There are plenty of spooky, scary things lurking in the dark—and that includes the dark web. We’re here to shed light on those shadows.
The most common cyberattacks plaguing the darkness are, unfortunately, becoming more regular, with an estimated 600 million attacks happening worldwide each day. Yikes!
The first step in reducing cyber risks is knowing what the monsters look like. The second step is understanding how you can protect your organization from external and internal cyber threats. Keep reading to learn about different types of cyberattacks, how threat actors are going about them, and what you can do to prevent future attacks.
Table of contents
- What is a cyberattack?
- Types of cyberattacks
- Malware-based attacks
- Phishing and social engineering
- Network attacksVulnerability exploitation attacks
- Other types of cybersecurity attacks
- How to protect against threat actors
- Avoid the most common cyberattacks with managed EDR
- FAQ
What is a cyberattack?
A cyberattack is defined as any malicious attempt to disrupt, damage, or gain unauthorized access to computer systems, networks, or devices. Basically, it's when someone tries to mess with your digital stuff, whether that's stealing your data, crashing your website, or holding your files hostage.
Think of it like a digital break-in, but instead of smashing a window, they're exploiting software vulnerabilities or tricking people into giving up their passwords. These attacks can range from simple annoyances like adware to serious threats like ransomware that can completely stall operations for entire organizations. They come in all shapes and sizes, and threat actors are always developing new ways to cause trouble in the digital world.
Looking to brush up on your cyber savvy? The cybersecurity glossary has your back.
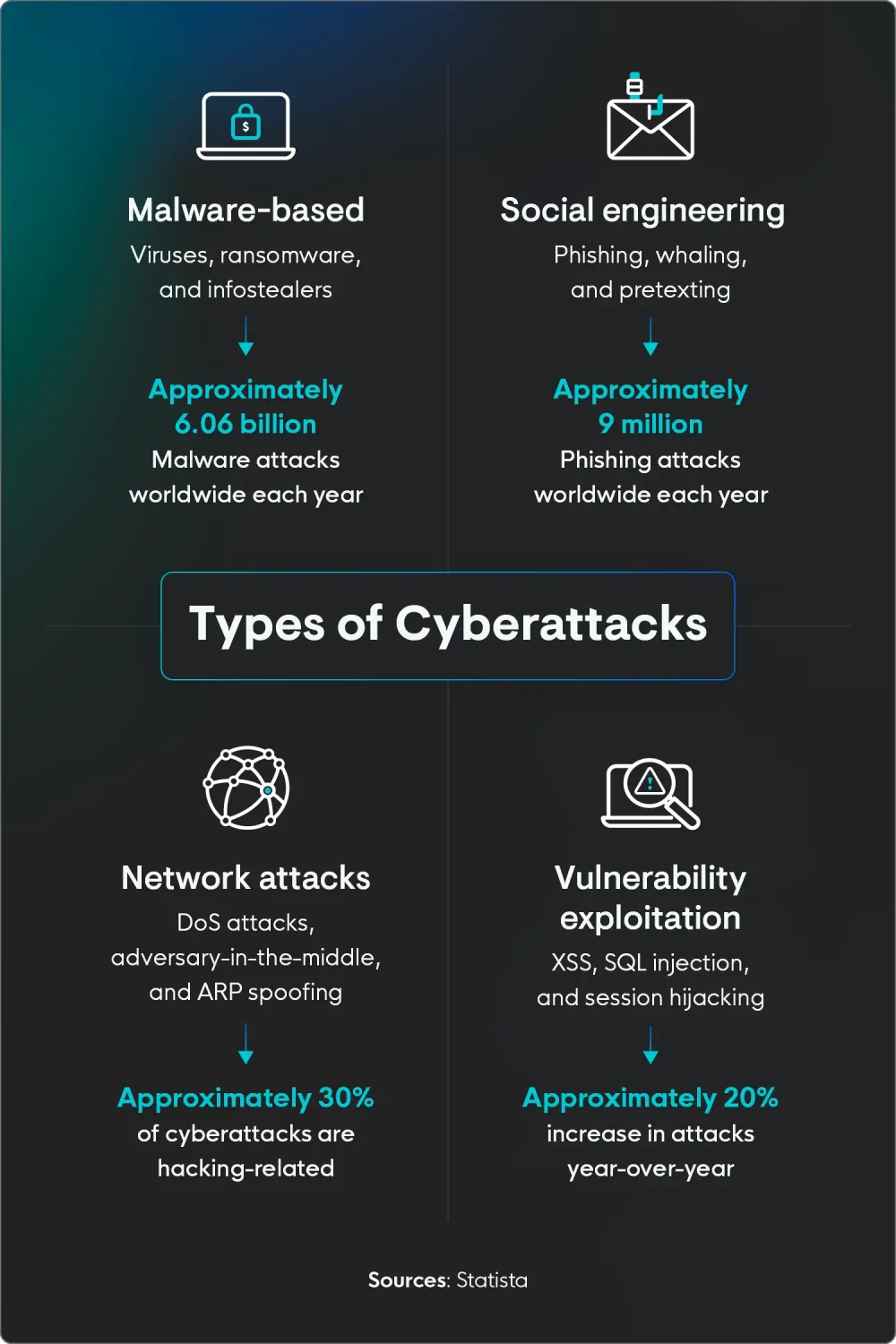
Types of cyberattacks
There are many different types of cyberattacks, and different techniques that threat actors use to carry out attacks, defined by how they gain access to the system, what they do once they’ve gained access, and what they’re after specifically. While this is not an exhaustive list, cyberattacks tend to fall under these four categories:
- Malware-based attacks: Think of malware as the digital equivalent of a nasty virus. Someone slips a sneaky program onto your device, and it starts causing trouble, whether it's stealing info, messing up files, or just generally being a pain. It's like having a digital gremlin running loose in your system.
- Phishing and social engineering: This is where the bad guys try to trick you into doing something they want. They might send a fake business email pretending to be your manager or try to get you to click a dodgy link. They play on your trust or curiosity to get what they want. It's like a con artist, but online.
