In the ever-evolving landscape of cyber threats, a new and insidious danger is emerging, shifting focus from external attacks to internal infiltration. While our last blog covered the tactics of fake recruiters targeting job seekers, this installment unveils a more sophisticated and potentially devastating scam: hackers impersonating seasoned cybersecurity and IT workers to gain privileged access within your organization.
These aren't just phishing attempts; we're talking about malicious actors who manipulate the hiring process to become your "trusted" staff, all with the intent of breaking into your company's databases or stealing sensitive information.
This post will dive into what this alarming threat looks like, why it poses such a significant danger, and most importantly, how you can protect your organization from falling prey to these digital imposters.
The imposter playbook: How they sneak in
This scam hinges on deception at its core. Threat actors craft elaborate fake personas, complete with fabricated resumes, convincing online presences, and even sophisticated deepfake technology to ace virtual interviews. They essentially become "fake workers" who are then hired into legitimate positions.
You might wonder how this even happens, or how threat actors could manipulate the hiring process so effectively. The hiring process, particularly for remote roles, has become a prime target. Cybercriminals leverage stolen or fabricated identities, often using real US citizens' personal data, to create seemingly legitimate candidates. They might utilize "laptop farms" in other countries where their illicit activities are based, using proxies and VPNs to mask their true location.
The rise of remote work, while offering flexibility, has inadvertently created new vulnerabilities in candidate vetting. The lack of in-person interactions makes it harder to verify identity and observe subtle cues that might raise suspicions. This remote environment is precisely what these threat actors exploit.
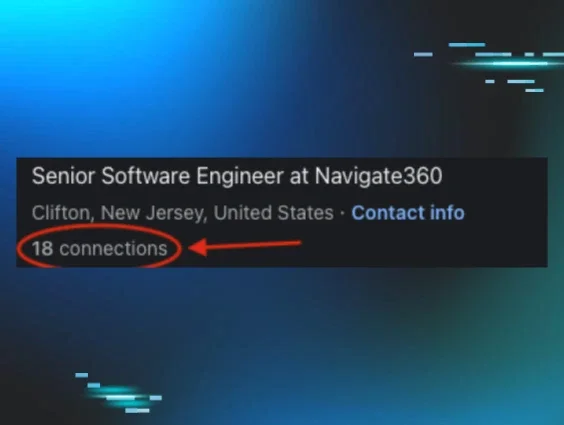
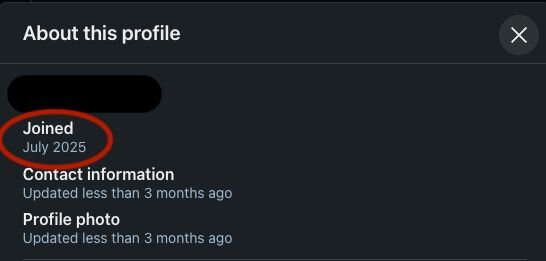
To trick employers and make these impersonations believable, these cunning individuals employ a range of sophisticated techniques. They use AI-generated video and voice technology to create hyper-realistic personas for video interviews, making it incredibly difficult to distinguish between real and fake, mimicking facial cues, voice patterns, and even online backgrounds. Resumes are meticulously crafted with fake work experience, degrees, and certifications, often accompanied by fake LinkedIn profiles featuring AI-generated profile pictures and limited connections to appear legitimate but untraceable.
Some red flags to note in a profile
Beyond technical trickery, threat actors excel at social engineering, exploiting human trust by appearing knowledgeable, professional, and eager to join the team, often with practiced responses for technical interviews to give the illusion of expertise. They may even resort to "identity laundering," using "witting" or "unwitting" individuals to rent out their personal information or appear for identity verifications on their behalf, and may siphon wages via third-party accounts, leaving behind payment tracks that hide their true identity.
