Network File System (NFS) is a distributed file system protocol developed by Sun Microsystems that allows users on client computers to access files over a network as if those files were locally stored. NFS is a common attack surface in enterprise environments because misconfigured NFS shares can expose sensitive data to unauthorized users.
Key Takeaways
By reading this guide, you'll learn:
- What NFS (Network File System) is and how it operates on a client-server model using RPC and TCP
- Why NFS versions matter for security — and why NFSv3 remains dangerously common despite lacking authentication and encryption
- The most exploited NFS misconfigurations, including world-readable exports, disabled root squashing, and UID/GID spoofing
- How attackers find and access exposed NFS shares with no credentials required
- How NFS compares to other file sharing protocols like CIFS and SMB
- The answers to the most common NFS security questions, including port usage, encryption, lateral movement risk, and the showmount command
Understanding NFS and Its Role in Modern Networks
Network File System operates on a client-server model where one machine (the server) shares its files and directories with other machines (the clients) over a network. When properly configured, users can access remote files as naturally as opening a document on their local hard drive. Organizations commonly deploy NFS in environments where multiple users need to collaborate on shared files, such as development teams working on code repositories or research institutions sharing large datasets.
The NFS protocol uses Remote Procedure Calls (RPC) to handle communication between clients and servers and also uses the standard TCP three way handshake (syn, syn-ack, ack) to transfer packets between clients and servers. When a client requests a file, the NFS server processes the request and either grants or denies access based on configured permissions. Continue reading on to see how NFS’s security configuration has evolved over the years.
NFS remains popular in enterprise environments, particularly those running Linux-based systems. Cloud providers frequently support NFS for shared storage solutions, and many organizations use it for:
Development environments where teams need shared access to code repositories
Scientific computing applications requiring access to large datasets
Backup and archival systems
High-performance computing clusters
What Is NFS (Network File System)?
NFS (Network File System) is a distributed file system protocol that allows users and applications on one computer to access files stored on another computer over a network, as if those files were stored locally.
Originally developed by Sun Microsystems in 1984, NFS is widely deployed in Linux and Unix environments, and is commonly found in enterprise networks supporting development teams, data storage infrastructure, and cloud workloads.
When configured correctly, NFS is a legitimate and useful protocol. When misconfigured — which is common — it becomes one of the easiest entry points an attacker can exploit.
How NFS Works
NFS operates on a client-server model:
- A server exports one or more directories and makes them available over the network
- A client mounts those exported directories and accesses them as if they were local storage
- Communication happens over TCP/UDP port 2049, with the RPC portmapper running on port 111
- Access control is managed through the server's export configuration file (
/etc/exportson Linux systems)
The critical security issue: in older NFS versions, that access control is based almost entirely on IP address and hostname trust — not on strong authentication.
NFS Versions and Security Comparison
| Version | Authentication | Encryption | Recommendation |
|---|---|---|---|
| NFSv2 | IP/host-based only | None | Do not use — deprecated |
| NFSv3 | IP/host-based only | None by default | Common but insecure |
| NFSv4 | Kerberos supported | Optional (krb5p) | Recommended with Kerberos |
The bottom line: NFSv3 — still the most widely deployed version — has no native encryption and relies on network-level trust for access control. This makes it inherently risky in any environment where network access isn't tightly controlled.
Why Is NFS a Cybersecurity Risk?
NFS is a cybersecurity risk primarily because it was designed for trusted internal networks — not the adversarial environments most organizations operate in today.
The core security weaknesses of NFS include:
- No authentication by default (NFSv2/v3): Access is granted based on IP address or hostname, which can be spoofed
- No encryption (NFSv3 and earlier): All data transmitted over NFS is sent in plaintext and can be intercepted
- Overly permissive exports: Administrators frequently configure NFS exports with wildcards (
*) that allow any host to mount the share - Root squashing misconfigurations: When root squashing is disabled or incorrectly configured, remote users can gain root-level access to shared files
- Wide deployment, low visibility: NFS traffic often blends into normal network activity, making exploitation difficult to detect without specific monitoring
These weaknesses don't require a sophisticated attacker to exploit. In many cases, discovering and mounting an exposed NFS share takes less than five minutes with freely available tools.
What Are Common NFS Vulnerabilities?
The most dangerous NFS vulnerabilities aren't zero-days — they're misconfigurations that exist in thousands of environments right now.
1. World-Readable NFS Exports
When /etc/exports is configured with a wildcard, any host on the network (or internet, if the server is externally accessible) can mount the share:
This is the single most common NFS misconfiguration and the first thing an attacker checks.
2. Root Squashing Disabled (no_root_squash)
Root squashing maps the remote root user to an unprivileged user on the server, limiting damage. When disabled with no_root_squash, a remote user with root access on their own machine gains root-level access to the NFS share.
This is a direct path to privilege escalation.
3. NFS Over an Unrestricted Network
