Before Huntress, I always assumed that threat hunting was done like this:
- Gather as much visibility as you could afford
- Make sure it includes sophisticated machine learning, AI, behavioral analytics, [insert buzzword du jour here]
- Find smart security people to constantly tune the engines to sift through and bring the important stuff to the surface
But every solution I saw was expensive, unwieldy, and often very manual. There had to be a better way!
A New Approach to Threat Hunting
According to Huntress lore, the concept of hunting for persistence was cooked up during our founders’ time at the NSA. As cyber operators, they understood the crucial role that persistent footholds played in the attack chain. Footholds allow attackers to maintain access to their targets—and yet, they often don't get the attention they deserve from defenders.
The truth is, most attacks would not be successful if defenders could just reboot to remediate the issue; attackers want their malware to keep running, especially if they’ve spent countless hours rearchitecting to evade defensive measures.
And that’s not all. In most cases, footholds are established after the attacker has already bypassed many different preventive tools—like AV/NGAV, firewalls, DNS filtering and, even in some cases, more advanced EDR solutions.
So if we could figure out a scalable way to hunt for these footholds, then couldn’t defenders essentially root out these attackers? This was how the idea of Huntress was born.

Snippet from an initial proposal of a “persistence hunting” solution by Kyle Hanslovan
What Is a Persistent Foothold?
A persistent foothold is simply an attacker mechanism to automatically re-trigger some malware (maybe a stub or even fully loaded malware) across potential interruptions like restarts or user logoffs.
In most cases, a foothold is implanted as soon as preventive defenses are evaded and initial access is achieved. It is an indicator that proves the attacker has already slipped by your defenses. And the thing is, a foothold is a very concrete almost tangible thing that actually can be examined on the machine—which means we should be able to hunt and detect them.
What Do You Mean by Access? Is Someone Actually Logged in?
We typically think of “access” as a kid in a hoodie sitting in a dark basement who has remoted into your computer. But in this context, it’s even simpler than that.
It’s kind of like the attacker getting a copy of the key after breaking in, giving them the chance to return once they’ve figured out their plan. Having access means the ability to re-execute some piece of malware code—maybe even one that beacons out waiting for further instructions.
To take the definition even more literally, a foothold (per Google definitions, as of the date of this post) is a secure position from which further progress may be made.
Once an attacker makes her way onto the endpoint, the foothold essentially buys the attacker time while she figures out what she wants to do next. Then, even if the victim decides to log out or reboot the machine, this foothold has an ability to “respawn” so that the attacker doesn’t have to start from scratch and phish you again (besides, what is the likelihood that anyone would open that same attachment twice?).
What Does a Persistent Foothold Look Like?
Let’s take a foothold that Huntress has seen before. It kind of looks like this:
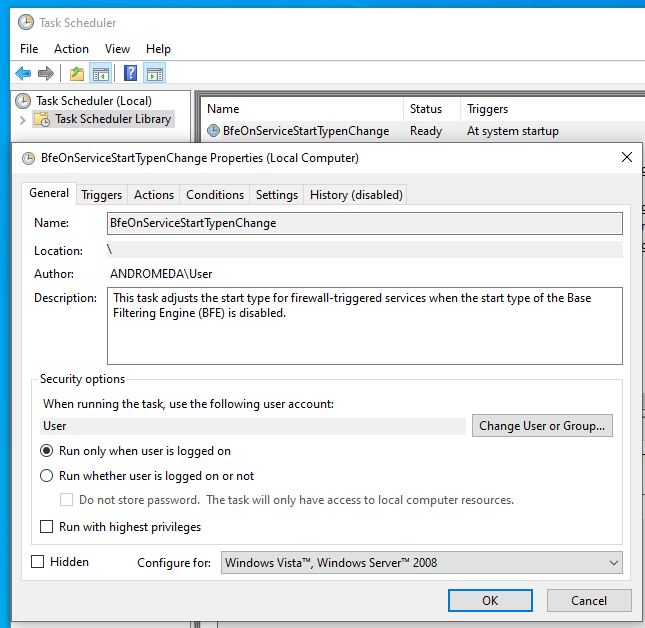
For a non-security practitioner, we often think of cybersecurity as bad files, emails, or even services or processes. To Huntress, we relish in finds like this that use and abuse parts of the operating system. But what is it?
Let’s unpack this a little bit more:
First and foremost, what are we looking at? We’re looking at an entry within Windows Task Scheduler.
“The Task Scheduler service allows you to perform automated tasks on a chosen computer. With this service, you can schedule any program to run at a convenient time for you or when a specific event occurs.”
For you Linux/Unix folks, it’s kind of like a cron job. It’s a way to tell the machine to automatically execute something—a script or a program—at a certain time or moment without you having to actually jump in and do anything.