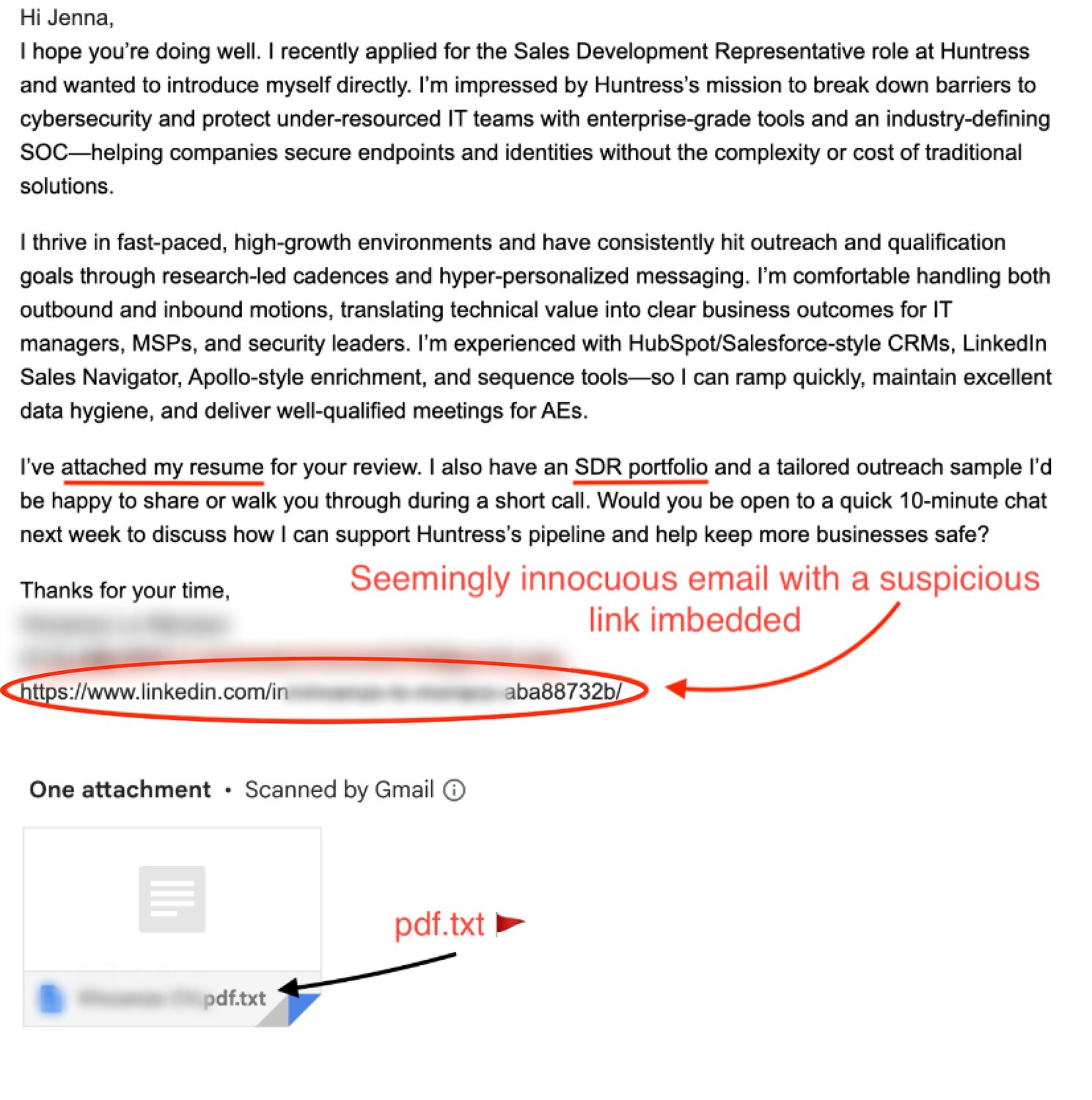
Hiring teams must remain vigilant against these types of threats, such as "candidate reach out" phishing. These deceptive attacks are cleverly disguised as pitches from prospective job candidates, often containing a compelling cover letter or portfolio. However, embedded within these seemingly innocuous messages are malicious links or attachments that could compromise your company's network. Always exercise caution and verify the authenticity of any unsolicited communication before clicking on links or downloading files, as a single misstep could lead to a significant data breach.
Be wary of emails with suspicious links and attachments
The hidden costs: What's really at stake
The danger of a fake worker isn't just about a bad hire. It's about a highly motivated threat actor gaining the keys to your kingdom. These imposters are after privileged access to your most sensitive systems.
The primary goals are multifaceted and highly damaging. Data theft is often a top priority, as they seek to steal customer data, financial records, intellectual property, trade secrets, and proprietary source codes. While less common as a direct objective of the "fake worker" scheme itself, the access they gain can facilitate financial fraud through manipulation of systems or direct extortion.
Cyber espionage is another significant motivator, with state-sponsored groups, such as those linked to North Korea, known to deploy these fake workers to collect intelligence and illicit revenue for their regimes. In alarming recent developments, some fraudulent workers have even extorted their employers by threatening to release stolen data after their employment is terminated or their cover is blown. Beyond theft, they could introduce malware, disrupt operations, or plant backdoors for future attacks.
The consequences of such an insider threat are catastrophic. Imagine the impact on your company's brand reputation, regulatory compliance (GDPR, HIPAA, etc.), and most importantly, customer trust. Data breaches can lead to significant financial penalties, legal repercussions, and a long-lasting erosion of customer loyalty. The cost of recovering from such a breach, auditing compromised systems, and securing devices can easily run into hundreds of thousands, if not millions, of dollars.
Echoes in the news: Real-world infiltrations
The threat of fake workers isn’t theoretical. It's a stark reality being exposed by intelligence agencies and law enforcement.
-
North Korean IT worker schemes: The US Treasury and Justice Department have issued repeated warnings and taken action against sophisticated North Korean IT worker schemes. These operatives, often working from countries like China and Russia, use stolen or fabricated identities of US citizens to secure remote employment in tech companies, frequently in Web3, software development, or blockchain infrastructure. Their goal is to generate illicit revenue for the Kim regime. In some instances, these workers were among the most "talented" employees, while quietly exfiltrating data and even demanding ransoms upon termination.
