Don’t view SIEM as a luxury dashboard. It’s the difference between catching trouble early and reading about it in the incident report later.
This guide lays out the essentials for anyone evaluating SIEM and focuses on outcomes: less noise, faster detection, cleaner audits, and a security program that scales. It’s for teams of any size wrestling with SIEM defined in practical terms, weighing SIEM vs. EDR decisions, or mapping a roadmap from first deployment to mature operations.
We put this guide together because too many teams are buying tools and getting log fatigue instead of results. You’ll walk away with a clearer blueprint for rollout, the core signals to monitor, and a realistic view of costs, effort, and ROI.
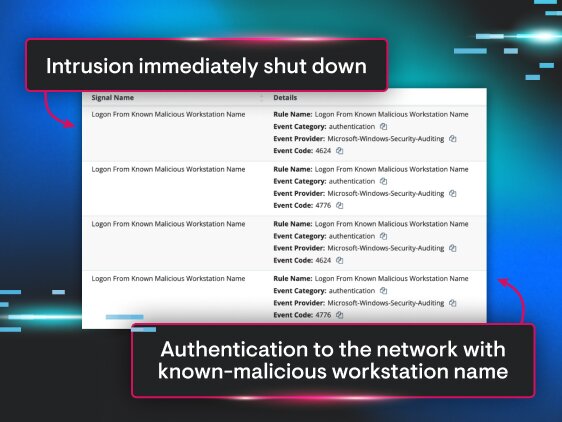
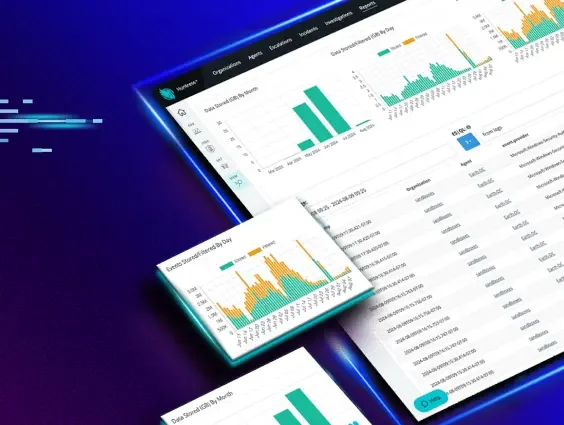
Huntress Managed SIEM that cuts through noise with smart filtering, transparent pricing, and a 24/7 SOC that actually handles the alerts for you. That’s the difference between another log bucket and a real defense layer.