Data exfiltration has quietly become one of the fastest-moving—and most damaging—outcomes of modern cyberattacks.
Today’s attackers aren’t breaking in and lurking for weeks before touching sensitive data. They’re compromising identities and immediately enumerating and exfiltrating data, often within seconds of initial access. In many cases, this happens before traditional security tools even generate usable logs or recognizable indicators of compromise.
As more organizations move sensitive intellectual property, financial data, regulated records, and operational systems to cloud platforms like Microsoft 365 and Google Workspace, the blast radius of identity compromise continues to expand. Once an attacker gains access to a legitimate identity, they inherit trust, permissions, and visibility across massive data stores. The result? Data walks out the door faster than most security teams can react.
The data backs this up. The Verizon Data Breach Investigations Report (DBIR) continues to show that credential compromise and misuse of legitimate access remain among the most common initial attack vectors in confirmed breaches, while data disclosure remains one of the most frequent breach outcomes. Identity abuse paired with rapid data access has become the attacker’s preferred path to impact—quieter, faster, and harder to detect than traditional malware-driven intrusions.
That reality is exactly why Huntress Managed ITDR continues to evolve. And why we’re excited to introduce a powerful new capability: the Incident Report Timeline.
Why data exfiltration visibility matters
Stopping an identity-based attack quickly is critical, but understanding what happened during the attack is just as important.
When data exfiltration is suspected, organizations immediately face tough questions:
-
What data may have been accessed or stolen?
-
How long did the attacker have access?
-
What actions did they take inside the environment?
-
Were additional identities or systems impacted?
-
What regulatory, legal, or customer notifications may be required?
Without clear visibility, teams are often forced to rely on fragmented logs, scattered alerts, or educated guesses across multiple tools. That uncertainty slows response, increases business risk, and complicates executive and customer communication.
