But what is threat intelligence, why does it matter, and how can it protect your business from cybercriminals? This cybersecurity amplifier involves the collection, analysis, and actionable use of information about current and emerging threats, helping companies make informed decisions about protecting their networks, data, and people.
This blog unpacks the main goals of cyber threat intelligence, why there are four distinct types, and strategies to measure the benefits of threat intelligence in your overall security strategy.
What is threat intelligence, and why is it important?
“Threat intelligence is understanding what adversaries are doing, how they’re doing it, finding ways that you can implement the data to detect and disrupt them, and areas you can gain advantages over attackers,” says Greg Linares, Principal Threat Intelligence Analyst at Huntress. The goal is to give organizations actionable insights to anticipate and mitigate risks before major damage is done.
Attackers are constantly finding creative ways to exploit vulnerable exposures in your environment and avoid detection. Threat intelligence contextualizes raw threat data from these attacks on your attack surface and transforms it into meaningful info that organizations can use to make informed decisions about defending against cyber threats, whether those threats target networks, systems, data, or people. By giving actionable info on current and emerging threats, threat intelligence helps businesses get the upper hand to stay steps ahead of malicious threat actors.
Why threat intelligence matters
Informed decision-making
Optimized defense readiness
Stronger culture of security awareness
One key benefit to using threat intelligence is improved and informed decision-making. Threat intelligence gives security teams accurate, up-to-date information, helping them prioritize responses and allocate resources more effectively, especially when alert fatigue is real.
Another major advantage is the ability to identify vulnerabilities before they can be exploited. By understanding the tactics, techniques, and procedures (TTPs) used by threat actors, organizations have a better idea of how they might be targeted and can boost their defenses. Additionally, threat intelligence enhances IR, reducing the time to detect, contain, and remediate attacks. This minimizes potential damage and operational disruptions to business as usual.
Finally, adopting a threat intelligence-driven approach builds a security culture of vigilance and preparedness, preparing organizations to both strategically and tactically cut down risks.
Without threat intelligence as part of the cybersecurity foundation, businesses are stuck cleaning up cyberattacks rather than stopping them. The ability to anticipate and stop cyberattacks from happening, instead of reacting to them, makes threat intelligence a crucial investment for any security-minded organization.
How is threat intelligence different from threat data?
Before we keep going, it’s important to differentiate between threat intelligence and threat data. It’s a common misconception to equate these two types of intelligence. While they’re interconnected, they’re not the same and don’t give the same results. Here’s why:
-
Threat data is raw, unrefined threat information, such as logs of failed login attempts (think brute force attacks), suspicious network traffic, malware files, or malicious workstation names. It holds potential value but requires additional analysis from a Security Operations Center threat hunter or security researcher, for example, to be actionable. Individual pieces of data from Managed Endpoint Detection and Response (EDR) alerts, like evidence of enumeration or credential dumping, are threat data.
-
Threat intelligence, on the other hand, is what happens when you take that raw data, consolidate it, analyze it, and derive actionable insights. It’s the result of analyzing pieces of threat data to deliver useful insights, such as tactics, techniques, and procedures (TTPs), tradecraft trends, attacker motives, and potential targets. For example, when our SOC analysts retroactively put Security Information and Event Management (SIEM) data with EDR compromise data mentioned above, a bigger picture comes to light of how, when, what, and where the incident occurred.
Threat data might tell you that four failed login attempts occurred from a specific IP. Threat intelligence would identify a pattern showing that the IP is part of a larger brute-force attack campaign targeting your industry.
“We regularly look at EDR event data month over month to better correlate the who, what, where, and why of incidents. So we start by piecing together the raw data of several alerts that have common attack vectors. We dig deeper to link raw threat data commonalities between the compromised customers, their verticals, time of attack, and geography to make a threat intelligence picture that feeds into and informs our managed security solutions like EDR and SIEM,” says Linares.