- Network attacks: These attacks go after the connections between computers. Imagine someone jamming the signal on your Wi-Fi or flooding a website with so much traffic it crashes. They disrupt the flow of information, kind of like a digital traffic jam.
- Vulnerability exploitation attacks: Every software has potential weaknesses, or "vulnerabilities." These attacks occur when someone finds those weak spots and uses them to break in. It's like finding an unlocked back door to a building and going inside to cause problems.
Malware-based attacks
Malware, or malicious software, is when a software program is secretly installed onto your device. This can be done in a variety of ways, but is usually done without the user knowing in an effort to stay undetectable. Examples include:
1. Viruses
Think of a virus as a digital disease that spreads through contact. Before users even know they’ve been infected, the malicious programs start to replicate and spread.
They work by attaching themselves to legitimate files or programs. When that infected file is opened or run, the virus activates and starts spreading, potentially corrupting files, stealing data, or disrupting system operations.
Threat actors distribute viruses in different ways, like:
- Embedding them in email attachments
- Disguising them as seemingly harmless software downloads
- Exploiting vulnerabilities in websites to inject malicious code
The goal is to trick the user into opening the infected file, which then lets the virus take hold and do its dirty work.
2. Ransomware
Ransomware is a type of malicious software that lets attackers hold your data hostage. The threat actor locks users out of their devices, encrypts files, and then asks for payment to restore things.
Ransomware can come from phishing emails, malicious downloads, or by exploiting software vulnerabilities. Once the ransomware infects a system, it encrypts files rapidly, often displaying a message with instructions for payment, usually in cryptocurrency. Threat actors might also threaten to publicly release sensitive data if the ransom isn't paid. The goal is to maximize disruption and fear, increasing the likelihood of victims paying up.
3. Trojans
Think of the trojan horse from Greek mythology—it looks like a gift, but it's hiding something dangerous inside. Once installed, a trojan can perform a variety of malicious actions, like:
- Stealing data
- Opening backdoors for other malware
- Controlling the infected computer remotely
Like the original Trojan horse, these malicious programs (the attack) are disguised as legitimate software (a giant, beautiful wooden horse). Unlike viruses, they don't self-replicate. Instead, they trick users into installing them by appearing harmless or even useful.
