On October 1, 2024, over six thousand people opened the Calculator application on their computer—all at the same time.
But they weren’t solving any equations or doing any sort of calculations… in fact, they were starting to analyze what process actually opened the innocent digital abacus. They would reverse engineer code, unravel and deobfuscate syntax, and look to find anything out of the ordinary: perhaps a malicious payload, a backdoor, or any special secrets that were in hiding.
This was the very start of the national Cybersecurity Awareness Month, and the very start of the 2024 Huntress Capture the Flag (CTF) event.
Soon enough, engineers, technicians, security practitioners, and students all over the globe uncovered the answer to that curious question: “What’s up with this strange calculator?”
And the answer?
flag{e55ef8d0e8da0f20e187e102832f6513}
For many people, this string of text and random gibberish may mean nothing, but for the Huntress CTF participants at the start of the month, this meant 500 points in the game—and a place on the leaderboard!
But this was only day one… they might not hold their position for long, because each and every day of the Huntress CTF competition, new challenges were released! In just 24 hours there would be new exercises, tasks, and activities to practice malware analysis, reverse engineering, and application security.
This blog is a retrospective of the great 2024 Huntress CTF. 🚩

What Is a CTF?
In case you are not familiar, a “Capture the Flag” (abbreviated CTF) event is a digital game. Not like a video game where you move a joystick on a controller—but instead, your hands fly across the keyboard to truly play a hacker’s sport.
For what is called a “Jeopardy-style” event, there are a handful of categories for different security topics each with a set of different challenges—and the competitors, either as individuals or working as a team, work to solve each exercise and uncover the “flag” to validate and prove they completed the task.
CTF events are a staple of hacker culture—and we mean the good hackers, the security professionals who remain ever-curious and strive for a deeper understanding of technology.
The Huntress CTF
Traditionally, Capture the Flag events run over the course of a weekend, or even a single day, with a short timeframe for players to sprint and solve as many challenges as they can. To celebrate Cybersecurity Awareness Month, Huntress wanted to add a special flair to a CTF competition: the game runs all month, with new challenges every day. 😎
Building on what we did last year, we wanted to foster a community for learning, with some competitive edge, but still a relaxed environment where players can take their time, take a break, and return to even more toys to play with.
The thing is, CTF competitions really test your mettle… the challenges can vary in topic, complexity, and difficulty. Players are exposed to new technologies or subjects they may never had experience with before, so struggling and learning from mistakes is all part of the game. That’s the thing about cybersecurity after all: there’s just too much out there to know absolutely everything, so we are all always learning!