Think about all the things you can do with this. For example: every weekday at 9am, automatically open email and Slack. Maybe even take it as far as the rumored folks who figured out ways to automate their jobs so they could sit around and play video games (though admittedly, most of these folks actually use cron).
And that’s just it! Attackers are lazy—just like the guy who automated his job. An attacker wants to know: how can they respawn their “access” to the machine without having to start over in the event of a reboot? This is where persistent footholds come in.
There are tons of mechanisms—called autoruns—within an operating system that can be exploited to create persistence. Anything that creates an automatic trigger to execute code can be used to create a foothold; whether it be a startup item, a run key, or even a scheduled task.
What Does a Persistent Foothold Do?
Let’s go back to the example above.
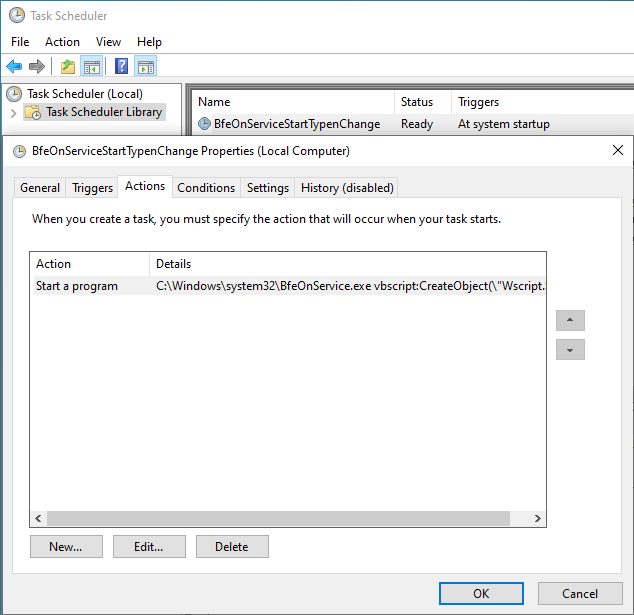
The triggered action isn’t to send an email or open a program. Instead, it’s to run malware. See under the “Actions” tab? It’s running an executable (which turns out to be renamed mshta.exe) that calls VBScript that in turn runs PowerShell. 🚩Shadiness alert!
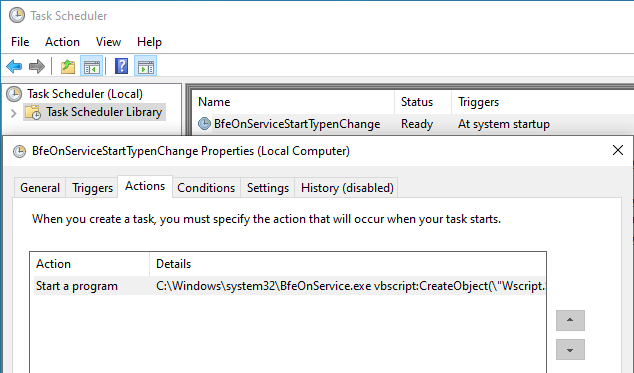
(Check out what this incredibly clever malware actually does in Part One and Part Two of our Hiding in Plain Sight blog series)
Taking a step back, the thing we have to remember is this:
“Malware can hide, but it must run” - Alissa Torres
Persistence gives malware the ability to run…. and run and run over and over again, even in the event of an interruption such as a machine reboot or a user logoff. No need to regain that initial access through a new phishing email, a new brute force attempt, or finding a new exploitable vulnerability.
Where Does “Threat Hunting” Come Into Play?
The reason why it’s so important to include human threat hunters when hunting for footholds is simply because these footholds are exploiting core parts of the operating system. Autoruns that can create persistence—such as run keys, system trays, WMI events—are necessary for the machine to keep the wheels turning in the first place so you can keep doing your work. But it’s also the perfect place for an attacker to hide.
As a defender, how can you separate the wheat from the chaff? How do you surface the autoruns that are hidden exploitations by an attacker while leaving legitimate autoruns alone?
The key here is to avoid incorrectly turning off or eliminating legitimate autoruns that are needed by the OS and applications; doing this too much or too often can actually hurt way more than it helps.
Training a machine or a system to differentiate between the two is much easier said than done. And if the machine gets it wrong, there is a potential cost of breaking these core elements needed to run the machine. Humans are needed in this hunt—they can learn quickly and are extremely good at discerning right from wrong.
“Cyber threat hunters […] must be unleashed on these networks to look for the hidden, persistent access controls. These information security professionals actively search for, isolate and remove advanced, malicious code that evades automated safeguards.”
- Thomas Bossert, Former US Homeland Security Advisor
If you want to learn more about human-powered threat hunting and how it works, check out this blog post.
Want to learn more about persistence? Download our eBook.