Creating accessible (and actionable) cybersecurity education is a huge part of our mission at Huntress — and last week, we were thrilled to host a unique event with 1,000+ live attendees: hack_it 2020.
This two-day event was packed with interactive exercises, malware research and analysis, and a healthy balance of offensive vs. defensive security tactics.
Missed the live event? We got you covered:
- Check out all of the sessions on-demand.
- Register for hack_it 2021 so you don't miss out on the fun this year.
- Or hit the recap below for some highlights.
Preparing for Worst-Case Scenarios
We played through two tabletop exercises, each designed as a choose-your-own-adventure session where our MSP audience controlled the content and steered its way through some tough ‘what if’ scenarios.
In some cases, our gamemasters Kyle Hanslovan and Kelvin Tegelaar really pushed the envelope of how you or your team might respond to a security incident — so our audience could learn how to handle situations that don’t go as planned.
Each scenario started out a little something like this: A phishing incident leads to an infection in your network. The attacker moves laterally through your network — gathering data, locating the ‘crown jewels’ and ultimately, deploying ransomware to your clients through your endpoint management software.
So what do you do in this situation? Where do you start?
Most of our attendees agreed that they would begin by assembling a response team and delegating roles — a wise choice which reinforced the idea that these incidents are not just technical problems; they’re company-wide problems. Before you start booting up backups and doing any forensic analysis, you’ve got to ensure you have a formal incident response plan to activate.
From here, we talked through other steps like how you would communicate what’s happening to your clients, or how you might take action from a technical standpoint. I won’t spoil too much for you — check out the recording of these exercises here.
Equally important during these tabletops was the question of what to do after an incident. What does communication look like? What needs to be documented and available for later review? How can you tighten up security to reduce the risk of a similar future incident?
The majority of our attendees agreed that you should perform an incident retrospect and document lessons learned, but Kelvin really emphasized the importance of checking in with your team.

A Deep Dive into Cobalt Strike
We’ve seen a slew of incidents that centered around abusing the Cobalt Strike penetration-testing framework, which was the focus of a special Tradecraft Tuesday episode on the hack_it 2020 agenda.
If you’re familiar with Tradecraft Tuesday, you know it’s where we expose hackers’ tactics, techniques and procedures — and in this case, we were joined by Annie Ballew and Tom Lawrence to look at Cobalt Strike from the adversary’s perspective.
Cobalt Strike is a commercial penetration-testing tool intended for red team exercises that anyone can buy and use. But we’re seeing that it’s actually becoming a favorite among malicious actors, who crack the software and repurpose it for nefarious purposes because it’s so flexible.
Cobalt Strike has a few notable features, but one that was of most interest to the Huntress team was its covert communication, which enables attackers to modify their network indicators on the fly to look like standard network traffic. And Cobalt Strike was built with “malleable command and control (C2),” so as a further evasion tactic, attackers are able to load C2 profiles to appear like another actor (or even other application traffic) and egress a network using HTTP, HTTPS or DNS.
When speaking about this capability during Whitehat Wednesday — a defensive-focused follow-up to the previous day’s session (now including Mendy Green) — the team noted how this makes it difficult to prepare your internal IT team to identify a known actor based on a predetermined signature (because malleable C2 allows actors to dynamically change their ‘fingerprint’). And with this polymorphism, your network-based detection will have a really hard time being able to see that.
So, it’s important to understand the offense of an attack and what to look for in order to ensure the best defensive approach — and this session really emphasized that.
The Importance of Security Analysis
Our final session of each day wrapped up with an introduction to security analysis and malicious behavior. Jason Slagle and John Hammond teamed up to give us a crash-course in thinking like a security researcher.
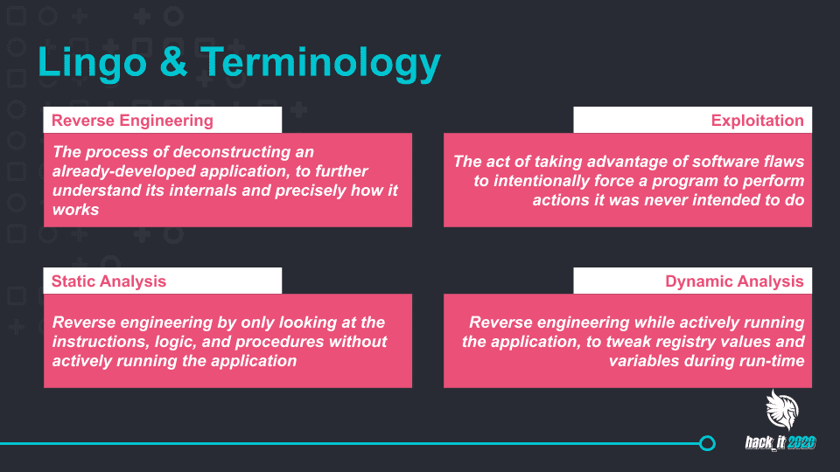
Sometimes you have to dive under the hood to poke holes in the tools we use. In this session, Jason and John did exactly that by looking at vulnerabilities that were found earlier this year — you can read up on them here and here. The pair showcased the importance of looking at software from a researcher’s perspective, recognizing odd behavior and reverse engineering to hunt for potential security flaws — all to help us level-up our security and make sure the whitehats find these types of holes before the blackhats do.
• • •
As you can tell, there was no shortage of valuable content at this year’s hack_it event — and this recap was just a small taste.
If you were able to join us live last week, thank you for being part of this event! It’s conferences and conversations like these that allow us to be a more security-conscious community. If you missed it, don’t worry. You can watch all of the recorded sessions here.
















