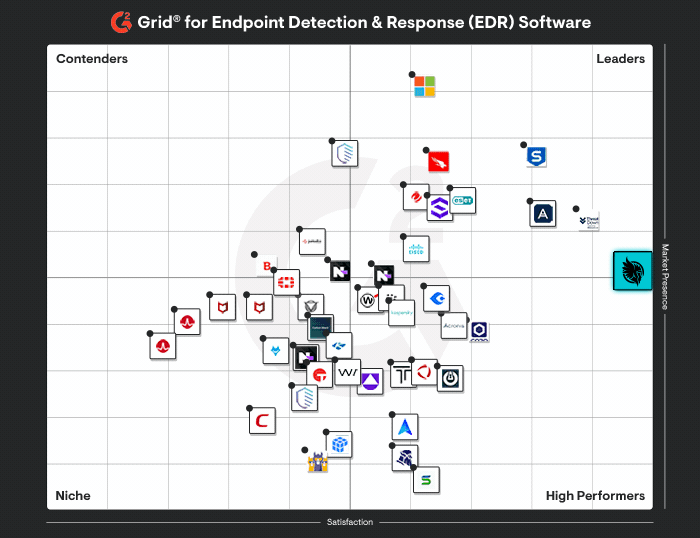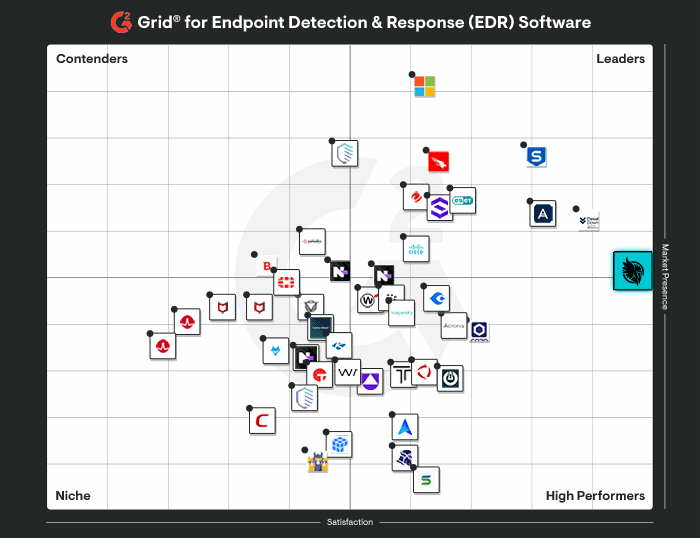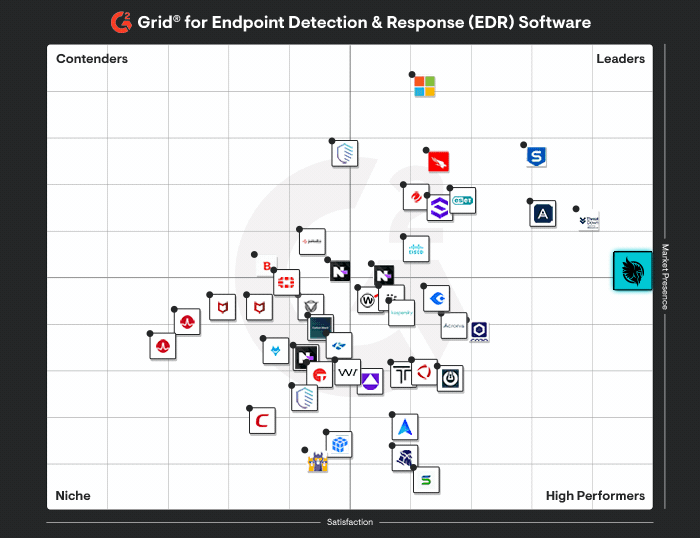