Check out this example to see how our SOC links threat data to build a bigger threat intelligence story with the full attack path and associated bigger ransomware trends:
Think about it this way: Threat data is like having pieces of a puzzle. Threat intelligence is the assembled puzzle that provides a clear picture.
Types of threat intelligence
There’s no cookie-cutter approach when it comes to threat intelligence. It’s grouped into four distinct types, each serving a unique role in an organization’s security strategy:
1. Strategic
Focus: High-level analysis for executives and decision-makers to understand long-term trends, risks, and industry-specific threats
Purpose: Helps in formulating long-term security tactics and budgetary decisions
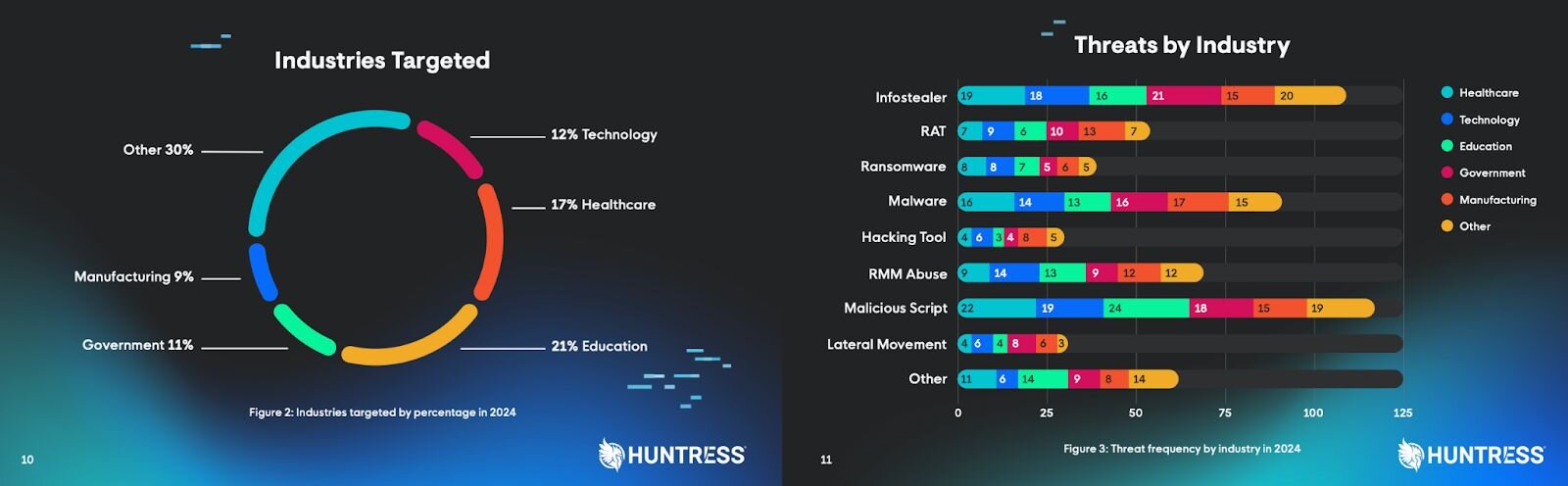