Security leaders don’t just need alerts. They need context, clarity, and confidence.
The Incident Timeline delivers exactly that.
Introducing the Incident Report Timeline in Managed ITDR
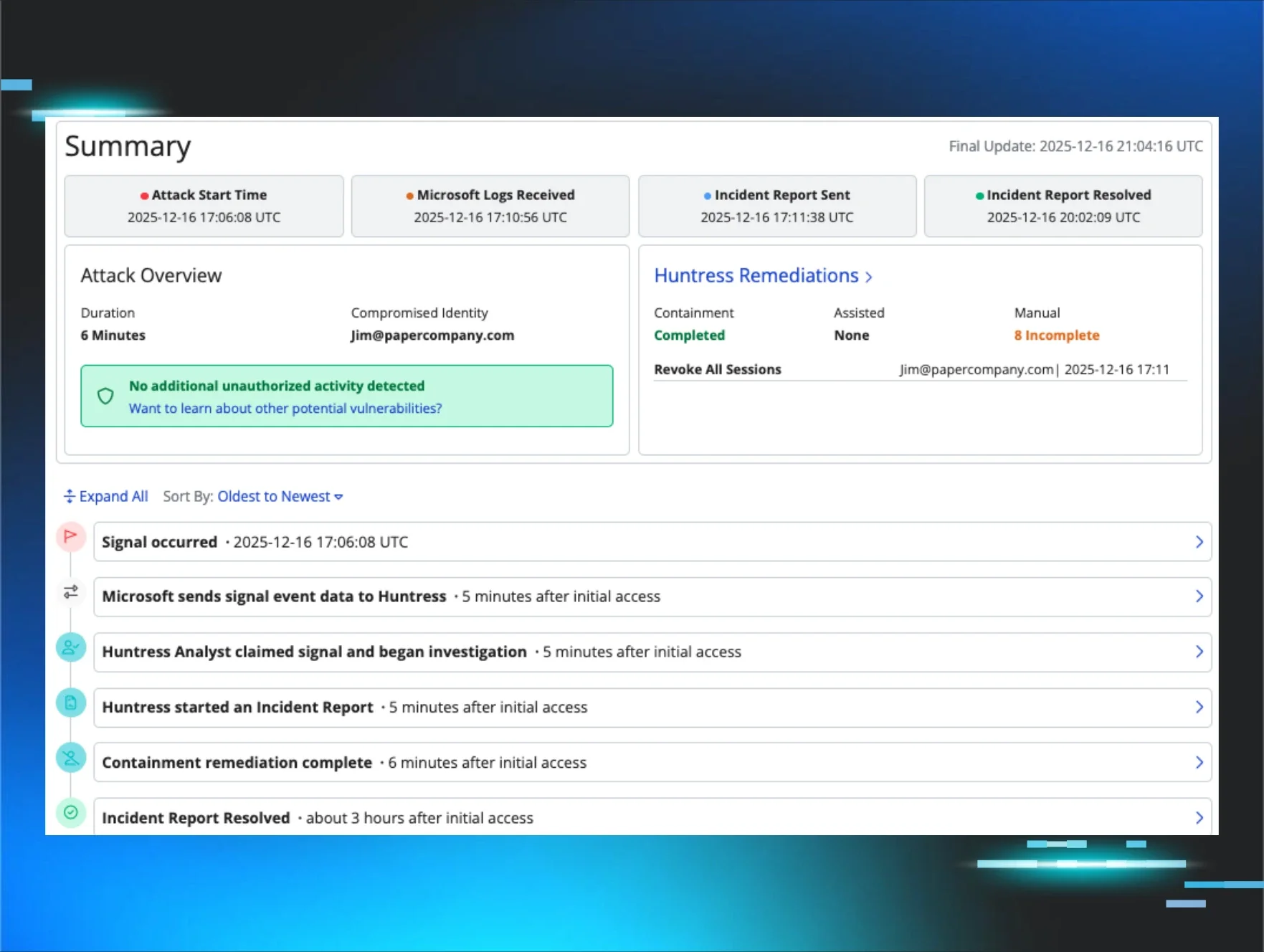
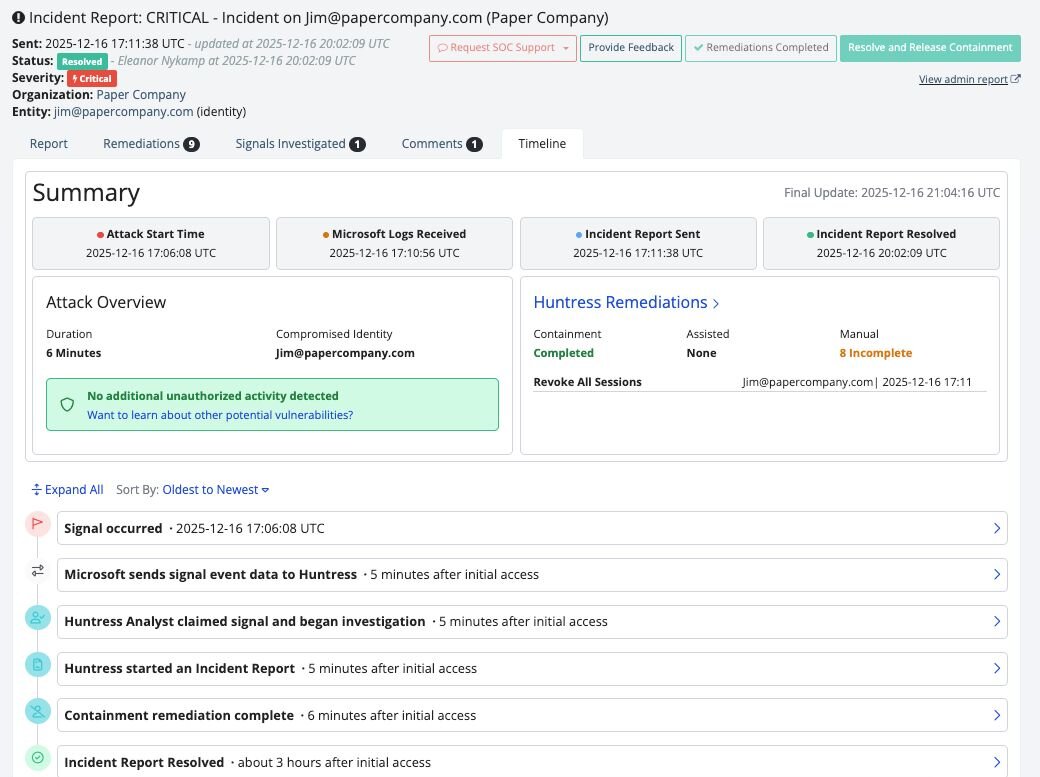
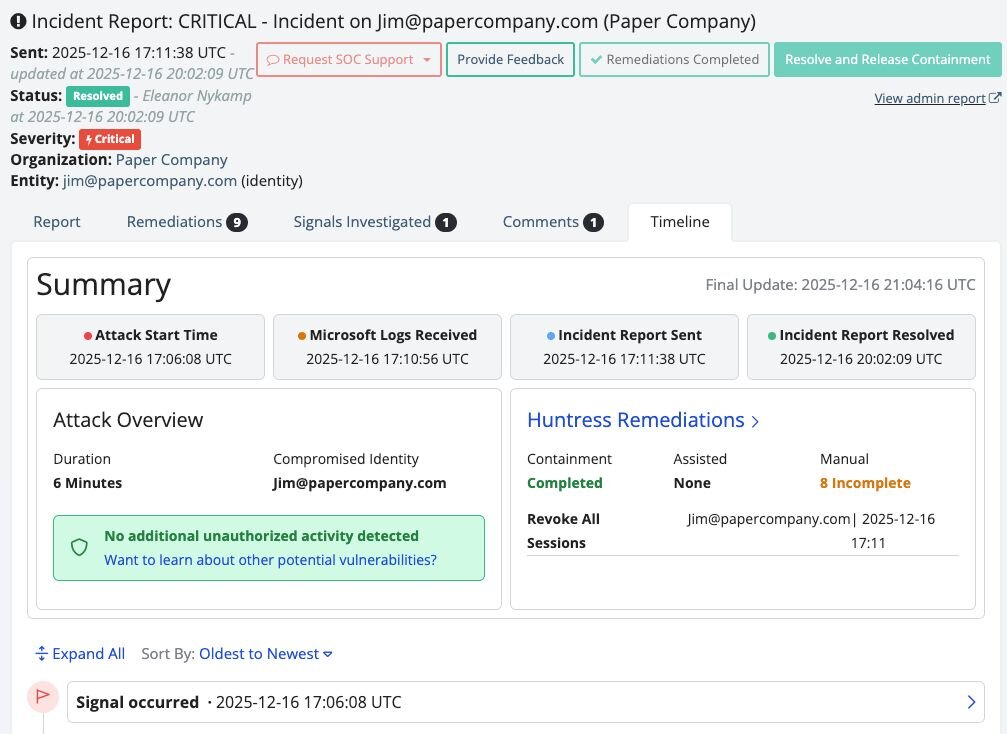
The Incident Report Timeline gives Managed ITDR customers a detailed, chronological view of what happened during an identity-driven incident—from initial detection through Huntress-led remediation and containment.
Instead of manually stitching together raw logs or jumping between dashboards, customers get a clear narrative of:
-
When suspicious activity began
-
What signals triggered investigation
-
What actions the attacker performed
-
How Huntress analysts validated the threat
-
What containment and remediation steps were executed
-
When the incident was fully resolved
This transforms incident response from a black box into a transparent story, one teams can easily understand, communicate, and act on.
An example of what customers see inside the new timeline.
It also reinforces something customers consistently value about Huntress—you’re not just getting alerts, you’re getting answers.
See the attacker’s path—not just the alert
One of the most powerful aspects of the Incident Report Timeline is that it doesn’t just show what Huntress did; it shows what the attacker did.
Customers gain meaningful insight into adversary behavior inside their environment, including:
-
Enumeration activity and access patterns
-
Suspicious session behavior
-
Indicators of potential data access or movement
-
Correlation between identity activity and cloud telemetry
-
Timing and sequencing of attacker actions
This level of visibility allows organizations to understand not just that an incident occurred, but how it unfolded and where residual risk may exist. That context directly informs smarter decisions around access reviews, credential resets, conditional access policies, security awareness training, and long-term hardening strategies.
In short, it turns incident data into operational intelligence.
By clearly mapping response actions against the incident lifecycle, teams can validate that threats were handled decisively and efficiently.
Faster decisions, better outcomes
When an identity compromise involves potential data exposure, speed matters. But clarity matters even more.
