Background / Summary
The Huntress DE&TH (Detection Engineering and Threat Hunting) Team has observed in-the-wild exploitation of a privileged account takeover vulnerability (CVE-2026-23760) in SmarterTool’s SmarterMail application that has resulted in successful remote code execution. Our testing has indicated that versions of SmarterMail prior to Build 9511 are vulnerable. Users of SmarterMail are urged to upgrade to the latest version, Build 9511, released on January 15, 2026.
Note that this is separate from the ongoing mass exploitation of CVE-2025-52691, an arbitrary file upload vulnerability in SmarterMail that also leads to remote code execution. At the time of writing Huntress contacted SmarterTools and held off publishing whilst CVE-2026-23760 was published as it was already in the process of being disclosed by WatchTowr. Despite this, Huntress has observed a different method being used for remote code execution in the wild.
In-depth analysis of the threat
Huntress’ DE&TH Team has observed in-the-wild exploitation of a privileged account takeover vulnerability within the SmarterMail application. Once exploited, the threat actor used a hijacked privileged account to access the SmarterMail System Events functionality, wherein malicious System Events were created to execute reconnaissance commands on vulnerable hosts.
A review of the relevant application logs on exploited hosts has shown that the threat actor(s) made a series of HTTP POST requests to the SmarterMail application to achieve their objectives.
Table 1 (below) presents the requests in the order in which they were observed, along with a corresponding note to detail their relevance in the attack.
|
Request |
Purpose |
|
POST /api/v1/auth/force-reset-password |
Exploits the account takeover vulnerability to gain access to a privileged user account. |
|
POST /api/v1/auth/authenticate-user |
Obtains a valid access token with the privileged user’s credentials. |
|
POST /api/v1/settings/sysadmin/event-hook |
Configures a malicious System Event. We suspect that the System Event was configured to execute the threat actor’s reconnaissance command(s) when a new domain was added to the SmarterMail application. |
|
POST /api/v1/settings/sysadmin/domain-put |
Adds a new domain to SmarterMail, and therefore triggers the System Event created in the previous request. |
|
