Threat actors love a good phish.
In this year’s Data Breach Investigations Report released by Verizon, phishing is named as one of the top four key paths for threat actors to achieve success in their attacks. Phishing is also ranked as one of the top five sources of breaches. In short, phishing is a real threat to today’s organizations.
And while many people may assume that the users in their organization would know better than to click on a link or act on a text, it’s never a bad idea to revisit phishing at its core to freshen up—or level up—your knowledge.
And that’s what I'll do in this blog, focusing on a specific phishing attempt as a concrete example.
What Is Phishing?
Let’s start with the basics: what is phishing?
NIST offers a solid definition:
A technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a web site, in which the perpetrator masquerades as a legitimate business or reputable person.
In essence, phishing is an attempt to lure someone into giving away their sensitive information by posing as a legitimate person or entity.
When you think about it, phishing evades all logic in terms of what most people envision when they hear the word hacker. Hackers are supposed to be basement dwellers who bruteforce their way into networks through malicious code.
But here’s the million-dollar question for threat actors: why bruteforce your way in when you could gain someone’s credentials simply by asking for them?
The Attempt
I was recently targeted by a phishing attempt via text (this is called smishing—SMS phishing) that was clearly just that. But one of the best ways to learn how to analyze more sophisticated phishing attempts is to return to the basics.
Without further ado, here’s the magnificent attempt in all its glory that wound up on my phone:
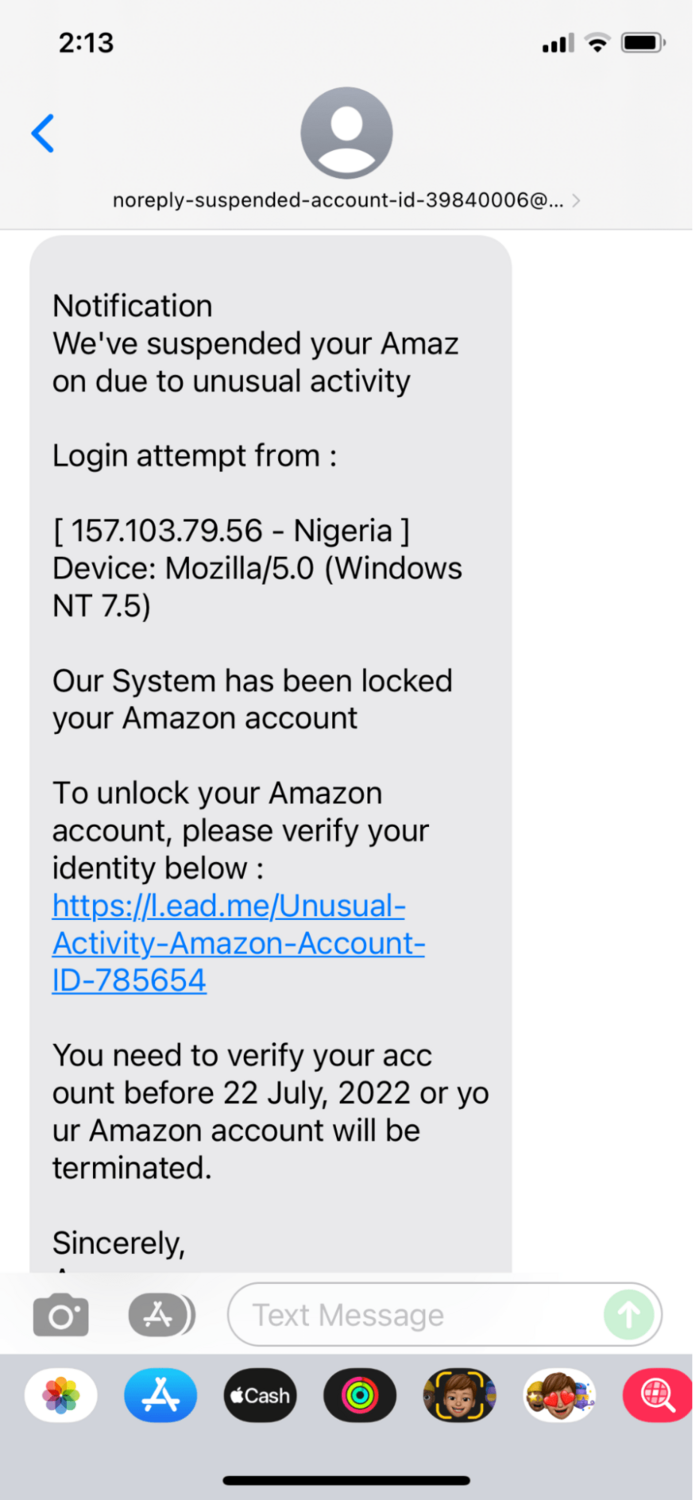
Let’s dig into this suspicious text and talk about a few of the ways we can research its legitimacy.