Exposing NFS ports (111, 2049) to the internet or broad internal network segments without firewall restrictions dramatically increases attack surface. Shodan and similar tools regularly index internet-facing NFS shares containing sensitive data.
4. UID/GID Spoofing
NFS relies on user and group IDs (UIDs/GIDs) for file permissions. An attacker who knows the UID of a privileged user on the NFS server can create a local account with the same UID on their own machine and gain access to that user's files on the share.
5. Sensitive Data Exposure via Mounted Shares
Even read-only NFS shares can expose:
- SSH private keys
- Configuration files containing credentials
- Database files
- Backup archives
- Application source code
NFS vs. Other File Sharing Protocols
Understanding how NFS compares to other protocols helps organizations make informed decisions about their file sharing infrastructure. AWS documentation provides detailed comparisons between NFS and protocols like CIFS (Common Internet File System).
NFS excels in Unix and Linux environments, offering lightweight protocol overhead and faster performance. However, it requires additional configuration for Windows compatibility. CIFS, while more suitable for Windows environments, has largely been superseded by newer SMB versions and carries its own security considerations.
The choice between protocols often depends on your organization's operating system environment, security requirements, and performance needs.
Frequently asked questions about NFS security
In cybersecurity, NFS (Network File System) is a protocol and common attack surface. Attackers target NFS because misconfigured exports can provide unauthenticated access to sensitive files, a mechanism for privilege escalation via root squashing misconfigurations, and an avenue for lateral movement within a network. NFS security focuses on hardening export configurations, enforcing strong authentication, and monitoring for unauthorized access.
NFS uses port 2049 (TCP and UDP) for file system operations, and port 111 (TCP and UDP) for the RPC portmapper service that NFS depends on. Both ports should be restricted at the firewall to only allow connections from trusted hosts.
NFS is not encrypted by default in NFSv2 and NFSv3. All data is transmitted in plaintext, making it susceptible to network interception. NFSv4 supports encryption when configured with Kerberos in krb5p mode, which provides authentication, integrity checking, and full encryption of data in transit.
Root squashing is an NFS security feature that maps the root user on a client machine (UID 0) to an unprivileged anonymous user on the NFS server. This prevents a remote user with root access from automatically having root-level control over files on the server. Root squashing is enabled with the root_squash option in /etc/exports and should be enabled on all NFS exports. Disabling it with no_root_squash creates a significant privilege escalation vulnerability.
NFSv3 relies on IP address and hostname-based trust for access control, has no native encryption, and is vulnerable to UID spoofing. NFSv4 introduces support for Kerberos-based authentication, adds encryption capabilities (krb5p), has better support for access control lists (ACLs), and operates over a single port (2049), simplifying firewall rules. NFSv4 is significantly more secure than NFSv3 when properly configured with Kerberos.
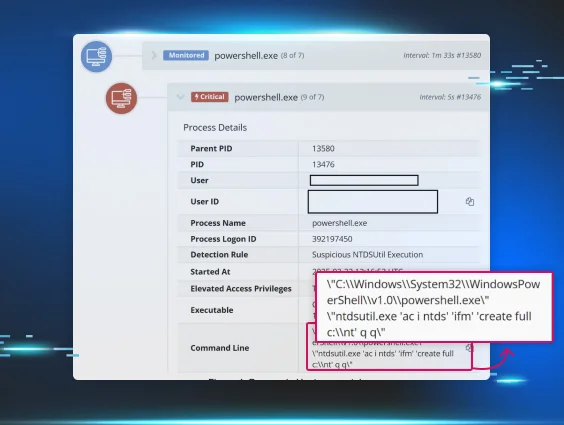
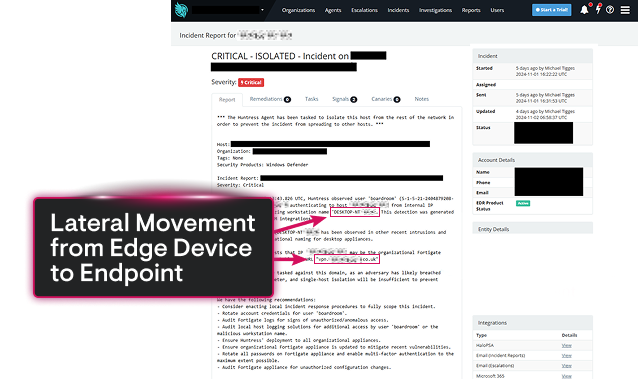
Yes. NFS is a documented lateral movement vector. Attackers who gain access to an NFS share can use it to move files and tools between systems, access credentials that enable further compromise, and in some cases directly pivot to other hosts. MITRE ATT&CK documents NFS-related techniques under T1135 (Network Share Discovery), T1039 (Data from Network Shared Drive), and T1570 (Lateral Tool Transfer).
showmount -e [hostname] is a legitimate Linux command that lists the NFS exports available on a server. It's dangerous from a security perspective because it requires no authentication — any host that can reach port 111 of an NFS server can run showmount and enumerate all available shares. Attackers routinely use this command during reconnaissance to identify accessible NFS shares. You can restrict showmount access by blocking port 111 or disabling the rpcbind service where it isn't needed.
Attackers find exposed NFS shares through internal network scanning with tools like nmap (targeting ports 111 and 2049), running showmount -e against discovered hosts, and using internet scanning tools like Shodan to find internet-facing NFS servers. Many organizations inadvertently expose NFS to the internet through misconfigured firewall rules or cloud security groups.
NFS exploitation has appeared in numerous real-world attacks and penetration tests. Common scenarios include attackers gaining initial access to a corporate network and finding NFS shares containing SSH private keys used to compromise additional servers, and red team engagements where exposed NFS shares containing configuration files with database credentials led to full environment compromise. NFS exploitation is also a standard technique in CTF (Capture the Flag) challenges, reflecting its prevalence as a real attack vector.



Staying Vigilant in File Sharing Security
NFS continues to serve as a crucial component in many organizations' IT infrastructure, but security cannot be an afterthought. The protocol's evolution demonstrates the cybersecurity community's ongoing efforts to address vulnerabilities while maintaining functionality.
Remember that no file-sharing protocol is inherently secure without proper implementation and ongoing management. Regular security assessments, proper configuration, and staying current with protocol updates form the foundation of a secure NFS deployment.
By understanding both the capabilities and limitations of NFS, organizations can make informed decisions about their file sharing strategies while maintaining the security vigilance that modern threat landscapes demand.

Related NFS Topics



Protect What Matters