The key is deception: they rely on users being unaware of the true nature of the software they're installing, like pirated software, fake updates, or seemingly legitimate applications downloaded from trusted sources.
4. Spyware
Spyware is like having a digital stalker lurking in your devices, silently watching your every move. It can track your browsing history, capture keystrokes (including passwords and credit card numbers), monitor emails and messages, and even activate your webcam or microphone.
The threat actor then gathers data they can do whatever they want with, like identity theft, financial fraud, or targeted advertising. Threat actors often exploit software vulnerabilities as their attack vector to install spyware without the user's knowledge.
5. Adware
Also known as advertising-supported software, adware is a type of software that displays unwanted ads on a user's computer or mobile device. While not always inherently malicious, it can be incredibly annoying and sometimes carry security risks as a gateway for more serious malware.
Think of it as those pop-up ads that won't go away or software that suddenly floods your browser with unwanted toolbars and search engines. It can significantly disrupt your browsing experience and slow down your device.
Here are some ways threat actors may use adware:
- Bundle it with free software downloads, tricking users into installing it alongside the desired program.
- Spread it through malicious websites or browser extensions.
- More aggressive types of adware can collect your browsing data and display targeted ads or even redirect you to potentially dangerous websites.
6. Infostealers
Like digital pickpockets, infostealers target your login credentials, financial information, personal files, and browsing history. Instead of disrupting your system, this type of malware focuses on quietly extracting valuable data.
We found that infostealers were one of the top threats in our 2025 Cyber Threat Report. They’re often disguised as legitimate software or embedded in seemingly harmless files. Once installed, the infostealer silently collects data in the background, often logging keystrokes, capturing screenshots, and extracting saved passwords from browsers.
7. Bots
While many bots are used for legitimate purposes, like search engine indexing or customer service chatbots, malicious bots are used by threat actors for nefarious activities, like automating spamming, distributed denial-of-service (DDoS) attacks, or credential stuffing. Think of them as digital soldiers carrying out commands without human intervention.
Threat actors create botnets, which are networks of infected computers or devices controlled by a single attacker, to amplify the impact of their attacks. They infect devices through malware, often distributed via phishing emails or software vulnerabilities.
Once a device is infected, it becomes part of the botnet, and the attacker can remotely control it to carry out attacks. These botnets can grow to massive sizes, letting threat actors launch large-scale attacks that can overwhelm websites, steal data, or spread malware further.
8. Worms
Computer worms are a type of malware that can self-replicate and spread across networks without needing user interaction. Unlike viruses, which attach themselves to existing files, worms are standalone programs that can propagate on their own. Worms can also carry payloads that perform other malicious actions, like stealing data, deleting files, or installing backdoors.
They exploit vulnerabilities in operating systems or applications to spread from one device to another, often causing significant network congestion and disruption. Imagine a digital contagion that spreads rapidly through your network, infecting every vulnerable device it encounters.
9. Keyloggers
Keyloggers are a type of spyware that records every keystroke a user makes on a computer or mobile device. Think of them as silent observers, capturing everything you type, including passwords, credit card numbers, personal messages, and searches.
This information is then stored and transmitted to the threat actor, who can use it for identity theft, financial fraud, or other malicious purposes. It's like having someone looking over your shoulder as you enter all your sensitive information.
Keyloggers can be software-based or hardware-based. Hardware keyloggers are physical devices that are plugged into the keyboard connection. Software-based keyloggers are much more common.
10. Rootkits
Like digital camouflage, rootkits are a type of malicious software designed to hide the presence of other malware in a system. Essentially, a rootkit is a set of tools used to mask the existence of malicious files, processes, and network connections, making it difficult for security software or users to detect and remove them. Sneaky, sneaky!
