As a managed endpoint detection and response (EDR) company, we see attacks hitting all kinds of sectors. But cyberattacks hitting the education sector can be particularly sinister.
The education space encompasses both K-12 school districts and higher education institutions, meaning that data being compromised often belongs to students, some as young as children in kindergarten.
Think of the 2024 attack on PowerSchool, a cloud-based service provider for K-12 schools, which led to hackers reportedly grabbing sensitive personal data for millions of students and educators, including contact, medical, and Social Security numbers. Or the Los Angeles Unified School District ransomware attack in 2022, where threat actors contacted the parents of impacted students to pressure the district to pay the ransom. Or a 2021 ransomware attack on Howard University, which led to the cancellation of online and hybrid classes.
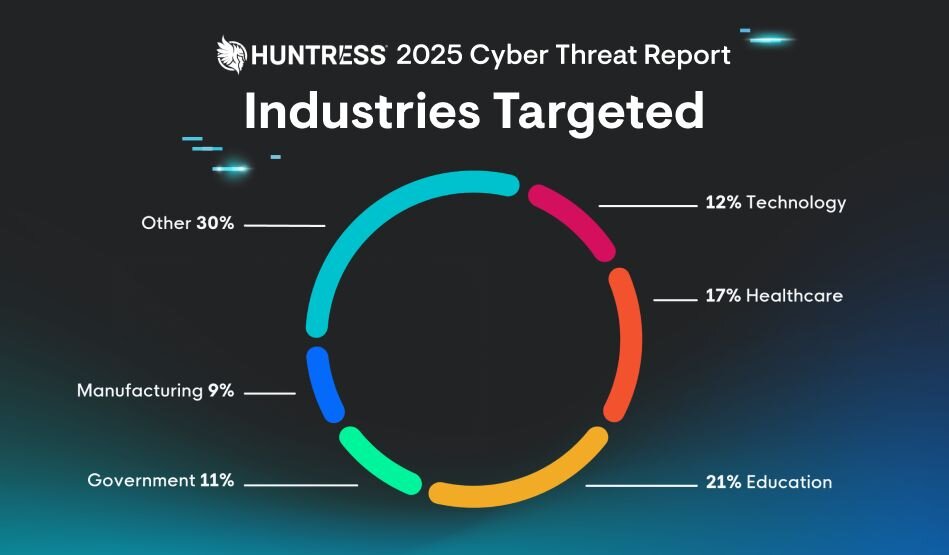
The Huntress 2025 Cyber Threat Report found hackers focusing many of their attacks on educational facilities, with education making up 21% of all incidents observed last year.
Figure 1: Threat actors targeted the education sector in 21% of incidents seen in 2024
Threats facing schools
Threat actors target higher education and K-12 school districts through various means. This includes phishing attacks against faculty and students, which often include lures that pretend to come from the university or school district itself and aim to compromise accounts or steal credentials; targeting exposed Remote Desktop Protocol (RDP) services in order to gain initial access to the environment and manually deploy ransomware; or other techniques.
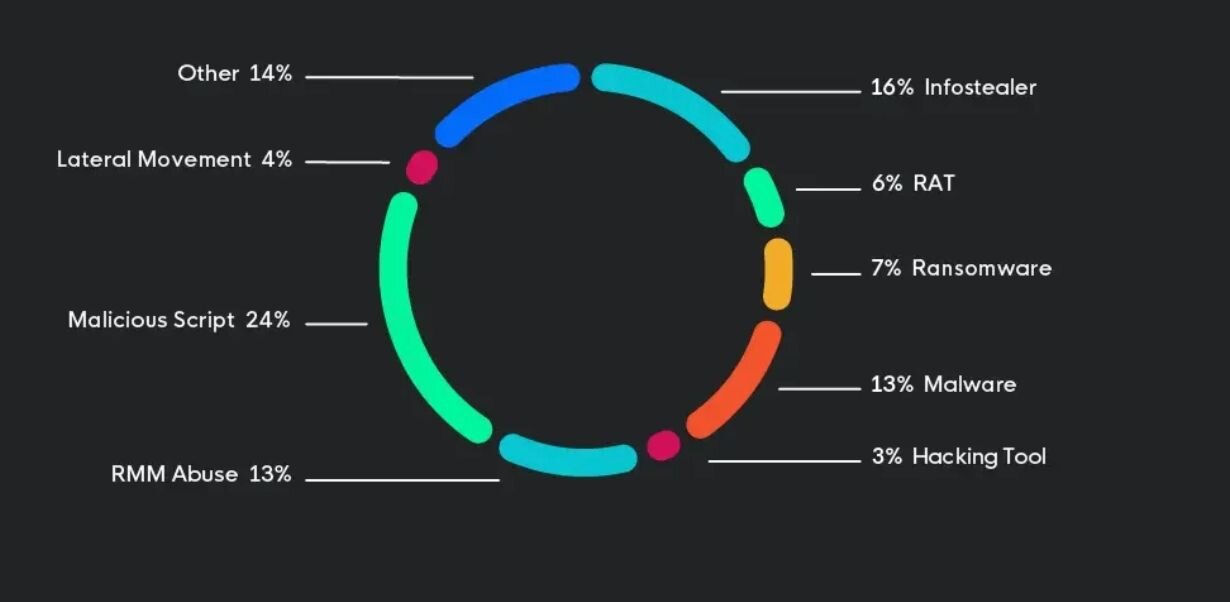
Our 2025 Cyber Threat Report found several education-specific threats. Malicious scripts made up 24% of the threats targeting the education sector, followed by infostealers (16%), malware (13%), and ransomware (7%). Out of the infostealer infections seen, Chromeloader was the most prevalent, accounting for almost 70% of incidents.