Example: The Huntress 2025 Cyber Threat Reportshows significant cybersecurity trends uncovered from monitoring millions of endpoints and thousands of organizations throughout 2024
Figure 1 - Most targeted industries and most frequent threats by industry vertical in 2024
2. Tactical
Focus: Information about adversary tactics, techniques, and procedures (TTPs)
Purpose: Gives security teams knowledge of how attackers operate
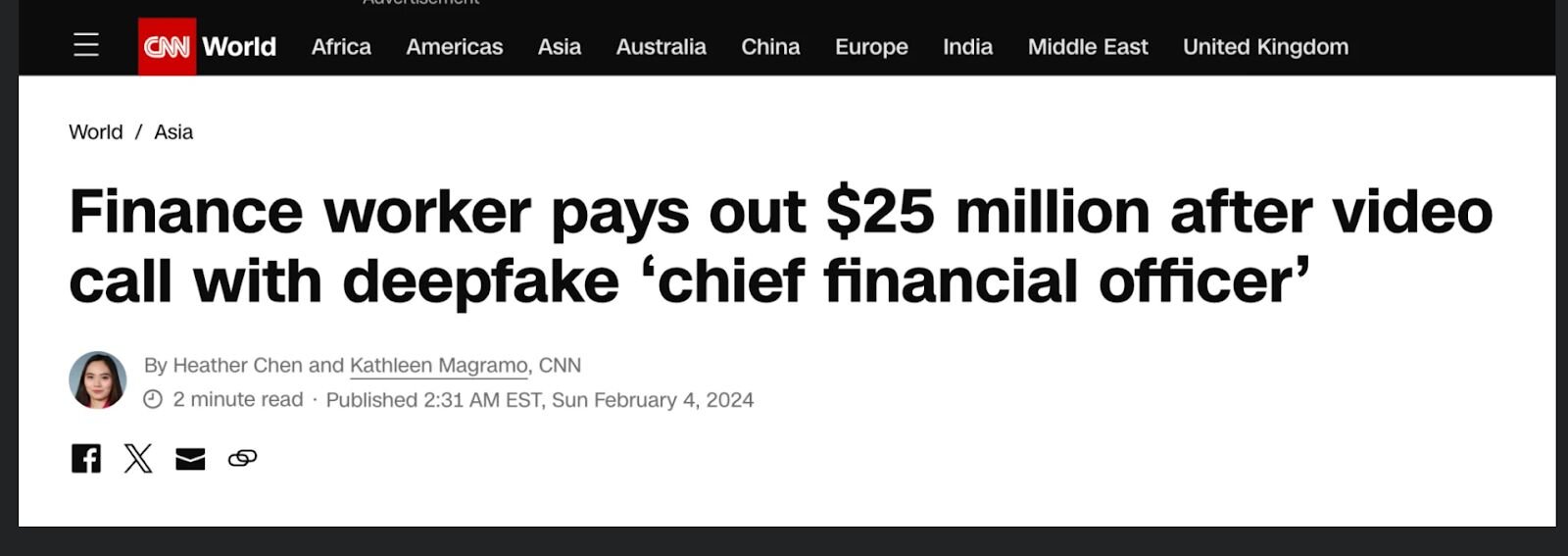
Example: Recognizing phishing schemes targeting employees in a specific industry
Figure 2 - Image showing a type of phishing scheme
3. Operational
Focus: Details of specific attacks, including attack timelines, threat actors, and their motivations. It’s real-time or near-real-time detection of cyberattacks focused on who, what, when, where, and how an attack goes down.