Threat actors deploy rootkits by exploiting vulnerabilities in operating systems or applications. They often gain initial access through phishing attacks or other malware, then install the rootkit to solidify their control. Rootkits can modify system files and processes, making it appear as if everything is normal.
They can also disable security software and hide malicious activity from system administrators. This lets threat actors maintain long-term access to compromised systems, letting them steal data and wreak additional havoc.
Phishing and social engineering
We surveyed IT professionals about remote and hybrid cybersecurity and found that phishing and social engineering were a top concern. What’s more? Roughly one in four (27%) rated opening or downloading obvious phishing scams as the worst habit of remote and hybrid workers.
It’s no wonder that it’s such a problem, given the variety of types to watch for and the continuing changes in threat actors' tactics to avoid detection.
11. Phishing
Phishing is a type of cyberattack in which threat actors pretend to be someone they’re not to get the victims to reveal personal information. They often do this by creating a sense of urgency or trust by impersonating legitimate organizations or individuals through deceptive emails, messages, or websites.
In phishing scams, threat actors might:
- Create fake websites that look identical to real ones.
- Send emails that appear to be from a reputable source, like a notification from your bank or an email saying there’s a sale at your favorite store.
- Take advantage of current events or popular trends to make their campaigns more relevant and effective.
Their key strategy is to play on emotions like fear, curiosity, or greed to increase the likelihood of victims falling for their tricks.
12. Spear phishing
Spear phishing is a highly targeted form of phishing where threat actors craft personalized attacks aimed at specific people or organizations. Unlike general phishing campaigns that cast a wide net, spear phishing focuses on a specific victim, using information gathered from social media, company websites, or other public sources to create a highly convincing message.
This personalized approach dramatically increases the likelihood of the victim falling for the scam. Here’s how a threat actor may do it:
- Research their target extensively, learning about their job, colleagues, interests, and even personal relationships.
- Use this information to create a seemingly legitimate email or message that appears to come from a trusted source, like a coworker, business partner, or even a friend.
- The message might contain a malicious link or attachment that, when clicked, installs malware or steals credentials.
Because of the personalized nature of spear phishing, it can be extremely difficult to detect, even for experienced users.
13. Whaling
A reference to the famous white whale from Moby Dick, whaling is when threat actors intentionally go after high-profile individuals within organizations, like CEOs, CFOs, and other executives. These individuals have access to sensitive information and significant financial resources, making them prime targets for attacks.
Whaling attacks are essentially even more targeted spear phishing campaigns, using sophisticated social engineering techniques and meticulously crafted messages to deceive their victims. The goal is to trick these executives into performing actions that benefit the attackers, like transferring funds, revealing confidential data, or granting unauthorized access.
Whaling attacks usually involve urgent or high-stakes scenarios, like fraudulent wire transfers, fake legal demands, or urgent requests from superiors. Because of the targeted nature and the high value of the potential payoff, whaling attacks can be extremely lucrative for bad actors.
14. Baiting
Baiting is a social engineering attack that entices victims with a false promise or reward to trick them into revealing sensitive information or installing malware. Threat actors create a sense of urgency or exclusivity, making the victim feel like they're getting a valuable opportunity that they can't pass up.
Threat actors often use baiting to distribute malware or steal credentials by:
- Leaving an infected USB drive in public places, hoping someone will plug it into their computer.
- Offering free software, movies, or music downloads from untrusted sources online.
These downloads often contain malware or redirect users to phishing websites that steal personal information.
15. Pretexting
In pretexting, the threat actor creates a fabricated scenario, or "pretext," to manipulate a victim into sharing personal information or performing a desired action. They essentially construct a believable story to gain your trust and exploit that trust for their own gain.
Threat actors often use pretexting to impersonate authority figures, like IT support, bank representatives, or law enforcement officers. They might claim there's an urgent problem that requires immediate action, like a security breach or system error.
By creating a sense of urgency or fear, they pressure victims into providing sensitive information or doing things they wouldn't normally do. They might also use information gathered from social media or other public sources to make their pretext more believable.