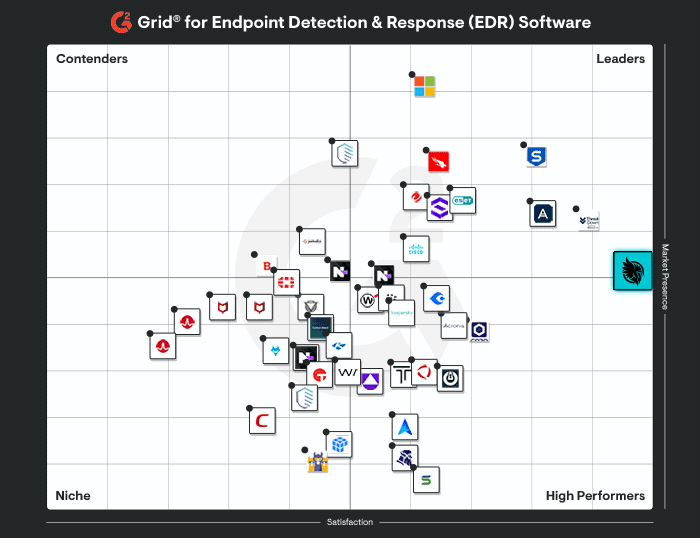
Explore the Huntress Platform
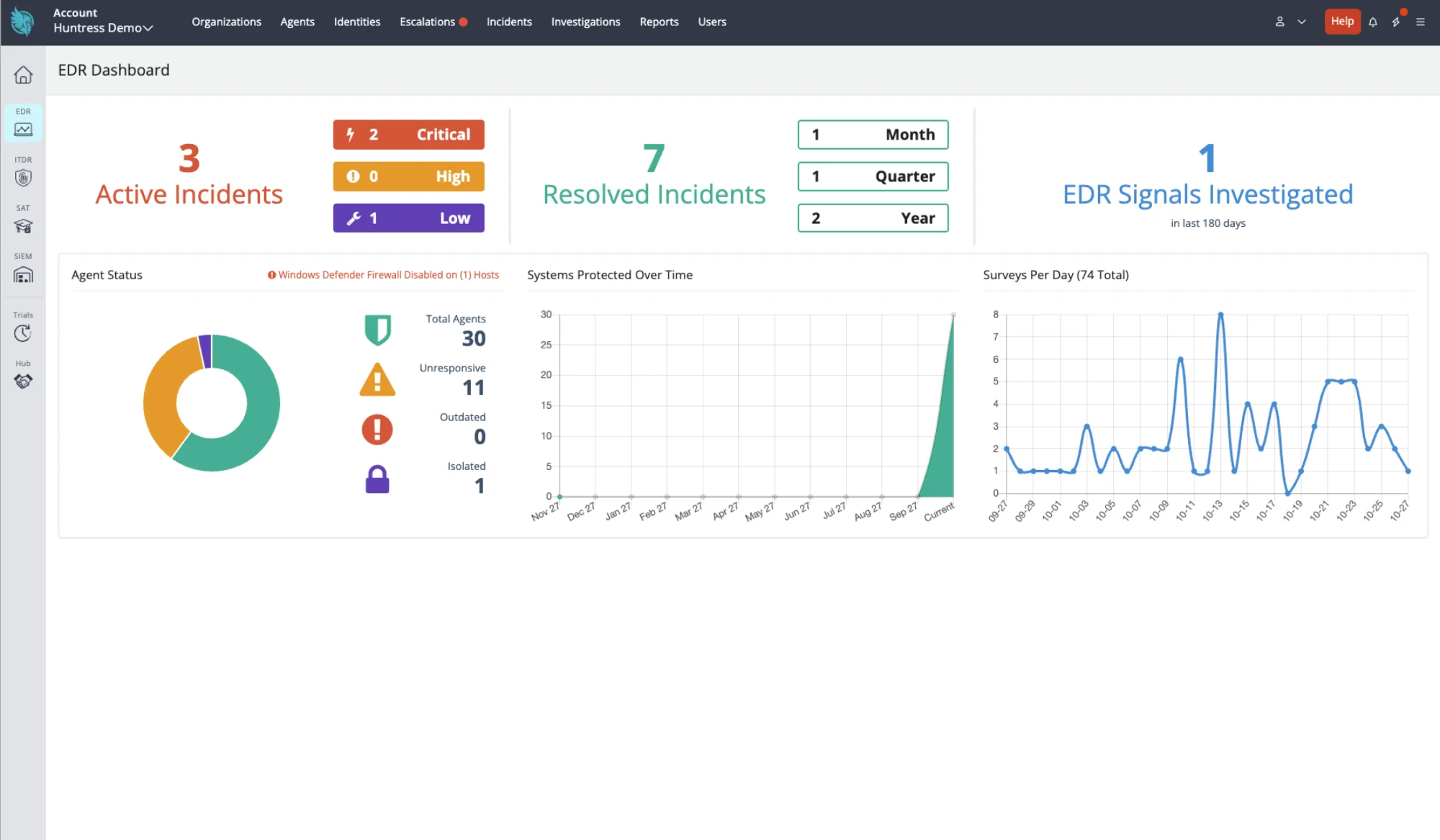
Managed EDR