-
Deepfake job interview incidents: While specific company names are often kept confidential for security reasons, the FBI has reported cases where scammers successfully used deepfake videos and voice-altering technology to secure remote IT and financial positions, gaining access to corporate databases. Companies have identified candidates using AI-generated resumes and deepfake-enhanced interviews to bypass traditional hiring protocols.
Building your fortress: Defending against digital disguises
Mitigating the risk of fake workers requires a multi-layered approach, which involves robust HR practices, advanced technical controls, and continuous security awareness training.
HR teams are on the front lines of defense. Their role is critical in strengthening employee verification by moving beyond basic resume reviews. This means implementing multi-factor identity validation, including live video interviews, real-time document verification against government databases, and biometric authentication to detect fake IDs.
Thorough background checks are essential, involving comprehensive and continuous verification of work history directly with previous employers (not just references provided by the candidate), and a keen eye for inconsistencies in names, addresses, and dates. HR should also scrutinize online presences, confirming a digital footprint and looking for signs of authenticity, being suspicious of new or sparsely populated social media profiles.
Implementing secure onboarding protocols is crucial. Work closely with IT to restrict access for new hires, gradually granting privileges based on trust and necessity. Establish clear policies for handling sensitive data and ensure thorough vetting for all remote roles. Additionally, collaborating with federal agencies and cybersecurity organizations can help HR teams stay informed about emerging threats and adopt best practices.
Beyond HR, robust internal measures are crucial for reducing risk. These include stronger technical controls:
-
Multi-factor authentication (MFA): Enforce MFA for all systems, especially those with privileged access. This provides a crucial layer of defense even if credentials are stolen.
-
Principle of least privilege: Grant users (including IT staff) only the minimum necessary access to perform their job functions.
-
Network segmentation: Isolate critical systems to prevent lateral movement in case of a breach.
-
Behavioral analytics and user activity monitoring (UAM): Implement tools that monitor user behavior for anomalies. Look for unusual access patterns (e.g., accessing sensitive data outside of normal work hours, from unusual locations), excessive data downloads, or frequent unauthorized system access attempts.
-
Monitor remote administration tools: Be cautious of the use of unapproved remote administration tools or the installation of multiple such tools on one device. If an unapproved tool is used, it can open up a backdoor that bad actors can exploit.
-
Geolocation of devices: During onboarding, verify that corporate laptops are geolocated to the reported employee residence. Be suspicious if a worker requests a different shipping address for company equipment.
-
Hardware-based MFA: This is the most secure form of MFA, requiring the use of physical devices, such as hardware security keys, to gain physical access to corporate devices. For instance, USB security keys require manual plug-in to a corporate device for authentication.
Regular, interactive security awareness training (SAT) for all employees is also vital. This training should cover how to recognize social engineering tactics and phishing attempts, and the importance of reporting suspicious activity. Finally, a robust incident response plan specifically for insider threats should be in place. It should outline clear steps for detection, containment, eradication, and recovery, including how to handle situations where an insider is suspected.
Employees, particularly those interacting with new hires, should be vigilant for certain warning signs that hint at insider impersonation:
-
Reluctance to appear on camera or engage in video calls, which could indicate they’re using deepfake technology or an impostor.
-
Inconsistencies or evasiveness, such as discrepancies in their online profiles versus their work portfolios, or a complete lack of an online presence.
-
Suspicious behavior during coding tests or interviews, like excessive pauses, eye movements suggesting they're reading from a script, or difficulty with impromptu problem-solving.
-
Unusual requests, such as repeated requests for prepayments or insistence on using personal laptops for company work.
-
Incorrect or changing contact information, specifically phone numbers and emails.
-
Requests to send company equipment to an unknown address.
-
The use of "mouse jiggling" software can indicate they’re managing multiple remote profiles simultaneously.
Managed service providers (MSPs) face a uniquely elevated risk from this type of threat. Because MSPs typically manage the IT infrastructure and security for multiple client organizations, a single successful infiltration of an MSP can provide a gateway to a vast network of sensitive data and critical systems across many businesses. This makes MSPs an incredibly attractive target for malicious actors looking to maximize their impact.
For MSPs, having the most stringent security measures in place is absolutely critical. This includes rigorous vetting processes for their own employees, implementing advanced access controls, and maintaining robust incident response plans specifically tailored to insider threats. Their interconnected nature means the potential damage of a fake worker isn't just amplified for the MSP itself, but for every client they serve.
Final byte: Securing your digital gates
The threat of fake workers is a sobering reminder that cybercriminals are constantly innovating their methods. By impersonating trusted professionals, they aim to bypass perimeter defenses and exploit the very human element of trust. But if you can understand how these threats operate, implement rigorous hiring and vetting processes, deploy advanced technical controls, foster a culture of security awareness, and remain vigilant for warning signs, your organization can significantly reduce its risks.
Staying ahead of these evolving scams is a collective effort. Your organization's security is only as strong as its weakest link, and in the case of fake workers, that link can be the very people you trust with your most critical assets. By taking proactive steps, you can turn your recruitment process into a formidable defense against these insider impostors.