1. The Sender
First, let’s take a look at the sender. Five hundred characters later, the entire “from” line is legible:
noreply-suspended-account-id-39840006@blogger-bukuharian[.]art
There’s a lot we can do to verify who this sender actually is, but for simplicity’s sake, let’s start with Domain Dossier, ICANN and urlscan.io.
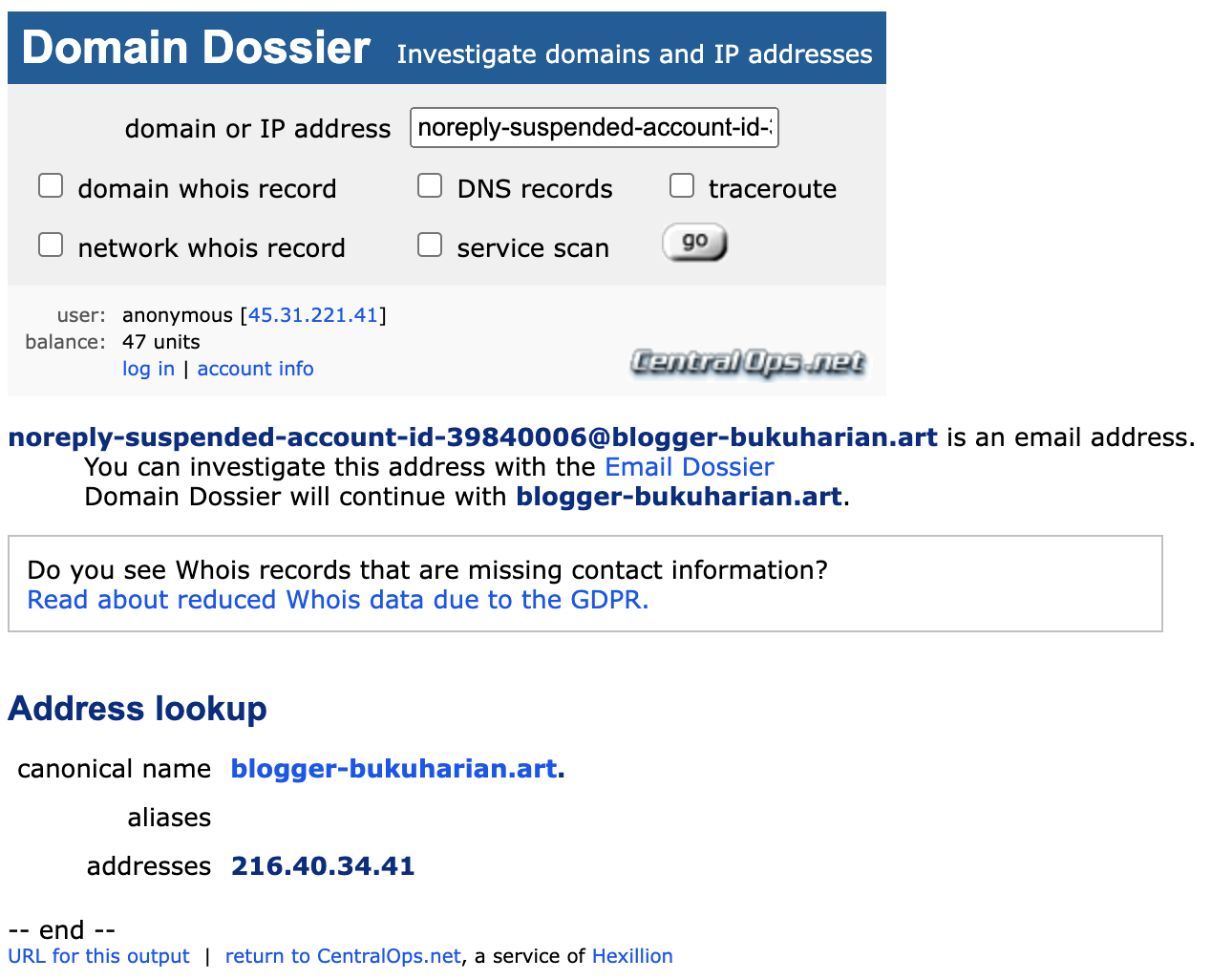
Domain Dossier is a great database to search through public records to learn about domain names and IP addresses, while ICANN provides us with some additional supplementary information, such as when the domain was registered and who it’s registered to. urlscan.io is an incredibly cool site that grabs a screenshot of the page you’d land on if you were to follow a link.
