloozyanimailfeeddeals[.]shop.
But it didn’t stop there.
Threat actors then used the SimpleHelp RMM to install a malicious ScreenConnect instance, configured with the domain support[.]innerschapel[.]com, in the directory:
C:\Program Files (x86)\ScreenConnect Client (2f193a6e5e15c3cc)\
At this point, Huntress SOC analysts caught and stopped the threat actor before they could deploy any further processes or persistence mechanisms.
Continued use of social engineering
One way that threat actors spread RMMs is via phishing emails that use various lures to convince victims to download them. Recently, a few social engineering lures caught our eyes:
-
The Holiday Lure: On November 2, a user was tricked into executing a malicious process (
Thanksgiving-iv.exe) from the directoryC:\Users\REDACTED\Downloads\on the impacted host. Further inspection revealed that this file is a rogue installer for GoTo Resolve RMM. The victim’s Firefox browser artifacts revealed that this installer was downloaded from the URLhttps[:]//pub-0e9274b4f4a74997bcafd5c5c778bf91[.]r2[.]dev/Thanksgiving-iv.exe. The malicious RMM then deployed a rogue ScreenConnect installer into the directoryC:\Program Files (x86)\ScreenConnect Client (3bf4055180e70e5b), which was configured for the domainwilkensealsivc[.]shop. -
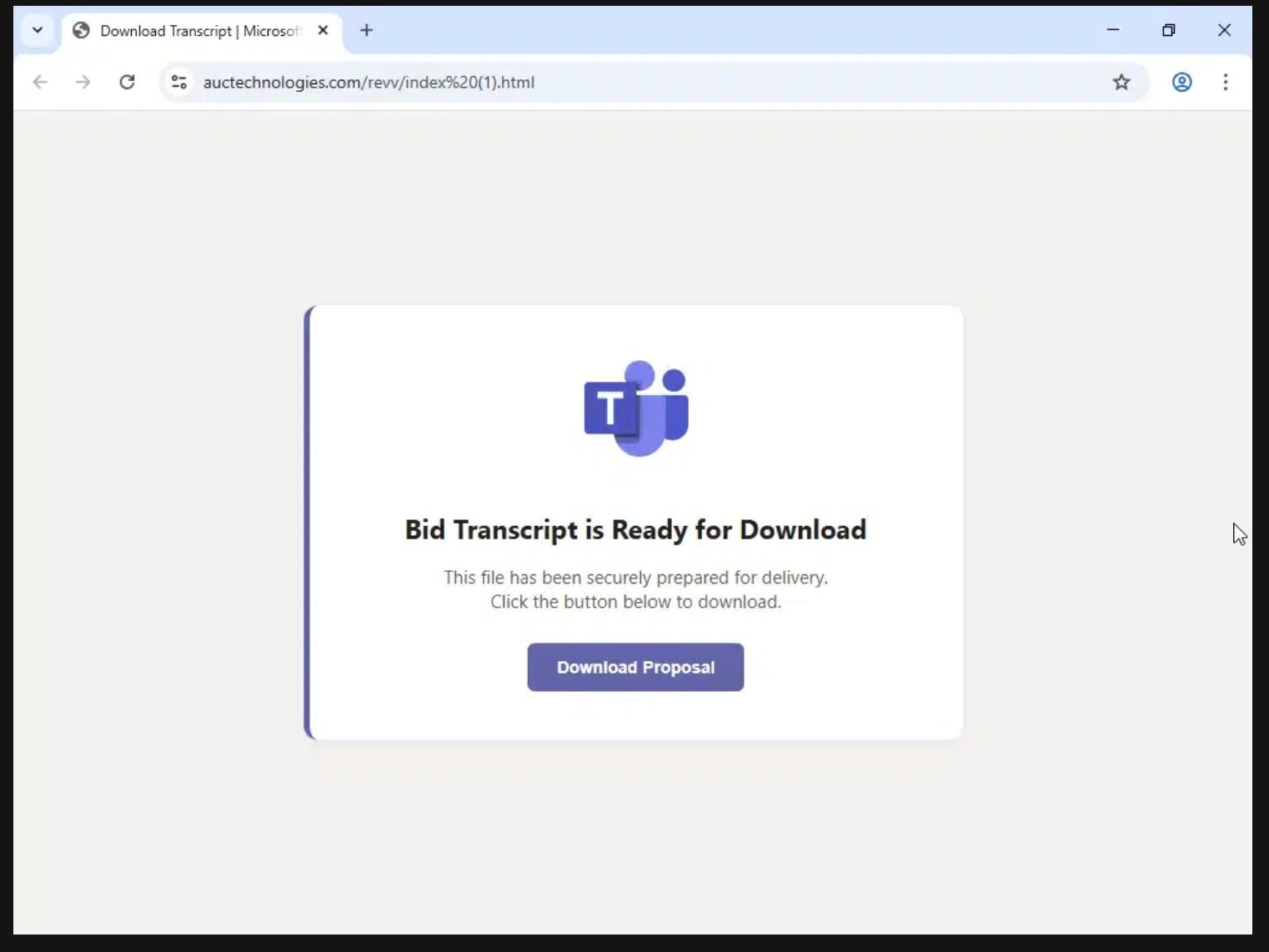
The Fake Bid Transcript: On October 15, a phishing message purporting to contain a Bid Transcript from Microsoft Teams duped a user into downloading and executing the file
Contract Revised.exe, as seen in Figure 6 below. The file was actually a GoTo Resolve rogue RMM, downloaded fromhttps[:]//auctechnologies[.]com/revv/index%20(1)[.]html. After installation, the instance executed several executables (HideUL.exeandPIN.exe), but they weren’t accessible for further analysis on disk. -
The Evite (A Classic): Fake invitations are a popular type of lure used by threat actors, which we have seen across many different rogue RMM incidents. On November 3, a user was tricked into executing
EVITEINVITERSOLVELIST.exe, which was actually a malicious GoTo Resolve installer. Interestingly, threat actors jumped from GoTo Resolve to then make use of living-off-the-land (LotL) techniques by downloading and executing a rogue ScreenConnect installer withmsiexecvia a remote domain(https[:]//con[.]wepivifllc[.]de/Bin/ReadAdobe_MICR0S0FTxxPDF.ClientSetup[.]msi).
Multiple RMMs and the power of a managed SOC
