Cybersecurity has hit a turning point—and it’s centered on identity. The Huntress 2025 Managed ITDR Report makes one thing painfully clear: identity isn’t just an attack vector. It’s the attack surface.
While many businesses are still securing endpoints and hoping multi-factor authentication (MFA) will hold the line, attackers have moved on. They’re exploiting logins, session tokens, rogue apps, and overlooked configurations in Microsoft 365. And they’re doing it at scale.
This new report, based on input from over 600 IT and security professionals, delivers some eye-opening (and wallet-emptying) truths about how identity-based attacks are surging and why detection and response timelines are failing to keep up.
Here’s what you need to know—and why you should download the full report today.
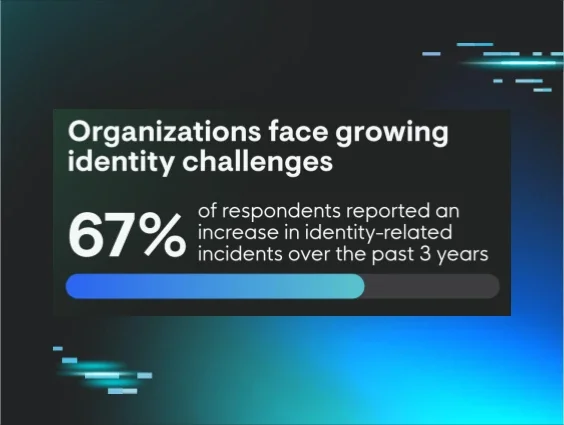
The identity threat surge: It’s not just coming. It’s here.
Let’s start with the wake-up call:
- 67% of organizations have seen identity-related incidents increase in just the past 3 years.
-
More than 1 in 3 say identity-based attacks now make up over 40% of all their security incidents.
-
Over half (51%) have been hit by business email compromise (BEC) in the past year alone.
It doesn’t stop there. Organizations are also dealing with:
- Credential theft (39%)
-
VPN misuse and session hijacking (43% and 23%, respectively)
-
Rogue or malicious applications (45%) lurking in cloud environments like Microsoft 365
These aren’t isolated incidents. They’re the new normal.
The price of delay: Identity threats cost more than time
Many businesses think they’ll have time to catch identity attacks before the damage is done. The data says otherwise:
- 68% of organizations can’t detect identity threats until after attackers have established persistence.
-
Only 25% can detect these threats within minutes.
And once detected? Half still take hours to respond.
That’s a massive window of opportunity for attackers to escalate privileges, exfiltrate data, and deploy ransomware. In fact, 32% of businesses reported losses of $100,000 or more from identity attacks.
Confidence vs. capability: The reality gap
There’s also a striking disconnect between how secure organizations feel versus how secure they actually are.
While 65% say they’re confident in detecting rogue apps, only 45% have advanced identity protection maturity.
And just 66% have implemented identity threat detection and response (ITDR) at all, despite reporting that identity attacks are more prevalent and damaging than endpoint-based ones.
It’s clear that many businesses are relying on legacy defenses like MFA and static policy rules, while attackers are already two steps ahead.

Budgets are rising. So are expectations.
There’s some good news:
- 89% of organizations say identity protection will be a top priority in the next year.
-
74% plan to implement or expand their ITDR capabilities.
-
68% have already increased their identity protection budgets in response to rising threats.
But here’s the catch: 71% still struggle to measure ROI. That leaves a big gap between investment and impact, and it means businesses need tools that actually stop attacks, not just check compliance boxes.
Why ITDR security, and why Huntress
Huntress Managed ITDR is built to address this new identity battleground. It doesn’t just flag suspicious behavior—it acts.
With capabilities like:
- Unwanted Access: Shuts down credential theft and session hijacking.
-
Shadow Workflows: Catches inbox rule abuse and stops BEC at the source.
-
Rogue Apps: Proactively detects and eliminates malicious OAuth applications before they’re used as backdoors.
…it’s no surprise that Huntress Managed ITDR has already stopped 28,000 identity-based threats in the past 6 months across 2 million identities, with an average response time of under 3 minutes.
Final word: Identity threats are on the rise, so protection is no longer optional
The Huntress 2025 Managed ITDR Report makes the stakes clear: attackers are in your inboxes, your cloud apps, and your sessions—not your firewalls.
And if you’re still relying on traditional defenses, you’re already compromised.
🧠 Want to see the full breakdown, real-world insights, and data-backed recommendations fine-tuned to your environment? Try Managed ITDR for free.
📥 Download the full Huntress 2025 Managed ITDR Report and learn how to take back control of your identity perimeter before attackers take it for you.