Purpose: Supports response planning and immediate risk mitigation
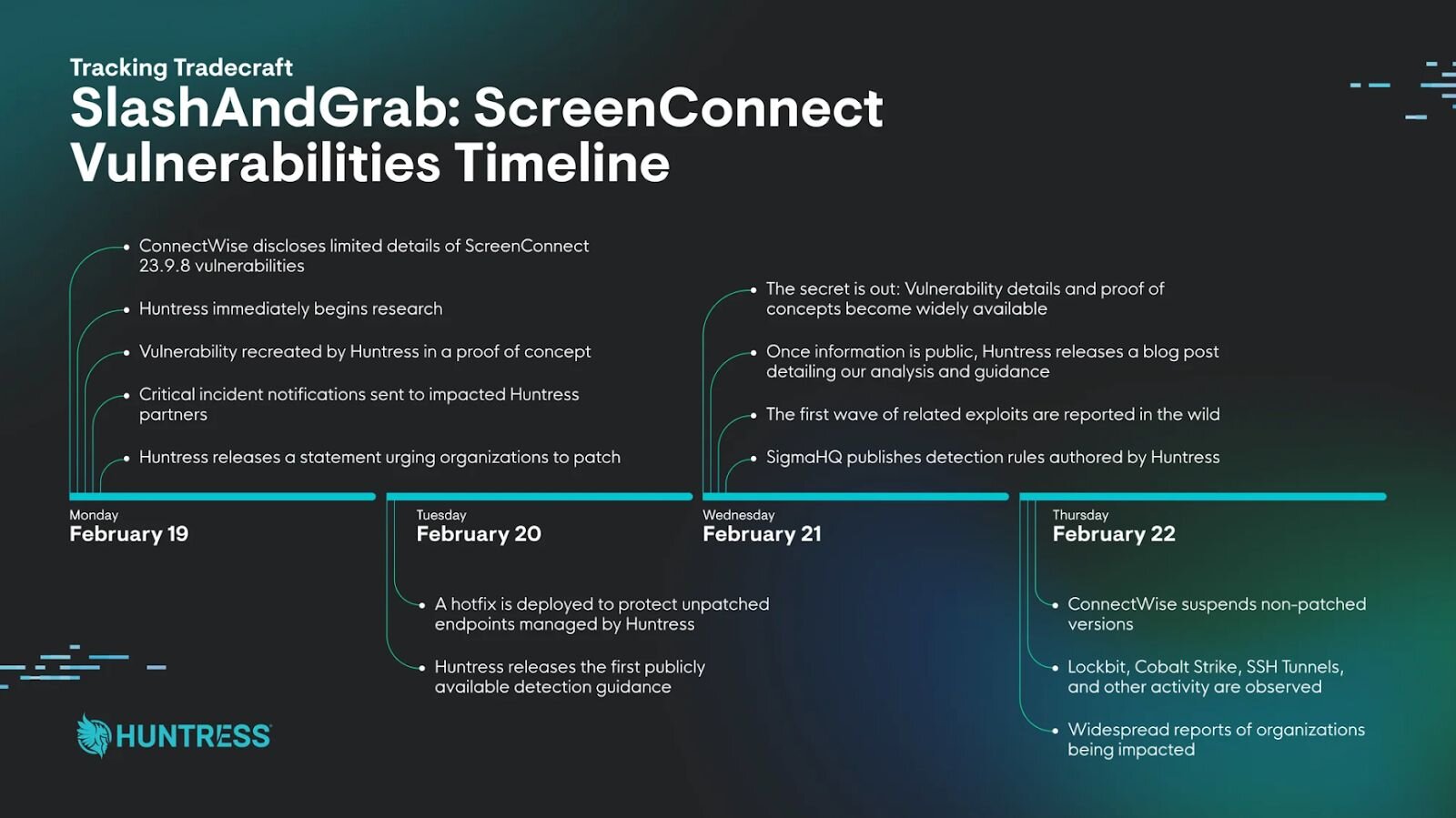
Example: Intelligence on how ransomware groups are using Remote Monitoring and Management (RMM) software to infiltrate, move laterally, and exfiltrate stolen data from victims.
“At Huntress, one of the ways we focus on operational intelligence is for a deeper understanding of ransomware groups: who are the malicious actors, how they’re operating, their TTPs, and how we can identify them,” says Linares.
Figure 3 - Image showing the timeline of the ScreenConnect vulnerabilities incident
4. Technical
Focus: Information on Indicators of Compromise (IOCs) such as IP addresses, domains, malware hashes, and email headers
Purpose: Sheds light on granular details that help with identifying and addressing specific threats. It’s often used by security teams for deep analysis and developing countermeasures
Example: Sharing real-time data about malicious IPs or workstation names with a firewall to block access
“A good example of technical intelligence is when we have a rapid response incident. Our deep dive technical research involves things like reverse engineering, Proof of Concept (PoC) development, and technical trends that we publish in blog posts for broader community awareness,” says Linares.