Domain Dossier returns a canonical name (the domain name with actual IP address records) of blogger-bukuharian[.]art linking to the IP address 216[.]40[.]34[.]41:
ICANN offers up some additional helpful information:
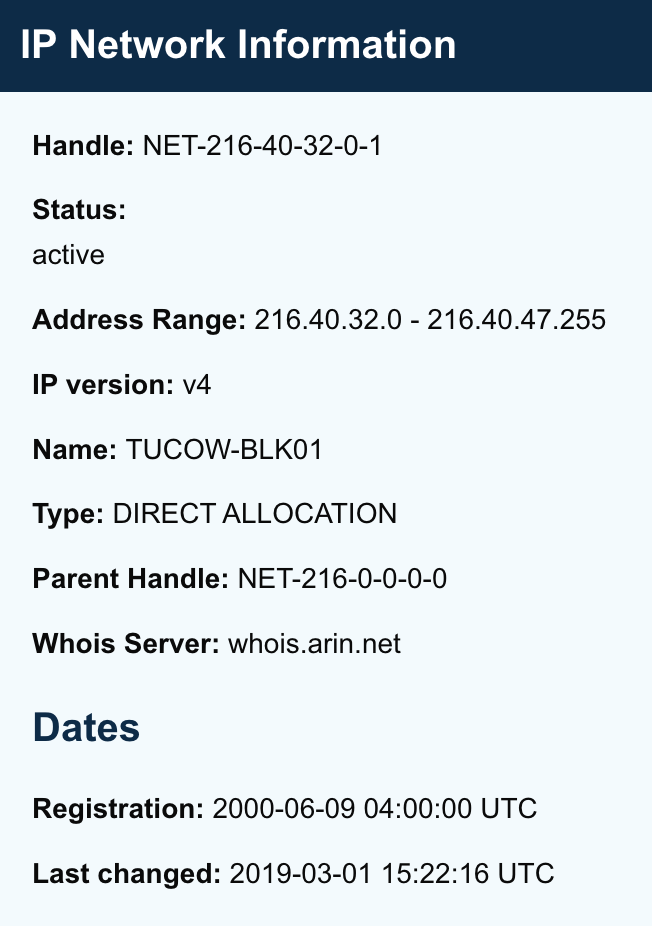
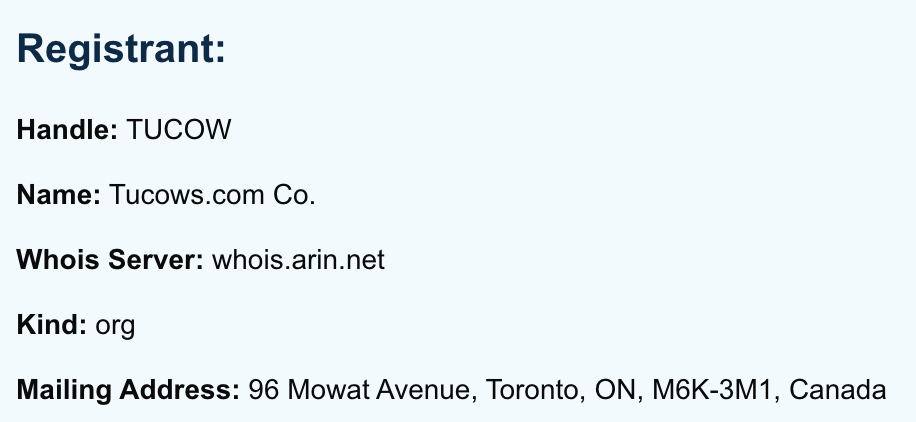
It begs the question, why is Amazon contacting me from a Tucow IP? Shouldn’t it be linked to Amazon’s domain, which is linked to Amazon Technologies Inc.? 🤔
I’ll offer up one more tool in my toolbox: urlscan.io. I copied and pasted the canonical name into this site to yield this interesting result:
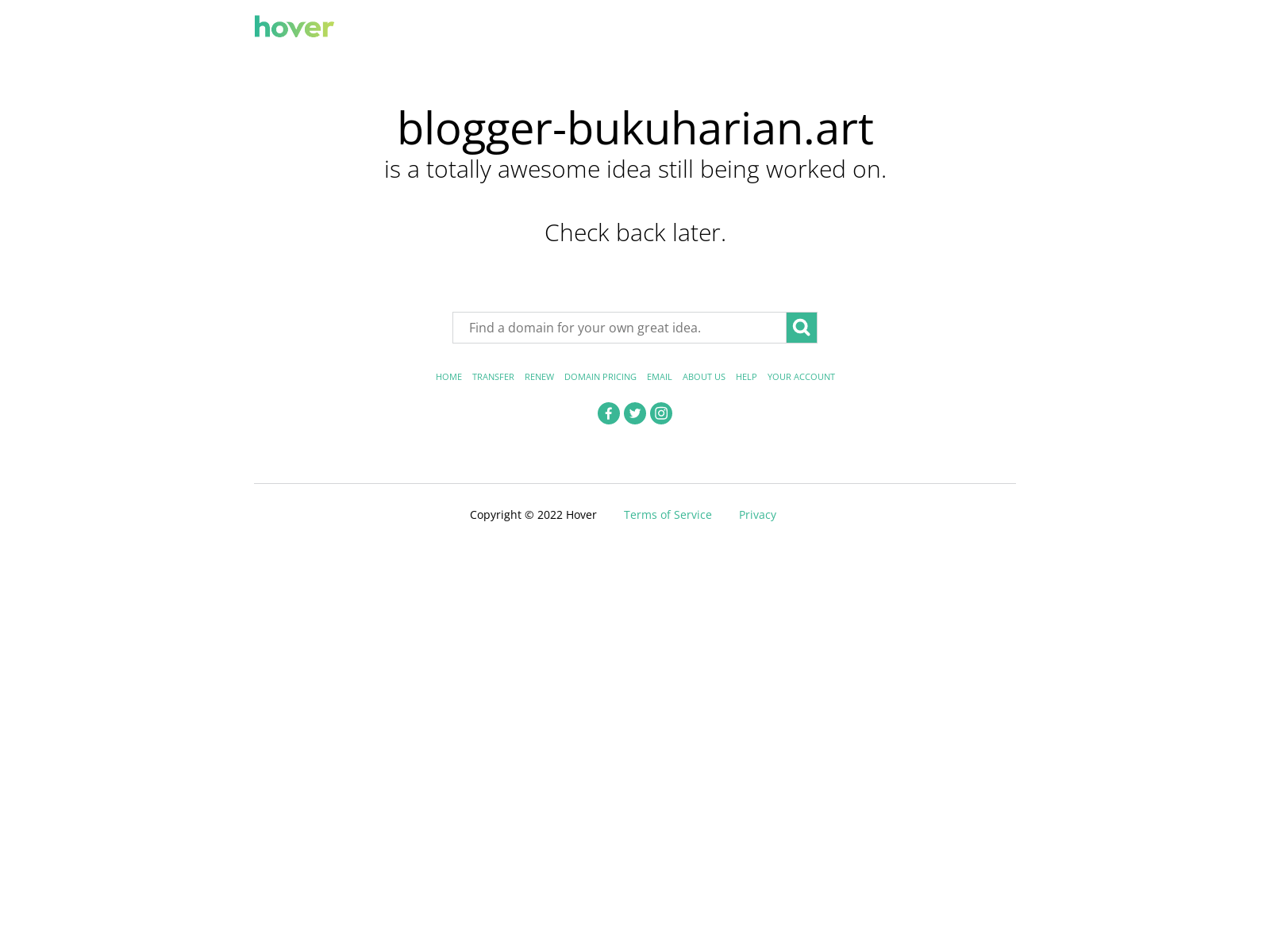
Doesn’t look like Amazon to me! But to be sure, let’s keep digging.
2. The Link
What would a phishing attempt be without a link to hook, line and sinker?
Never fear—this questionable text included a link as well:
https://l[.]ead[.]me/Unusual-Activity-Amazon-Account-ID-785654
I shop at Amazon enough to know that most shortened Amazon links come in variations of amzn.to, but let’s dig into the link they sent, anyway—for the sake of learning, of course.