Threat actors are also abusing remote monitoring and management (RMM) tools to stealthily perform reconnaissance on networks. In fact, we noticed RMM abuse in the education sector was slightly higher than in other sectors, likely due to educational systems relying heavily on remote administration.
Deep-dive: What do cyberattacks on schools look like?
We’ve seen endless media coverage about cyberattacks on the education sector, but what does an attack look like behind the scenes at a school?
An RDP brute force attack
On September 4, we identified a malicious authentication into a local school district’s network. Specifically, the threat actor gained access to the environment by brute forcing an exposed RDP instance.
Our SOC team was able to identify this behavior while launching a retrospective threat hunt. Threat hunting involves querying various telemetries with specific security inquiries in order to reach a finding. This allows us to uncover malicious activity that other security tools didn’t catch, reduce threat actor dwell time in a business environment, and improve organizations’ overall security posture.
This specific threat hunt looked at cases that involved a malicious public IPv4 that had previously been seen in use by an adversary machine. Through this investigation, the SOC was able to find the malicious authentication via an exposed RDP instance for this school, which used both Managed SIEM and Managed EDR.
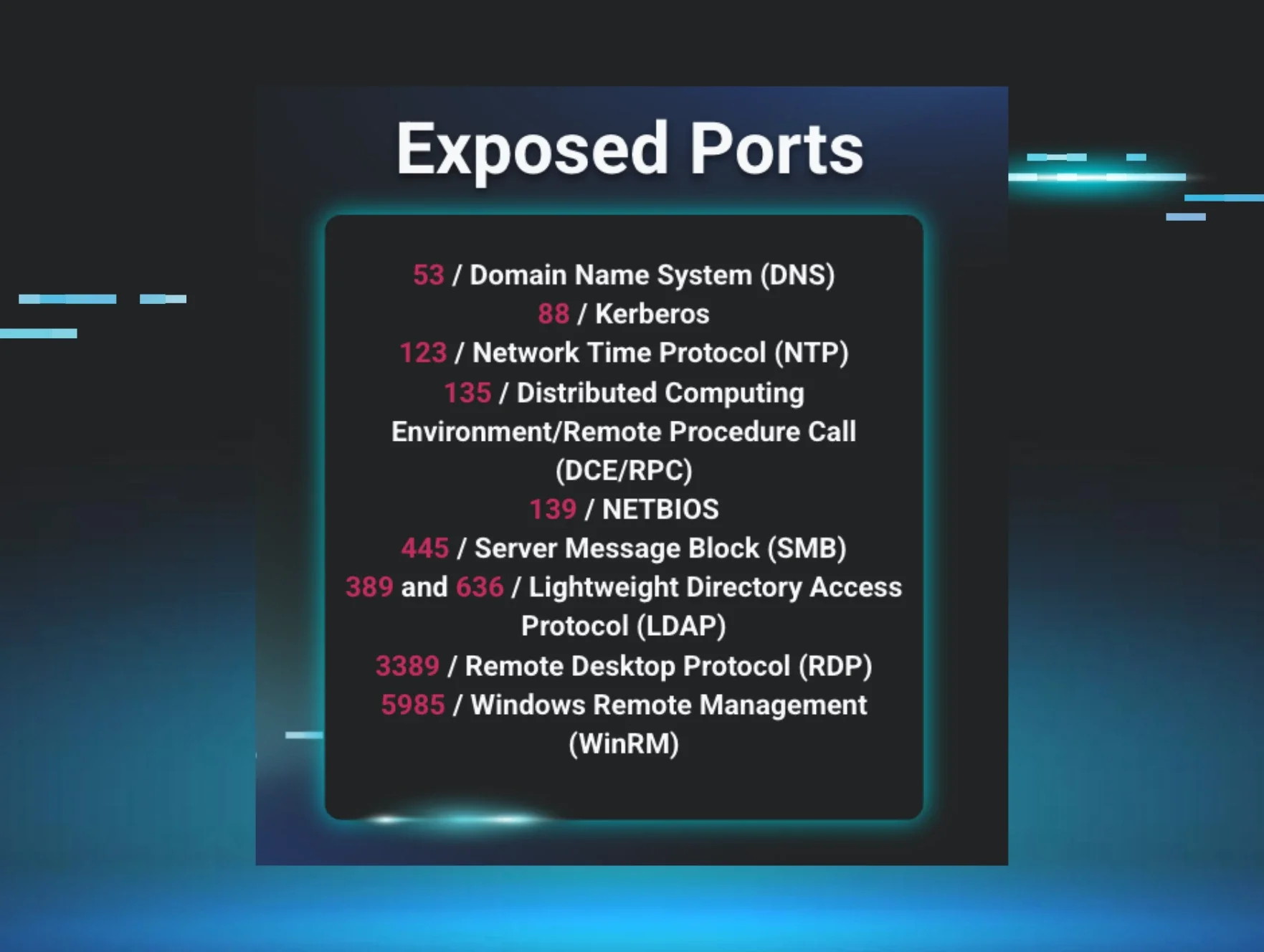
