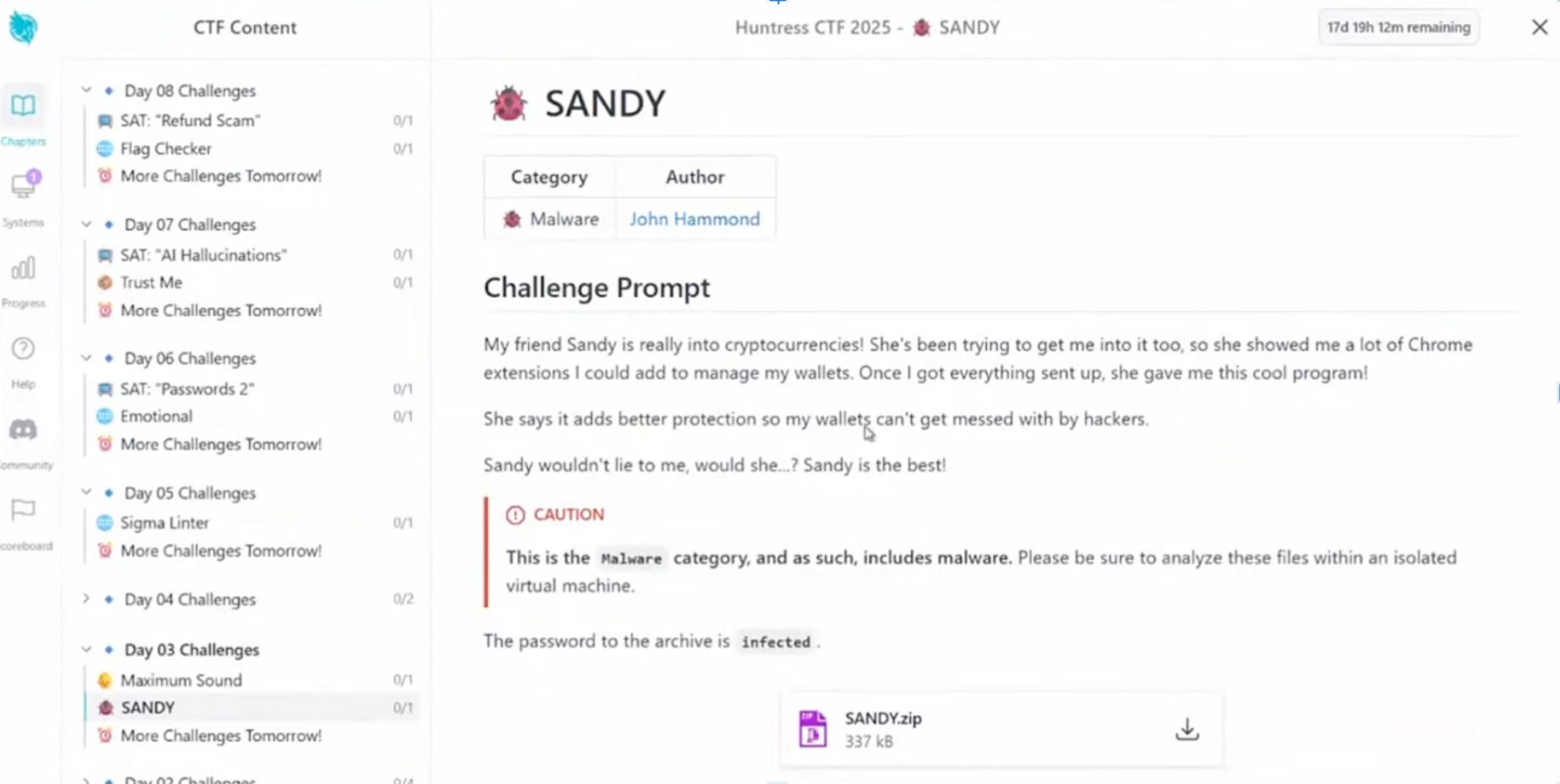
Imagine this: you’re a hacker, and you’re working through an executable file made up of a compiled AutoIT script. You’ve decompiled the script (thanks to the help of Exe2Aut, an EXE to AutoIT script converter tool). You’ve pushed past some disastrous-looking source code, littered by nonsensical random variable names and characters, to finally identify and decode the Base64 chunks in the code, revealing a cryptocurrency stealer.
