Hackers are there all the time: lurking in the shadows, constantly hunting for weak points in your networks, or stumbling on their next target. You can ignore this and hope for the best, risking time, money, reputation, and a lot of unnecessary stress. Or you can fire up a reliable cybersecurity hygiene strategy that wrecks a hacker’s day and locks them out for good.
If the latter is your plan (we hope it is!), keep reading for our hot takes on cyber hygiene, straight from the threat hunters in our 24/7 Security Operations Center (SOC). They see everything (and we mean everything) that hackers are doing around the clock to get access to your data, systems, and people.
What is cyber hygiene?
Think of cyber hygiene as the digital version of brushing your teeth. It’s all about maintaining healthy habits and routines to keep your IT environment safe and clean. Skipping over these steps, even once in a while, increases the risk of vulnerable exposures, just like cavities when you don’t brush regularly.
Now, let’s get into the cyber hygiene tips that will flip the script on hackers.
Double bolt the front door with multi-factor authentication (MFA)
Passwords aren’t enough anymore. That’s why MFA should be part of your security playbook with few to no exceptions.
With MFA, hackers have to pick two locks on your perimeter instead of one (username and password) to access your identities and endpoints.
For users, MFA adds an extra step, like a code sent to their phone or a fingerprint scan. Yes, this might be a little annoying or inconvenient.
But for hackers, this is a total buzzkill. They’re locked out. They can’t authenticate in your environment unless they get or replicate access to this secondary lock you’ve set up.
We can’t stress enough how important it is to turn on MFA for all external-facing services whenever possible. Build a hostile, thorny, and prickly fortified wall around your email accounts, payment portals, and VPNs at a minimum.
Stop clicking like it’s 2005
We’ve all received (and ignored) those weird emails or text messages from “EZPass” or “USPS” demanding urgent action.
We all know that those aren’t legit, but phishing, vishing, and smishing scams are still cheap and easy hacks for cybercriminals to sneak in unnoticed.
- Be wary of emails or messages asking you to open attachments, click links, or “log in” to your account
- Always double check sender details and think before you click
So, if it’s an unexpected message that makes you scratch your head, someone might be trying to take advantage of your trust to get access to systems, data, or money. Ignore it and keep on moving!
Always patch things up
Updates and patches might not seem like a big deal. You might even gloss over them once in a while. But these low-key security defenses should never be ignored because out-of-date software is an open invitation for unauthorized access into your environment.
Hackers look for outdated applications, operating systems, and firmware to exploit vulnerabilities you haven’t fixed or might not even know about. If you aren’t regularly patching, it’s a safe bet you’ve got unknown, exploitable exposures on your attack surface that hackers use as easy access points.
Here are a few things to remember so updates aren’t a headache:
- Automate patches where you can so they install without human interaction
- Use attack surface management to prioritize patching where you need it most
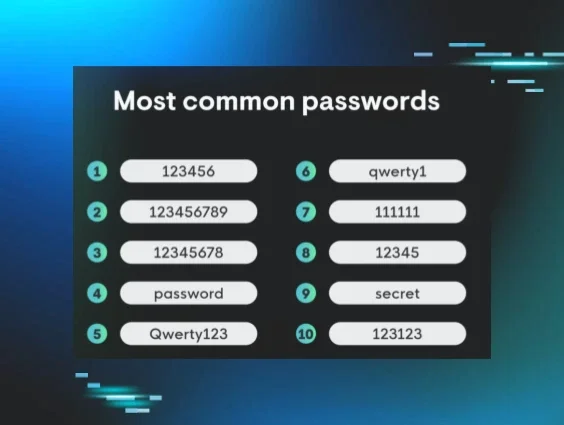
Hell yes to strong passwords
If you’re using “123456” or “secret” as your password, you might want to start rotating those ASAP. These are two of the most commonly used passwords, and hackers love weak passwords like you love Friday nights.