Network attacks
A big problem in many industries, network attacks can lead to a screeching halt in business operations. Not only are they a threat to data security, but they also make it nearly impossible for businesses to continue as usual, as they disrupt essential communication and services, causing potential downtime and financial losses.
16. Denial-of-service (DoS) attack
Imagine trying to get into a store with a massive, unexpected crowd; you simply can't get through. In a DoS attack, the threat actor floods the target with so many requests that it becomes overloaded and crashes. The aim is to overwhelm the system, like a website or network, with a flood of traffic, rendering it unavailable to legitimate users.
Threat actors often exploit vulnerabilities in network protocols or applications to generate excessive traffic. The goal is to disrupt the target's operations, causing financial losses, reputational damage, or even political disruption.
17. Distributed denial-of-service (DDoS) attack
A DDoS attack is a more powerful and complex version of a DoS attack. Instead of a single source, a DDoS attack uses a network of compromised computers, known as a botnet, to flood a target system with traffic. This distributed nature makes it much harder to defend against, as the attack originates from numerous locations simultaneously. Think of it as a coordinated mob overwhelming a single point of entry.
Threat actors build botnets by infecting numerous devices with malware, turning them into "bots" that they can control remotely. They then have these bots overwhelm the target by sending a massive number of requests, causing it to crash. DDoS attacks are often used for extortion, political activism, or simply to disrupt online services.
18. Adversary-in-the-middle attack
Also known as man-in-the-middle attacks or eavesdropping attacks, adversary-in-the-middle attacks are when a threat actor gains access to data or information by intercepting between you and the website or app, both on send and return.
An example of this would be something like working in a cafe and signing in to their network, but an attacker has actually spoofed the Wi-Fi. Any data you send over that connection—login credentials, credit card numbers, personal information—passes through the attacker's hands. The attacker can intercept, view, and even modify this data before passing it on to its intended destination.
19. IP spoofing
IP spoofing is a technique where a threat actor forges the "return address" on their digital communications. This lets them hide their true identity, bypass security measures, or launch attacks that appear to originate from a trusted source. Imagine someone sending a letter with a fake return address to trick you into opening it.
Threat actors use various methods to spoof IP addresses, like:
- Manipulating packet headers and using specialized software.
- Spoofing the IP address of a trusted server to gain unauthorized access to a network.
- Launching a DDoS attack that appears to come from multiple sources.
IP spoofing can also be used in adversary-in-the-middle attacks to intercept and manipulate network traffic.
20. ARP spoofing
Also known as ARP poisoning, ARP spoofing is a type of attack where a threat actor sends forged Address Resolution Protocol (ARP) messages onto a local area network. ARP is used to map IP addresses to media access control (MAC) addresses, which are unique, physical hardware addresses.
By sending fake ARP messages, an attacker can associate their MAC address with the IP address of another host, like a router or another computer. This essentially tricks devices on the network into sending their traffic to the attacker's machine.
Threat actors typically perform ARP spoofing to intercept, modify, or block network traffic. They might use it to launch adversary-in-the-middle attacks, stealing sensitive information like passwords or credit card numbers.
ARP spoofing can also be used to redirect traffic to malicious websites or launch DoS attacks. The attacker sends out these forged ARP packets consistently, poisoning the ARP caches of the devices on the network.
21. DNS spoofing
Also called DNS cache poisoning, DNS spoofing is a cyberattack where a threat actor manipulates the Domain Name System (DNS) to redirect users to malicious websites. DNS translates domain names (like "example.com") into IP addresses (like "192.168.1.1").
In a spoofing attack, the attacker inserts false DNS records into a DNS server's cache, redirecting users who try to access a legitimate website to a fake one. It’s like changing the phone book entry for a business so callers end up at a different number.
Threat actors achieve this by:
- Exploiting vulnerabilities in DNS servers.
- Intercepting DNS queries and providing false responses.
- Sending forged DNS responses to a target server, poisoning its cache with incorrect IP address mappings.
- This can be done through techniques like transaction ID prediction or by exploiting known vulnerabilities in DNS software.