Within the crypto drainer is an encoded JSON variable, where you can see extension IDs for crypto wallets that are being targeted. And there, in a layer of JSON data for the wallet browser extension IDs, you have it:
flag{27768419fd176648b335aa92b8d2dab2}
Success! This is what it was all about, after all, as you’re a participant in a Capture the Flag (CTF) competition. And you’ve just found the flag.
In fact, this isn’t just any CTF–it’s the annual October event put on by Huntress, which over the last two years has drawn fierce competition. This year’s event was no different, with 11,898 registered users and 6,892 teams. The challenge described above–“Sandy”–was only on the third day of the event, and there were 30 more days of challenges full of twists and turns.
Figure 1: The Sandy challenge in the Huntress CTF
What is Capture the Flag?
A CTF event is a competition for hackers, where players solve different challenges in order to find a “flag,” which is a unique string of text. These challenges involve different areas of cybersecurity expertise–from digital forensics to web security–and put various skillsets to the test, like deobfuscation or reverse engineering. Some CTFs are popular for continual practice, like TryHackMe or Hack The Box, while others are more large-scale and intense, like DEFCON’s CTF.
The ultimate goal? Find the flag and submit it to earn points. Some do it for fun or to hone their craft and creativity, while others compete for the top spot and for a chance to win some epic prizes (in our case, winners got gift cards, RDV4 Kit (360), OMB Cable Elite, Huntress swag, and more).
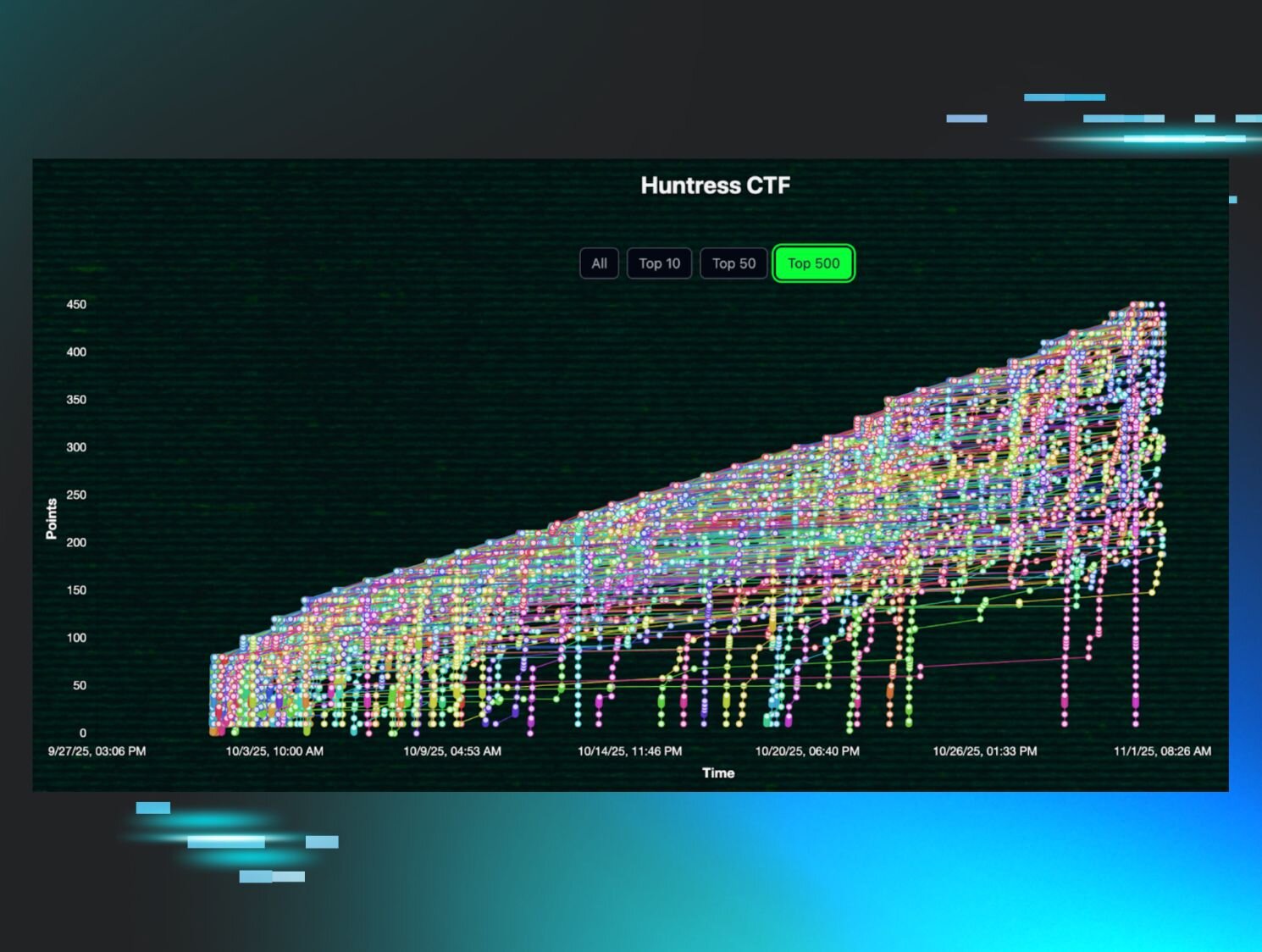
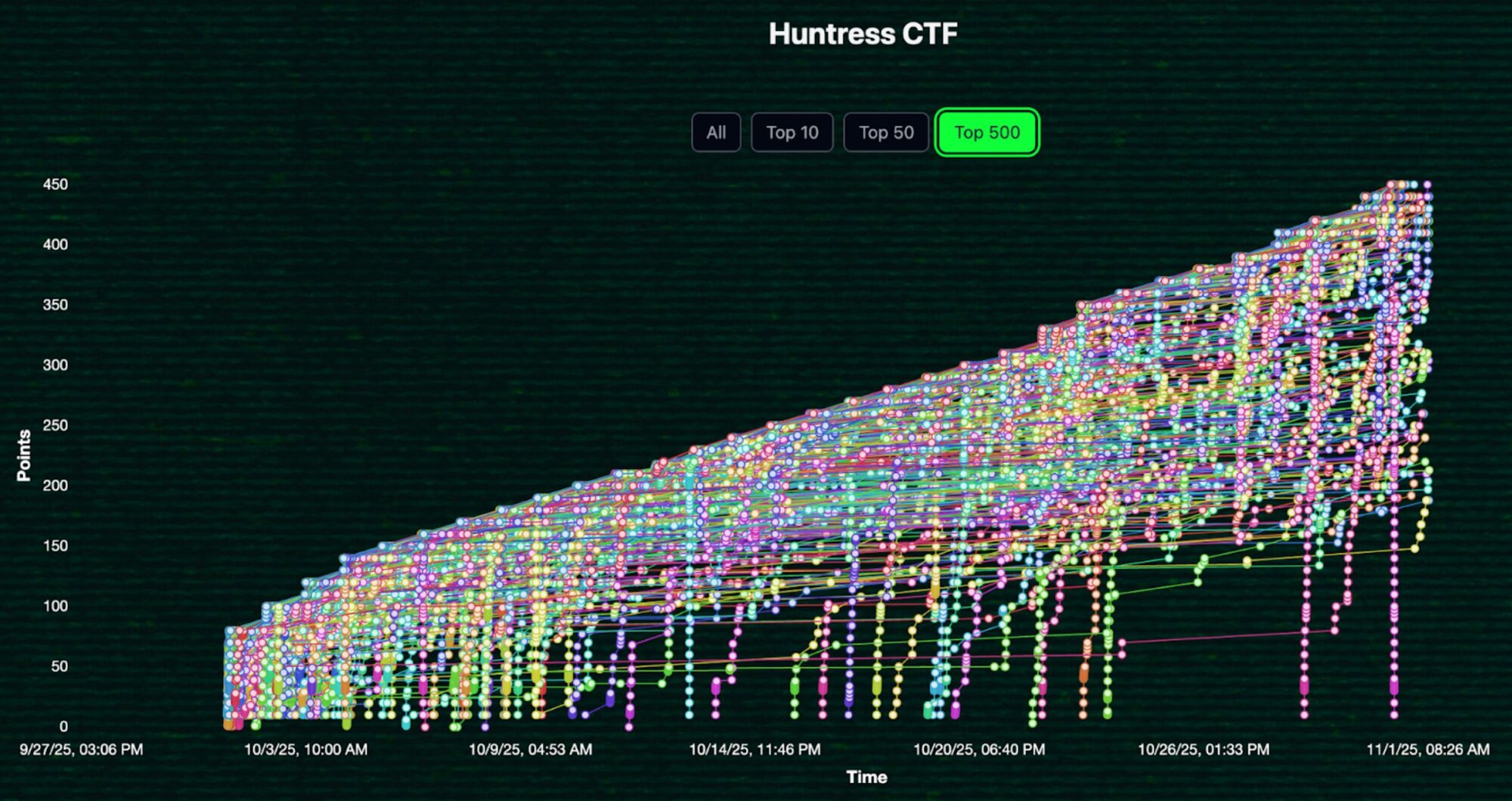
Figure 2: Huntress CTF 2025 scoreboard for the top 500 players
How CTF helps with cybersecurity awareness
The idea for the Huntress CTF came while our team was brainstorming ideas for Cybersecurity Awareness Month in 2023. We wanted to do something more than just preach about why MFA matters or why you shouldn’t reuse your passwords. We wanted people to actually come together and stay engaged in a meaningful way for the entirety of the month.