What should strong passwords look like? Think: complexity.
Storage for your passwords is equally important. You can make your passwords elaborate, but it doesn’t matter if they aren’t securely managed. Invest in secure password managers and stop using plain text passwords. If you’re curious about how your password storage policies stack up to others, check out the "Top 10 Worst Places to Store a Password."
Does Remote Desktop Protocol (RDP) really need to be exposed?
Our SOC runs into far too many brute force attacks on exposed Remote Desktop Protocol (RDP). Hackers lock onto vulnerable RDP until they gain unauthorized access to scope out your network, escalate privileges, move laterally, and steal sensitive information.
So don’t leave RDP exposed if you don’t need to. And if it does need to be internet-facing, consider putting it behind a VPN with MFA for extra layers of protection. Or maybe you don’t need RDP at all, so just disable it altogether. Problem solved.
Worried that RDP will be a weak point? Managed Security Information and Event Management (SIEM) is an early warning system for brute force attacks on RDP. If attackers find vulnerable RDP instances on your perimeter, SIEM will tip off SOC analysts so they can shut things down before your endpoints get caught in the crosshairs.
Learn about our SOC’s technical analysis of vulnerable RDP exposures in our blog "Brute Force or Something More? Ransomware Initial Access Brokers Exposed"
Watch out for weird behavior
Once hackers get into your environment, they’ll start taking steps to hide in plain sight, covering their tracks. Some of this activity is harder to spot, but all of it should look sketchy compared to legitimate traffic.
Some red flags to look out for include:
-
Microsoft Defender modifications
- Strange domain enumeration
- Unexpected registry modifications
- New or changed administrative privileges
- Logs and forensics clearing
If you’re not sure how to catch all of these different activities, Huntress Endpoint Detection and Response (EDR) and Managed Microsoft Defender watch your endpoints for you 24/7. They alert our SOC to strange behaviors of possible compromise so they can step in right away, fix the problem, and let you focus on what matters most for your business.
Create strong allow and deny lists
Yes, you need to be strict. Purposefully managing allowed or blocked applications, resources, and network traffic is a huge step toward keeping attackers out.
For example, if a user doesn’t need Windows OpenSSH, block it or remove it from the host. If VPN logins aren't allowed from specific locations, make sure they're on the deny list. Clearly defining unwanted access rules, especially with help from Huntress Identify Threat Detection and Response (ITDR) means minimal risk and exposure.
Example of the Unwanted Access Rules capability in Managed ITDR
Log data smarter, not harder
When hackers get into your system, they love to mess with logs to throw you off their trail. They might overwrite logs to hide their dirty work.
Logs are a superpower that let you peel back the layers of a cyberattack to figure out what happened and how to avoid it in the future. But logging security data can be pricey and cumbersome, especially for small teams that are understandably overwhelmed with alert fatigue.
Here are a few ideas to get data logging into your cybersecurity hygiene routine:
- Create an asset inventory, figure out what to log, and store backups in separate locations
- Managed SIEM takes the burden off your team with SOC investigative and response powers. Plus, we only take the security data that really matters, so you’re not paying for data storage you don’t really need.
Use complex conditional access
Need better oversight on who can access which resources in your environment? Consider adding conditional access policies (the more complex, the better). These if / then scenarios dynamically control access to protected resources by setting out conditions the user must meet to gain access. In other words, if you want access to Microsoft 365, then you must use MFA (not just credentials).
The more complex the access policies are, the tougher it is for attackers to crack the rules you’ve set up. This is another cybersecurity hygiene option that keeps things clean and helps build a thicker perimeter moat so hackers are up against multiple layers of your security stack instead of one.
Step up your cyber hygiene
Cyber hygiene isn’t just a buzzword anymore. You can’t afford to not think like a hacker anymore, or get help from experts who do. Give your security program a scrub and consider running with managed services to fortify your defenses for the long term.
Try it out now with a Huntress free trial.