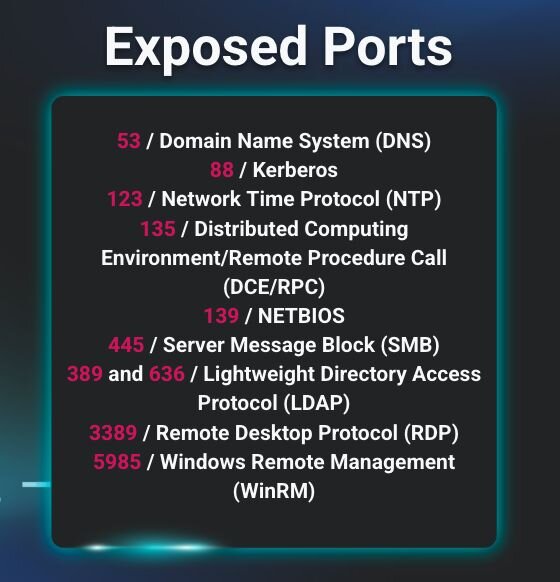
Further investigation into one of the school’s hosts revealed it was exposing its domain controller. Exposed ports are major security risks for organizations and can open systems to various attacks, from brute force to ransomware, if they're not properly managed and secured. In this case, the host was reportedly exposing 10 different ports to public access across various connections, from RDP to SMB, suggesting that its firewall was not implemented properly.
Figure 3: Ports that were exposed on a school’s host
Huntress isolated the server and blocked the malicious IP in order to deny the threat actor further access. However, this incident shows that threat actors are looking for initial access vectors across school environments.
An RMM compromise
In May, threat actors compromised an Atera RMM instance used by a managed service provider (MSP) and used that access to hit several of their customers, including a school district. We've seen this type of attack several times this year, where threat actors hit an MSP’s RMM instance to cast a wide net across their downstream customer base, effectively hitting multiple organizations through one attack.
In this incident, a user operating as SYSTEM used the Atera instance to execute C:\ProgramData\AnyDesk.exe and then install an additional AnyDesk RMM onto the host. The threat actor also added a user “WDAGUtilltyAccount” to the local Administrators group.