Since then, we’ve hosted CTFs every year in October with new challenges released every day during the month, like the BlackCat ransomware challenge or Whamazon (hardcore participants from 2023 and 2024 might remember these ones).
Some of our challenges have featured "Jeopardy” CTF-style challenges with options in the cryptography or web app exploitation realms. However, we’ve leaned in on DFIR and malware analysis material, because we wanted players to get a taste of the real intrusions and incidents that our security analysts were seeing out and about in the landscape.
In 2025, we also switched our CTF platform to CourseStack as our number of registered users continued to ramp up above 10,000. Check out our October Tradecraft Tuesday episode to learn more details about our CTF event’s background, featuring a conversation between John Hammond, principal security researcher with Huntress and one of this year’s CTF hosts, and Chris Myers, founder at CourseStack.
Highlights from Huntress Capture the Flag 2025
This year’s competition featured hands-on exercises around malware analysis, threat hunting, and more, while drawing from real-world malware samples, CVEs, and exploits in the wild. Here were some of our favorite challenges, and some of the writeups on them from participants:
Rust Tickler (by Nordgaren): Rust Tickler was based on real-world supply-chain malware that was re-implemented in the Rust programming language. This challenge was a tough one for players to dig through, as it involved slogging through code and reverse engineering.
Writeup: https://github.com/Rurik/CTF/tree/master/Huntress_2025
My Hawaii Vacation (by John Hammond): This challenge involved an infostealer malware sample written in Lua. To find the flag, players needed to work through deobfuscation and decode data.
Writeup: https://github.com/sp34rh34d/CTF-writeups/tree/main/Huntress2025/My%20Hawaii%20Vacation
Lizard (by Adam Rice): Lizard included a nested PowerShell malware as part of a spam-adware-style challenge.
Writeup: https://github.com/j0hn-G4lt/huntressCTF-2025/blob/main/Daily%20Breakdown/Day%2024/Lizard.md
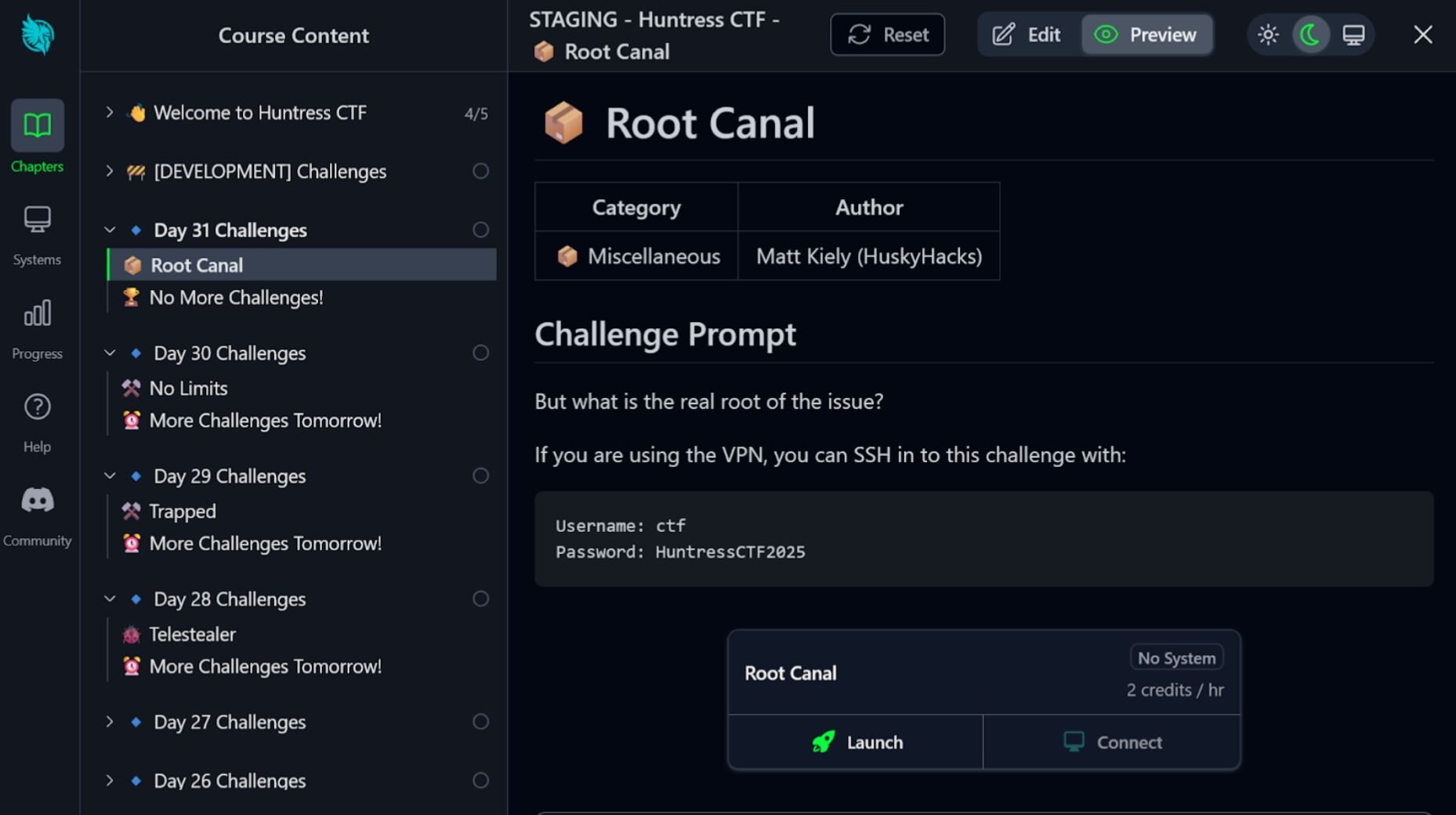
Root Canal (by Matt Kiely, aka HuskyHacks): Root Canal involved a Linux kernel rootkit that needed to be reverse engineered to find the flag on the filesystem.
Follow the Money (by Brady Heilman):An OSINT challenge that started with examining a set of .eml files to track down the flag.