When I have a link, my go-to is always urlscan.io, so let’s run this unusual link through this tool*:
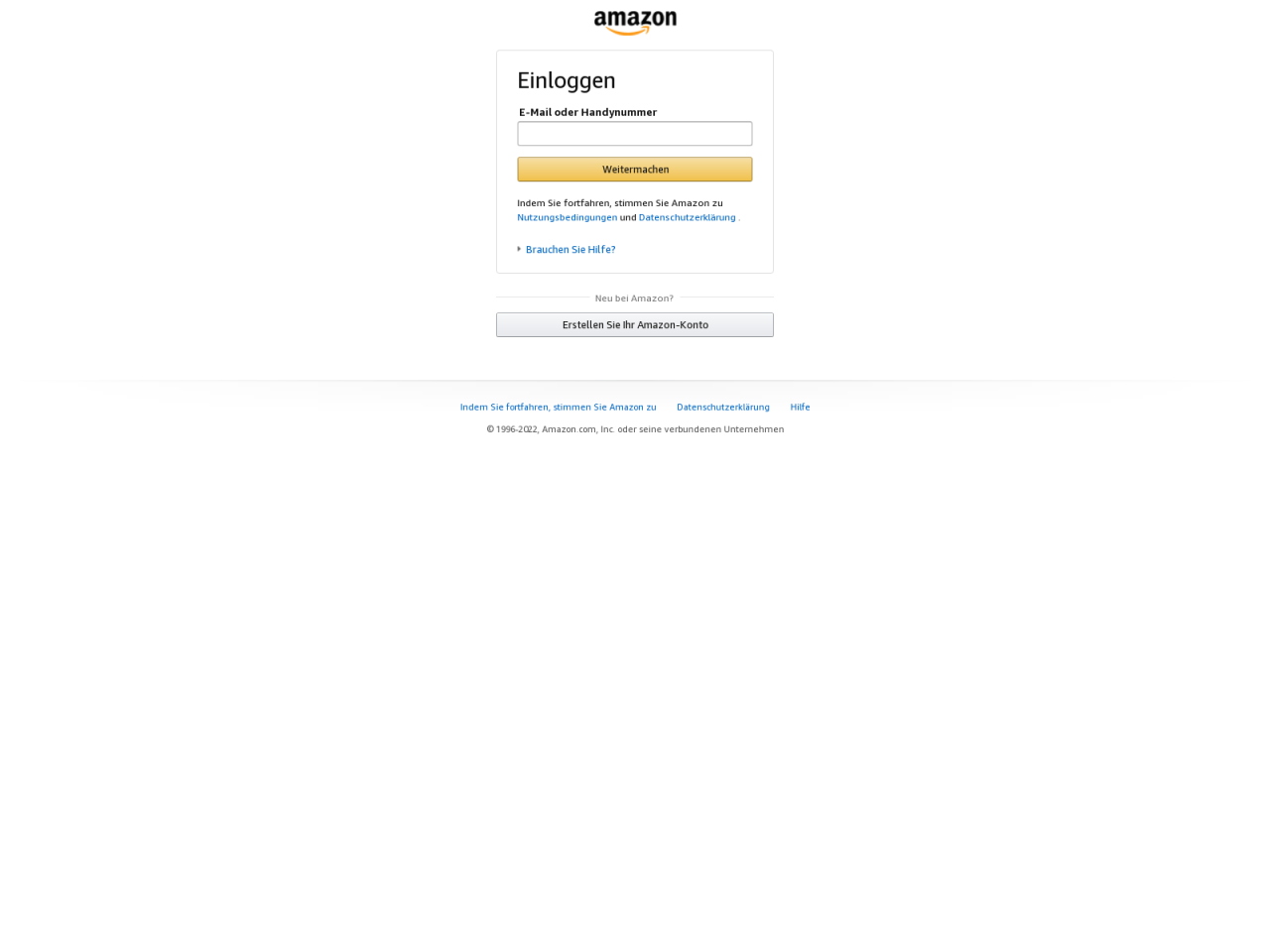
That definitely looks like Amazon, sort of—but not in any language I’m used to.
What’s notable here is I’m being asked to log into my Amazon account to save it. What would really happen if I were to enter in my credentials is that they’d be going right into the hands of the bad actors—not Amazon.