Here are a few examples of technical intelligence in action:
CVE-2025-30406 - Critical Gladinet CentreStack & Triofox Vulnerability Exploited In The Wild
Threat Advisory: Oh No Cleo! Cleo Software Actively Being Exploited in the Wild
SlashAndGrab: ScreenConnect Post-Exploitation in the Wild (CVE-2024-1709 & CVE-2024-1708)
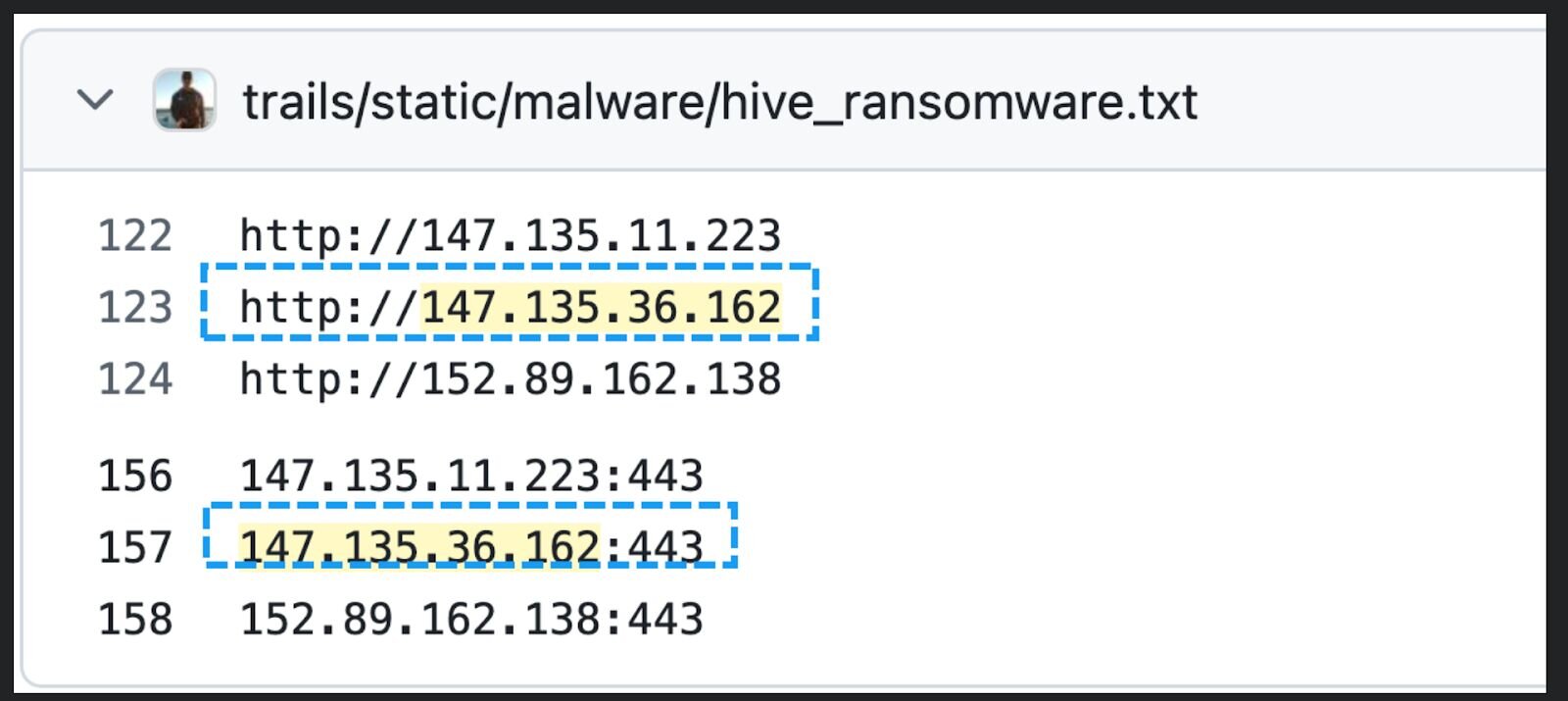
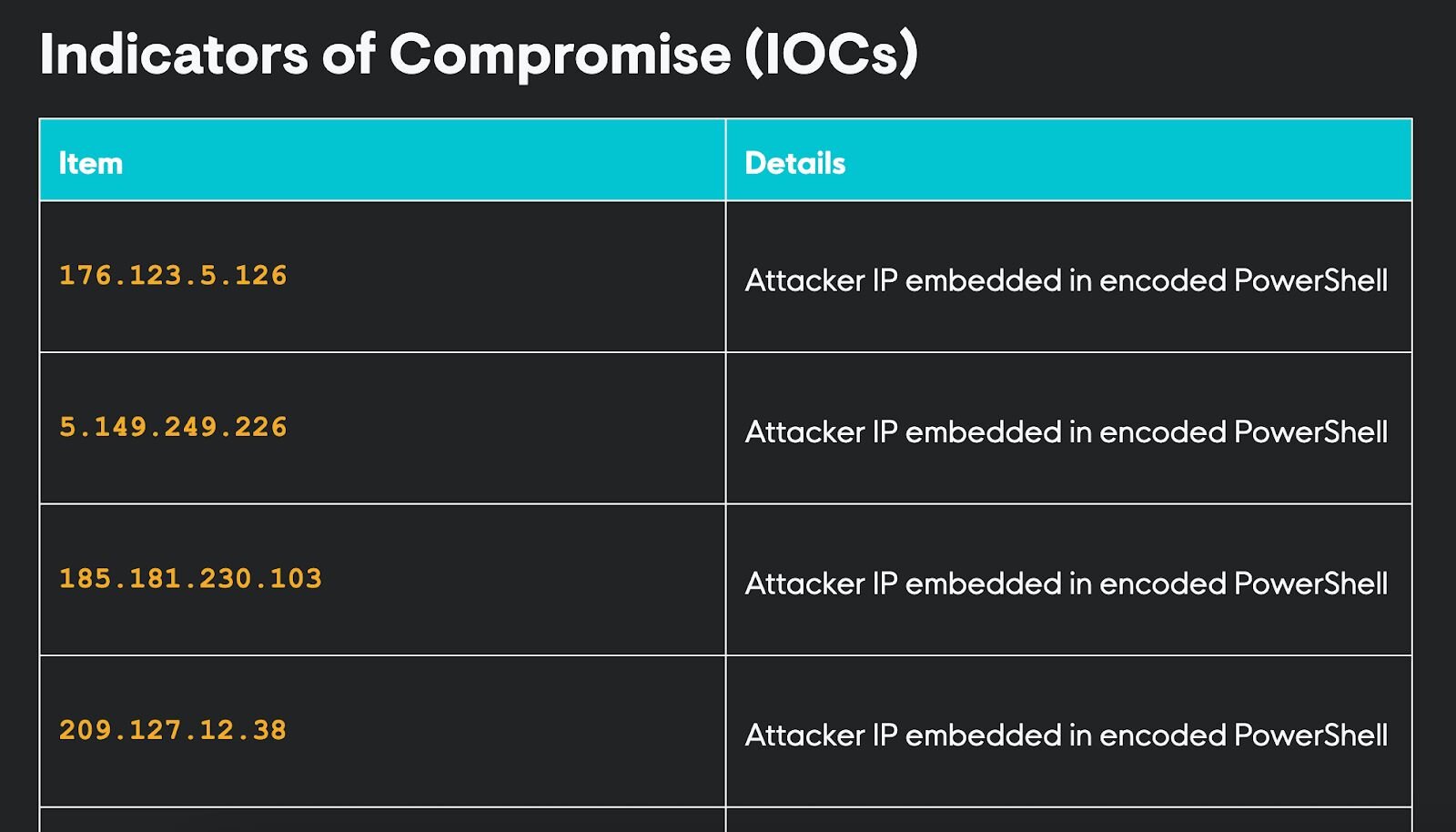
Figure 4 -Image showing brute force IP addresses associated with Hive ransomware
Figure 5 - Example of IOCs for Cleo’s LexiCom, VLTransfer, and Harmony software (CVE-2024-50623)
How to get started with threat intelligence
If you want to bring threat intelligence into your organization’s cybersecurity program, consider these steps to help you get started:
Lay out the objectives: Define clear goals for your organization’s threat intelligence needs, like reducing response time, predicting attack trends, or improving vulnerability management
Scope what you’re working with: Figure out whether your organization has the necessary team and resources to act on threat intelligence or if outsourcing is a better option
Identify reliable sources: Investigate the capabilities of different threat intelligence feeds. Choose one that aligns with your business's cybersecurity goals.
