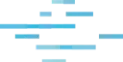

Huntress vs. Arctic Wolf
See why businesses choose Huntress over Arctic Wolf’s solutions
Bought, not built tech stack
Focus on threat monitoring and alerting, leaving remediation to customers
Support
Experience the difference of enterprise-grade security and expertise. Request a demo today or experience it yourself with our free trial.

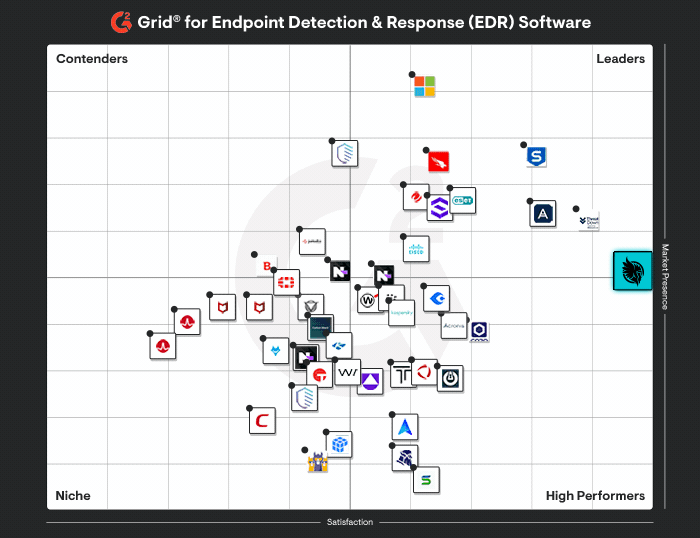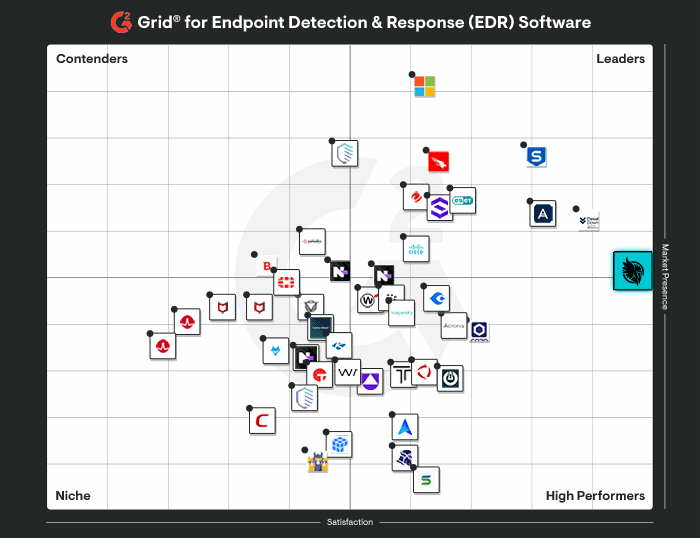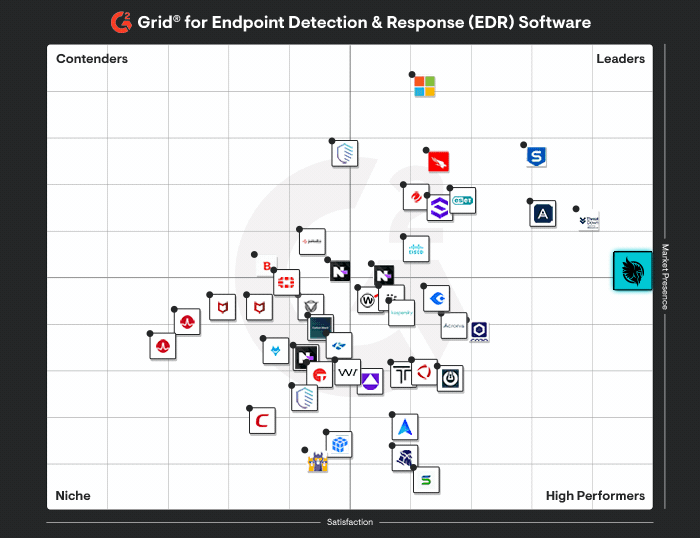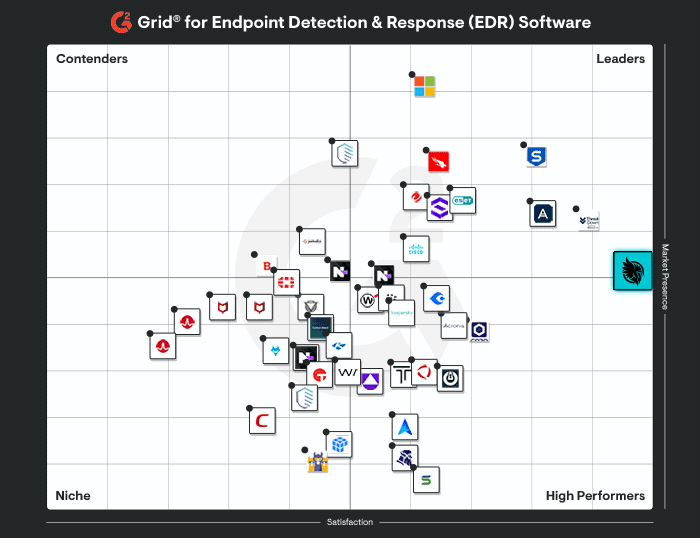
Huntress vs Artic Wolf


Huntress delivers predictable security outcomes with transparent guidance, backed by a 24/7 AI-assisted SOC, <1% false positives, and 8-minute MTTR.

Bought, not built tech stack is prone to false positives.


Industry-recognized team of threat experts, CVE Naming Authority, and Verizon DBIR contributor.

Lack of industry-recognition and community-involvement.


Huntress 24/7 SOC reviews alerts, provides context, and remediates for you with permission. Delivers remediation steps in plain text, along with a 1-click Assisted Remediation button.

Focus on threat monitoring and alerting. Post-incident support and remediation limited to just guidance. Active remediation requires an IR retainer.


Huntress Managed EDR and 24/7 SOC is included at a single, affordable price, with Managed AV for Microsoft Defender included at no extra cost.

Incident remediation costs extra.


Huntress focuses on protecting against advanced threats with Managed MDR, ITDR, SIEM, and SAT.

Arctic Wolf bundles cybersecurity with IT management by partnering with other providers, offering services like RMM, backup, and other core IT tools.


We own the tech stack, so detection and response are smarter, faster, and built for your needs.

They bolt on someone else’s tech (or use their recently acquired EDR, Cylance) that could lead to slower detections and unpredictable response outcomes.


Purpose-built EDR that delivers high-accuracy threat detection, < 1% false positive rate, 24/7 monitoring with fast response.

Acquired Cylance. Their MDR service integrates with other EDR technologies.


Identity threat detection and response for M365 with 24/7 monitoring and human-validated alerts

Recognized as a broad SOC/MDR player; identity enhancements are newer to their stack.


Built from the ground up to reduce the complexity and cost of log collection, analysis, and storage. Simple pricing per log source backed by our 24/7 SOC

For larger enterprises that have heterogeneous systems (on-prem/ cloud/ hybrid) and lots of logs/telemetry.


Managed by security experts and integrates with the broader Huntress platform. By linking endpoint, ITDR, and SIEM data, training can align with real threats and trigger assignments based on actual incidents.

Frequent, concierge-delivered microlearning + quizzes + phishing simulations.



Get Next-Level Outcomes with Huntress
Purpose-built Tech, Never Bolted Together
Industry-recognized Human Expertise
Fully-managed, 24/7 Coverage

The Huntress Managed Security Platform