But the real kicker? Check out the results returned to me after copying and pasting the link into VirusTotal:
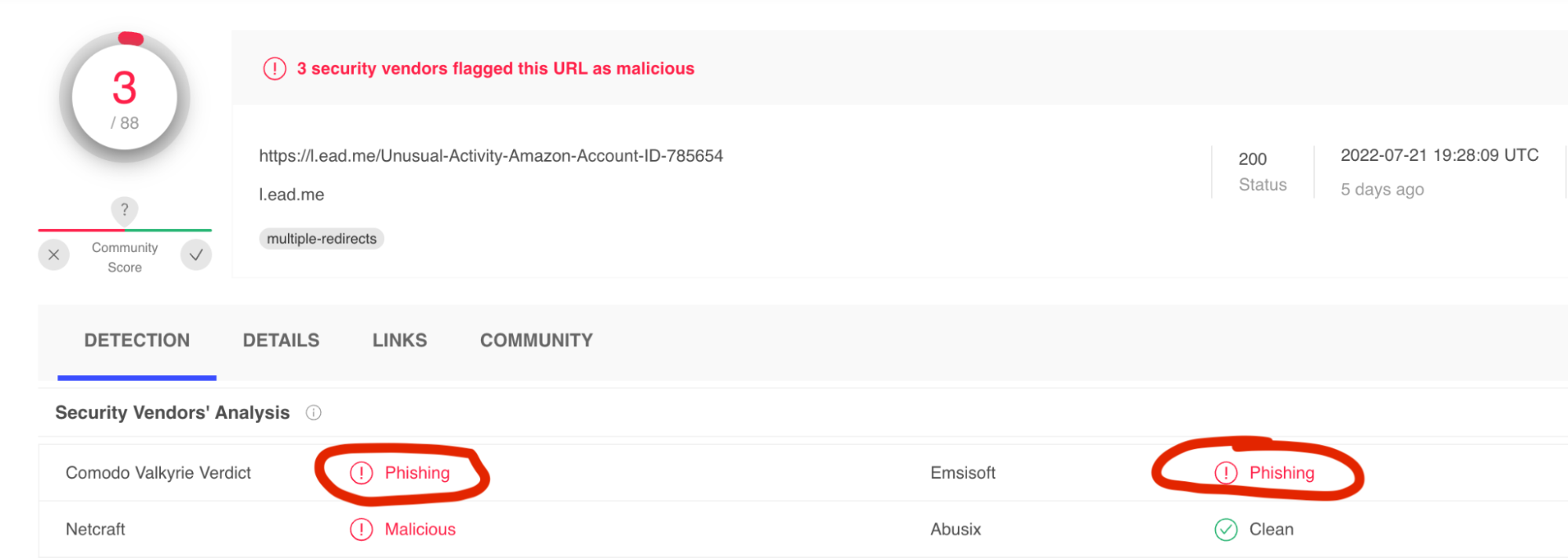
Glad to know it’s not just me, I guess. 😅
* I want to note that the above screenshot was the result I got via urlscan.io the day I received this text. Since then, it looks like our bad actors may have had a bad day:

You love to see it.
3. The Text
You can tell a lot about a phish by analyzing its text.
We’ve all made fun of emails and texts that include laughable typos and grammatical errors. As it turns out, these are intentional in phishing attempts.
Why? Because threat actors don’t want to waste their time on someone who won’t ultimately fall victim to their scheme.
Many people will see these mistakes and raise an eyebrow before deleting the attempt immediately. Others will either ignore or not notice the mistakes—and threat actors are betting that those people will be gullible enough to engage with their phish.
Plus, phishing attempts with spelling/grammatical mistakes may even be more likely to bypass spam filters. These filters scan for specific words that threat actors tend to use in their phishing attempts. A typo makes it that much harder for the spam filter to flag the email.
Interestingly, this attempt doesn’t include too many red flags in the text itself. Aside from some unusual line breaks and an occasional grammatical error, this text checks out. These awkward line breaks are certainly worth flagging, though.
4. The Vibes
Sometimes, you just gotta trust your gut.
I don’t like feeling pressured. Most people don’t. And hackers are betting on you to act fast to eliminate the discomfort a sense of urgency carries.
In the text I received, the sender initiated a sense of urgency in two ways:
- By telling me my beloved Amazon account has been suspended—a red alert, crisis situation in my household
- By telling me I only have 24 hours to remedy the situation
A good rule of thumb is to always take a beat before taking action. So many phishing attempts are successful because people act on their emotions. When those emotions run high and something valuable to them is at stake, they’re more likely to act on impulse versus logic.
A real, reputable business will give you ample time to remedy a situation before locking you out for good, and there are exceptions to every “time-sensitive” rule. When in doubt, slow down and rationalize!
***
I hope this dive into a laughable phishing attempt was enjoyable for you—and even if this is elementary knowledge in your world, I hope it’ll perhaps help a friend or family member stop and think before succumbing to the next phishing attempt that targets them.
And by the way, in case you were waiting with bated breath: my Amazon account is just fine. 😉
















