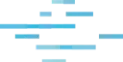

Huntress vs. Cynet
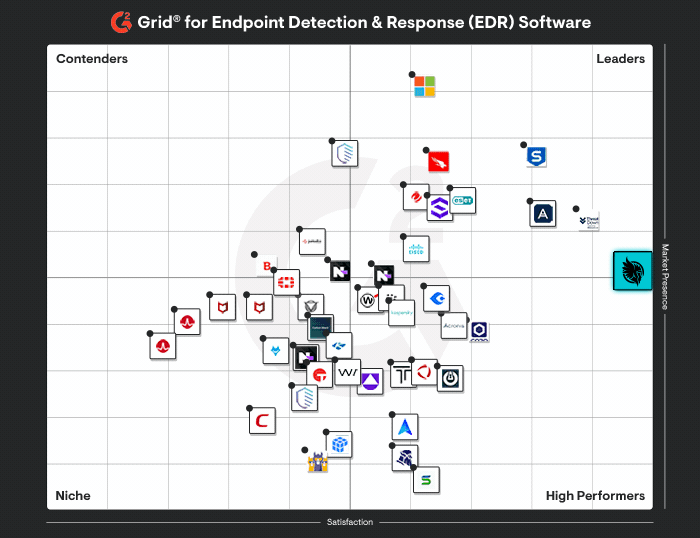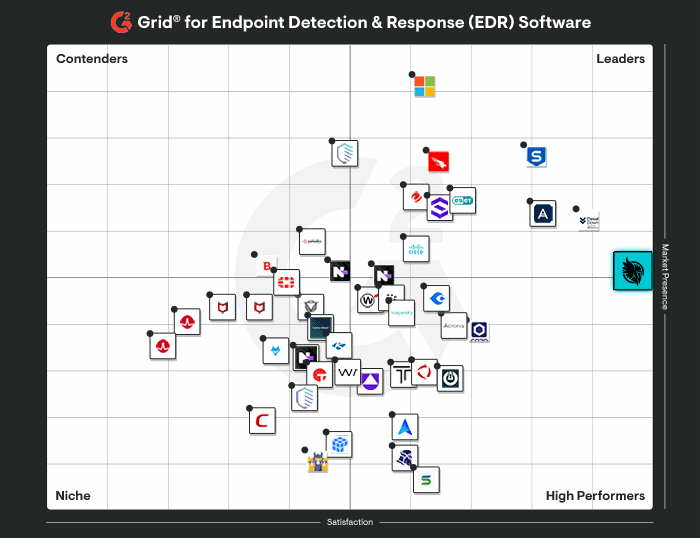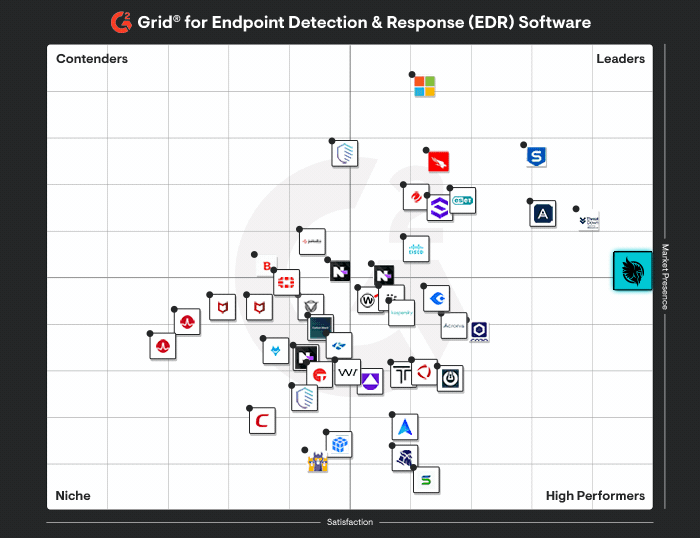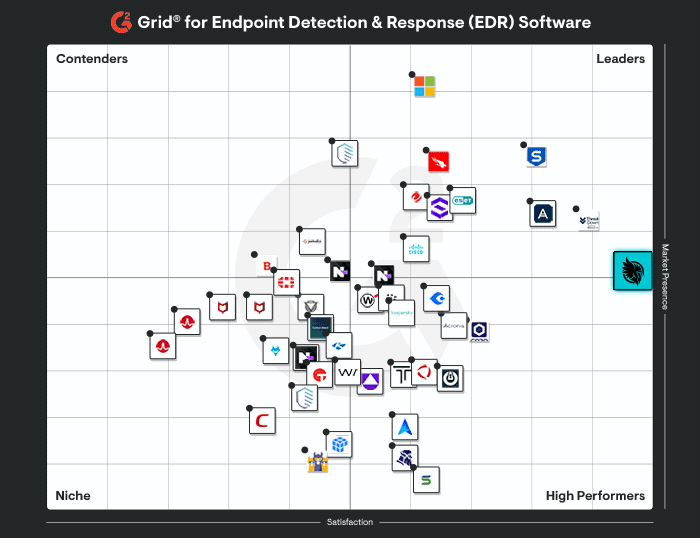
Huntress doesn’t just give you a single pane of glass like Cynet. Huntress gives you a full, 24/7 Security Operations Center behind it, built for endpoints and identities. See why human-led detection beats an automated platform you have to manage yourself.
Huntress outperforms Cynet at every turn, delivering security with precision and simplicity tailored for organizations of all sizes.
-
Human-led outcomes vs. automated noise.
-
Comprehensive solutions include the tech, threat experts, and 24/7 AI-assisted SOC for one simple, affordable price.
-
Built for every business.
Experience the difference of enterprise-grade protection and industry-leading threat expertise. Schedule a demo today.

Huntress vs Cynet


Fully managed MDR with human-validated alerts, investigation, and response. Analysts handle detection and escalation end-to-end.

Automated-first XDR platform with MDR support via CyOps, requiring customer tuning and workflow management.


Expert threat hunters; not just monitoring but interpreting and acting on your behalf.

Heavy Reliance on automation and MDR support as an option.


Dedicated 24/7 SOC that acts as an extension of your team across all modules.

Global SOC supports the platform, but core detection relies heavily on automated analytics.


Low-noise alerts, human context, and predictable outcomes without security engineering effort.

Broad feature set increases operational complexity and tuning requirements.


Purpose-built ITDR focused on identity attack tradecraft with human validation and guided response.

Identity telemetry and correlation as part of XDR, without a dedicated ITDR discipline.


Managed SIEM designed for clarity, investigation, and compliance without tuning overhead.

SIEM-style correlation within XDR, requiring configuration and ongoing management.


Native SAT with phishing simulations and behavior-driven reporting, backed by threat intelligence.

No native security awareness training offering.


Purpose-built managed platform that is focused on detecting real-world attacker tradecraft as it is actively used, with continuous detection engineering, human validation, and response tuned to current adversary behavior rather than generic coverage.

Broad XDR platform that consolidates endpoint, network, identity, and log telemetry into a single interface, best suited for teams that are prepared to manage, tune, and interpret large volumes of security data on their own.



A Multi-Layer Security Solution
Get Security Outcomes, Not Just a Platform
Enterprise-grade technology, delivered as a service
Human expertise is built in
Fully-managed, 24/7 Coverage

The Huntress Managed Security Platform