One of the major challenges in the cybersecurity industry is that vendors tend to overpromise and underdeliver. I see it time and time again. In fact, the biggest objection that we have to overcome when introducing Huntress to a new audience is, “My endpoint protection provider (EPP) told me that they already do this.”
In these cases, they’re referring to antivirus (AV), next-generation antivirus (NGAV), or endpoint detection and response (EDR) tools. Even after we talk about the limitations of software and attempt to dispel the myths, they sometimes go back and ask their EPP vendor directly, “Do you cover what Huntress does?” Unshockingly, the answer is always the same: “Of course we already do that for you.” But these quickly made promises don’t always meet reality.
When you’ve been in cybersecurity for any length of time, you get desensitized to the marketing buzzwords and bold claims made by industry players. Case in point: it took me five minutes to create the following list of claims from a few EPP vendor websites:
- “The End of Cyberattacks”
- “Defeating Every Attack. Every Second. Every Day.”
- “One package — everything you need”
- “Powered by Artificial intelligence”
- “Get Easy and Fast Protection Against All Threats”
- “3D online protection”
- “Complete solutions for businesses’ biggest security challenges”
- “Prevents, detects and responds to all threats”
- “Fully proven 360-degree protection”
- “Safety through advanced machine learning”
- “Prevent Tomorrow’s Threats. Today.”
Now, I’m not saying that these software vendors’ security solutions don’t have any value. They all provide some value. Actually, many are really great software tools that address the endpoint prevention layer. But the problem is, we’re equating prevention with complete protection.
Prevention ≠ Complete Security
The only real answer to building a proper cybersecurity program is to first understand your risks. Then you can use a framework of choice to establish the right processes and behaviors while adding as many layers of security as possible to address those risks.
Multiple EPP tools will invariably be among those layers. In fact, there’s a good chance that you might be using one of the tools whose website is making a claim I listed above. (Once you’re done reading this blog, do a quick search to test this theory. 😉)
While those claims don’t diminish the true value of the tool, they do create an environment where businesses end up spending too much of their precious budget—and their teams’ precious time—on one layer of security that’s willing to say it does it all, when in reality...
There will never be one security tool that does it all!
This isn’t The Lord of the Rings—there’s no one ring to rule them all. Do each of these tools have a particular strength and use case? Absolutely. Does that mean you need one and you’re done? Not a chance.
Let’s look at how these endpoint protection tools were developed and what they actually do.
Antivirus (AV)
Market adoption: 1990s - Present
Average price today: Free to $4 per system
The term antivirus was coined by Fred Cohen in 1983. Prophetically, four years later, he wrote...
“There is no algorithm that can perfectly detect all possible computer viruses.”
Since the earliest days of AV, the founders of the industry understood (and never tried to hide the fact) that software created to find and remove computer viruses will be forever fighting a losing battle. They are reactionary by design and not intended to stand up against a savvy attacker aiming to evade your AV software.
Antivirus relies on a signature-centric approach and searches for pre-identified malicious patterns and behaviors exhibited by a program, script or a command. If something shows up that your AV has never seen before, it has no way to determine if it’s malicious.
The Promise: A computer program created to prevent computer viruses.
The Reality: A computer program that prevents previously seen viruses or viruses written with commonly used malicious code.
While the threats were serious, they were limited in scope. In 2007, AV-TEST reported only 5.9 million new unique malware samples (based on MD5) for that year. Over time, as additional ways to monetize their malicious code grew, computer viruses—aka malware—grew as well. By 2012, that number was 34.4 million, and just two years later, that number more than quadrupled to 143.1 million.
By this point, it became clear that new methods were needed to fight the (many) new threats.
Next-Generation Antivirus (NGAV)
Market adoption: 2014 - Present
Average price today: $4-10 per system
NGAV moved away from a signature-based approach to focus more on the interaction of the entire operating system with the goal to analyze the full context of an attack. Numerous approaches to address these new forms of threats have appeared, including behavioral detection, artificial intelligence (AI), machine learning (ML) and cloud-based file detonation.
You may recognize these buzzwords, and using a traditional AV plus a NGAV—or relying on one vendor that does both—does provide layering to increase security. If you can afford both, and they don’t consume too many human or CPU resources, it's encouraged to layer up for better protection.