Once the DNS cache is poisoned, anyone using that DNS server will be redirected to the attacker's malicious website, which may look identical to the legitimate one. This lets them steal credentials, distribute malware, or carry out other malicious activities.
Vulnerability exploitation attacks
While many types of cyberattacks use vulnerabilities to execute an attack, vulnerability exploitation attacks are done exclusively through weaknesses in software or hardware to gain unauthorized access or control. Attackers find and exploit these flaws to inject malicious code, steal data, or disrupt systems.
Essentially, they take advantage of known or unknown security holes to compromise a target.
22. SQL injection
SQL injection is a type of cyberattack that exploits vulnerabilities in web applications that use SQL databases. Threat actors inject malicious SQL code into input fields, like login forms or search boxes, and the database server then executes it.
This lets them manipulate the database, retrieve sensitive information, modify data, or even gain administrative control of the server. Think of it as tricking the database into running commands it wasn't supposed to.
Threat actors identify input fields that aren't properly sanitized or validated, then craft SQL queries that are attached to real requests. For example:
- They might enter a specially crafted string into a username field.
- When processed, it bypasses authentication or retrieves data from other tables.
- This lets them access data they shouldn't have access to or even change or delete data within the database.
23. Cross-site scripting (XSS)
XSS is a type of web security vulnerability that lets attackers inject malicious scripts into websites viewed by other users. It's about tricking a website into displaying untrusted content as if it were part of the site itself. This can lead to stolen cookies, hijacked user sessions, or even redirection to malicious websites.
Threat actors implement XSS by finding input fields or other areas of a website that don't properly remove user-supplied data. They then inject malicious JavaScript code, which gets executed when other users view the affected page. This code can then steal user credentials, modify website content, or perform other harmful actions.
24. Cross-site request forgery (CSRF)
CSRF is a type of vulnerability that lets an attacker trick a user's browser into sending unwanted requests to a website where the user is currently authenticated. The attacker essentially uses the user's existing session to perform actions without their knowledge or consent.
Threat actors implement CSRF by creating malicious websites or embedding malicious code in legitimate websites or emails. When a logged-in user visits the attacker's website or opens a malicious email, the hidden code sends a request to the vulnerable website using the user's existing session cookies.
If the vulnerable website doesn't have proper CSRF protection, it will process the request as if it came from the user, letting the attacker perform actions like changing passwords, transferring funds, or making purchases.
25. Clickjacking
Clickjacking, also known as UI redressing, is a malicious technique where attackers trick users into clicking on something they didn’t mean to. They do this by overlaying hidden elements on top of legitimate web pages, effectively hijacking the user's clicks. Imagine a transparent button placed over a "delete" button, tricking you into deleting something when you thought you were clicking something harmless.
These layers are added by using iframes or other HTML techniques. They’re then positioned over interactive elements, like buttons or links, tricking users into clicking on them.
Threat actors can use this method for various actions, some less insidious, such as liking a Facebook page or following a Twitter account, or more malicious, like making unauthorized purchases. The victim is unaware that they’re performing these actions, as they believe they are clicking on something else.
26. Session hijacking
Also called cookie hijacking, session hijacking is a cyberattack in which an attacker impersonates a user by stealing their session cookies, which are used to maintain a user's logged-in state. Stealing them lets the attacker bypass authentication and perform actions as if they were the actual user.
Threat actors implement session hijacking through various methods, including XSS attacks, adversary-in-the-middle attacks, and malware. Once they have the cookie, they can access the user's account without needing their username or password.
27. Zero-day exploit
A zero-day exploit is a cyberattack that takes advantage of a software vulnerability that hasn’t been discovered or addressed yet by the vendor or users. Essentially, it's an attack that occurs "zero days" after the vulnerability is discovered, meaning there's no patch or fix available. Zero-day exploits are particularly dangerous because you can’t fix a problem you don’t know about!
Threat actors discover zero-day vulnerabilities through reverse engineering, code analysis, or by purchasing them from researchers or other threat actors. They then develop exploits that can take advantage of these vulnerabilities to gain unauthorized access, steal data, or install malware.