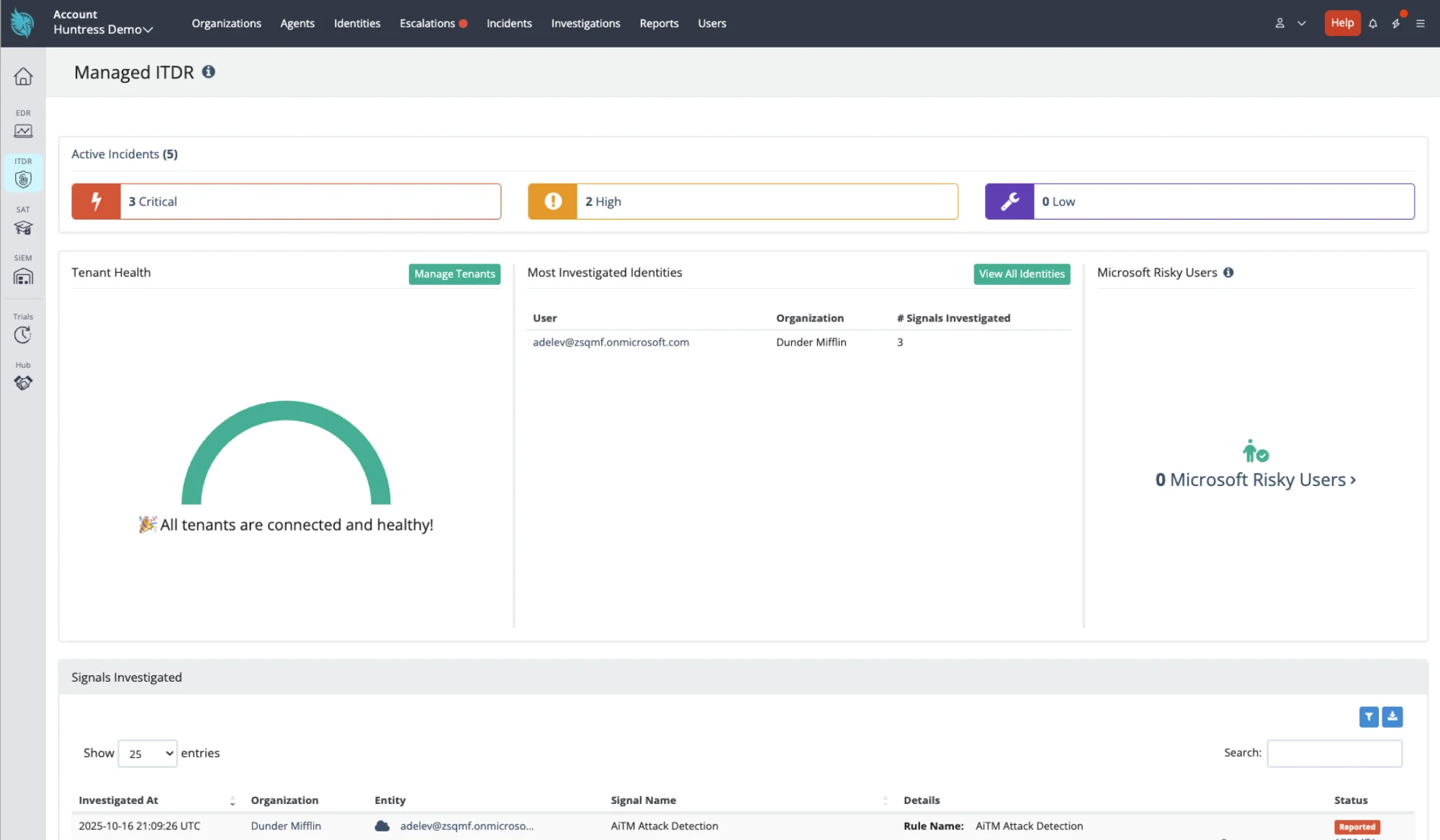
Managed ITDR

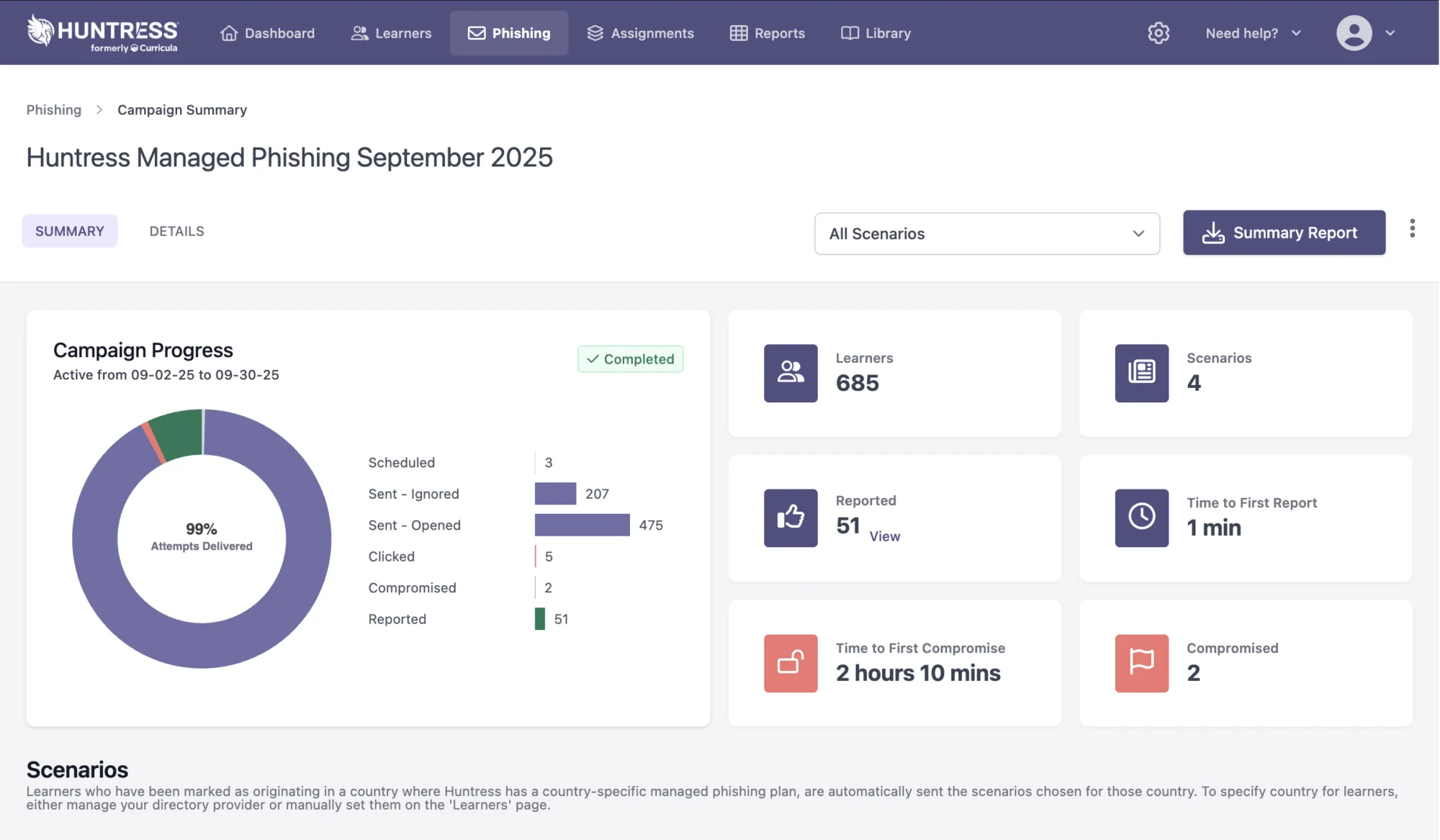
Managed Security Awareness Training

Managed SIEM


Threat Fighting at its Best
Protecting endpoints and identities doesn’t happen magically. See the features and services that act as our platform’s foundation.

Persistent Footholds
Eliminate threats hiding in plain sight on Windows and Mac.

Managed Antivirus
Make the most of your frontline protection with Microsoft Defender

Ransomware Canaries
Catch potential ransomware incidents early and quickly respond.

External Recon
Highlight external vulnerabilities to tighten perimeter defenses.

Powered by 24/7 Cybersecurity Expertise