However, don’t mistake AI and ML for magic. While they sound great, they too are software written by humans—software that can be easily evaded with little effort if a threat actor needs to as a part of their attack.
The Promise: The End of Cyberattacks - Defeating Every Attack. Every Second. Every Day.
The Reality: It’s a useful additional layer to include in your security stack if your budget permits.
For example, if traditional AV is a solution that catches 75% of the threats, NGAV might help you catch an additional 10% that are slipping by. If that works out for your budget, that’s great, but don’t only get AV or NGAV or both and believe their claims that now you’re getting “easy and fast protection against all threats” because even with AV and NGAV installed, a targeted attack or a carefully crafted polymorphic malware will evade both with ease.
Endpoint Detection and Response (EDR)
Market adoption: 2014 - Present
Average price today: $8-15 per system
In 2013, Anton Chuvakin of Gartner coined the term endpoint threat detection and response with this description:
“Endpoint threat detection and response tools help organizations speedily investigate security incidents and detect malicious activities.”
Now, it is commonly known as endpoint detection and response.
While EDR has always been about enabling an organization by providing them more security telemetry in order to help them investigate their own security incidents, it is commonly thought of as the (next) NextGen-AV.
Many organizations that have little or no ability to investigate security threats themselves purchase an EDR as an add-on to their NGAV with the belief that it will help block additional attacks. Unfortunately, unless you have security experts whose job is to chase down NGAV alerts and use the data collected in the EDR to find additional anomalies and then write new detections for your organizations, an EDR is rarely a great investment. Ultimately, it overwhelms an understaffed IT organization with information and alerts that they don’t have the capacity to deal with.
The Promise: Continuous, comprehensive endpoint visibility that spans detection, response and forensics to ensure nothing is missed and potential breaches are stopped.
The Reality: An overwhelming amount of information that requires proactive security experts to manage, utilize, and write custom detections to realize a return on investment and an actual marked increase in security posture.
The 1987 fundamental truth from the man who coined the term antivirus is as true today as it was then:
“There is no algorithm that can perfectly detect all possible computer viruses.”
Frankly, many marketing teams in the antivirus industry have taken an avoid-this-truth-at-all-costs approach at times. Doing so has actually hurt the overall security industry. For generations now, businesses have spent the lion's share of their budget on over-priced EPP tools because it is much easier to believe a vendor who is willing to say, “one package—everything you need” when the reality of the situation calls for...
- Research and self-education
- Writing a security policy based on a security framework
- Assessing your overall risk, or having a third party do it for you
- Mapping controls to your gaps
- Hardening your tools and processes
- Mapping products to your controls to cover additional gaps, etc.
Who wouldn’t rather buy a tool that claims to be a silver bullet?
Unfortunately, the same old problem remains as illustrated by Allie Mellen at Forrester:
“Stop trying to take humans out of security operations. Despite the development of AI that can consistently beat human beings at StarCraft II, there’s still a large difference between true human consciousness and the artificial simulation we lean on so heavily in marketing.
"AI is only as good as the model on which it’s built. AI and automation lose to human beings because we’re unconstrained and do the unpredictable, which is exactly what attackers do in security.
"The core capabilities of human beings are AI’s blind spots; 'humanness' is simply not yet (or possibly ever) replicable by artificial intelligence. We have yet to build an effective security tool that can operate without human intervention. The bottom line is this: Security tools cannot do what humans can do.
"To win, augment.”
How Huntress Complements All of the Above
Now that we’ve outlined some of the most common endpoint protection tools, let's take a quick look at why Huntress is actually complementary to all of them.
Huntress was founded by former NSA offensive cybersecurity hackers. Their job during their time in the intelligence community was to evade all of the protections put in place by the targets that they were assigned, and then dwell in the targeted systems for long periods of time. It was so easy for them that they decided to try and develop a security service that would actually have stopped them if they were attacking a target who used it.
In essence, Huntress performs threat hunting on a massive scale, but for a very specific thing: persistent footholds. We focus on footholds because they are the most important part of the attack chain. But they’re also the part that you may have never heard of.
Attackers use persistence mechanisms to maintain long-term access to systems so they aren’t kicked out by a simple reboot or a password change. After initial access, most attackers will lurk around for days, weeks, or even months to wait until the right time to drop their final payload.