Because these vulnerabilities are unknown, traditional security measures like antivirus software or intrusion detection systems may not be effective. Once the vendor discovers the vulnerability, they quickly develop patches, making the window of opportunity short but highly damaging.
Other types of cybersecurity attacks
Many types of cybersecurity attacks fall outside of the four above categories. These include attacks that come from inside the organization, like insider threats, or others that use techniques that don’t fit within a specific strategy or framework.
28. Brute force attack
Brute force attacks are a trial-and-error approach where the attacker keeps guessing until they find the correct credentials. The threat actor tries every possible combination of passwords or encryption keys until they guess the right one.
Threat actors implement brute force attacks using automated tools that generate and test numerous password combinations. They might target login forms, encrypted files, or wireless networks. To increase their chances of success, they often use dictionaries of common passwords or variations of known passwords.
29. Password spraying
Where a brute force attack tries a ton of passwords to gain access to a specific account, password spraying, or dictionary attacks, try accessing many accounts using common passwords.
So, instead of hammering one account with endless password guesses, password spraying distributes a small set of commonly used passwords across a large number of accounts. This makes it less likely to trigger account lockouts, as it avoids excessive failed login attempts on any single account.
30. Credential stuffing
Credential stuffing is why password hygiene is so important.
A threat actor uses credentials they got from another data breach and tests them across accounts to try to gain access. They essentially "stuff" these stolen credentials into login forms across various websites, hoping users have reused the same username and password.
Threat actors acquire these credential lists from the dark web or other sources where stolen data is sold or shared. They then use automated tools to rapidly test these credentials against numerous websites.
If a user has reused the same username and password combination, the attacker gains access to their account. This is a very efficient attack method because it requires little effort from the attacker and preys on the common habit of password reuse.
31. Backdoor attack
A backdoor attack involves a threat actor creating a hidden entry point into a system or network, bypassing normal security measures. This lets them gain unauthorized access and control, often without the knowledge of the system's legitimate users or administrators. Think of it as a secret passage that lets an intruder bypass the front door and security system.
Threat actors implement backdoors through various methods, including installing malicious software, exploiting software vulnerabilities, or modifying system configurations. They might use trojans, rootkits, or other malware to create these hidden entry points.
Once a backdoor is established, they can use it to remotely access the system, steal data, install additional malware, or launch further attacks. Backdoors can stay undetected for extended periods, letting threat actors maintain persistent access to compromised systems.
32. Cyber espionage
Cyber espionage involves using hacking techniques to get unauthorized access to sensitive information from governments, organizations, or individuals for political, economic, or military advantage. It's essentially digital spying, where attackers seek to steal confidential data, intellectual property, or trade secrets.
Threat actors, often state-sponsored or organized criminal groups, carry out cyber espionage through various methods, including phishing, malware, and zero-day exploits. They target specific individuals or systems with access to valuable information, using sophisticated techniques to bypass security measures and stay undetected.
They might use spear phishing to target key personnel, use advanced persistent threat (APTs) attacks to infiltrate networks, or exploit software vulnerabilities to gain access to sensitive databases. The stolen information is then used to further the attacker's objectives.
33. Insider threat
The call’s coming from inside the house.
Insider threats involve security risks from within an organization, posed by employees, contractors, or other authorized users who have access to sensitive information or systems. These threats can be intentional, where someone purposely steals data or sabotages systems, or unintentional, like an employee accidentally clicking on phishing links or mishandling sensitive information.
Besides carelessness, insider threats may happen for any number of reasons, whether that’s personal gain, revenge, or to sell to competitors. Sometimes, external threat actors may even try to recruit insiders to perform malicious actions on their behalf.
34. Data breach
Data breaches are a top concern in various industries. They’re a larger category that describes many of the types of attacks on this list where sensitive, confidential, or protected data is accessed or disclosed without authorization. This can lead to identity theft, financial fraud, reputational damage, and legal consequences.
Methods include malware infections, phishing attacks, SQL injection, and exploiting software vulnerabilities. They might steal credentials to gain access to databases, use ransomware to extort victims, or exfiltrate data through compromised systems. Breaches often occur when multiple attack types happen at the same time.