POST /api/v1/settings/sysadmin/domain-delete/google.abc[.]com/true |
Clean-up activities as a part of indicator removal. |
|
POST /api/v1/settings/sysadmin/event-hook-delete |
Clean-up activities as a part of indicator removal. |
These requests were made in quick succession across multiple customers, suggesting mass automated exploitation.
Vulnerability analysis
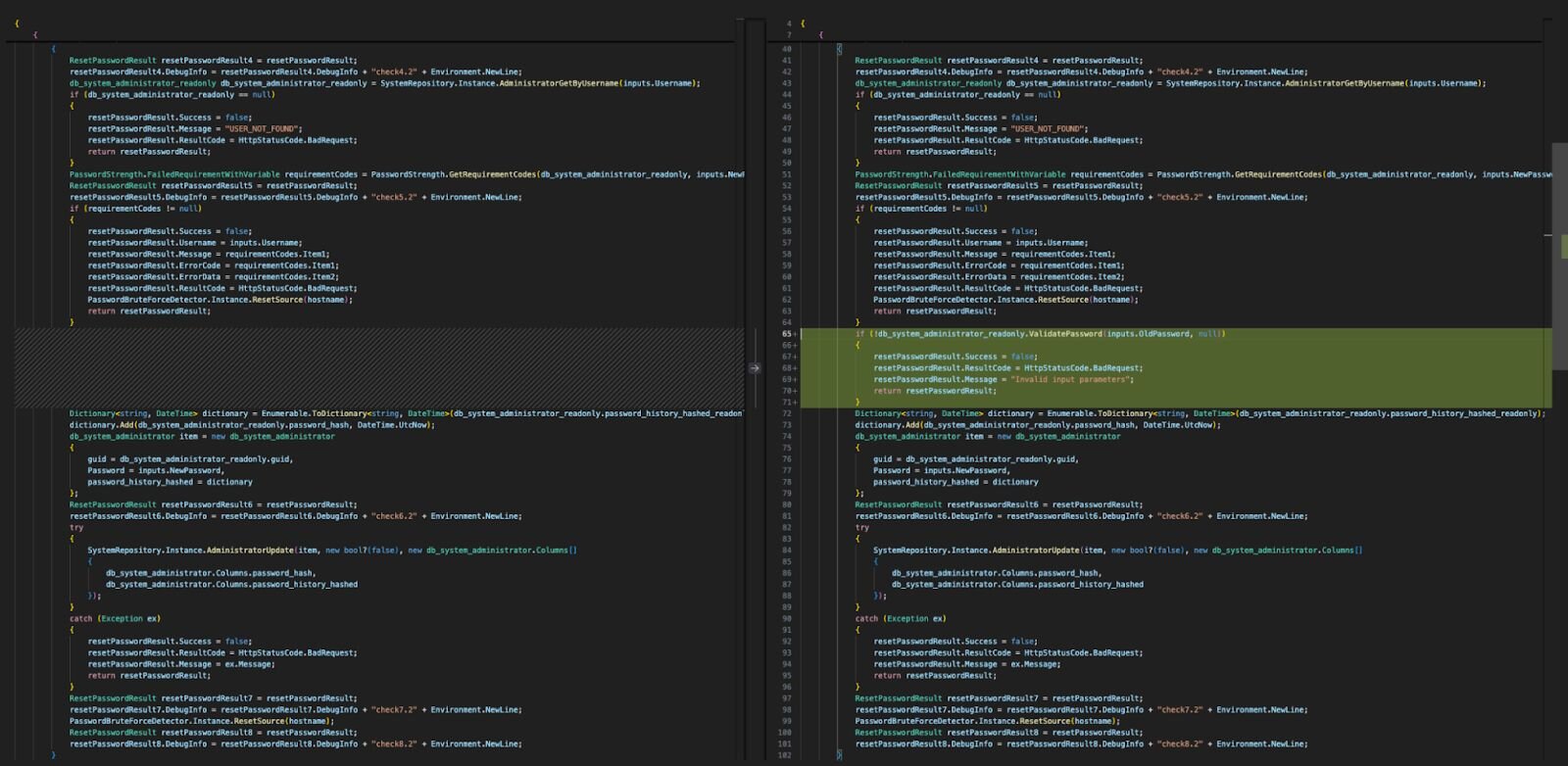
Comparing version 9504 which was released on January 8, and 9511 which was released on January 15th, we can see the root cause of the vulnerability being fixed, whereby it previously didn’t check if the old password submitted to /api/v1/auth/force-reset-password was valid or not.
Figure 1: Comparison of SmarterMail binary versions 9504 and 9511
Huntress has successfully created an exploit for the aforementioned vulnerability which demonstrates that a privileged user’s password can be changed without authentication.
Conclusion
Given the severity of this vulnerability, active exploitation, and exploitation of the additional CVE-2025-52691 being observed in the wild, businesses should prioritize the deployment of SmarterMail updates and review any outdated systems for signs of infection.
Indicators of compromise
|
Item |
Details |
|
142.111.152[.]57 142.111.152[.]229 155.2.215[.]66 142.111.152[.]54 142.111.152[.]53 142.111.152[.]222 142.111.152[.]159 142.111.152[.]165 155.2.215[.]70 142.111.152[.]49 155.2.215[.]74 142.111.152[.]160 155.2.215[.]73 142.111.152[.]51 155.2.215[.]60 142.111.152[.]151 142.111.152[.]46 155.2.215[.]68 142.111.152[.]155 142.111.152[.]45 155.2.215[.]72 155.2.215[.]67 142.111.152[.]47 142.111.152[.]59 142.111.152[.]56 142.111.152[.]154 142.111.152[.]150 155.2.215[.]62 |
IP addresses observed as the source of the attacks. |
|
python-requests/2.32.4 |
User-agent observed conducting the attacks. Note: This is a default user-agent used by the Python requests module version 2.32.4 |
|
C:\Program Files (x86)\SmarterTools\SmarterMail\Service\wwwroot\result.txt |
File containing output of reconnaissance. |
|
/api/v1/auth/force-reset-password /api/v1/auth/authenticate-user /api/v1/settings/sysadmin/event-hook /api/v1/settings/sysadmin/domain-put /api/v1/settings/sysadmin/domain-delete/google.abc.com/true /api/v1/settings/sysadmin/event-hook-delete |
POST requests to these endpoints were observed in the attacks. |