Start small: To test the waters, start with a limited set of use cases, like monitoring phishing threats or identifying ransomware trends. Expand slowly so the team doesn’t get overwhelmed with information to act on.
Work together internally: Don’t keep threat intelligence in a silo! Talk about how to optimize threat intelligence insights with your IT team, security personnel, and decision-makers.
Pick the right tools: Don’t get lost in the threat intelligence weeds. Use a Threat Intelligence Platform (TIP) to aggregate, process, and analyze threat data efficiently.
Train Your Team: Invest in your people. Security tools aren’t enough if your team doesn’t know how to interpret and use the intelligence to improve security.
What’s the ROI of investing in threat intelligence?
The return on investment (ROI) of threat intelligence is more nuanced than other solutions like EDR or SIEM, but overall, it helps security teams make smarter decisions on both strategic and tactical levels, which saves money and cuts down unnecessary costs in the long run.
Key ROI benefits of threat intelligence are:
Less frequent data breach payouts: In 2024, the global average cost of a data breach reached $4.9 million, the highest total ever, and a 10% increase over 2023.
Improving your team’s ability to identify and respond to threats faster
Better efficiency by focusing on relevant threats more likely to do damage
Less operational downtime: Fast and comprehensive threat response keeps business operations running smoothly.
Better brand trust: Level up trust with your customers, partners, and investors. Taking all possible measures to safeguard sensitive information like personally identifiable information (PII) and financial data shows a business is serious about cybersecurity for itself and its clients. This may lead to bigger, better deals in the future.
Supporting compliance regulations and cyber insurance requirements, which avoids pricy penalties.
Investing in threat intelligence isn’t just good practice; it’s good cost-saving business for the long haul.
What types of IOCs should businesses monitor?
Indicators of Compromise (IOCs) are crucial pieces of threat intelligence evidence for accurate and timely threat detection. They’re like digital breadcrumbs of malicious activity in your environment. However, the IOCs you monitor for detection should depend heavily on the unique characteristics of your security stack, IT infrastructure, industry vertical, and geographic focus in the threat landscape. It’s not a one-size-fits-all threat intelligence solution.
Here are examples of commonly monitored IOCs:
Suspicious IP addresses attempting to access your systems
Malware file hashes flagged by your antivirus
Domains linked to phishing attacks
Strange outbound traffic patterns
Unauthorized access attempts from unfamiliar IPs
Unusual behavior or actions from workstations or accounts
Regularly updating IOC databases with fresh threat intelligence feed information helps make sure your defenses stay up-to-date with threat actor tactics. Frequent updates to your monitoring criteria are crucial for accurate and actionable threat intelligence.
Integrating threat intelligence into SIEM and SOAR
One of the best ways to take threat intelligence to the next level is to integrate it with Managed Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms. These tools are force multipliers for threat intelligence. They’re designed to collect and analyze security events from your systems, speeding up threat detection and response times.