Video Walkthrough: https://www.youtube.com/watch?v=IN7N_Mtm11w&list=PLibtqDrMgX7pU5ly2UI_Lk2toFhxOJ0xx&index=6
Angler (by Tim Sword): This challenge tested the limits of phishing within EntraID environments.
Writeup: https://github.com/sp34rh34d/CTF-writeups/tree/main/Huntress2025/Angler
NetSupport, Webshellz (by Ben Folland): Here, players could practice their digital forensics and malware analysis skills.
Writeups: https://mresecurity.com/blog/huntressctf-2025-forensics-challenges-full-writeup#webshellz
https://github.com/j0hn-G4lt/huntressCTF-2025/blob/main/Daily%20Breakdown/Day%2023/Net%20Support.md
Figure 3: The Root Canal challenge, which involved reverse engineering a Linux kernel rootkit
Bloopers and outtakes
The CTF wasn’t without its roadblocks, and we hit our first one early on. At the start of the competition, the number of people coming in and hammering the platform all at once led to the database load being way more than anticipated. This created a spike in 404 issues. At the same time, the function timeouts exponentially increased the log streams created on the backend, compounding the issue. Luckily, the solution was fairly quick and easy: download more RAM and restart the database server.
Meanwhile, on the competitor side, several challenges in the malware category required participants to spin out isolated virtual machines in order to analyze malware. However, some players forgot to do so. In a few cases, this even led to our Security Operations Center (SOC) analysts noticing Microsoft Defender Antivirus (MAV) alerts on impacted hosts, which pointed to files that were part of the CTF (such as Sandy.exe, which was the executable for the day three challenge referenced above).
Happy hacking–and we’ll see you next year!
CTFs are a great resource because they help participants with some of the fundamental skills needed in the hacking community–including persistence, creativity, and rethinking our strategies after failure.
A big thank you to this year’s participants and congratulations to the winners: we loved seeing the community come together this year, collaborate, and grow.
We're already cooking up new challenges for Huntress CTF 2026! Check back next October for registration details and more. And in the meantime, you can practice your skills by joining us at Tradecraft Tuesday, our monthly session dedicated to revealing hacker techniques, exploring tech, and sharpening defensive know-how.