We know all the tricks attackers use. That’s why we built a solution that can remove attacker persistence in minutes and hours instead of only finding it after the damage has been done. Our goal is to save our customers from the most devastating attacks—all without creating mountains of unnecessary alerts.
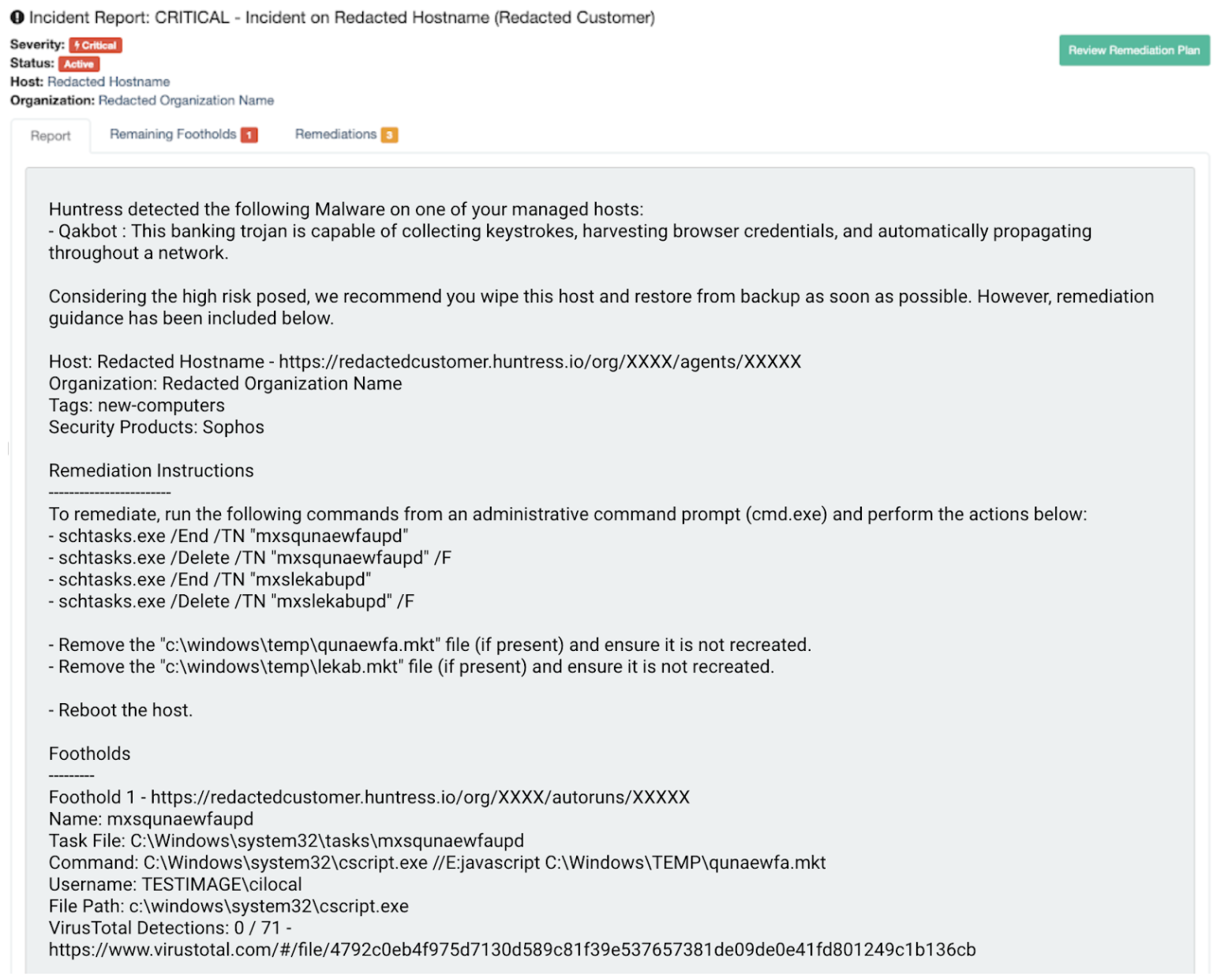
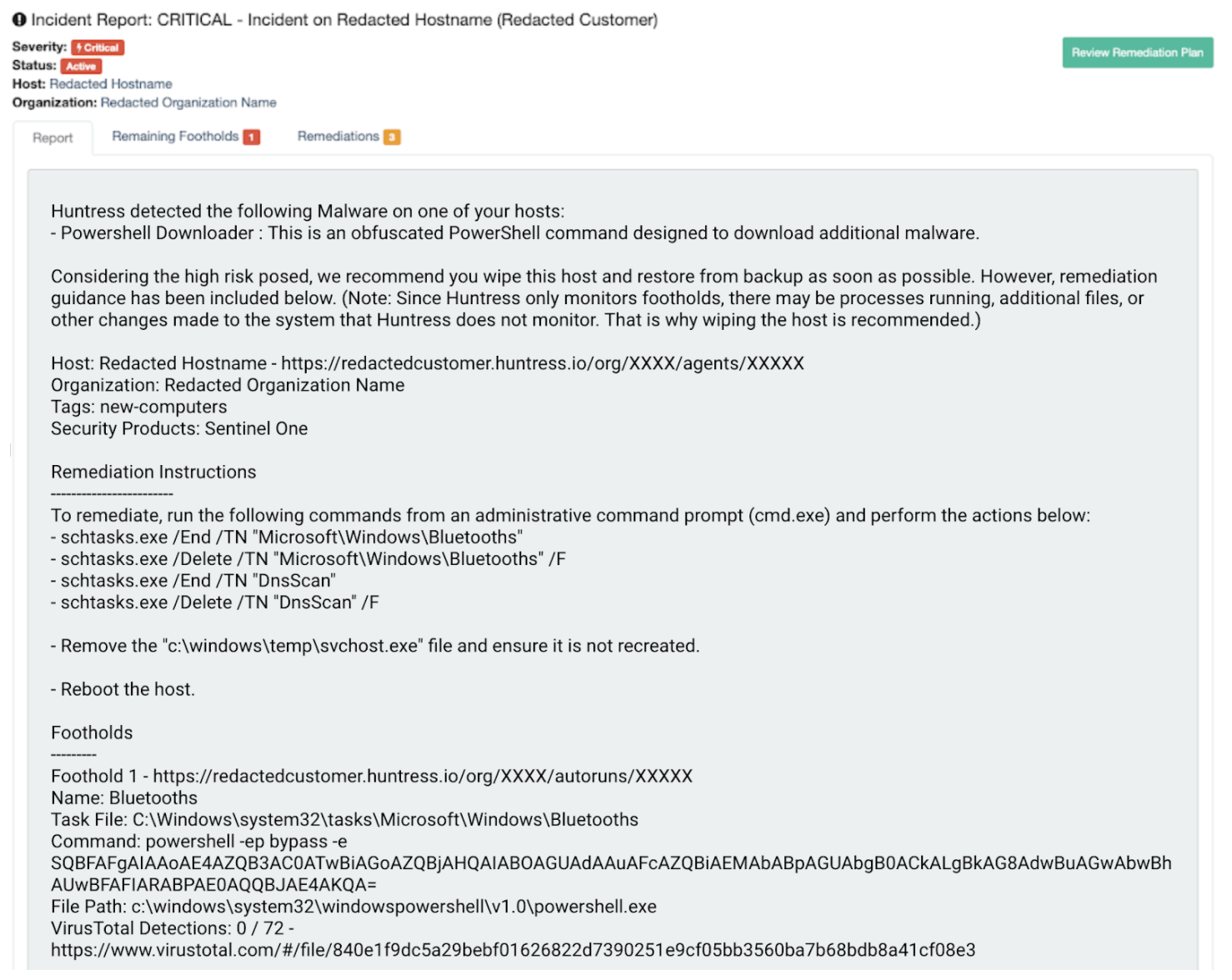
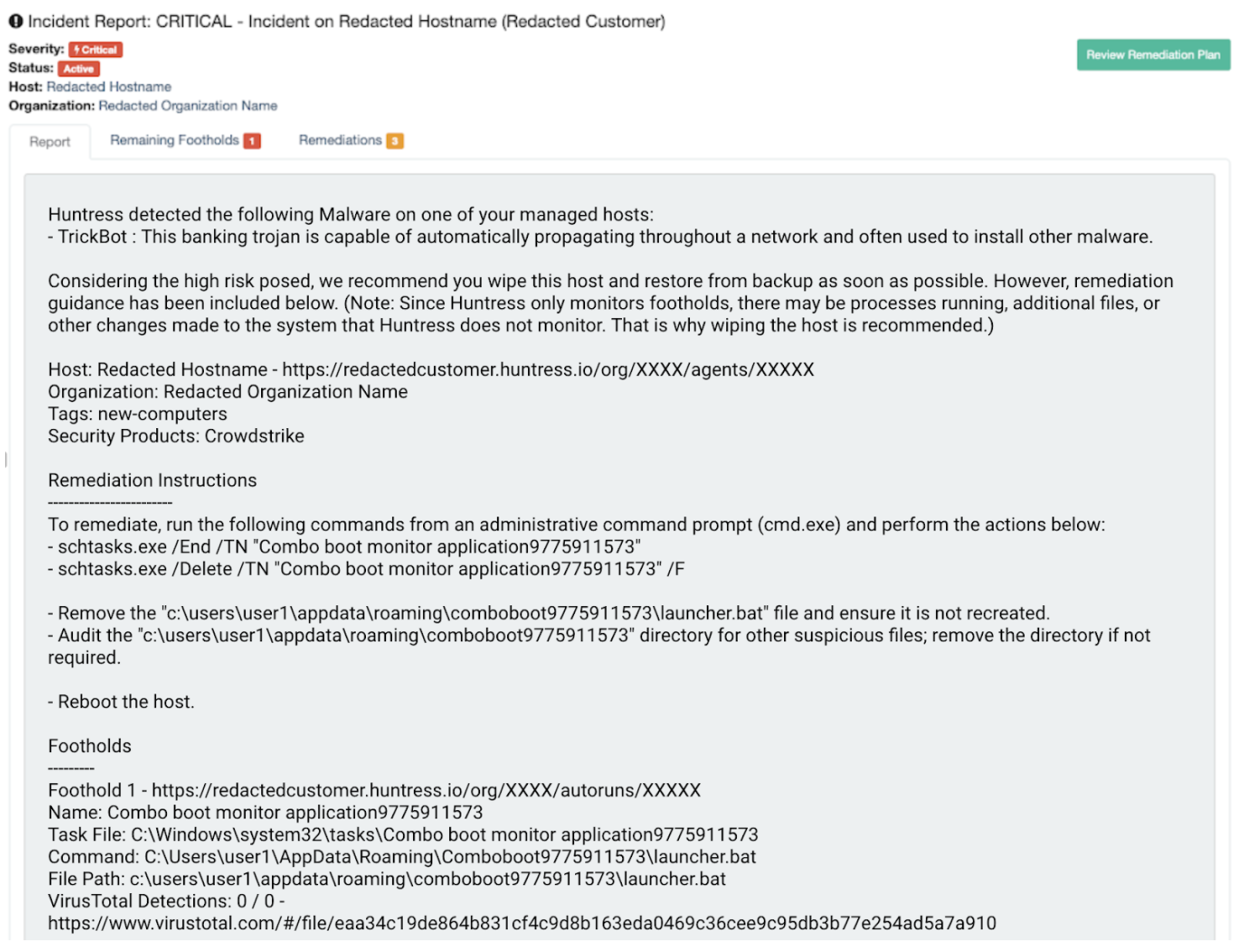
Here are a few examples of redacted Huntress incident reports we’ve sent to partners where common AV/NGAV/EDR vendors were installed and running on their systems.
We are in no way saying that those solutions aren't doing their jobs. The Huntress team of ThreatOps engineers hunt for the things that EPP software solutions miss. That’s our value.
When the game is savvy attackers versus software, attackers win every time. When it’s savvy attackers versus Huntress’ ThreatOps engineers, the script gets flipped. Now it’s the attackers who have to determine their ROI on coming back to a target where their persistence has been removed.
Pro-tip: Attackers understand the value of their time, and once persistence has been expelled, they’ll just move on to lower-hanging fruit. You don’t have to have a perfect cybersecurity program; you just have to be more secure than your peers. Huntress does just that, which makes our service the perfect complement to any cybersecurity solutions that you’re using today.
Want to see how Huntress fits into your security stack? Sign up for a free trial.