At Huntress, we’re constantly listening to our partners. And this one’s been loud and clear.
We’re excited to announce that one of the most requested features for Huntress Managed ITDR is now live: identity disablement and re-enablement for Active Directory (AD) synced identities, also known as hybrid identities.
This update closes a significant gap in our containment and remediation capabilities—and it brings protection parity to the 47%+ of identities using AD sync in their Microsoft 365 configurations. Previously, these environments couldn’t fully benefit from Huntress-initiated identity containment. Now, that changes.
Why it matters
When Huntress detects a compromised identity, one of the most effective ways to contain the threat is to disable that identity, just like isolating a device during a malware infection. But for organizations using Microsoft Entra Connect, disabling a cloud identity wasn’t enough.
Here’s why: when cloud-based disablement occurs, the on-prem Active Directory server—via sync—often re-enables the identity, sometimes within seconds. That leaves a critical gap where attackers can continue leveraging compromised credentials, and until now, it meant Managed ITDR couldn’t complete containment for these organizations.
In fact, in up to one in four identity-related incidents in AD-synced environments, Huntress was only able to revoke sessions, often leading to multiple consecutive reports when threat actors regained access before partners were able to manually disable and remediate the malicious access.
That’s no longer the case.
How it works
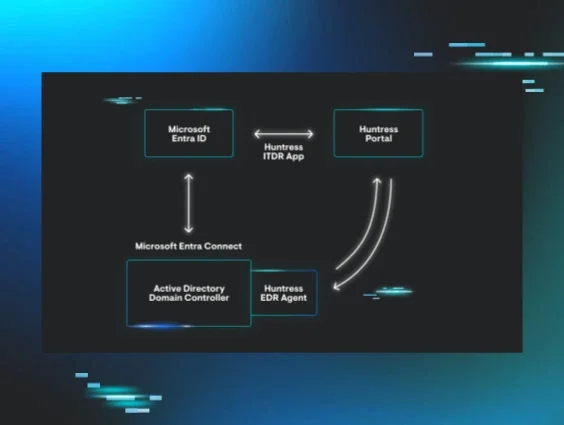
With this new capability, Managed ITDR can now disable and re-enable AD-synced identities by communicating directly with the on-prem AD server via the Huntress agent. If a customer has the Huntress agent (v0.14.22 or later) installed on a domain controller, Huntress can initiate disablement actions at both the cloud and on-prem layers simultaneously.
This change is huge. It ensures that disablement sticks, eliminating the sync “tug of war” that previously made remediation unreliable.
Here’s what’s included:
- Automatic remediation: Huntress can now disable AD-synced identities as part of real-time, analyst-driven containment.
- Assisted remediation: Partners can also trigger disablement from the Huntress portal in response to an incident report.
- Manual portal actions: Direct identity disablement and re-enablement from the portal identity page is now available for synced identities.
- Escalations: If a disablement attempt fails due to missing agents or misconfiguration, partners will now receive a dedicated escalation message so they can take action.
Microsoft Entra Connect in Huntress Managed ITDR
What you need to enable it
If you’re already using Huntress Managed EDR and have our agent deployed to your domain controllers, you’re good to go. No extra configuration needed.
If you're not using EDR but are an ITDR customer, this functionality will still work! We have a free EDR agent tier specifically for this task, and it's available in the Huntress Portal menu.
How it stands up to the competition
Some competitors try to work around this problem by disabling identities repeatedly on a timer—essentially racing the sync cycle and bringing up reliability concerns at scale. That’s better than nothing, but still leaves critical gaps attackers can exploit in the window between syncs.
Our approach is surgical. We don’t just keep hammering the identity in the cloud. We disable it on-prem and in the cloud at the same time, using our agent as a bridge. That’s how you stop the threat, immediately and reliably.
A quick note on tradeoffs
Disabling a synced identity will cut off that user from all AD-integrated systems—email, desktops, cloud apps, everything. That’s intentional. If an identity is compromised, we want full lockdown until it’s secure again.
That said, partners who need exceptions can use our existing identity exclusion features. We’ll also be rolling out in-portal visibility and alerts to help partners understand when they’re in a directory-synced environment and what actions are available to them.
Built for the real world
This capability isn’t theoretical. It was built with the complexities of real-world partner environments in mind. Whether you're protecting 10 identities or 10,000, we’ve designed it to scale and work reliably without requiring you to babysit the sync cycle.
With over 2.5 million identities across 57k+ organizations in Huntress-monitored environments, this isn’t a niche edge case. It’s a critical capability that unlocks full remediation for a huge chunk of our user base.
Ready to roll
This new functionality is available now for organizations running the Huntress agent (v0.14.22+) on their domain controllers.
We’ll be sharing full deployment instructions, documentation, and support articles to guide you through rollout. And, of course, if you have any questions, our team is here to help.
Let’s shut the door on this gap for good.