35. Watering hole attack
A watering hole attack is a targeted cyberattack where threat actors compromise a website that is frequently visited by their intended victims. Instead of directly attacking the target, they infect a website that the target trusts and regularly uses, like a watering hole where animals gather. This lets them infect multiple victims with a single point of compromise.
Threat actors find vulnerabilities in these websites and inject malicious code, like JavaScript or iframes. When a target user visits the compromised site, their browser executes the malicious code, which can then install malware, steal credentials, or redirect them to phishing websites. This attack is effective because it leverages victims' trust in familiar websites.
36. Supply chain attack
Instead of directly attacking a target organization, supply chain attackers infiltrate a vendor or supplier that provides products or services to that organization. This lets them distribute malware or gain unauthorized access through a trusted channel.
“You could try to keep building as securely as possible, but if the thing that you've put on your machine is compromised or can be compromised, it's a backdoor for attackers to get in,” says Seth Geftic, former Huntress VP of Product Marketing. “It's really hard for defenders to do much about that, because normally you can't vet your accounting software or whatever else for security loopholes if no one knows those exist.”
Threat actors implement supply chain attacks by compromising software development tools, injecting malicious code into software updates, or tampering with hardware components during manufacturing or distribution. They might target open-source libraries, third-party software vendors, or hardware manufacturers.
Once a compromised component is integrated into the target organization's systems, the attacker can gain access to sensitive data, install malware, or disrupt operations. This type of attack is particularly effective because it leverages trust relationships and can affect a large number of victims.
How to protect against threat actors
Protecting yourself and your organization from the many, many types of cyberattacks may seem overwhelming. But staying vigilant and implementing strong security practices can significantly reduce your risk. Here are some key tips to help prevent cyberattacks:
- Employee training and awareness: Human error is a major vulnerability. Regular employee security training on phishing, social engineering, and safe online practices is crucial.
- Strong password policies and multi-factor authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security. MFA requires users to provide multiple forms of verification, making it much harder for attackers to gain unauthorized access.
- Regular software updates and patching: Software vulnerabilities are a common entry point for cyberattacks. Keeping operating systems, applications, and firmware up-to-date with the latest security patches is essential.
- Firewalls and intrusion detection/prevention systems (IDPS): Firewalls act as a barrier between an organization's network and external threats, while IDPS watches for unusual activity and reports and stops potential attacks.
- Data backup and recovery: Regularly backing up critical data and storing it securely lets organizations recover from ransomware attacks or other data loss incidents. Having a reliable recovery plan is crucial for business continuity.
- Endpoint protection and antivirus software: Implementing robust endpoint protection solutions and up-to-date antivirus software on all devices is critical. These tools can detect and remove malware, prevent unauthorized access, and protect against other cyber threats.
- Invest in cyber insurance: Cyber insurance is increasingly common, with some 79% of organizations having coverage. It can’t prevent an attack from happening, but ensures that any costs associated with one will be covered.
Avoid the most common cyberattacks with managed EDR
So, there you have it—a rundown of some of the nastiest things lurking in the digital shadows. While knowing about all these threats is helpful, keeping up with the ever-evolving landscape of the most common cyberattacks can feel like a full-time job.
That's where having a solid defense comes in. If you're looking for a way to seriously beef up your security and take the worry out of dealing with all this, consider a managed endpoint detection and response (EDR) solution. Let Huntress handle the heavy lifting with managed EDR so you can focus on what you do best.
FAQ
What is the most common cybersecurity attack?
Phishing and ransomware are two of the most common cyberattacks. It varies by industry, though—one of the top concerns in healthcare cybersecurity, for example, is data breaches.
What are the 5 most common types of cybersecurity threats?
The five most common types of cyberattacks include phishing, ransomware, malware, DDoS, and credential attacks like credential stuffing and password spraying. This varies by industry.
What do most cyberattacks start with?
Most cyberattacks start with some sort of vulnerability, whether that’s poor cybersecurity system management, human error, or a network issue, for example.