Our fully-managed detection and response for endpoints and email is possible thanks to the 24/7 support and expertise of our Security Operations Center (SOC) analysts.

Purpose-Built Protection
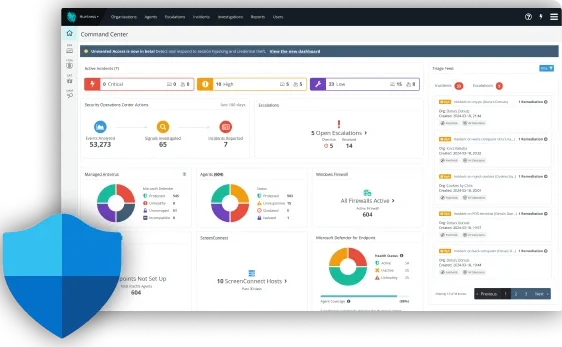
One Dashboard to Fight Threats
The Huntress dashboard combines the power of our Managed Security Platform and 24/7 Security Operations Center (SOC), giving you a complete view of your organization. From your dashboard, you get immediate access to:
- Security alerts
- Active incidents and investigations
- Remediation tools
- Real-time reporting



Empowering the 99%
4.5M
8.5M
204K+
8.8K

The Huntress Managed Security Platform








24/7 Managed Security
Deploy Huntress in minutes to protect your endpoints, identities, and teams—all backed by our 24/7 Security Operations Center. Start today with a free trial.