But our Huntress CTF is a bit more special: we bring to the table a ton of tasks focused on “blue team” work: digital forensics, incident response, malware analysis, reverse engineering, and more. There are of course some traditional challenges for more offensive security testing, but our goal is to present to the players real-world tradecraft from threats that are out there.
And from our perspective? It was a grand slam! 💥
- 70+ total challenges throughout the month of October
- 7000+ total participating players from all over the world
- 3000+ teams competing for prizes, glory, and bragging rights
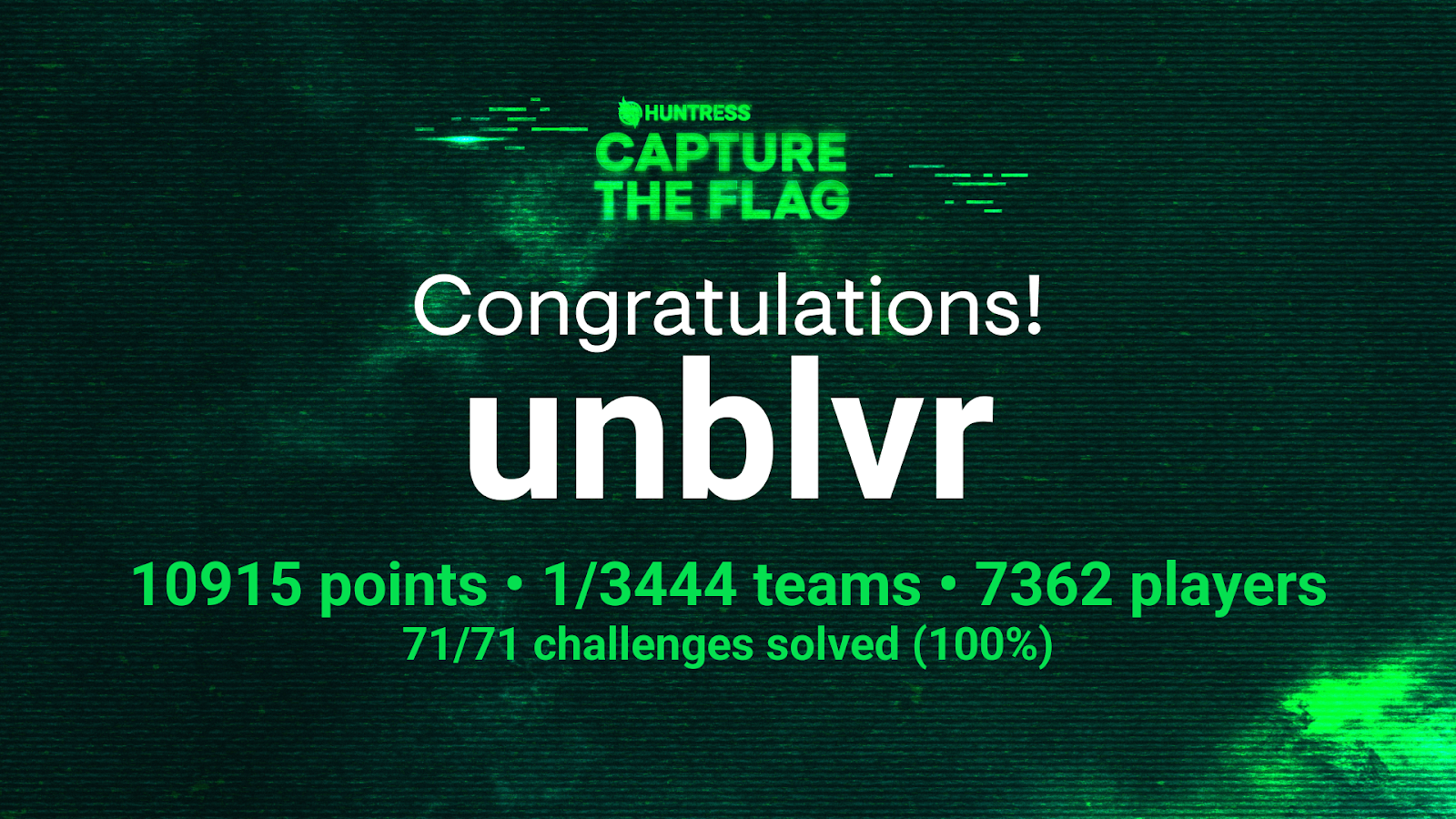
Massive congratulations to our top winner, and a huge thank you to everyone who joined us.
Throughout the game there were a handful of challenges that were inspired by and echoed real world case studies of vulnerabilities and incident response. In many cases for tasks in the “Malware” category, we would pick a payload off a real compromised endpoint, “defang” the sample and slap a flag inside—so players have challenges as real as it gets.
Some of the favorite challenges from both players and the development team:
- “MOVEable”, an homage to the MOVEit Transfer exploitation
- “Zippy”, a tribute to the SysAid vulnerability
- “HelpfulDesk”, a hat tip to the ScreenConnect “SlashAndGrab” chronicles
And other top-shelf multi-part incident response tasks:
- “Little Shop of Hashes”, a recreation of a real Pass the Hash intrusion
- “Nightmare on Hunt Street”, a SOC analysts’ day-to-day effort in log analysis
More difficult and hardcore challenges like “OceanLocust,” “Rustline,” and “GoCrackMes” kept players up at night reverse engineering complex compiled binaries. Others were chasing OSINT findings to find hackers with “Ran Somewhere,” cracking ciphers with “Base-p-,” uncovering clues to the “Mystery” challenge, or taking on “Discount Programming Devices.”
And yet, we still left room for the zany, off-the-wall kinds of challenges that are so near and dear to the CTF culture. Battle a samurai in the terminal in Sekrio, overwater plants to gain a reverse shell in Plantopia, and stare deep into the abyssal black square emojis in The Void. A good mix of real-life challenges and levity goes a long way. We never take ourselves too seriously, after all.
For the finale and capstone challenge, Adam Rice closed out the game with his masterpiece, “Palimpsest.” Taking its name from an archaic type of manuscript that has been effaced to write over, this challenge had players racing for the number one spot. By analyzing a set of Windows event logs chock full of secrets to unravel, players secured their final spots on the leaderboards and closed out an action-packed month.
So Long, and Thanks For All The Phish!
The goal while participating in a Capture the Flag event should not always be “to just win”—it’s to learn something new, and ultimately, to have fun.
CTFs bring the hacking community together and help us all collectively grow. Even if you don’t solve all the challenges, you can read writeups and solutions after the event and see all the tricks and tools you didn’t know before. That’s the best part—spreading the education and awareness, and helping level up our whole industry.
We hope the 2024 Huntress CTF was a great initiative for that. And we look forward to raising the bar for next year.
