Threat actors find success in using RMMs for the same reason that malicious instances are hard to weed out: they are legitimate tools, and therefore it’s difficult to discern what stems from end user behavior versus what is malicious.
This is where the value of a managed SOC can help: SOC analysts look at indicators like where instances are calling out to, where they’re being installed on the system, and how they’re being installed.
For instance, an RMM might be installed out of a temp directory (which is more suspicious) versus an application directory (with other legitimate applications). Or, maybe a rogue RMM instance calls out to an RMM free trial domain, versus a domain name that’s associated with the business that’s actually using the RMM legitimately.
There are several steps that businesses can take to attempt to prevent the threat of rogue RMMs in the first place, however. That includes:
- Developing an asset inventory to take into account installed applications and create application controls to cover RMMs (and block unauthorized programs)
- Audit and monitor RMMs in order to track ones that are currently used or authorized. Check curated lists like LOLRMM to better understand what RMM tools could potentially be abused by threat actors
- Check logs for instances where RMMs were executed to weed out suspicious RMM use
The incidents that we've outlined above are only a small fraction of the cases that the Huntress SOC team experiences daily when it comes to rogue RMM deployments. The SOC sees not only individual RMM installations, but multiple layers of rogue RMMs across various endpoints as threat actors seek to ensure persistence in their attacks. Businesses should prioritize the threat of RMM abuse accordingly.
Indicators of Compromise
ScreenConnect
|
Item |
Description |
|
support[.]innerschapel[.]com |
Download source |
|
wilkensealsivc[.]shop |
Download source |
|
deuwre[.]com |
Attacker-controlled domain |
|
wilkensealsivc[.]shop |
Attacker-controlled domain |
|
https[:]//con[.]wepivifllc[.]de |
Download source |
SimpleHelp
|
Item |
Description |
|
stsmithchurchitems[.]shop |
Attacker-controlled domain |
|
xtroloozyanimailfeeddeals[.]shop |
Attacker-controlled domain |
PDQ
|
Item |
Description |
|
hxxp[://]elegantparty[.]de |
Download source |
GoTo Resolve
|
Item |
Description |
|
abre[.]ai |
Download source |
ITarian
|
Item |
Description |
|
ssaaccount-helper[.]icu |
Download source |