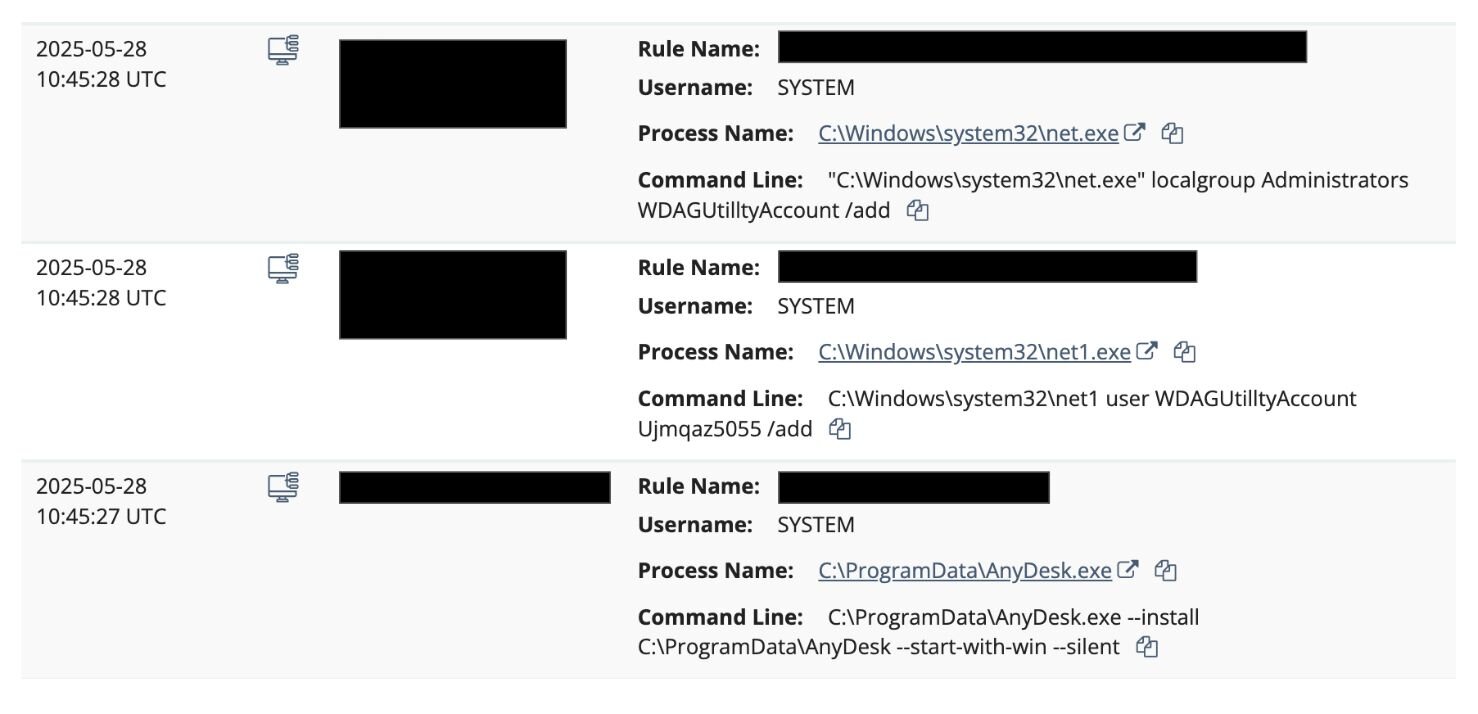
As seen in Figure 4, the password used by the threat actor to create the user “WDAGUtilltyAccount” is Ujmqaz5055. This is a commonly used password we've observed threat actors use repeatedly, as seen in this Huntress analysis and DFIR post.
These moves could've set the threat actor up to escalate their attack, but Huntress worked with the school district and upstream MSP to make sure the user “WDAGUtilltyAccount” was removed, credentials were rotated for the Atera instance, and the malicious AnyDesk instance was removed.
RClone data exfiltration
In May, the SOC encountered a threat actor downloading RClone and attempting to use it to exfiltrate data from a high school. RClone was used to attempt to obtain the contents from several directories (including ones related to the school’s main office, financials, and student and family emails). RClone, which is used to sync files to the cloud, is a popular method for attacker data exfiltration.
Further investigation into the incident showed that it appeared to stem from RDP brute force attacks. This then led to the threat actor moving laterally from a host that didn’t have a Huntress agent installed on it. But the deployment of mass isolation stopped the attack before it could escalate.
Difficult questions: What’s at stake?
Both higher education entities and K-12 districts face unique business challenges. Higher education institutions need to manage both faculty and students, sometimes across different locations and campuses. On top of that, they’re dealing with numerous unmanaged devices, with students bringing their own laptops and phones. Many institutions also include research facilities, which are lucrative for espionage-driven threat actors interested in IP theft.
K-12 school districts, meanwhile, face limited budgets and resources, which are allocated in a somewhat complex process by local, state, and federal governments. This can put a wrinkle in the process of obtaining key security resources.
For environments with limited resources like these, leaders should focus on making basic, prioritized investments that can put a dent in the most common attacks for threat actors. That includes:
-
Deploying multi-factor authentication (MFA)
-
Patching known and exploited vulnerabilities
-
Implementing and testing backups
-
Deploying a security awareness training (SAT) program
-
Implementing endpoint detection and monitoring solutions—particularly ones that are managed, to help fill in resources and personnel gaps
As they weigh risk, entities in the education sector also need to consider a key question: “What’s at stake?”
For K-12 school districts, that may come in the sensitivity of the data that they handle, which could include confidential medical information and Social Security numbers for children. For instance, after the Minneapolis Public Schools were hit by Medusa ransomware in 2023, the threat actors behind the attack released highly sensitive details about students, including sexual assault case files.
Understanding the techniques that threat actors use is important. Understanding how to stop them is essential as well. But knowing exactly who the potential victims of a cyberattack are, and the possible impact on them? When measuring risk, that’s absolutely critical.
Huntress helps defend the education sector with real-time monitoring with a dedicated team of 24/7 security experts. Address potential threats as they occur; we provide proactive remediation and instant alerts to any situation that needs attention.