The Incident Report Timeline enables teams to quickly assess impact and confidently determine next steps, including:
-
Whether sensitive data was likely accessed
-
Whether additional remediation is required
-
Whether legal or compliance escalation is necessary
-
Whether further investigation or monitoring is warranted
Instead of spending hours reconstructing events, teams can immediately understand what happened and move forward with precision. That reduces operational drag, shortens recovery timelines, and minimizes both business disruption and downstream risk.
For security teams already stretched thin, that efficiency is not a luxury. It’s essential.
A major win for MSPs and their customers
For managed service providers (MSPs), the Incident Report Timeline delivers even more strategic value.
MSPs are frequently responsible for explaining incident impact and response actions to business stakeholders who may not speak security fluently. The timeline provides a professional, easy-to-consume artifact that partners can confidently share with end customers.
Instead of vague summaries or screenshots pulled from multiple tools, MSPs can present:
-
A clear timeline of the incident
-
Proof of rapid detection and response
-
Transparent remediation documentation
-
Concrete evidence of security value delivered
This elevates customer conversations from reactive troubleshooting to proactive risk management, reinforcing the MSP’s role as a trusted security partner rather than just a ticket resolver.
Built for the reality of identity-driven attacks
Modern attacks move fast. Identities are abused instantly. Data is targeted immediately.
Security teams can no longer afford to rely solely on alerts and after-the-fact log analysis. They need visibility that keeps pace with attacker speed and business impact.
The Incident Report Timeline brings clarity to the moments that matter most, helping organizations understand attacker behavior, validate response effectiveness, and make informed decisions after identity-based incidents.
As identity continues to replace endpoints as the primary attack surface, Managed ITDR keeps raising the bar - giving customers and partners the insight they need to protect sensitive data, respond decisively, and stay ahead of modern attackers.
👉Try Managed ITDR for free today!