Here are the key benefits of combining threat intelligence with SIEM and SOAR:
Automation: Automate the identification and prioritization of suspicious red flag activity with known and confirmed threats from threat intelligence feeds
Incident prioritization: Flag false positives with certainty by enriching your SIEM alerts with context from threat intelligence feeds. Improve your focus on the threats that matter most.
Proactive response: SOAR tools can automate threat mitigation actions by blocking things like sketchy IPs from threat intelligence feeds and improving detection and response capabilities, especially for small security teams
Together, SIEM and SOAR turn threat intelligence insights into action, making it a strategic and value-added service for security programs.
Threat intelligence source feeds
Threat intelligence feeds are categorized into commercial and open-source options. Most organizations benefit from combining both types for the most well-rounded coverage.
Commercial threat intelligence feeds: Pay-for-use services offer comprehensive threat intelligence enriched with analytics and APIs for easy integration. They’re high-quality, validated data tailored to your industry vertical.
Typical advantages include:
Access to subject matter experts
Reliable updates on new vulnerabilities, malware, and attack patterns
Customization for your organization’s unique security needs
Integration options with existing security tools and platforms
Advanced analytics
Disadvantages: a hefty price tag and often requires a dedicated team to fully utilize Open Source threat intelligence feeds: Publicly available information that’s collected and analyzed to identify, assess, and respond to cyber threats. Data is collected from a wide range of sources with varying degrees of fidelity, like news articles, blogs, social media, forums, public databases, and the dark web.
Advantages: free and accessible to all
Disadvantages: be prepared to validate, correlate, and filter available information to your needs
Remember, when using threat intelligence to improve detection and response, your sources matter.
Validating and prioritizing threat intelligence
Not all intelligence has equal value. To make sure you’re maximizing your resources effectively:
Validate: Cross-check threat intelligence with multiple sources to confirm its relevance and veracity
Prioritize: Pay close attention to threats impacting your industry, technology stack, and geographic location. Focus on imminent and high-impact risks over low-priority or outdated threats
Automate: Use automation tools to correlate feeds with your current vulnerabilities
“Validating and prioritizing threat intelligence for our teams at Huntress is all about what we’ve seen threat actors do in the past, what we know has impacted our partners and customers, and what our customers have installed in their systems and machines. This makes a big impact in preventing ransomware attacks, for example, because we can use patterns and trends to make predictive mitigations for our partners and customers,” says Linares.
Measuring the effectiveness of your threat intelligence program
How do you know if your efforts with threat intelligence are working? Track these metrics:
Mean Time to Detect (MTTD): How quickly is your team identifying threats? MTTD is the average time between the beginning of a security incident and its discovery by the security team. Bring threat intelligence into your security program and check to see if your average threat identification time shortens over time.
Mean Time to Respond (MTTR): How long is the response time after detection of a potential threat? MTTR is the average time it takes from the discovery of an incident to remediation. For example, our Huntress Security Operations Center (SOC) has an average MTTR of eight minutes!
Incident Reduction: Are the number and severity of breaches decreasing? If threat intelligence is working correctly, major security incidents should go down in frequency and criticality, leaving more time to focus on proactive security and less time putting out cyberattack fires.
Cost Savings: Are you avoiding costly downtime and recovery expenses? A recent report that surveyed 450 CISOs, CIOs, and IT security leaders revealed that 43% had unplanned downtime from a cyberattack. That’s time, money, and potentially reputation down the drain.
Threat intelligence isn’t a static security solution, so it’s important to regularly review your strategy to keep up with emerging threats and scaling business goals. Continuously monitor and fine-tune your threat intelligence program for optimal results.
Build a safer future with threat intelligence
Threat intelligence isn’t just about defending organizations from cyberattacks. It’s about empowering them to operate confidently and proactively in a digital world brimming with risks and vulnerabilities. Whether you’re just starting to explore or looking to enhance an existing program, investing in threat intelligence is a move toward building a strong security stack.


Protect What Matters